Hardening Your Network with Accounting
Hardening Your Network with Accounting
Once you have configured authentication and authorization, the last component of AAA to configure is accounting. Accounting is designed to allow you to track what servers a user is accessing, what commands a user is attempting to use (successful or not), as well as the amount of network resources that they are using. This information can then be analyzed and used for network management decision-making, client billing, as well as auditing.
AAA Accounting on IOS-Based Equipment
Enabling AAA accounting is going to be a familiar process at this point, because it is largely the same process that you followed for authentication and authorization. Indeed, authentication and authorization is a prerequisite if you want to perform accounting.
Accounting uses method lists similar to our other AAA processes and supports five different types of accounting:
| Network | Allows you to configure accounting for all PPP, SLIP, or ARAP sessions |
| EXEC | Provides information about the EXEC terminal sessions that a user creates |
| Commands | Allows you to provide accounting information about all commands that a user issues |
| System | Provides accounting for system-level events |
| Resource | Provides start and stop records of all calls that have been authenticated as well as provides records of all calls that fail to authenticate |
We will look at enabling EXEC and command accounting, though all of the accounting methods use the same fundamental commands with a slightly different syntax.
EXEC Accounting Using TACACS+
Enabling EXEC accounting is a straightforward process if you have already configured the rest of AAA properly, as we have done previously in this chapter. If you want to enable EXEC accounting using TACACS+, you can run the following command at the global configuration mode:
local-rtr(config)#aaa accounting exec default start-stop group tacacs+
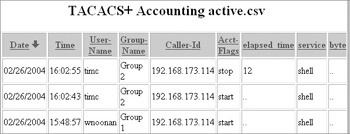
You can view the accounting reports on your Cisco Secure ACS server by clicking Reports And Activity in the navigation bar and clicking TACACS+ Accounting. Next, select the TACACS+ Accounting file that you want to view. The following shows an example of the accounting file, including the EXEC shell being started (when the user connects) and stopped (when the user disconnects).
Commands Accounting Using TACACS+
Commands accounting can be enabled by running the following command at the global configuration mode:
local-rtr(config)#aaa accounting commands 0 default start-stop group tacacs+
Repeat this command for privilege levels 1 “15 by replacing the 0 with the appropriate privilege level number. These commands specify that all commands running at any privilege level be logged for accounting. While most commands are going to run at privilege level 0, 1, or 15, I recommend implementing all privilege levels to ensure that you do not inadvertently miss something. To view the command accounting reports on the Cisco Secure ACS server, click Reports And Activity in the navigation bar and click TACACS+ Administration (not TACACS+ Accounting). Next, click the report that you want to view.
| Note | AAA accounting using RADIUS leaves a lot to be desired. As a result, I recommend that you use TACACS+ for accounting if at all possible. |
AAA Accounting on PIX Firewalls
You can configure accounting of your user connections through the PIX by running the following command after configuring the previous AAA configuration prerequisites (that is, authentication):
firewall(config)# aaa accounting include any inside 0 0 0 0 TACACS+
This will cause the PIX to log any traffic passing through the PIX to the TACACS+ accounting log. As previously mentioned, however, AAA authorization and accounting of user connections through the PIX, while useful, is not anywhere near as robust and reliable as content filtering. I recommend that you consider implementing a content filter before you implement authorization and accounting.
| |
Command accounting is not supported on the PIX. The PIX by default logs everything that occurs in a syslog format. You can get the same functionality by reviewing the syslogs that you get by enabling command accounting on your IOS-based devices.
| |
EAN: N/A
Pages: 125