Piconets and Scatternets
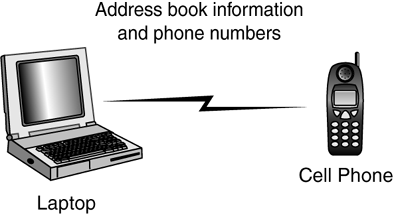
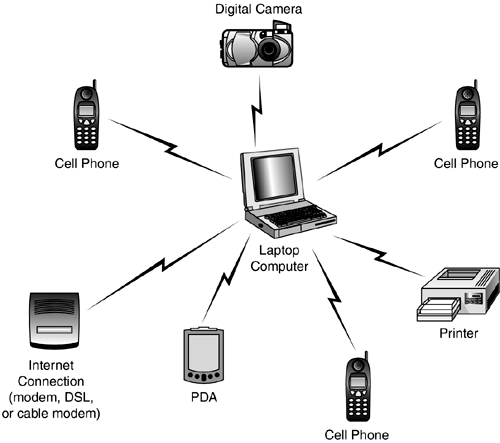
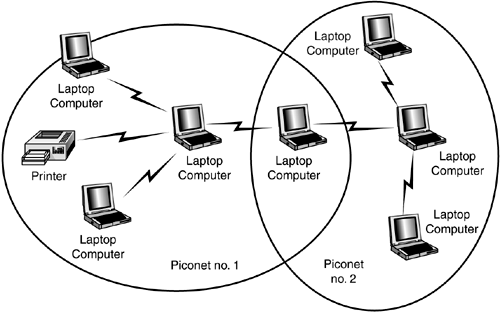
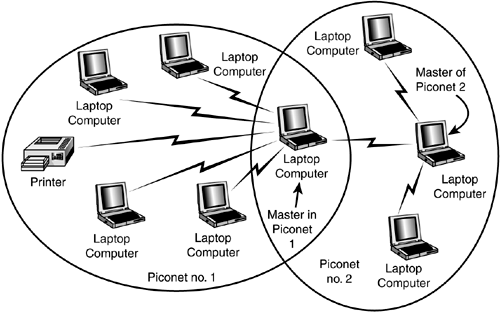
| The ad hoc nature of Bluetooth networking minimizes the need for management or administrative functions for networks made up of Bluetooth-enabled devices. In Chapter 19, "Introduction to Wireless Networking," you learned that an ad hoc network consists of multiple wireless devices that communicate with each other, without a central controlling device. This is basically the method used by Bluetooth. Contrast this with using an Access Point with 802.11 wireless networks. 802.11 wireless networks can be used to create an ad hoc network, but usually a controlling Access Point is used to coordinate communications between members of the wireless network. To put it quite simply, an ad hoc network consists of multiple wireless devices that communicate with each other. In the case of Bluetooth, as described next , there is no dedicated Access Point to control data transmissions. Instead, the first Bluetooth device that initiates a transmission becomes a temporary "master" of the small network, and other devices are "slaves" that receive permission to transmit/receive from this master. The master is not a dedicated device like an Access Point. In PANs, devices in close proximity can discover each other and form a small network (called a piconet) without user intervention. This enables users to transfer data between a cellular phone and a laptop computer, for example, by coming within range and instructing the cellular phone or computer what action to perform. PiconetsA piconet is formed when two or more devices discover each other and begin to communicate. A piconet can have up to eight devices, with one device acting as a master and the rest acting as slaves. The first device to initiate transmission becomes the master, although the specification provides for a master and slave unit to exchange roles. A specific frequency- hopping sequence is used by all devices within each piconet. Figure 23.2 shows the simplest example of a piconet: A cell phone is downloading address-book and telephone-number information to the user's laptop. Figure 23.2. A piconet consists of at least two Bluetooth-enabled devices. In this example, the laptop acts as a master. The application software running on the laptop contacts the cell phone when it is within range, and requests that it synchronize its database with the one stored on the laptop. As stated earlier, a single piconet can have up to eight devices. The reason for this limit is simple: The address is only 3 bits long. This means that in binary, only the values of 0 “7 can be stored in the address field. The master has no address, but 0 is reserved for broadcast messages; so the only addresses remaining for use by slaves are 1 “7. However, a device can participate in two different piconets (called a scatternet ), which is covered in the next section. Figure 23.3 shows an example of a larger piconet, in which one master controls multiple slaves in a piconet. Figure 23.3. A piconet can have only one master and up to seven slave devices. You can see that it's possible to link various devices in a piconet. You can download digital images from your digital camera to the laptop, use more than one Bluetooth-enabled cell phone to place voice calls, and even connect a personal digital assistant (PDA) to the laptop to exchange information. Another interesting thing to note in this figure is that you also can use a single connection to the Internet without having to have a direct cable connection to the modem or broadband connection. The master device in Figure 23.3 is the laptop computer. It controls the other devices, which are called slaves. ScatternetsA device can be a master of only one piconet. The device can, at the same time, also be a slave in another piconet that is within range. A slave can also participate in two different piconets that are within its range. However, because the master device determines the hopping pattern used for a piconet, a device cannot be a master of more than one piconet. An example of a simple scatternet is shown in Figure 23.4. Figure 23.4. A scatternet is formed when a device is a member of more than one piconet. In this example, a laptop computer communicates with devices in both piconets. Note that the laptop is a slave in both piconets. It is possible, however, for the laptop to be a master in one piconet and a slave in another, as shown in Figure 23.5. Figure 23.5. This Bluetooth-enabled laptop computer is a master in one piconet and a slave in another. When a device is a member of two piconets, it keeps track of both frequency-hopping patterns and occasionally listens in on the correct frequency on each of the two piconets so that it can stay in touch with both piconets. A master device transmits a packet to its slaves occasionally to maintain the link, based on negotiations between the master and its slave devices. Thus, a device that is a member of two piconets must listen for these transmissions (or make them if it's the master in one piconet) within the timeframe negotiated for each of the piconets of which it is a member. |
EAN: 2147483647
Pages: 434