A: A-Azimuth Beam Width
A-ABEND
A
-
Abbreviation for AMP or AMPERE, a unit of electric current. For a longer explanation, see Ampere.
-
The non-local wireline cellular carrier. In one of its less intelligent decisions, the FCC decided to issue two cellular franchises in each city in the United States. They gave one to the local phone company (the B carrier) and one to a competitor (the A carrier). This duopoly has naturally meant little real competition. But with the issuing of PCS licences in recent years , competition has begun to heat up, i.e. prices have dropped. Meantime, the "A" carrier on your cellular phone is the non-local wireline carrier, i.e. the competitor to the local phone company and "B" is the other one, namely the local phone company's cellular company. Recently, many of the "A" carriers have been purchased by other large telecom carriers , notably AT&T.
-
Abbreviation for atto, which is ten to the minus 18th. Which means it's very very small.
A & A1
Control leads that come from 1A2 key telephone sets to operate features like flashing of lights to indicate on hold, line ringing, etc.
A & B Bits
Bits used in older T-carrier channel banks for signaling and control purposes. Traditionally, T-1 frames are organized into superframes of 24 frames . Older channel banks (i.e., D1, D2, D3 and D4) use a process known as "bit robbing" for signaling and control purposes. In the sixth frame of a superframe, an "A bit" was robbed from each channel. In the 12th frame of a superframe, a "B bit" was robbed. In each case, the robbed bit was replaced with a signaling and control bit which could be used to indicate such things as "on-hook" or "off-hook" status, and to perform certain monitoring and alarming functions. This is an intrusive , in- band signaling and control technique, as the robbing of the bits violates the integrity of the bit stream and, therefore, violates the integrity of the datastream being transmitted. Newer Extended Superframe (ESF) channel banks perform their signaling and control functions without the use of this intrusive technique. See also C-Bit, Channel Bank, Extended Superframe, T-1, and T-Carrier.
A & B Leads
Additional leads used typically with a channel bank two-wire E&M interface to certain types of PBXs (also used to return talk battery to the PBX).
A & B Signaling
Procedure used in most T-1 transmission links where one bit, robbed from each of the 24 subchannels in every sixth frame, is used for carrying dialing and controlling information. A type of in-band signaling used in T-1 transmission. The way it works is thus. You start with 1.544 million bits per second. You knock it down by 8,000 framing bits to 1,536,000. To prove this, take eight bits for each channel and multiply by the number of channels (24) then multiply that by the sampling rate (8000 Hz) then add the framing bit multiplied with the sampling rate. Here's the arithmetic: ((8*24=192)*8000=1,536,000 bps)+1*8000= 1,544,000 bps or 1.544 Mbps.
A Battery
Another term for Talk Battery.
A Bit
See A & B Bits.
A Block
Cellular licenses received from the FCC with no initial association to a telephone company. Also referred to as non-wireline.
A Carrier
Cellular provider in the 824-849 Mhz frequency range. In U.S. markets that have only two cellular carriers, one is designated the A carrier and the other the B carrier, which operates in the 869-894 MHz range. The A band license was generally awarded to a new entrant and this license was dubbed the non-wireline license.
A Law
The PCM coding and companding standard used in Europe and in areas outside of North American influence. A Law Encoding is the method of encoding sampled audio waveforms used in the 2.048 Mbps, 30-channel PCM primary system known as E-carrier. See MU Law and PCM.
A Links
A SS7 term. A-Links connect an end office or signal point (SP) to a mated pair of Signal Transfer Points (STPs). Two-way path diversity is recommended so that one common disaster does not isolate a signal point from the rest of the network. The other location for A-Links is between mated pairs of STPs and the SCPs. Typically, this would occur at the regional level with the A-Links assigned in a quad arrangement. See B, C and D Links.
A Number
A cellular term for the number of the calling party. The originating switch analyzes the number in order to route the call to the B Number, the number of the called party.
A Port
Refers to the port in an FDDI topology which connects the incoming primary ring and the outgoing secondary ring of the FDDI dual ring. This port is part of the dual attachment station or a dual attachment concentrator.
A Records
Address Records. All machines (i.e., host computers) that are connected directly to the Internet have IP (Internet Protocol) addresses. The DNS (Domain Name Servers) translate the " names " of the machines from URLs (Uniform Resource Locators), such as Harry_Newton@TechnologyInvestor.com, into the dotted decimal notation characteristic of the IP addressing scheme. Those machines that are directly connected to the Internet have both their URLs and their IP addresses stored in the DNS as "A Records" (Address Records). Machines that are not directly connected, have their address translation information stored as "MX Records." The MX Records point to the IP address of the mail host (i.e., the machine that is accepting mail for that target machine). See also MX Record, CNAME Records, DNS, and URL.
A,B,C, and D-Bit Signaling
A signaling technique sometimes used in T-1 channel banks based on Extended SuperFrame (ESF). This approach is an in-band, or Channel-Associated Signaling (CAS), technique in which bit-robbing is used in frames 6, 12, 18, and 24 of a superframe of 24 frames. In each case, the eighth bit of each channel is "robbed," in a process known as "bit-robbing," in order to insert a signaling bit. Assuming that 16 states (i.e., values) are required for signaling purposes, each bit position in each channel can be either a "0" or a "1." (Note that 2 to the 4th power equals 16.) If 16 states are required, the signaling bits are known as A,B,C, and D-bits. If four states are required, the signaling bits are known as A,B,A, and B-bits. If only two states are required, the signaling bits are known as A,A,A, and A-bits. See also Bit-robbing, ESF, and T-1.
A-Band Carrier
See A Carrier.
A-B Rolls
A technique by which audio/video information is played back from two videotape machines rolled sequentially, often for the purpose of dubbing the sequential information onto a third tape, usually a composite master.
A-B Test
Direct comparison of the sound/picture quality of two pieces of audio/TV equipment by playing one, then the other.
A-Carrier or A-Band Carrier
Cellular provider in the 824-849 Mhz frequency range. In U.S. markets that have only two cellular carriers, one is designated the A carrier and the other the B carrier, which operates in the 869-894 MHz range. The A° band license was generally awarded to a new entrant and this license was dubbed the non-wireline° license.
A-Condition
In a start-stop teletypewriter system, the significant condition of the signal element that immediately precedes a character signal or block signal and prepares the receiving equipment for the reception of the code elements. Contrast with start signal.
A-GPS
A cell phone term. Assisted GPS, a satellite positioning system that improves the functionality and performance of GPS. Requires a special cell phone handset.
A-Interface
The network (air) interface between a Mobile End System (M-ES) and the Cellular Digital Packet Data (CDPD)-based wireless packet data service provider network.
A-Key
Authentication Key. An authentication mechanism of the ANSI-41 (formerly TIA IS-41C) standard for cellular intersystem inter-operability. The A-key is sent between the cellular phone and the Authentication Center (AC), and is known only to those two entities. Subsequently, the cellular phone and the AC generate a second secret key, known as a SSD (Shared Secret Data). Both the A-key and the SSD are transmitted around the ANSI- 41 network to be used by switches to perform the challenge-response process of authentication. Both keys are encrypted through the CAVE (Cellular Authentication and Voice Encryption) algorithm. See also CAVE.
A-Law
The ITU-T companding standard used in the conversion between analog and digital signals in PCM systems. A-law is used primarily in European telephone networks and is similar to the North American mu-law standard. See also Companding and Mu law.
A-link
SS7 access link. A dedicated SS7 signaling link not physically associated with any particular link carrying traffic.
A/B Switch
-
A switch that allows manual or remote switching between one input and two outputs. See A/B Switch Box.
-
A feature found on all new cellular telephones permitting the user to select either the "A" (non-wireline) carrier or the "B" (wireline) carrier when roaming away from home.
A/B Switch Box
A device used to switch one input between two devices, such as printers, modems, plotters , mice, phone lines, etc. An example of how you use such a box: You plug one phone line into the "C" (for Common) jack. You plug a fax machine into the "A" jack. You plug a modem into the "B" jack. By turning the switch, you can use one phone line for either a modem or a fax. A/B switch boxes come in many flavors, including also serial and parallel port versions. There are also A/B/C switches that switch among three devices, e.g. a fax, a modem and a phone. There is also a Crossover Switch that connects two inputs and two outputs. In one position the switch might connect input A with output D and input B with output C. In the other position, it might connect input A with output C and input B with output D. See also A/B Switch.
A/B Switches
Input Selector Switch. A switch used by cable customers to alternate between cable and over-the-air television reception through a cable box.
A/D
Analog to Digital conversion.
A/D Converter
Analog to Digital converter, or digitizer . It is a device which converts analog signals (such as sound or voice from microphone), to digital data so that the signal can be processed by a digital circuit such as a digital signal processor. See CODEC.
A/UX
An alternate operating system for the Macintosh based on UNIX. A/UX has its own, unique 32-bit addressing mode.
A/V Switching
A Satellite Term. A/V switching is a feature that allows users to connect one or more sources, such as a VCR, camera and/or laser videodisc player and select which source will be monitored .
A20 Line
A control line on the Intel 80386 microprocessor that allows MS-DOS and an extended memory manager to create the High Memory Area, or HMA. Only one program can claim control over the A20 at a time.
A4
The Basic Group 3 standard that defines the scanning and printing of a page 215 mm (8.5 in) wide. An A5 page is 151 mm (5.9 in) wide, and the A6 is 107mm (4.2 in) wide.
A5
See A4.
A6
See A4.
AA
-
Automated Attendant. A device which answers callers with a digital recording, and allows callers to route themselves to an extension.
-
Auto Answer. A modem indicator light that is meant to tell you the modem is ready to pick up the phone, so long as there's a communication program running and prepared to handle the call. See also Modem.
-
In telco parlance, AAA stands for Authentication, Authorization, and Accounting, and is an essential telco OSS (Operations Support System) function.
AAA
-
Authentication, authorization, and accounting. Pronounced "triple a." A framework used for network management and security that controls access to computer resources by identifying unique users, authorizing the level of service, and tracking the usage made of resources. AAA servers typically interact with network access and gateway servers and with databases and directories that contain user information.
-
American Automobile Association. The AAA was formed in 1905 for the express purpose of providing "scouts" who would warn motorists of hidden police speed traps. Since then its functions have expanded and now it rescues broken-down automobiles and provides discount travel services.
AABS
Automated Attendant Billing System. A feature which allows collect and third-number billed toll calls to be placed on an automated basis. A synthesized voice prompt guides the caller through the process, the system then seeks approval of the prospective billed party, and either completes or denies the call based on that authorization or lack thereof. AABS is automated in much the same way as calling card services have been automated, through the use of an Intelligent Peripheral (IP) device.
AAL
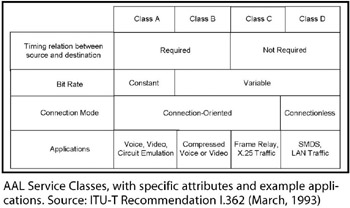
ATM Adaptation Layer of the ATM Protocol Reference Model, which is divided into the Convergence Sublayer (CS) and the Segmentation and Reassembly (SAR) sublayer. The AAL accomplishes conversion from the higher layer, native data format and service specifications of the user data into the ATM layer. On the originating side, the process includes segmentation of the original and larger set of data into the size and format of an ATM cell, which comprises 48 octets of data payload and 5 octets of overhead. On the termination side of the connect, the AAL accomplishes reassembly of the data. Taken together, these processes are known as Segmentation and Reassembly. AAL is defined in terms of Types supported by the Convergence Sublayer. Each type supports certain specific types of traffic, and each offers an appropriate Quality of Service (QoS), based on traditional network references. See the next five definitions for AAL specifics.
AAL-1
ATM Adaptation Layer Type 1: AAL functions in support of Class A traffic, which is connection-oriented, Constant Bit Rate (CBR), time-dependent traffic such as uncom- pressed, digitized voice and video. Such traffic is isochronous, i.e., stream-oriented and highly intolerant of delay.
AAL-2
ATM Adaptation Layer Type 2: This AAL supports Class B traffic, which is connection-oriented, Variable Bit Rate (VBR), isochronous traffic requiring precise timing between source and sink. Examples include compressed voice and video.
AAL-3/4
ATM Adaptation Layer Type 3/4: AAL support of Class C and D traffic, which is Variable Bit Rate (VBR), delay-tolerant data traffic requiring some sequencing and/or error detection support, but no precise timing between source and sink. Originally two AAL types, AAL types 3 and 4, were combined in support of both connection-oriented and connectionless traffic. Examples include X.25 packet and Frame Relay traffic.
AAL-5
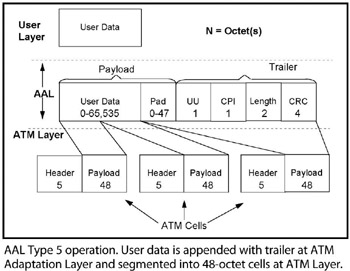
ATM Adaptation Layer Type 5. AAL functions in support of Class C traffic, which is of Variable Bit Rate (VBR), and which is delay-tolerant connection-oriented data traffic requiring minimal sequencing or error detection support. Such traffic involves only a single datagram in Message Mode. Examples of AAL-5 data include signaling and control data, and network management data. AAL-5 also is known as SEAL (Simple and Efficient AAL Layer). AAL-5 traffic originates in the form of a native data payload unit which is known as an IDU (Interface Data Unit). The IDU is of variable length, up to 65,536 octets. At the Convergence Layer the IDU is appended with a trailer including the UU, CPI, Length and CRC fields. The UU (User-to-User) field of one octet contains data to be transferred transparently between users. The CPI (Common Part Indicator) field of one octet aligns the trailer in the total bit stream. The Length field of two octets indicates the length of the total IDU payload. The CRC (Cyclic Redundancy Check) of four octets is used for purposes of error detection and correction in the trailer, only. When the payload user data plus the trailer data hit the ATM Adaptation Layer, the entire set of data is segmented into 48-octet pay- loads, with each being prepended with a 5-octet header to form a 53-octet ATM cell. See ATM.
AAL Connection
An ATM term. Association established by the AAL between two or more next higher layer entities.
AALn
See AAL-1, AAL-2, AAL-3/4, AAL-5.
AAN
Associated Account Number. Used in wireless service.
AAR
Automatic Alternate Routing.
AARP
-
AARP used to stand for American Association of Retired Persons, but it's now just AARP, since you don't have to be retired to join. You just have to be old ” 50 years old, to be exact. Don't laugh . You'll be old someday, and just before your 50th birthday AARP will send you a membership invitation . AARP is a remarkably successful marketing organization.
-
AppleTalk Address Resolution Protocol is a method of mapping addresses between the addresses of computers on an AppleTalk LAN and those known to Ethernet, Token Ring or some other LAN. AARP actually will map addresses at any level of protocol stacks to resolve issues of AppleTalk node address availability used by the AppleTalk DDP (Datagram Delivery Protocol), higher-layer AppleTalk protocols, and underlying data links providing AppleTalk connectivity. AppleTalk addresses are temporary addresses that are assigned dynamically from a pool, or cache. When a host Apple Macintosh computer boots (i.e., starts up), it chooses an address and checks with the address cache to see if that address is available. If it is not, the process repeats until an available address is discovered . AARP manages this process. See also AppleTalk and DDP.
AARP Probe Packets
Packets transmitted by AARP that determine if a randomly selected node ID is being used by another node in a nonextended AppleTalk network. If the node ID is not being used, the sending node uses that node ID. If the node ID is being used, the sending node chooses a different ID and sends more AARP probe packets.
AAV
Alternative Access Provider. Another name for a CAP. See CAP.
ABAM
A Lucent Technologies (see Western Electric) ordering code for a now-outmoded physical copper cable used in DSX (e.g., T-1 and T-2) implementations . ABAM cable is two- pair, foam insulated , twisted-pair cable of 22/24 gauge, with 100 ohms impedance at .772 MHz. ABAM is just an ordering code, which really doesn't stand for anything. ABAM has been replaced by Category/Level 2, or higher, cable.
Abandon On Ugly
A video call center term coined by Andrew Waite. The term refers to a caller seeing the not-attractive answering agent, and hanging up instantly. Often the caller redials in the hope of reaching someone more attractive.
Abandoned Attempt
An attempt to make a call that is aborted by the person making the call.
Abandoned Call
The non-technical explanation is: A call that is answered , but disconnected before any conversation happens. The technical explanation is: A call which has been offered unto a communications network or telephone system, but which is terminated by the person originating the call before it is answered by the person being called. Follow this sequence for an explanation: You call an airline. You hear ringing. Their phone rings. A machine, called an Automatic Call Distributor (ACD), answers the call, plays you some dumb message like, "Please don't hang up. A real human will answer eventually. Dial 1 to order a pizza, Dial 2 for anchovies,...." You, the caller, are put on Eternity Hold.
You get bored waiting and hang up before a live operator answers. You have just abandoned your phone call. Hence, the term Abandoned Call. Information about abandoned calls is highly useful for planning the number of people (also called operators, agents or telephone attendants) an owner of an automatic call distributor or other phone system should employ on what days, during what times of the day, and at what specific locations. Thus the company can organize its resources (i.e., schedule its people) to ensure that the "right" percentage of incoming calls are answered within the "right" amount of time to provide the caller (i.e., you, the customer) the service you deserve (or the service they think you deserve, or, the service they think you should deserve, or the level of service they can afford to provide to "optimize" the cost/benefit relationship).
Abandoned Call Cost
The amount of revenue lost because of abandoned calls. This is calculated based on the number of calls, your estimate of the percentage abandoning, and your estimate of the revenue per call. It's an impossible number to calculate since many callers do, in fact, call back and place their orders on another later call.
Abandoned Property
The term that some issuers of travelers checks give to the 15% or so of their checks which, for some reason or note, are never cashed.
Abandonment Rate
The percentage of callers who hang up after being entered into a queue.
Abbreviated Address Calling
A calling method that allows the user to employ a logical address (e.g., telephone number) involving fewer characters. The destination's assigned device addresses these characters when initiating a connection. May also be called Abbreviated Dialing when specifically used in connection with telephone systems.
Abbreviated Dialing
A feature that permits the calling party to dial the destination telephone number with fewer than the normal digits. Abbreviated Dialing numbers must be set up before using them. Speed Dialing is a typical example of Abbreviated Dialing. See Speed Dialing.
ABC
-
Automatic Bill Calling ” a method of billing for payphone calls. Changed in 1982 to Calling Card service.
-
Automated Business Connection.
ABCD Signaling Bits
These are bits robbed from bytes in each DS-0 or T-1 channel in particular subframes and used to carry in band all status information such as E&M signaling states.
ABD
See Average Business Day.
Abdicate
To give up all hope of ever having a flat stomach.
ABDN
Attendant Blocking of Directory Number.
ABEC
The Alternate Billing Entity Code, which is used by long distance companies (IntereXchange Carriers ” IXCs) to bill third parties' (other CICs ” Carrier Identification Codes) traffic through the primary IXC's CIC code. This is used by IXCs for sending EMI billing records to LECs for bill page presentation.
ABEND
ABnormal END, or ABortive END, or system "crash," and almost always very bad news. When an operating system detects a serious problem, such as a hardware or software failure, the system issues an abend (abnormal end) message. An abend recognized by Novell's NetWare, for instance, would stop the file server...and you're dead in the water. Usually caused by input or data presented to a computer which is beyond its ability to cope. If an abend happens in a single-task program (like MS-DOS), the machine will cease to take input ("lock up") and must be restarted ("re- booted "). Abends can be caused by a variety of factors, such as poorly functioning NetWare Loadable Modules (NLMs), power problems and heavy network traffic. They are the bane of a NetWare operating manager's existence. Multitasking operating systems (like UNIX) allow other programs to continue running while only stopping the one causing trouble. See VREPAIR which explains one way to repair your ABEND problem.