Using the Network on Purpose
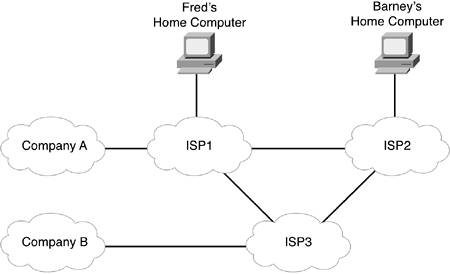
| For Fred to do his job, he really didn't need to know that the network existed. Sure, intellectually Fred could look at the new cabling Wilma had set up, see the printer cabled to Wilma's computer, and realize that something had to happen to let his computer print on Wilma's printer. But Fred didn't need to act any differently to use the networkhe still opened files, saved them, and printed them. Although some of Fred's job tasks didn't require that he think about being connected to a network, when he goes home and uses the Internet, chances are Fred will be aware that he is using a network. The Internet is the global network to which almost every company and organization in the world is connected. Unless you've been asleep for the past 10 years, you've probably heard of the Internet. In its most basic form, the Internet is a large number of networks that are connected together, allowing computers in each network to communicate with others. The Internet also includes many individual users that connect to the Internet from their homes. You can make a phone call to most anyone on the planet because all the telephone companies in the world connect to each other; similarly, most computers can communicate with each other over the Internet because most computer networks connect to each other through the Internet. You can think of the word "Internet" as meaning interconnected networks. Many of the networks that comprise the Internet are enterprise networks. To create the basic connectivity between enterprise networks and home Internet users, Internet service providers (ISPs) provide networking connections among enterprises, individual home users, and other ISPs. To create the Internet, any single organization simply needs at least one connection to another network. For instance, most enterprise networks connect to at least one ISP. Each ISP connects to at least one other ISPtypically several ISPsso that there is at least one path from every company to every other company. As a result, everyone who is connected to the Internet can communicate. The general populace can connect to an ISP of their choosing as well. By doing so, an individual can communicate with the computers in most of the companies of the world, as well as the computers owned by the general populace. Figure 2-5 shows the general idea. Figure 2-5. Conceptual View of the Internet
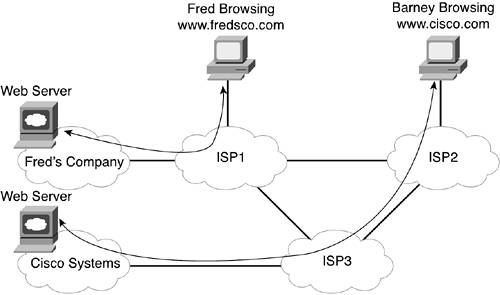
Figure 2-5 shows Company A with a line connecting it to ISP1. The line represents a cable that can allow the enterprise network and ISP1 to communicate. ISP1 has created a network, with the details hidden by a network cloud. ISP1's network allows individual computers, such as Fred's, to connect to it. It also allows corporate networks, such as Company A, to connect. So, Fred could communicate with computers inside Company A, assuming that the security policies at Company A allowed it. But that's another story for Chapters 17, "Accepting the Right People and Rejecting the Wrong People," and 18, "Keeping a Watchful Eye over Who Drives into (Your Network) Neighborhood." Company A created its enterprise network using hardware, software, and cabling paid for by Company A. ISP1 creates its network as well, using its own funds. ISP1 agrees to allow Company A's traffic to pass through ISP1 and on to other ISPs so that Company A can communicate with the rest of the world. In return for allowing Company A to communicate to the rest of the Internet using ISP1, Company A pays ISP1 an ongoing fee. Similarly, Figure 2-5 shows Barney connected to ISP2. Barney probably used his phone line, his computer, and a modem to connect to ISP2. A modem is a device that allows a computer to communicate with another computer using a plain old telephone line. The vast majority of individual Internet users use a modem and a phone line to connect to the Internet. After Barney has connected to ISP2, he can communicate with computers in Company A, Company B, and with his buddy, Fred. Like Company A, Barney pays his ISP (ISP2) a fee for allowing him to access the Internet. The Internet revolution has affected the world as profoundly as almost any invention in history. The ability to communicate across cultures, across national boundaries, relatively quickly, and with (relatively) unfettered freedom of speech has forever changed the way in which people live. News stories routinely emerge more quickly via the Internet than via the world's most powerful news services can find the story. The ability to communicate between computers in different companies' enterprise networks, as well as with individual users, allowed several popular applications to emerge. This section covers a few of the more popular applications, including web browsing, electronic mail (e-mail), file downloading, and file transferring. Web BrowsingAlmost everyone reading this book has probably used a web browser. A web browser allows you to sit at one computer and display information that resides in a web server somewhere on the Internet. The information can be in many forms, including simple text, graphics images, animation, video streams, and audio clips. Even if you've not heard of the term web browser, you might have heard of Internet Explorer or Netscape, which are the names of two of the more popular web browsers on the market today. The browser is actually software that resides on the computer used by the end user. The browser requests a web page from a web server, and after the server responds, the web browser displays the information sent to it by a web server. A web server consists of software that resides on the computer that is accessible to the end user via the Internet. After a browser requests a web page from a web server, the server replies by sending the contents of the web page back to the browser. Many people refer to the actual contentthe stuff that shows up on the screen when you are using a browseras a web page. So, if you go to http://www.cisco.com, you will see a web page for Cisco Systems, the largest vendor of networking equipment. If you click other links on that web page, you'll go to other web pages. If you do that, you will be using Cisco's website. The term website refers to all the content in the various web pages built by that company. The basic model revolving around web services is similar to how a new retail business works in real life. Someone has an idea about opening a store to sell something. For instance, perhaps this person wants to sell clothing for children. There's a lot to do before opening the store, including ordering inventory, leasing and preparing the store, hiring employees, advertising, and lots of other things. Finally, the day comes, and the owner opens the store for the first time and hopes someone will show up to buy something. Web services evolve in the same way. Someone has an idea for a website. Maybe it's a site for this same retail children's clothing store or for some established business, or maybe it's just someone who has something to say. This person then builds a website that consists of multiple web pages. The website resides on a web server that is connected to the Internet. At that point, it's like opening day at the retail storeyou hope someone shows up at the website! The usage of the webthe combination or web servers, web browsers, and websiteshas become one of the most prolific applications in the Internet, as well as in enterprise networks. Companies, organizations, and even individuals can create their own websites on the Internet. Anyone can then ask for the content in those web pages and see the results. Figure 2-6 shows an example of a couple of web servers on the Internet, with Fred and Barney browsing their websites. Figure 2-6. Web Browsers and Web Pages on the Internet
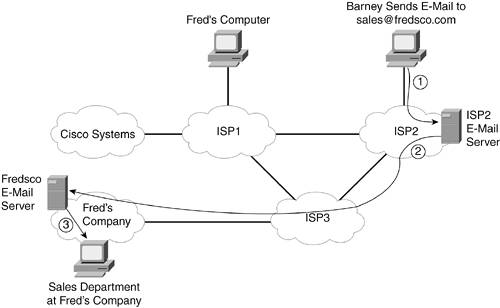
Each company's web server is inside its respective enterprise networks in Figure 2-6. Because each company has a connection to an ISP, Fred and Barney can connect to the web pages and browse the contents. To browse these web pages, Fred and Barney must each bring up the web browser software on their computers and point to the Universal Resource Locator (URL) of the website. The URL is a string of characters that uniquely identifies a particular web page. Sometimes, people refer to the URL as a web address. For instance, when Barney puts http://www.cisco.com into the right place in his browser, his browser asks for the web page of Cisco Systems. Figure 2-7 shows the Cisco web page. Figure 2-7. Example Web Page: http://www.cisco.com The web browser, in conjunction with websites, represents one of the most popular network applications today. And because the main purpose of a website is to make information available to other users of the network, it relies on the existence of a network. Electronic Mail (E-Mail)Another popular network application on the Internet is electronic mail, or e-mail. E-mail allows the user to create, send, and receive messages electronically. It's essentially the same thing as mail that you would send through the postal service, except that the message is sent electronically over a network, rather than physically sent using planes, trains, and trucks. In fact, the term snail mail is often used to refer to traditional paper mail, which takes days to deliver as opposed to seconds. Of course, the postal service has to overcome a lot more difficulties than e-mail does. For example, the postal service has to physically move tons of letters and packages, so it's reasonable that it takes a few days to deliver letters. E-mail works on a totally different conceptual model as compared to the web. With web content, if someone has something to say, he creates the content, and at some later time, anyone can look at the contents of the web page. E-mail, however, is sent between one user and another user, or in some cases, to multiple other users. So, the person sending the mail needs to know the e-mail address of the person who needs to receive the e-mail. An e-mail address is a text string that represents the address of a person for the purposes of sending and receiving e-mail, much like a mailing address used for snail mail. With web services, the web server needs to be connected to the Internet before someone can browse the website using a web browser. With e-mail, the sender and the receiver do not have to be connected to the network at the same time. For instance, Fred can connect to the Internet from home and send an e-mail to Barney, even if Barney isn't connected to the Internet at that time. Later, when Barney connects to the Internet, he can check his mail and get the e-mail that Fred sent earlier. To allow the sender to send an e-mail, even when the recipient is not connected to the Internet, e-mail uses the same general model that the postal service does. If you want to send a letter via snail mail, you put it in a nearby mailbox. The postal service moves the letter to the address of the recipient and puts it in the recipient's mailbox. The recipient does not have to be home when the postal carrier comes byhe just has to look in his mailbox for today's letters when he gets home. Figure 2-8 illustrates how e-mail uses a model similar to that of the postal service. Figure 2-8. E-Mail in the Internet Using Mail Servers
The e-mail passes through three steps before being received by the right person. The following list outlines the three steps, referring to the numbers on the figure. Afterward, I'll give a more detailed explanation of these steps.
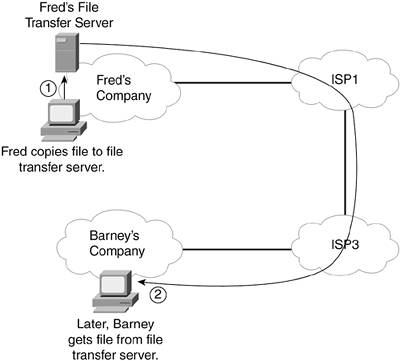
In the first step, Barney has visited the fredsco.com website, where he saw information telling him about some bowling balls for sale. Barney wants to beat Fred the next time they bowl, using a brand new bowling ball built by Fred's own company. So, Barney e-mails the sales department at Fred's Company by sending an e-mail to the address of sales@fredsco.com. Barney does not actually send the e-mail directly to a computer at Fred's Company. Barney sends the e-mail to his e-mail server, which for an individual Internet user like Barney, typically sits inside the ISP network to which the user is connected. An e-mail server is a server that receives, forwards, or holds e-mail, much like the service performed by the postal service. That e-mail server forwards the e-mail to the e-mail server at Fred's Company. By using these two steps, Barney can send the e-mail, even if the e-mail server for Fred's Company is not currently connected to the Internet. ISP2 keeps its e-mail server up and available all the time, just like you would for a web server. The e-mail server at ISP2 simply waits until it can successfully forward the e-mail to Fred's e-mail server. Finally, when the e-mail sits in the fredsco.com e-mail server, the end user (in this case, a friendly salesman at Fred's Company) can retrieve the e-mail messages at his convenience (Step 3 in Figure 2-8). So, after a morning golf "sales call," the salesman might come in and check his e-mail, finding Barney's e-mail. The terms e-mail client and client have specific meanings in networking. Generically, any application program that an end user uses to access some network server is called a client. A web browser, for instance, is a client program. An e-mail client is the client software used for e-mail. Microsoft Outlook is one of the more popular e-mail client programs. E-mail has become one of the most common networking applications, with a large portion of the population, both young and old, able to send messages to each other for no incremental cost. Even my parents, who grew up in a world where many people did not even have telephones, use e-mail today. Just like web applications, e-mail works just fine inside a single enterprise network. However, the Internet allows pervasive access to e-mail for literally billions of people, so you can communicate with friends and acquaintances all over the world. Downloading and Transferring FilesThe final end user application covered here is a broad topic area, but with one central theme: moving files into and out of your computer using a network. In most cases, the end user does not have the file, and he wants to get it. However, the user might want to do the opposite; in other words, he might want to move a file on his computer to another computer. Regardless of whether the user wants to retrieve a file or transfer a file to someone else, the action still falls under the category of file transfer. File transfer refers to a network application that allows a user to copy files from one computer to another. The term download typically refers to the process of retrieving a file that someone else has and making a copy on your computer. So, downloading would technically be the same thing as file transfer. (Conversely, the term upload refers to transferring a file from your computer to another computerin other words, giving a copy of the file to another computer.) One rather mundane type of file downloading is when you decide to update the software on a networking device. The vendor that sells the device allows you to download new software via the Internet. The vendors are happy to have you download the files; that's a lot cheaper for them than mailing the software to you using the postal service. A more interestingand much more controversialexample of downloading is the downloading of music files. I would imagine that a lot of you who are already active on the Internet know what I'm talking about already! It started with a craze called Napster, which eventually reinvented itself after lawsuits from the music industry. Several other tools have also emerged, all with the same goal: to allow people to download copies of music, often without paying for it. Legal and moral issues aside, these services allow you to move files, so they fall into the category of file transfer. Like web browsing and e-mail, file transfer can be used in an enterprise network or across the Internet. For example, imagine that Fred and Barney need to work on a project, and each needs to update a file called myproject.doc. Fred does not work at the same company as Barney, so Barney's file server is not available to Fred for security reasons. Figure 2-9 outlines the basic process. Figure 2-9. Copying myproject.doc Between Barney and Fred
Fred and Barney together do a little dance called the file transfer two-step, as numbered in the figure:
After this process is complete, both Barney and Fred have a copy of the file. However, if both keep working on their own copies of the file, merging the files back together can be a problem. So, although you can share files using file transfers, you need to be careful regarding who has "control" of the file at any one point in time. |
EAN: 2147483647
Pages: 173