Network Architecture
|
|
Typical Network Architecture with WLAN Added
The LAN network should be protected from users on wireless APs. Figure 4-12 shows a typical corporate infrastructure today. The Internet connects to a router on the WAN side. On the LAN side of the router, you may optionally connect a demilitarized zone (DMZ) server that is accessible from the Internet for file transfer, for example. A firewall separates the Internet from the corporate network on the LAN side. Often, this firewall function is included in the router. The LAN side serves computers and now more recently APs and wireless laptops. However, the new AP accidentally creates a way to get in behind the firewall through the air link.
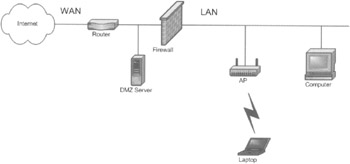
Figure 4-12: The WLAN architecture
Figure 4-12 shows how this leaves the network open to vulnerabilities. Once a user has gained wireless access, he or she also has access to the LAN inside the company.
Typical Network Architecture with a WLAN and Wireless Firewall Added
The network architecture can be changed by adding a wireless authentication firewall that regulates access to the LAN by enabling users to pass only after they have been authenticated, as shown in Figure 4-13. An optional wireless DMZ server or capture portal may exist on the WLAN side of the network. The wireless authentication firewall separates the WLAN from the LAN, thus protecting the enterprise's network from access through the wireless equipment. In an 802.1x/Extensible Authentication Protocol (EAP) arrangement, the AP will contain the firewall and an additional Remote Authentication Dial-In User Service (RADIUS) server will need to be located on the LAN. In a VPN arrangement, the LAN hosts a VPN server that forms the termination point of the VPN tunnel. Both of the firewalls will need a hole to carry VPN traffic from the WAN and WLAN side to the LAN.
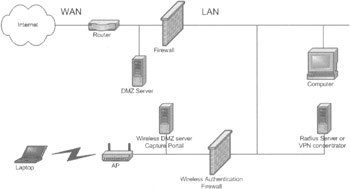
Figure 4-13: A wireless authentication firewall protects the LAN
Mobility and Security
If mobility is used, the solution must be secure during handoff. Handoffs open the network up to a redirection attack. If the network is not properly secured, the intruder can take over the communication with the destination entity after the handoff.
|
|
EAN: 2147483647
Pages: 96