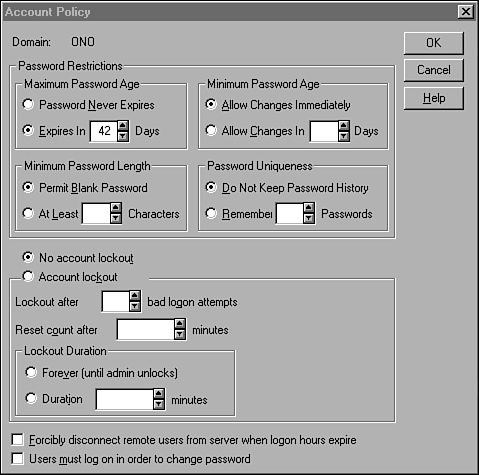
Passwords and Policies
| Windows NT enables the administrator to set certain parameters that control passwords and accounts. This is called the account policy for the domain. To view the defaults or make changes, select Account from the Policies menu in the User Manager for Domains utility. The Account Policy dialog box (see Figure 40.15) is displayed. Figure 40.15. The Account Policy dialog box. As you can see, you can configure various settings here. The values you choose for these parameters should reflect the degree of security you want to enforce at your site. At the same time, you need to balance your concerns with the abilities of your users. For example, if you set a large minimum password size and a low value for the number of days it can be used, users might end up writing down passwords just to keep track of them. These are the parameters you can configure here:
At the bottom of this dialog box, you can see two other check boxes. The Forcibly Disconnect Remote Users check box must be checked in order for the user to be disconnected from the server when he stays logged on past the authorized period specified in the Hours button of the user's Account Properties dialog box. If the second check box, User Must Log On in Order to Change Password, is checked, users will not be able to log on after their password expires and change it. The administrator will have to perform this function instead. If this box is not checked, after a user password expires the user still will be allowed to log on but will be required to change the password before performing any other function. Detecting Failed Logon AttemptsUser logon failures occur for many reasons. The most common reason is that users forget passwords or type them incorrectly enough times to trigger the account lockout mechanism. Because Windows NT allows you to create a single username and password logon for each user, the problem of multiple passwords is usually not a problem as it is some other networks. The Windows NT Event Viewer utility, found in the Administrative Tools section along with the User Manager for Domains, can be used to check for failed logon attempts. This is the first place you should look when a user is having problems logging on to the domain or connecting to a resource on a remote server. The user might not be providing the correct password or might be trying a username for which there is no account. The Event Viewer keeps three log files: Application, System, and Security. It is in the Security log file that you will find messages that relate to logon attempts. Some of the more common logon attempt “ related messages found in the Event Viewer are listed in Table 40.1. Table 40.1. Common Logon Errors You Can See Using the Event Viewer
As you can see, successful logon and logout events can be tracked. These types of messages can be useful when you are trying to determine who was on the system, perhaps during off hours, when you are trying to troubleshoot security problems. The other messages can be helpful in quickly identifying what the problem is when a user cannot log on to a server or connect to a resource. The security log file you can examine using the Event Viewer can be configured to track all successful and unsuccessful logon attempts. This includes users who log on locally at the computer, connections made through network access, and logons by special accounts that you set up to run services. Windows NT does not automatically track events such as these. You must enable the types of events you want to audit before they will be recorded in the security log file. See Chapter 47, "Auditing and Other Monitoring Measures," for information on how to set up the events to audit for Windows NT computers. |
EAN: 2147483647
Pages: 434