Bifurcated Routing-Blind Carbon Copy
Bifurcated Routing
Routing that may split one traffic flow among multiple routes.
Big Brother
"Big Brother is watching you". A phrase coined by George Orwell in his classic novel '1984', a fictional tale of a totalitarian future in which "Thought police" monitor one's every move via telescreens which broadcast propaganda and have a built in camera and microphone. The phrase is now used to describe the huge amounts of personal information collected by government and commercial organizations.
Big Hat, No Cattle
Texas expression used to dismiss a cowboy wanabee. In Lone Star IT circles, it describes a technician with a certificate or degree in computer science, but little or no field experience.
Big LEO
LEO stands for Low-Earth-Orbit. Big LEO is a low-earth- orbit satellite system that will offer voice and data services.
Bigamy
The only crime in which two rites make a wrong.
Big-endian
An architectural format for storage of binary data, big-endian is most significant in multi-byte data types. Big-endian considers the most significant bytes to be the leftmost (i.e., those with a lower address) in a multi-byte data word. Some architectures use big-endian for ordering bits within bytes. Some architectures use big-endian for ordering bits, and little-endian for ordering bytes. Little-endian considers the right-most bytes (or bits) to be most significant. IBM and many other mainframe computers use big-endian architecture, while most PCs use little-endian. The PowerPC is bi-endian, as it can understand both approaches. Conversion of data between the two data architectures is known as the NUXI problem. If the word "UNIX" were stored in two two-byte words, a big-endian system would store it as "UNIX," while a little-endian system would store it as "NUXI." The terms "big-endian" and "little-endian" are derived from "Gulliver's Travels," wherein the Lilliputians were divided politically over the issue of whether soft-boiled eggs should be opened on the big side or the little side.
Bikini Transmitter
The Bikini Transmitter is a body wire developed for a special surveillance project. Law Enforcement professionals needed to secretly record a conversation between a suspect and a female agent. The suspect insisted the meeting take place at a topless beach . An audio transmitter was sewn into a string bikini with the antenna threaded through the string. The largest component, the battery, was carried, uh...internally. It is not known whether the transmitter was waterproof .
Bilateral Synchronization
A synchronization control system between exchanges A and B in which the clock at exchange A controls the received data at exchange B and the clock at exchange B controls the received data at exchange A. Normally implemented by deriving the receive timing from the incoming bit stream.
Bildschirmtext
German word for interactive videotex. The German Bundespost likes this service. But the German version isn't as successful as the French because the French gave away the videotex terminals. And the Germans didn't. Also, the French really encourage videotex entrepreneurs by giving a real piece of the action ” 60% of the collected revenues .
Bill
An itemized list or statement of charges. If you can't bill for a product or service, you're engaged in a hobby rather than a business.
Bill and Keep
Imagine a phone call from New York to Los Angeles. It may start with the customer of a new phone company, then proceed to a local phone company (let's say New York Telephone, now called Bell Atlantic). Then it may proceed to a long distance company before ending in Los Angeles and going through another one or two local phone companies before reaching the person dialed . Under the existing rules, all the companies carrying these phone calls have to be paid in some way for their transmission and switching services. There are programs in place such that the company doing the billing and collecting the money pays over some of those monies to the other phone companies in the chain. One such program is called "reciprocal compensation." The opposite of reciprocal compensation is called "Bill and Keep." Under this program, the company billing the call gets to keep all the money. The others in the chain (or most of the others in the chain) get nothing. The concept of "bill and keep" has its roots in the international postal service where "bill and keep" has been in place for many years .
Bill Gates
Years ago, Bill Gates formed a company to sell a computerized traffic counting system to cities, which made $20,000 its first year. Business dropped sharply when customers learned Gates was only 14 years old.
Bill Of Materials
A list of specific types and amounts of direct materials expected to be used to produce a given job or quantity of output.
Bill To Room
A billing option associated with Operator Assisted calls that allows the calling party to bill a call to their hotel room. With this option, the carrier is required to notify the hotel, upon completion of the call, of the time and charges.
Billboard
Electronic sales pitches that come up on your computer screen at any time.
Billboard Antenna
A broadside antenna array with flat reflectors.
Billed Number Screening
You (at home or your business) establish who can and cannot charge a call to your phone by making an agreement with your local telephone company to screen your calls. (e.g. refusal of all collect call requests .)
Billed Telephone Number
BTN. The primary telephone number used for billing regardless of the number of telephone lines associated with that number. Apparently, the term "billing telephone number" is more accurate than billed telephone number. For a longer explanation, see Billing Telephone Number.
Billibit
Someone's absolutely awful term for one billion bits. Also (and better) called a gigabit.
Billing Account Number
BAN. Used by telephone companies to designate a customer or customer location that will be billed. A single customer may have multiple billing accounts. See Billing Telephone Number.
Billing Company
The company that will bill the customer for collect or third number billed calls. It may or may not be the same as the Earned Company.
Billing Increment
The increments of time in which the phone company (long distance or local) bills. Some services are measured and billed in one minute increments. Others are measured and billed in six or ten second increments. The billing increment is a major competitive weapon between long distance companies. Short billing increments become important to you, as a user , when your average calls are very short ” for example, if you're making a lot of very short data calls (say for credit card authorizations). Being billed for a lot of six second calls is a lot cheaper than being billed for a lot of one minute calls.
Billing Media Converter
A Billing Media Converter, as made by the Cook division of Northern Telecom, provides a means of transporting Automatic Message Accounting (AMA) data from DMS-10 central offices to regional accounting offices with the physical transfer of magnetic tapes. The BMC is polled.
Billing Telephone Number
BTN. The primary telephone number used for billing regardless of the number of telephone lines associated with that number. Multiple WTNs (Working Telephone Numbers), also known as ETNs (Earning Telephone Numbers ) can be associated with a single BTN. A Billing Telephone Number is the number to which calls to given location are billed. It is the seven-digit number with the area code followed by an alphanumeric code assigned by the local telephone company (e.g. NPA-NXX-XXXX).
Billing Validation Service
See BVA and BVS.
Billion
In North America, a billion is a thousand million. In many countries overseas, a billion is a million million.
Binaries
Binary, machine readable forms of programs which have been compiled or assembled . As opposed to source language forms of programs.
Binary
Where only two values or states are possible for a particular condition, such as "ON" or "OFF" or "One" or "Zero." Binary is the way digital computers function because they can only represent things as "ON" or "OFF." This binary system contrasts with the "normal" way we write numbers ” i.e. decimal. In decimal, every time you push the number one position to the left, it means you increase it by ten. For example, 100 is ten times the number 10. Computers don't work this way. They work with binary notation. Every time you push the number one position to the right it means you double it. In binary, only two digits are used ” the "0" (zero) and the "1" (the one). If you write the number 10101 in binary, and you want to figure it in decimal as we know it, here's how you do it. 1 is one thing; Zero x 2 = zero; 1 times 2 x 2 = 4; 0 x 2 x 2 x 2 = 0; 1 x 2 x 2 x 2 x 2 = 16. Therefore the total 10101 in binary = 1 + 0 + 4 + 0 + 16 = 21 in decimal.
Binary notation differs slightly from notation used in ASCII or EBCDIC. In ASCII and EBCDIC, the binary values are used for coding of individual characters or keys or symbols on keyboards or in computers. So each string of seven (as in ASCII) or eight (as in EBCDIC) ones and zeros is a unique value ” but not a mathematical one.
ASCII uses a seven bit coding scheme. Thus, the maximum number of different things you can code using seven bits is 128, i.e. 2 x 2 x 2 x 2 x 2 x 2 x 2 = 128. The maximum number represented by a byte (8 bits) in the IBM EBCDIC coding system is 256. i.e. 2 x 2 x 2 x 2 x 2 x 2 x 2 x 2 = 256. See Binary Coded Decimal, Binary File and Binary Transfer.
Binary Code
A code in which every element has only one of two possible values, which may be the presence or absence of a pulse, a one or a zero, or high or a low condition for a voltage or current.
Binary Coded Decimal
BCD. A system of binary numbering that uses a 4-bit code to represent each decimal digit from 0 to 9 and multiple 4-bit patterns for higher numbers. The decimal numbers 0 to 9 are represented by the four-bit binary numbers from 0000 to 1001.
Binary Digit
A number in the binary system of notation.
Binary File
A file containing information that is in machine-readable form. It is an application. Or it can only be read by an application. See Binary Transfer.
Binary File Transfer
BFT. The transmission of binary files, software, documents, images, video and electronic data exchange information between communicating devices, including PCs, fax devices, etc. When binary files are transferred via telecommunications, they must not be changed in any way during the transfer; otherwise they will be destroyed . Many electronic mail services, such as CompuServe or MCI Mail, have ways of "attaching" binary files to electronic mail, such that the binary file will not be affected or changed in any way during transmission. But that only works between MCI users or between CompuServe users. The Internet uses a different system. It's called MIME, which stands for Multipurpose Internet Mail Extension. MIME uses software to encode the binary file into as ASCII file. It transmits the ASCII file. At the other end, that file is decoded into its original binary format. MIME uses many software techniques for doing this. But all have the same effect of not changing the original binary file. See MIME.
Binary Logarithmic Access Method
BLAM. A proposed alternative to the IEEE 802.3 backoff algorithm.
Binary Notation
Any notation that uses two different characters, usually the binary digits O and 1.
Binary Number System
A number system that uses two characters (O and 1) with two as its base, just as the decimal number system uses ten characters (O through 9) with ten as its base.
Binary Phase Shift Keying
See BPSK for an explanation.
Binary Runtime Environment for Wireless
See BREW.
Binary Symmetric Channel
A channel designed so that the probability of changing binary bits in one direction is the same as the probability of changing them back to the correct state.
Binary Synchronous Communications
BISYNC or BSC.
-
In data transmission the synchronization of the transmitted characters by timing signals. The timing elements at the sending and receiving terminal define where one character ends and another begins. There are no start or stop elements in this form of transmission. For a more detailed explanation, see BSC.
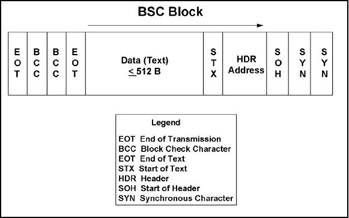
-
Also a uniform discipline or protocol for synchronized transmission of binary coded data using a set of control characters and control character sequences.
Binary To Decimal Conversion
Conversion from base 2 to base 10. See Binary.
Binary Transfer
See Binary File Transfer and MIME.
BIND
Berkeley Internet Name Daemon. BIND is the software that allows us to type site names like www.yahoo.com instead of a string of numbers. BIND is the implementation of a DNS server originally developed and distributed by the University of California at Berkeley. Many Internet Hosts run BIND, and it is the ancestor of many commercial BIND implementations .
Bind
A request to activate a session between two logical units (LUs). See BIND.
Binder
A way to separate groups of 25 pairs in a twisted-pair cable with more than 25. Color plastic ribbon binds separate each group of 25. The first group (1-25) is white/blue, the second (26-50) is white/orange, the third (51-75) is white/green, the fourth (76- 100) is white/brown, etc. Binders are helically applied colored thread, yarn, or plastic ribbon. They're used to confine, separate and identify groups of fibers or wires in a cable. Binders are usually used for holding assembled cable components in place.
Binder Group
A typical phone line ” business or residence, analog or digital ” is a pair of wires. When the phone company installs cabling along the street ” up in the air or underground ” it installs a cable containing many pairs of wires. The pairs are color coded so you can find which is which. Often there are so many of them you have to do something better ” like take a bunch of cable pairs and wind something (or bind something) around them. That's called a binder group. The binder is a spirally wound colored thread or plastic ribbon used to separate and identify cable pairs by means of color coding. The groups are composed of insulated twisted copper pairs that are also twisted within each binder. Typically, they are wrapped in 25-pair bundles. Normal telephone color-coding provides for only 25 pairs of wire, so binder groups allow multiple pairs of the same color wire to be in one cable. A 50-pair cable has blue and orange binder groups; a 75-pair cable has blue, orange, and green groups. Since several wire pairs have the same color markings , installers must be careful when stripping cable insulation so they do not destroy the binder threads. For example. pairs 1-25 might he in one binder group and pairs 26-50 in another. In xDSL, one often hears discussions of signal interference between adjacent pairs within a binder group. The best of all worlds is to keep a data pair separated from another data pair by assigning it to an adjacent bindergroup. If the data pairs are too close to each other they create what telephone companies call "disturbers" (i.e., crosstalk).
Bindery
A Novell NetWare database containing definitions for entities such as users, groups, and workgroups. The bindery contains three components: objects, properties, and property data sets. Objects represent any physical or logical entity, including users, user groups, file servers, print servers, or any other entity given a name. Properties are the characteristics of each bindery object, including passwords, account restrictions, account balances , internetwork addresses, list of authorized clients , workgroups, and group members . Property data sets are values assigned to entities' bindery properties.
Binding
A Windows 95 definition. Binding is a process that establishes the communication channel between a protocol driver and a network adapter driver.
Binding Post
-
A screw with a small nut. You take your wires and join them together on a binding post by wrapping them together around the screw and then tightening the nut on them. You'll find binding posts on huge wall-mounted things called terminal boxes. We have several in the basement of the building in Manhattan, New York, in which I live. Binding posts are numbered on the terminal box and those numbers are entered into the phone company's cable management system. That way, when the technician comes to check out a trouble report, he can quickly find the offending pairs. These days, other more modern termination devices (such as Krone Boxes, 110-connecting blocks, and even 66- blocks) are replacing binding posts. Our building's binding posts are probably 60 years old. See also House Box.
-
A post witches were attached to just before they were burned at the stake. Rude switchboard operators and ACDs with long queues should also suffer this fate.
BinHex
When sending files which aren't plain ASCII across a network ” dial-up, leased line or the Internet ” you basically have two options. First, you can attach them as a binary file (i.e. non-ASCII file). Or second, you can encode them into ASCII characters and send the file as part of your message. The first method is preferable. But you can typically only send binary files from one account to another on the same network, or between two networks that have agreed between themselves to a method of transferring files. But that's a rarity. And it certainly doesn't work in and around the Internet. Thus something called MIME was created. MIME stands for Multipurpose Internet Mail Extensions. It is the name for encoding binary files into ASCII characters for transfer across the Internet and online services. Under MIME, there are a number of methods of encoding binary files, one of which is called BinHex, which is a popular encoding algorithm that uses Run-Length Encoding (RLE). To send a binary file, you encode it using BinHex encoding software. You then include the ASCII encoded file in your message. The recipient of your message then decodes the ASCII using BinHex decoding software, which may or may not be built into his electronic mail or browser package.
Binomial Distribution
The binomial is a two-parameter distribution, the parameters being n, the number of trials, and p, the probability of a particular outcome of a single trial.
Bio-Surveillance
Monitoring hospital admissions to detect increases in similar symptoms that could indicate a biological attack.
Biogorrhea
Pointless or excessive filler in a weblog. As one Net diarist wrote; "I was accused recently of biogorrhea. Well, yes, that's fair. But see, here's the thing. I'm leaving town for a month..." Courtesy , Gareth Branwyn, Wired Magazine.
Biohacker
A hobbyist who tinkers with DNA and other aspects of genetics . Also: bio- hacker. Some speculate a "biohacker" ” the equivalent of a computer hacker seeking thrills rather than impact ” could be behind the anthrax letters . "Hacker" is usually considered a bad word.
Bioinformatics
Bioinformatics is the process of using computer systems for the purposes of acquisition, storage and analysis of biological data. Computer databases and algorithms are used to speed up biological research and to characterize the molecular components of living things. Bioinformatics is notably being used in the Human Genome Project, the effort to identify the 80,000 genes in human DNA. Bioinformatics includes a wide spectrum of technologies including computer architectures, knowledge management, networking and collaboration tools as well as traditional life-science equipment needed to handle biological samples.
Biometrics
Biometrics is the study of unique and measurable physical (or biological) characteristics such as fingerprints , retinal pattern, or handwriting, Biometric authentication devices capture, encrypt and use these unique and measurable characteristics as the basis for confirming identity and determining whether to grant or deny access to physical or logical assets. When used for authentication, personal biometrics are used much like a door key, however that key cannot be duplicated or lost. The basic principles of biometric verification have been understood and practiced for thousands of years. References occur as early as ancient Egypt, where individuals were identified via unique "biometrics" such as scars or a combination of measured features such as complexion, eye color, height and so on. Biometrics as we know it today really began in the late nineteenth century when criminology researchers attempted to tie physical features and characteristics with criminal tendencies. The results were not conclusive but the idea of measuring individual physical characteristics became accepted, leading the way for fingerprinting to become the international methodology among police forces for identity verification. Today it is taken for granted that fingerprints (and foot and handprints) accurately identify not just criminals, but newborns, minors (as a means of thwarting abduction), military and police personnel, and a host of others. Once technology simplified the collection, codification and encryption of biometric data, the stage has become set for biometrics to become the security standard of the electronic world, replacing passwords, bits of paper, etc. See also Biometric Access Control.
Biometric Access Control
Any means of controlling access through human measurements, such as fingerprinting, handwriting analysis, retinal scanning, hand geometry and voiceprinting. See Biometrics.
Biometric Device
A device used in authenticating access to a system. A biometric device authenticates a user by measuring some hard-to- forge physical characteristic, such as a fingerprint or retinal scan. You see a lot of biometric devices in Hollywood thrillers, including Mission Impossible, a movie which was released in the summer of 1996.
Bionic code
A problem-solving routine for human behavior as it is exercised in the realm of networks and cyberspace . The first bionic codes were developed by Ebon Fisher based on a series of his theatrical experiments involving communication systems amongst audience members. Fisher's bionic codes have been formalized as a series of diagrams and statements which "float" in the infosphere in a variety of media.
Bioinformatics
Bioinformatics applies informatics to biological research. Informatics is the use of advanced computing techniques to manage and analyze data. It has become indispensable because of the large volumes of complex data pouring out of genomics, proteomics, drug screening and medicinal chemistry research. Bioinformatics is also the integration and mining (detailed searching) of the ever-expanding databases in all these areas. In short, bioinformatics concerns itself with using computer databases to help unravel the human genetic code and develop new drugs.
BIOS
Basic Input/Output System of desktop computers. The BIOS contains the buffers for sending information from a program to the actual hardware device the information should go to.
BIOS Enumerator
A Windows 95 term. Bios enumerator is responsible, in a Plug and Play system, for identifying all hardware devices on the motherboard of the computer. The BIOS supports an API that allows all Plug and Play computers to be queried in a common manner.
Biosensors
Devices such as fingerprint readers and signature recognition systems.
BIP
Billing Interconnection Percentage. A calculation of who owns how much of a route when there are multiple providers between two points. Used to allocate revenue in MPB arrangements.
BIP-8
Bit Interleaved Parity 8. A method of error monitoring used in SONET optical fiber transmission systems. A SONET frame of data comprises a large number of bits organized into bytes, or 8-bit values. The bytes, of course, are interleaved into a byte stream. The BIP-8 method looks across all matching bit positions for those distinct bytes in a frame, and calculates parity, which should be even, rather than odd. If an odd parity is calculated at the receiving end, a bit error is indicated. The number of such errors in frames over a period of time constitutes the Bit Error Rate (BER). The specific period of time involved is known as a "sliding time window," as it varies according to the maximum detection time, which is sensitive to the transmission rate, or level of the Optical Carrier (e.g., OC-1, OC- 3, OC-24, OC-48, OC-192). The higher the OC-N level, the higher the rate of transmission, and the shorter the sliding time window. In other words, the faster the rate of transmission, the more quickly the error detection process must take place in order to establish the BER and to correct the problem.
BIP-N
Bit Interleaved Parity N. A method of error monitoring. With even parity, an N bit code is generated by the transmitting equipment over a specified portion of the signal in such a manner that the first bit of the code provides even parity over the first bit of all N- bit sequences within the specified portion, etc. Even parity is generated by setting the BIPN bits so that there are an even number of 1s in each of all N-bit sequences including the BIP-N. See BIP-8 for a concrete example.
Bipolar
The predominant signaling method used for digital transmission services, such as DDS and T-1. The signal carrying the binary value alternates between positive and negative. Zero and one values are represented by the signal amplitude at either polarity, while no-value "spaces" are at zero amplitude.
Bipolar with 8 Zero Substitution
See B8ZS.
Bipolar Coding
The T carrier line coding system that inverts the polarity of alternate "one" bits.
Bipolar Signal
A signal having two polarities, both of which are not zero. It must have a two-state or three-state binary coding scheme. It is usually symmetrical with respect to zero amplitude.
Bipolar Violation
The presence of two consecutive "one" bits of the same polarity on the T carrier line. See also Bipolar Coding.
Bird
A satellite.
Bird Dog Device
An electronic tracking device used by law enforcement to track the physical location of a subject.
Birdie
A birdie is a lightweight device that you blow through underground cement pipes through which you want to pull cable. Here's how it typically works: First, you use a bore to make an underground hole. Then you fill that hole with hollow concrete cement pipes joined together to form one long underground conduit (i.e. tunnel). Then you go to one end of the tunnel and use a air compressed device to blow a very lightweight "birdie" attached to a lightweight string through the tunnel. Someone at the other end catches the birdie and pulls gently on the string. Attached to the end of the string is strong mule tape. He keeps pulling on it. Attached to the end of the mule tape is the telecommunications cable ” fiber or wire ” that you really want to instal in the underground conduit. The whole point of this elaborate procedure is that it's far better for the cable to lay it after the pipes are laid than it is during the installation process when the cable could be damaged.
Birefringent
A fiber optic term. Having a refractive index that differs for light of different polarizations.
Birthdays
February 11, 1847 Thomas Alva Edison born
February 16, 1982 Michael Allen Newton born
February 20, 1980 Claire Elizabeth Newton born
February 23, 1965 Michael Dell (Dell Computer) born
March 3, 1847 Alexander Graham Bell born
March 11, 1933 Ben Rosen (Compaq, SRX, etc.) born
March 15, 1949 Gerry Friesen born
April 6, 1939 John Sculley born
April 27, 1791 Samuel Morse born
May 11, 1948 International Communications Association born
June 10, 1942 Harry Newton born in Sydney, Australia
June 13, 1961 TeleCommunications Association born
June 19, 1924 Ray Noorda (Novell) born
June 27, 1968 Carterfone decision handed down by FCC
July 4, 1943 Susan Newton born in Perth, Australia
August 31, 1962 The Communications Satellite Act is born
September 2, 1936 Andy Grove (Intel)
September 12, 1948 Communications Managers Association
October 28, 1955 Bill Gates (Microsoft)
November 10, 1946 Ray Horak (Context Corporation)
November 13, 1954 Scott McNealy (Sun Microsystems)
December 10, 1928 William G. McGowan, founder of MCI
Bis
-
The French term for "second" or "encore." It is used by the ITU/ITU to designate the second in a family of related standards. "Ter" designates the third in a family. See V Series.
-
Border Intermediate System
-
Bus Interface Card.
Biscuit
A biscuit is a regular phone jack that is frequently located in a residence.
BISDN
Also spelled B-ISDN. Broadband ISDN. This is a vaguely defined term. It basically means any circuit capable of transmitting more than one Basic Rate ISDN, i.e. 144 Kbps. One definition I read recently suggested that BISDN is "a set of public network services that are delivered over ATM, including data, voice, and video. BISDN will provide services such as high-definition television (HDTV), multi-lingual TV, voice and image storage and retrieval, video conferencing. high-speed LANs, and multimedia." See B-ISDN for a longer explanation. See also ISDN.
Bistable Trigger Circuit
A trigger circuit that has two stable states.
BISUP
Broadband ISDN User's Part: A SS7 protocol which defines the signaling messages to control connections and services. See Signaling System 7.
BISYNC
(pronounced bye-sink). BISYNChronous Transmission. A half-duplex, character- oriented, synchronous data communications transmission method originated by IBM in 1964. See Synchronous.
Bisynchronous Transmission
Also called BISYNC. A data character-oriented communications protocol developed by IBM for synchronous transmission of binary-coded data between two devices. BISYNC uses a specific set of control characters to synchronize the transmission of that binary coded data. See also Binary Synchronous Communication.
Bit
Bit is a contraction of the term BInary digiT. It is the smallest unit of information (data) a computer can process, a "1" or "0." Similarly, a bit is the basic unit in digital communications. Across a transmission facility, a bit can be represented in a variety of ways, including positive (+) and negative (-) voltage, relatively high (e.g., +3.0) volts and relatively low (e.g., +1.5) volts , positive (+) and null (0) voltage, presence and absence of light, and relatively high-amplitude and relatively low-amplitude radio signal. The term was coined by John W. Tukey, a professor at Princeton and a researcher at Bell Telephone Laboratories. Tukey also coined the term "software." See also Software and Tukey.
Bit Bucket
Slang for throwing out bits ” into a wastepaper bucket.
Bit Buffer
A section of memory capable of temporarily storing a single bit (BInary digiT) of information. Used to make data transmission accurate or consistent.
Bit Check
A bit added to a digital signal and used for error checking, i.e. a parity bit. See also Parity.
Bit Count Integrity
A means of determining the integrity of a data packet. The counting of bits is very important. If the receiver can't confirm that it received all of the bits, it can't confirm that the integrity of the received data packet is maintained . Bit count integrity is especially important in the domain of compressed, encrypted data networking.
Bit Depth
The number of bits used to represent the color of each pixel in a graphic file or the sound in an audio file. The higher the number, the more information included in the file and the higher the quality of the data. Common graphic bit depths are 4-bit, 8-bit, 16-bit, 24-bit and 32-bit. Common sound bit depths are 8-bit and 16-bit.
Bit Duration
See Bit Time.
Bit Error
A mistake in transmitting a bit. Error rate statistics play a key role in measuring the performance of a network. As errors increase, user payload (especially data) must be re-transmitted. The end effect is creation of more (non-revenue) traffic in the network. See Bit Error Rate.
Bit Error Rate
BER. The percentage of received bits in error compared to the total number of bits received. Usually expressed as a number to the power of 10. For example, 10 to the fifth power means that one in every 100,000 bits transmitted will be wrong. In transmitting data a high error rate on the transmission medium (i.e. some noise), doesn't mean there'll be lots of problems with the final transmission. It just means there'll have to be lots of re-transmissions ” "until one gets it right." These re-transmissions reduce the amount of data transmitted in a unit of time and therefore, increase the time needed to send that information. If the BER gets too high, it might be worth while to go to a slower transmission rate. Otherwise, you would spend more time retransmitting bad packets than getting good ones through. The theory is that the faster the speed of data transmission the more likelihood of error. This is not always so. But if you are getting lots of errors, the first ” and easiest ” step is to drop the transmission speed.
Bit Flipper
A person who flips bits for a living. In other words, an industrial strength member of the digiterati, which I guess would be a digiteratus. These people are way kewl (that's a NetHead term for cool, or k00l) when it comes to really technical data protocol stuff. See also Digiterati, Nethead and Gearhead.
Bit Interleaving
A form of TDM for synchronous protocols, including HDLC, SDLC, BiSync and X.25. Bit interleaving retains the sequence and number of bits, so that correct synchronization is achieved between both ends. See Bit Interleaving/Multiplexing.
Bit Interleaving/Multiplexing
In multiplexing, individual bits from different lower speed channel sources are combined one bit at a time/one channel at a time into one continuous higher speed bit stream. Compare with byte interleaving/ multiplexing.
Bit Oriented
Used to describe communications protocols in which control information may be coded in fields as small as a single bit.
Bit Oriented Protocol
BOP. A data link control protocol that uses specific bit patterns to transfer controlling information. Examples are IBM's Synchronous Data Link Control (SDLC) and the ITU-T High-Level Data Link Control (HDLC). Bit-oriented protocols are normally used for synchronous transmission only. Bit-oriented protocols are code transparent (meaning they work regardless of the character encoding method used), since no encoded characters are used in the control sequence.
Bit Oriented Transmission
An efficient transmission protocol that encodes communications control information in fields of bits rather than characters or bytes.
Bit Parity
A binary bit appended to an array of bits to make the sum of all the bits always odd or always even. See Parity.
Bit Pattern
A group of bits arranged in specified ways to represent numbers, letters or symbols, forming a unique binary number for each character. For example, the 7-bit ASCII code produces 128 different characters, i.e. 2 x 2 x 2 x 2 x 2 x 2 x 2 = 128.
Bit Pump
A device which pumps out bits at a high rate of speed. Slang for high-speed carrier electronics such as ADSL terminating units, which can achieve speeds of multiple Mbps over standard twisted-pair local loops . "Bit pumps" possess no particular intelligence (e.g., protocol conversion, or error detection and correction); they just pump bits.
Bit Rate
The number of bits of data transmitted over a phone line per second. You can usually figure how many characters per second you will be transmitting ” in asynchronous communications ” if you divide the bit rate by ten. For example, if you are transmitting at 1200 bits per second, you will be transmitting 120 characters per second. In real life, it's never this simple, however. The total bits transmitted will depend on re-trans- missions, which depends on the noise of the line, etc. See BAUD RATE.
Bit Robbing
A technique to signal in-band in digital facilities, which typically use out of band signaling, e.g. Signaling System 7. In bit robbing, we steal bits from the speech path a few line-signal bits. The remaining bits are adequate to recreate the original electrical analog signal (and ultimately, the original sound). Bit robbing typically uses the least significant bit per channel in every sixth frame for signaling. See Bit Stuffing and Robbed Bit Signaling.
Bit Specifications
Number of colors or levels of gray that can be displayed at one time. Controlled by the amount of memory in the computer's graphics controller card. An 8-bit controller can display 256 colors or levels of gray; a 16-bit controller, 64,000 colors: a 24-bit controller, 16.8 million colors.
Bit Seven
BIT7. A TR008 DS1 line code that performs zero code suppression by placing a one in bit 7 of an all-zeros byte.
Bit Stream
A continuous flow of binary digits (bits), through some form of communications medium_e.g., fiber optics, air (wireless) or twisted-pair, with no break or separators between the characters.
Bit Stuffing
-
A process in some synchronous data communications protocols to ensure that the transmission is properly clocked. In HDLC (High-level Data Link Control), for example, each frame of data is both preceded and succeeded by a "flag" of six consecutive "one" bits. The flags signal the beginning and ending of the data frame, and are used by the receiving devices to synchronize on the rate of transmission. In order to avoid confusion, therefore, any set of six consecutive "one" data bits must be broken by a stuffed "zero" bit. This stuffed bit is added by the sender and stripped by the receiver. The idea of inserting the "one" bit is to avoid the data's mimicking the flag, and confusing the receiver. Stuff bits also are used in SONET (Synchronous Optical NETwork) prior to the multiplexing of DS-1s and DS-2s in order to resolve clocking differences prior to the construction of a SONET frame. See Zero Stuffing.
-
A process used in some packet data network protocols in order to fill a packet to the prescribed, fixed size. For example, X.25 requires that all packets in a specific network be of the same size (e.g., 128B, 256B, or 512B, where B = Byte of eight bits). If the amount of data to be transmitted in a packet is not sufficient, stuff bits are added to fill up the packet. Again, the stuff bits are added by the sender, which signals their presence, and are stripped away by the receiver.
Bit Synchronous
A SONET term describing the manner in which information streams are mapped into the SONET frame format for unchannelized VT (Virtual Tributary) transport. For instance, multiple VT1.5s can be mapped into a SONET frame, with each VT1.5 carrying a single T-1 signal within the STS-1 SPE (Synchronous Payload Envelope). In the LOH (Line OverHead) of the SONET are included VT pointers which identify the established portions of the SPE in which the beginning byte of each VT1.5 is located. As each VT1.5 works its way through the SONET network, its actual position may change within the various SPEs, thereby requiring that the pointer be reset; this process is very complex and expensive, and results in a small level of delay. Regardless of issues of complexity, cost and ( slight ) processing delay, it is essential that the timing of the various T-carrier and SONET data be maintained in order that the data arrive at an identifiable and consistent point in time; otherwise, it would be unrecognizable. As is true with many things in life, timing can be everything. Compare and contrast with Byte Synchronous. See also SONET and VT.
Bit Time
Also known as "bit duration," the bit time is the length of time associated with a bit placed on a transmission medium. In somewhat oversimplified terms, a transmission system that runs at a signaling speed of 1 Gbps supports bits that have an individual duration of 1 billionth of a second.
Bit Transfer Rate
The number of bits transferred per unit of time. Usually expressed in Bits Per Second (BPS).
Bit Twiddler
A technical person. Twiddle, according to the Random House Dictionary, means "to play or trifle idly with something; fiddle." The expression bit twiddler is used thus, "I'm not a bit twiddler. You'll have to ask Joe in Engineering if you want the answer to that."
BITBLT
BIT BLock Transfer. Microsoft Windows relies intensively on a type of operation called bit block transfer (BITBLT) to redraw rectangular areas of the image on the computer's screen. Generally , BITBLT operations are accomplished by software routines in the video driver, a cheap, but slow method that uses many of your CPU's clock cycles. If you add a separate video controller with a special processor to handle BITBLT, you will be able to offload video tasks from your main CPU and make your computer run faster.
BITE
Built-in test equipment. Features designed into a piece of equipment that allow online diagnosis and testing of failures and operating status.
Bitmap
Representation of characters or graphics by individual pixels arranged in row (horizontal) and column (vertical) order. Each pixel can be represented by one bit (simple black and white) or up to 32 bits (high-definition color). Bitmapped images can be displayed on screens or printed. The method of storing information that maps an image pixel, bit by bit. There are many bitmapped file formats, .bmp, .pcx, .pict, .pict-2, tiff/.tif,.gif (89a), and so on. Most image files are bit mapped. This type of file gives you stair stepped edges, the 'jaggies'. When examined closely you can see the line of pixels that creates edges. Bitmap images are used by all computers. The desktop for all Windows machines uses .bmp files, while the Macintosh uses pict files. Most Internet publishing and e-mail use JPEG or .JPG and .GIF (89a) formats." See Bit Specifications.
Bitmapped Graphics
Images which are created with matrices of pixels, or dots. Also called raster graphics. See Bitmap.
BITNET
Because It's Time NETwork. An academic computer network based originally on IBM mainframes connected with leased 9600 bps lines. BITNET has recently merged with CSNET, The Computer+Science Network (another academic computer network) to form CREN: The Corporation for Research and Educational Networking. The network connects more than 200 institutions and has more than 900 computational nodes.
Bitnik
A person who uses a coin-operated computer terminal installed in a coffee house to log into cyberspace.
Bitronix
Hewlett Packard's term for its bidirectional parallel port communications "standard." It introduced this standard with its 600 dps LaserJet 4 plain paper printer in the fall of 1992. It is hoping other manufacturers will adopt the standard. The big plus of the standard is that it allows a printer to tell a connected computer that it (the printer) has run out of paper, or the paper has jammed , etc. Having that communication back and forth will allow the user to clear the problem and get the printer and up and running faster and stop the computer from locking up.
BITS
Building Integrated Timing Supply. A single building master timing supply. BITS generally supplies DS1 and DS0 level timing throughout an office. The BITS concept minimizes the number of synchronization links entering an office, since only the BITS will receive timing from outside the office. In North America, BITS are thus the clocks that provide and distribute timing to a wireline network's lower levels. Known in the rest of the world as a SSU (Synchronization Supply Unit).
Bits Clock
The bits clock provides a pulse that synchronizes the entire network. The pulse is a 1-0-1-0-1-0-1-0 stream. Used extensively in SONET network.
Bits Per Second
The number of bits passing a specific point per second. See Bps.
A KILObit per second is one thousand bits per second.
A MEGAbit per second is one million bits per second (thousands of kilos).
A GIGAbit per second is one billion bits per second (thousands of millions).
A TERAbit per second is one trillion bits per second (thousands of billions).
A PETAbit per second is equal to 10 to the 15th or 1,000 terabits per second.
Bits Versus Bytes
Bits are the smallest units of information in telecom and data processing; the term bit is derived from binary digit. One byte is typically equivalent to 8 bits. Given that a bit can carry two pieces of information (represented by either 0 or 1), two bits together can represent four (or 22) pieces of information: 00, 01, 10, and II. Similarly, eight bits or one byte mean that 256 (28) pieces of information can be represented, stored, and transmitted. These pieces of information can be color codes, sound levels, or numbers and letters. See also asynchronous and synchronous. See also the Introduction to this book at the very beginning.
Bitslag
All the useless rubble on the Net one has to plow through to get to the rich information core .
Bitspit
To transmit. "Did you bitspit the file to Harry?"
Bix
A Nortel Networks' trade name for an in-building termination and cross-connect system for unshielded twisted pair cables, also called a terminal block. See also Terminal Block.
BL
Business Line.
Black Ball
See White List.
Black Body
A totally absorbing body that does not reflect radiation (i.e. light). In thermal equilibrium, a black body absorbs and radiates at the same rate; the radiation will just equal absorption when thermal equilibrium is maintained.
Black Box
-
An electronic device that you don't want to take the time to understand. As in, "We'll put the data through a black box that will put it into X.25 format." The term has recently come also to mean PBX switches. While "Black Box" is a generic term, The Black Box Corporation of Pittsburgh, PA, has had the audacity (and brilliance) to register the term as a trademark. The Phone Phreak community has used the term black box to describe a device that's put on phone lines in electromechanical central office areas (they don't work under ESS offices). To the phone phreak community, a black box is made up of a resistor, a capacitor and a toggle switch that would "fool" the central office into thinking the phone had not been picked up when receiving a long distance call. Since the call was not " answered ," the call could not be billed. Clever, eh? (Illegal, too.) See Blue Box, Red Box and White Box.
-
Cockpit voice recorder and flight data recorders that investigators use to reconstruct the events leading up to a plane crash. The box is actually bright orange.
Black Box Corporation
A leading direct marketer of connectivity solutions ” everything from cables to routers. It publishes and distributes the award-wining Black Box Catalog. Black Box is based in Pittsburgh. They kindly provided the pinout diagrams for the back of this dictionary. www. blackbox .com.
Black Facsimile Transmission
-
In facsimile systems using amplitude modulation, that form of transmission in which the maximum transmitted power corresponds to the maximum density of the subject copy.
-
In facsimile systems using frequency modulation, that form of transmission in which the lowest transmitted frequency corresponds to the maximum density of the subject copy.
Black Hats
These guys are the bad hackers. They're the ones that break into systems, steal confidential information to sell or destroy, delete documents, remove legitimate users, and above all they usually just break stuff. Sometimes they get paid to do it, sometimes they do it because of a grudge they have on their previous employer, and sometimes they do it simply for personal enjoyment.
Black Hole
-
Routing term for an area of the network where packets enter, but do not emerge, owing to adverse conditions or poor system configuration within a portion of the network.
-
A theorized invisible (thus perceived as dark) region in space with a small diameter in relation to its intense gravitational field that is proposed to result from the collapse of a massive star in which the escape velocity equals the speed of light. Basically an object whose gravity is so strong that not even light can escape from it.
Black Jack
When Samuel Morse won a contract from the U.S. Congress in the 1800s to build a telegraph line from Washington, DC to Baltimore, he initially tried to install the lines underground, alongside railroad tracks. There were problems with the lines and the wires were later suspended from poles. To this day, millions of miles of communications cables are installed on utility poles. Since the wooden poles are subject to weathering, they are coated with creosote, a preservative derived from coal tar. It has come to be called black jack.
Black Level
The lowest luminance level that can occur in video or television transmission and which, when viewed on a monitor, appears as the color 'black.'
Black List
See White List.
Black Matrix
Picture tube in which the color phosphors are surrounded by black for increased contrast.
Black Recording
-
In facsimile systems using amplitude modulation, that form of recording in which the maximum received power corresponds to the maximum density of the record medium.
-
In a facsimile system using frequency modulation, that form of recording in which the lowest received frequency corresponds to the maximum density of the record medium.
Black Signal
-
In facsimile, the signal resulting from the scanning of a maximum- density area of the subject copy.
-
In cryptographic systems, a signal containing only unclassified or encrypted information.
Black Thursday
The day that began the Great Depression. It was October 24, 1929.
Blackbird
Blackbird is a multifunction system, providing home users with a single box that can work as a game system, network computer, home broadband router, and set-top box. The primary backer behind Blackbird is Motorola. Much of Blackbird's "middleware" software was developed with partners . According to David Lammers, of EE Times, Spyglass built a browser and other networking software that will let companies customize their own offerings and get to the retail channel by next year. Another key partner is VM Labs, a Silicon Valley-based game company headed up by former Atari president Richard Miller. VM Labs worked with Motorola to create a media processor, Nuon, which, at different times, has gone under the code names of Merlin and Project X, Burgess said. Nuon is a 128-bit VLIW engine that will work in tandem with the CPU in Blackbird, a PowerPC 860 core.
Blackout
A total loss of commercial electric power. A blackout has a decidedly negative affect on your ability to compute and communicate, assuming that your systems are wired, rather than wireless. UPS (Uninterruptible Power Supply) systems provide battery backup protection from a blackout. Carriers use diesel power generators to keep their central offices operating during a blackout-that way, the phones still work when the lights go out.
Blackout Area
A CATV and satellite TV definition. A pre-defined area of the country where a particular programming service will not be available, usually because of contractual agreements.
Blacksburg Electronic Village
Blacksburg is a town of 40,000 people in the mountains of Southwestern Virginia which contains the main campus of Virginia Polytechnic Institute & State University, also known as Virginia Tech, They have wired both Virginia Tech students and thousands of their town's citizens with email, internet access and bulletin boards . The official explanation is: The Blacksburg Electronic Village (BEV) is a cooperative project of Virginia Tech, Bell Atlantic of Virginia and the Town of Blacksburg. It links the town's citizens to each other and to the Internet via computer lines. Citizens gain access to the Internet from their home or office through a high-speed modem pool or by using Ethernet LANs which are available in some offices and hundreds of apartment units in town. Blacksburg residents may take advantage of a full spectrum of services including the Internet, World Wide Web, Gopher, electronic mail, electronic mailing lists and thousands of Usenet newsgroups. In addition to full Internet access, citizens enjoy the benefits of extensive online local resources. The Blacksburg Electronic Village is famous because it really is the first town to aggressively ensure that the bulk of citizenry could and would have access to electronic mail and to the various resources on the Internet. It has apparently made a major difference in how people live and communicate in Blacksburg. www.bev.net.
Blade
-
A blade is any card placed into a backplane in a telephone system. Usually a blade is an additional module. The "blade" term shows the aspect of insertion of the flat plane. This definition contributed by Bob Frankenberger. A blade is also a "computer-on-a- card." Several hundred of these computers can now be crammed into a chassis that now holds 40-plus of today's popular pizza-box shaped server computers. According to the Wall Street Journal, "their small size, their ability to share Internet connections and the disk storage among the blades allow these computers to operate on a fraction of the power and air conditioning of traditional servers" ” thereby promising to reduce important costs for data centers. Says the Journal, "for the companies that house and manage thousands of computers for Internet operations, such very small and cost-efficient machines allow to collect more fees per square foot of computer space." See also Blade Server.
-
Some people in telecom also refer to a blade as software.
-
When people get fired , they often refer to the event as "the blade fell."
Blade Server
A computer server built on or several computer printed circuit cards and then . Many blade servers can fit on a single rack. They can be linked together and can provide the power of a big server for a fraction of the price. See also Blade.
BLAM
Binary Logarithmic Access Method. A proposed alternative to the IEEE 802.3 backoff algorithm.
Blamestorming
Blamestorming occurs when people sit around in a group and discuss why a deadline was missed or a project failed, and most importantly, who was responsible.
In contemporary telecom-speak, WorldCom technologists didn't troubleshoot, they blamestormed.
Blank
A character on teletype terminals that does not punch holes in paper tape (except for feed holes to push the paper through). Also the character between words, usually called a "Space" is referred to in IBM jargon as a Blank.
Blank and Burst
On the AMPS cellular telephone network, certain administrative messages are sent on the voice channel by blocking the voice signal (blanking) and sending a short high speed data message (burst). The blank and burst technique is one that causes a momentary dropout of the audio connection (and sometimes disconnection of cellular modem connections) when a power level message is transmitted to the cellular phone.
Blank Cell
The hollow space of a cellular metal or cellular concrete floor unit without factory installed fittings.
Blanket
Covering or intended to cover a large group or class of things, conditions, situations, etc.: a blanket proposal; a blanket LOA (Letter of Agency). An LOA is a letter you give to someone whom you allow to represent you and act on your behalf. For example, a letter of agency is used when your interconnect company orders lines from your local phone company on your behalf . Letters of Agency are also used when companies switch their long distance service from one carrier to another. A blanket LOA can mean everything from a group of numbers belonging to one customer at multiple sites or multiple customers at multiple sites.
Blanking
The suppression of the display of one or more display elements or display segments.
Blanking Interval
Period during the television picture formation when the electron gun returns from right to left after each line (horizontal blanking) or from top to bottom after each field (vertical blanking) during which the picture is suppressed.
Blanking Pulses
The process of transmitting pulses that extinguish or blank the reproducing spot during the horizontal and vertical retrace intervals.
Blast
BLocked ASynchronous Transmission. A proprietary technology.
Blatherer
A Internet user who takes four screens to say something where four words would work a lot better.
BLEC
-
Broadband Local Exchange Carrier. A service provider offering broadband services locally.
-
Building Local Exchange Carrier. BLECs are business entities ” mostly specialists, aligned with REITs (Real Estate Investment Trusts) or landlords ” who invest in creating and managing the " intelligent local loop" ” a combination of premise wiring, demarc systems, basement POPs filled with co-located equipment and applications servers, and, possibly higher order local aggregation points (i.e. central offices) filled with the same ” and all dedicated to providing end-user customers (business and residence) with a wide range of communications services (voice, broadband data, Internet) and computer networking applications (e.g. directory, messaging, DNS, IP telecom gateway, etc.)
Blend
To have outbound and inbound phone calls answered by the same agents . See the next two definitions.
Blended Agent
A call center person who answers both incoming and makes outgoing calls. This idea of a blended agent is a new concept in a Call Center. In the past call centers have typically kept their inbound and outbound agents separate. The reason? Management felt that the necessary skills were very different and no one could master both.
Blended Call Center
A telephone call center whose agents both receive and make calls. In other words, a call center whose phone system acts both as an automatic call distributor and a predictive dialer.
Blended Floor System
A combination of cellular floor units with raceway capability and other floor units with raceway capability systematically arranged in a modular pattern.
BLER
Block Error Ratio. The ratio of the blocks in error received in a specified time period to the total number of blocks received in the same period.
BLERT
BLock Error Rate Test. Data transmission testing in which the error rate counted is the number of blocks containing errored bits instead of the raw number of errored bits. Many users claim this is more representative of the real throughput quality of a circuit than simple raw BER testing. See BERT.
BLES
Broadband Loop Emulation Service. Developing specifications from both the ADSL Forum and the ATM Forum. BLES addresses the requirements for an end-to-end architecture to support voice and data over frame-based DSL loops, with voice supported over an emulated circuit. One BLES approach is for all traffic to be carried in ATM cells. The other approach is a mixture of IP and ATM, with data carried in IP packets, and with compressed voice carried in ATM cells using AAL 2 (ATM Adaption Layer 2) and supported by the rt-VBR (real time-Variable Bit Rate) service category. In either case, BLES extends Class 5 Central Office (CO) capabilities (e.g., custom calling and Centrex services, as well as voice trunking) over a DSL local loop for support of network-based circuit switched voice. The other approach is VoMBN (Voice over Multiservice Broadband Networks), which also supports VoDSL (Voice over DSL), but without the involvement of a Class 5 switch. Rather, VoMBN involves various gateway devices at the network edge in support of VoIP (Voice over Internet Protocol) or VoATM (Voice over ATM) packet voice traffic. BLES generally appeals to incumbent PSTN carriers while VoMBN appeals to newer carriers that have built backbone networks based on either ATM or IP, rather than traditional circuit-switching technology. See also AAL 2, ADSL, ADSL Forum, ATM, IP, LES, and rt-VBR.
BLF
The Busy Lamp Field is a visual display of the status of all or some of your phones. Your BLF tells you if a phone is busy or on hold. Your Busy Lamp Field is typically attached to or part of your operator's phone. See Busy Lamp Field.
Blind Bore
Imagine you want to lay fiber cable along the side of a highway. You know from blue staking and from the city maps that there are other utility cables along the highway you want. The first thing we know is that we can't trust the maps or the blue staking. The second thing we know is that we don't want our activities to cut someone else's cable. There are expensive implications to doing this. So what we do is we hand dig pot holes every so often along what's known as the running line ” where the utilities are meant to be buried. The idea is that our pot holes will locate the existing underground cables and thus make it safer to bore our own cable. Blind boring occurs when we bore underground without digging pot holes. The reason we might do this? Some states and some cities simply don't allow pot holing. They trade the risk of hitting a utility line against creating a hole in the middle of the street. They don't want pot holes in their street, since an asphalt patch has never the same integrity as a total overlay and they don't want their streets messed up. See Blue Stake.
Blind Carbon Copy
bcc. A list of recipients of an e-mail message whose names do not appear in the normal message header, so the original recipient of the message does not know that copies have been forwarded to other locations. Sometimes called blind courtesy copy.