Common Firewall Management Tasks
| One of the first things to accomplish when deploying a new firewall, whether this is for an enterprise deployment or for a deployment in a small office or home office, is to configure some basic aspects of networking. Doing so includes changing the default administrative password, configuring the default gateway, configuring the IP addresses for the internal and external (and possibly other) interfaces, and configuring the logging of messages from the firewall. In addition to these tasks, the firewall administrator must also manage the configuration of the firewall over time. Doing so may require the use of a change control system such as the Revision Control System (RCS), which is available both on the UNIX/Linux platforms as well as the Windows platform. The following sections discuss each of these tasks in more detail. Initial ConfigurationThe initial configuration of a firewall requires several items of information. This information includes both the internal and external interface IP addresses (or the use of DHCP on one of those interfaces), the next-hop gateway, logging, and an administrative password. The first three items are discussed in the following paragraphs. A discussion of administrative passwords was provided earlier in the "Default Passwords" section. InterfacesMost small office/home office (SOHO) firewalls have only two interfaces. On enterprise firewalls, there can be well over a half dozen interfaces that comprise various demilitarized zones (DMZ) with varying levels of security. In addition, newer enterprise firewalls can also support VLANs and filtering between VLANs while only having a limited number of physical interfaces. All firewalls have at least two interfaces:
In addition to the IP addresses on the various interfaces, the firewall can also run a DHCP server to provide IP addresses and other configuration information to systems inside the firewall. This server makes the deployment of a SOHO firewall much easier because most vendors also provide some default configuration for the DHCP server, too. Care must be taken to ensure that the scope of the DHCP server does not overlap or conflict with any DHCP scope already in place in the network. Also, in the case of wireless firewall routers (such as the Linksys BEFW11S4 or the WRT54G) that are popular these days, it is extremely important for the administrator of the device to ensure that only authorized users can associate and authenticate to the device. If these devices are not locked down, any user can authenticate and associate to the device, and the DHCP server will provide them with a network address that they can use. Routing/GatewayIn many cases, where simple firewalls such as the Linksys, the Linux NetFilter, or the PIX 501 or 506E firewalls are used, there is a simple network topologyessentially an internal network behind the firewall and an external network (typically consisting of the external IP address provided by the service provider). These firewalls do not do complex routing but rather just forward packets from the internal network to the external network using a default gateway. The default gateway information is provided either by the administrator or by the service provider's DHCP server when the firewall boots up. In enterprise networks, however, the firewall can segment multiple networks and DMZs from each other. In this case, the routing can be quite complex and may require the use of a dynamic routing protocol such as the Routing Information Protocol (RIP) or the Open Shortest Path First (OSPF) routing protocol. To add a default route to a Cisco PIX during initial configuration, you need to use the route command as follows: pix(config)# route outside 0.0.0.0 0.0.0.0 172.16.45.1 1This tells the PIX that the default route goes out the outside interface, that the next hop is 172.16.45.1, and that it is only one hop away (that is, it is the next device going outbound). LoggingLogging is also essential for maintaining and administering a firewall. Logging enables the administrator to see all the traffic blocked by the firewall as well as troubleshoot the firewall configuration when a particular function, such as Network Address Translation (NAT), is not working as expected. Most firewalls such as the PIX 501 or 506E and Linux's NetFilter allow for logging of messages to remote syslog servers. Syslog's origins are in the UNIX operating system, and syslog is used by a wide variety of processes on many Linux, BSD, and UNIX-derivative operating systems. In addition, many vendors, such as Cisco, have adapted syslog to their products such as IOS and PIX OS. Syslog is defined in the Internet RFC 3164 (available from the Internet Engineering Task Force (IETF) website at http://www.ietf.org/rfc/rfc3164.txt?number=3164). The two primary concepts to understand with syslog is the message facility and the severity. Each message generated and sent to a syslog server must be sent with a defined facility and severity for the syslog server to understand how to handle the message. The currently defined facilities and severities defined in the syslog RFC (3164) are listed in Table 11-2 and Table 11-3, respectively. There are eight levels of syslog severities possible, as defined in RFC 3164 and shown in Table 11-3 in descending order. One of the confusing aspects of the syslog severity levels is that the lower the numeric value of the severity (with 0 being an Emergency), the higher the severity of the message being sent. Also, the "lower" the severity (that is, the higher the numeric value of the severity), the greater amount of information that is generated by the process. So, level 7, Debug, produces a prodigious amount of syslog log messages, whereas level 0, Emergency, produces few messages (but of critical significance). Because syslog originally was developed on the BSD UNIX operating system, many facilities are assigned to specific processes and daemons in UNIX. Processes that have not been explicitly assigned a facility may use one of the "local-use" facilities.
In many cases, syslog servers are kept behind the firewall and, more preferably, in the management network; therefore, there is no need to open up the firewall to allow these messages to reach the server. Example 11-3 demonstrates the commands to configure a PIX 501 or 506E to send its logs to a remote syslog server. The following commands are entered in the configuration or config mode of the PIX device. Example 11-3. PIX Logging
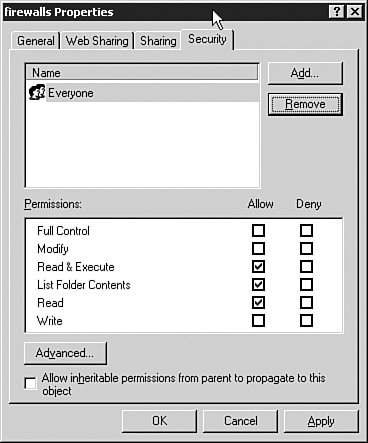
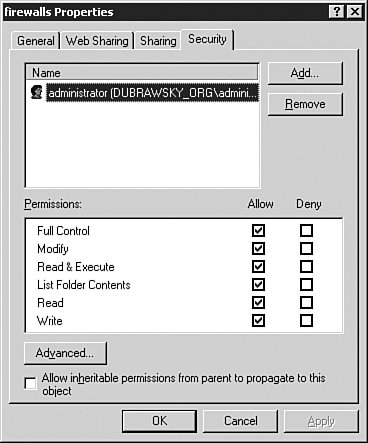
The command logging on tells the device to turn on logging on the device, and the logging timestamp command ensures that a date/time field is inserted in each syslog message sent to the remote syslog server. The logging trap informational command specifies the level of logging to be conducted. The reason why Informational is a good level to use for logging with the PIX is because it provides enough information to monitor the traffic going through the PIX without overwhelming the administrator with unnecessary information. Level 7, Debug, is typically used only to try and determine a problem with the configuration of the PIX or why some capability of the PIX does not work. The logging facility 21 syntax specifies which syslog facility is used. The facility 21 syntax translates, according to Table 11-2, to local use 5. Finally, the last line, logging host inside 10.16.17.124, tells the PIX to send its messages to the host on the "inside" of the PIX (that is, the host on the internal network) with the IP address of 10.16.17.124. No matter how the firewall logs information, it is critical that the logged information be reviewed by an administrator. Administrators can distill the information from firewalls and other sources via a variety of different log analysis tools. These tools range from commercial tools such as CiscoWorks VMS to open source or freeware tools. An excellent resource for log analysis tools is the website http://www.loganalysis.org. Cisco provides detailed instructions on how to set up a syslog server to receive the various messages generated by the PIX firewall. These instructions are applicable to any device that can generate a syslog message and can be found here: http://www.cisco.com/en/US/products/hw/vpndevc/ps2030/products_tech_note09186a0080094030.shtml#setupsyslogd Modifying the ConfigurationAs with any device, from time to time you will need to modify the configuration of the firewall. Whether this is due to a new device brought on line to access the Internet or the addition of a new web server behind the firewall, it will be necessary to change the firewall configuration. The problem with modifying the configuration comes down to change controlensuring that changes made to a firewall are tracked and logged in case of problems. These items are discussed in the sections that follow. Change ControlChange control is defined as the process and procedures to manage changes being made to a product or its configuration. For the sake of this discussion, the focus is on the control of changes made to the configuration of a firewall. Change control for firewalls relies on either those changes being logged or a copy of the previous configuration being stored or both. One of the simplest ways to control changes to the configuration of a firewall is to use some sort of revision control systemsuch as Revision Control Service (RCS) or Concurrent Version System (CVS)to check the changes and, if necessary, to re-create a previous version of the configuration should a problem arise. This works when the configuration of the firewall is stored as a text file that can be downloaded to a system acting as the RCS or CVS repository. When the configuration of the firewall cannot be downloaded as a text file, a running log of the changes made to the firewall should be kept so that changes can be backed out of if necessary. See http://www.cs.purdue.edu/homes/trinkle/RCS for more information regarding RCS, CVS, and other change-control software systems. To set up a simple change-control system such as RCS (on UNIX, Linux, or Windows) to manage the changes to firewall configurations, it is important to remember that configurations sometimes contain sensitive administrative information such as passwords or access control lists (ACLs). It is important that the RCS (or CVS) system and the directory or folder containing the configuration files be kept secure. In UNIX or Linux, this requires changing the permissions of the RCS repository such that only root or others within an administrative group have access privileges, for example: # chgrp wheel configs # chmod -R 750 configs These commands change the group ownership of the configs directory to the wheel group and then change the permissions on it, as well as all directories beneath it, to read, write, and execute for the owner; read and execute for group members; and no permission for everyone else. This restricts access to the directory, in this example, to just the owner as well as those other users who are members of the wheel group. However, the group members cannot make changes to the files within the directory. They can only view them. Only the owner can make changes to the files in the configs directory. Under Windows, the process is similar. To restrict access to the administrator only or to the administrative group, the everyone group must be removed. This can be accomplished by setting the permissions as shown in Figure 11-7. To set the security permissions on the folder, you must right-click the folder and choose Properties. This opens the folder Properties window as shown in Figure 11-7. In the folder Properties window, open the Security tab. This opens the Security permissions for the folder, as shown in Figure 11-8. Figure 11-7. Folder Properties Figure 11-8. Initial Security Settings for Folder Select the Everyone group and click the Remove button on the right side of the Properties window. Then click the Add button to add the user you want to have ownership of the folder (in this example, the domain administrator has ownership). Figure 11-9 shows the result. Figure 11-9. Final Security Settings for Folder When that is accomplished, access to the folder is limited to only those with the proper credentials, as shown in Figure 11-10. Figure 11-10. Access Denied Without Proper Credentials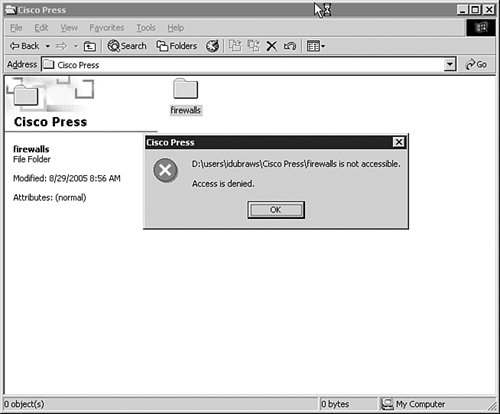 When the configuration repository directory has been secured sufficiently, the next step is to check in the initial configuration to the repository. The initial configuration is the starting point that you will use as a known good configuration for the device. Any changes made after the initial configuration is tracked using the configuration repository. By doing this, you will be able to reconstruct a good configuration in case a specific change is not good or needs to be removed. In addition, by using revision control, you can find out who made what changes and why by requiring the individual making the change to enter a log entry explaining the change and the need for it. To check in the initial, known good configuration for the device, you just use the checkin (ci) command as shown in Example 11-4. This example shows how to check in a file to the repository as well as how to check out a file from the repository. These commands are entered on the command line in both UNIX and the Windows environment. Example 11-4. Using RCS for Configuration Control
The ci command checks the configuration into the repository. The i flag tells the RCS software to create and initialize a new repository. The co command is used to check items out of the repository. The l flag also locks the repository for the specific user who issued the co command. When the configuration file is checked out of the repository, it appears in the local directory (or folder in the case of Windows) as shown above at the end of Example 11-4. The working file in this case is frodo.cfg. After the file has been checked out and locked, only the current user can make changes to the configuration. When the file is then checked back into the repository, the changes made must be logged. Whenever you check a new revision back into the repository, the RCS software allows you to add a log message to the repository to explain the changes. Example 11-5 demonstrates how to check the configuration changes into the RCS repository. Notice that the i flag was not used because we are not initializing the repository. After the configuration has been checked back into the repository, the working file (in this case, frodo.cfg) is deleted by the RCS software. Example 11-5. Checking in Changes to the RCS Repository
RCS, CVS, and other open source revision-control systems provide an easy, low-cost way of managing and controlling configuration changes. Change-Control LoggingChange-control logging is the process by which information is entered in the change-control system regarding changes made to a configuration. It is important that information about configuration changes be included when they are made. This provides for easier troubleshooting should a problem occur with the new configuration. When new configuration revisions are checked in to the repository, the RCS software automatically provides for the addition of a log message. The log message should sufficiently reflect the changes made to the configuration so that another person can go in, identify the changes, and be able to back them out if necessary. One way of viewing all the changes made to a particular configuration file through RCS is the use of the rlog program. The rlog program prints log messages and other information about files in the RCS repository. Example 11-6 demonstrates viewing the RCS log for a configuration using the rlog command. To view the log file for changes made to the configuration being managed through RCS, the syntax is just rlog filename. This displays the log entries for all changes made to the file. Example 11-6. Viewing the RCS Log for Configuration Changes
The output in Example 11-6 provides a lot of information. For example, the working file is identified in the Working file line. In addition, it shows how many revisions have been made to the file (in the example, two revisions have been made). A description of the file is provided and below that the revision log entries. This shows all log entries of the changes made since the configuration file was first checked in to the repository. Note that the name of the user which made the change to the NAT configuration was entered into the log message itself. The user was using the root administrative account however. This is important if the person needs to be contacted regarding the changes he or she made. It is better practice to use individual user accounts to provide accountability for any changes that need to be rolled back out of a configuration. To view changes made between configurations, the administrator can use the rcsdiff command as shown in Example 11-7. The rcsdiff command shows the difference between two revisions of a given file in the RCS repository. In the case of Example 11-7, this shows the configuration commands that were entered between the revision levels specified using the r flag on the command line. Example 11-7. Viewing Differences in Configuration Revisions
Although RCS is useful for a small site, an enterprise network administrator would be better served by commercial configuration management tools such as the CiscoWorks Management Center for Firewalls. This tool not only provides revision control for the configurations but also a workflow tool that provides for separation of duty among administrators. This prevents a single administrator from making changes and pushing the configuration to the firewall without having another administrator review the changes and approve them. Updating the Firewall SoftwareThe final topic to consider when managing firewalls is updating the firewall software. There are two primary reasons to update the software. One reason is to take advantage of new capabilities added to newer software versions. The other reason is the need to fix bugs and vulnerabilities in the software. Like all software, firewall software is complicated and contains many lines of code. The code in the firewall may have been rigorously tested, but there will still be corner cases that the software developers did not consider or just outright overlooked. A corner case is a situation that only occurs outside of normal operations. Typically, corner cases arise when multiple conditions occur simultaneously and at an extreme level. For example, a DHCP starvation attack (an attack where the attacker tries to exhaust a DHCP server's ability to provide clients with leases by generating multiple requests for all the IP addresses in the DHCP server's scope) along with a distributed denial-of-service (DDoS) attack. The combination of these two attacks may cause a resource exhaustion on the firewall or trip some other software bug that could make the firewall unusable. These bugs may result in the firewall resetting itself or may result in the firewall allowing invalid traffic through when it should be blocked. Choosing the Correct VersionThe first step in updating a firewall's software is determining the right version. This means determining which version will run on the firewall platform to be upgraded and which version provides all the capabilities desired and for which the firewall is licensed. On SOHO firewalls such as a Linksys device or the PIX 501/506E, the most recent version is typically the correct version to use. However, recently Cisco released PIX OS 7.0 for the PIX platform. This version works on all PIX platforms except for the PIX 501 and the 506E platforms. Take care when a new software version is released by the manufacturer that the requirements for that version are met before attempting to upgrade the firewall. Otherwise, this could result in the firewall being nonfunctional and requiring a software downgrade to a previous version to restore operation. In the case of Linux NetFilter-based firewalls, the administrator must be careful to ensure that the NetFilter firewall code is compiled into the Linux kernel (either statically or as dynamically loaded modules). In the more recent Linux kernels of the 2.6 series, the NetFilter is automatically included in the kernel configuration as dynamically loaded modules. Reading the Release NotesOne of the first items to do when deciding with which software release to upgrade a firewall (or any device for that matter) is to read the release notes for that version. The release notes typically include a detailed list of supported devices, new features in the release, and software bugs fixed in the release. In addition, some manufacturers include a list of outstanding bugs that have not been addressed in the release at the time of shipment. The release notes represent a one-stop shop for much, if not all, of the necessary information needed to determine whether the software release being considered is appropriate for the firewall to be upgraded. Defects and BugsFirewall software is complex and contains many subsystems and lines of code. Although the vendors make every effort to identify potential bugs or other errors in the software, not all possible cases can be discovered during testing before the software is released to the general public. Therefore, possible bugs and vulnerabilities in the software may not be detected until after the software has been released. VulnerabilitiesA vulnerability is a defect that might result in the potential exploitation of the firewall by an attacker to cause either a denial-of-service (DoS) attack or to gain access to the firewall itself. A vulnerability can also be caused by a misconfiguration of the firewall. An example of a vulnerability in firewall software is the Cisco PIX Telnet/SSH DoS attack described on SecurityFocus (http://www.securityfocus.com/bid/6110). This vulnerability, although not providing access to the PIX itself, causes the PIX Telnet/SSH service to become nonresponsive. Cisco immediately released a fix for this problem in PIX OS 6.2.2.111. A vulnerability due to a misconfiguration of the firewall can range from allowing access to Remote Procedure Call (RPC) ports on systems behind the firewall to not setting an access password on the device itself. These types of vulnerabilities are not mitigated by software upgrades but rather by correcting the configuration of the device. One of the quickest ways to find any ports that may be open due to a firewall misconfiguration is to use a network-scanning tool such as Nmap (available at http://www.insecure.org) or Foundstone's Fscan (available from http://www.foundstone.com) Tracking a DefectSo, a bug or a vulnerability has been discovered in the software version running on your firewall. What do you do now? If the vendor has released a version that resolves the bug or vulnerability, the simplest solution is to download it and apply the patched software. If no fixed software is available, it is important to keep track of the bug and any possible workarounds the vendor has devised. Typically, vendors provide a portal on their websites that include defect information and whether a specific defect has been resolved. For Cisco PIX devices, the Product Security Incident Response Team provides security advisories that can be viewed on the Cisco website at http://www.cisco.com/go/psirt. In addition, for registered users, a database of security-related and non-security-related defects is available. For Linksys devices, this section is part of their technical support website (http://www.linksys.com). Information related to bugs in the Linux kernel is available at the Linux Kernel Archives website (http://www.kernel.org). For Linux kernels 2.6 bugs, there is a specific bug-tracking system, http://bugzilla.kernel.org. For bugs that are NetFilter specific (whether it is the NetFilter code in the kernel or the utilities used to manipulate the NetFilter firewall), there is http://bugzilla.netfilter.org. Regardless of the device, it is important to be aware of bugs and other software issues to be prepared to mitigate any new vulnerabilities that they may introduce into the network. |
EAN: 2147483647
Pages: 147