The File Transfer Protocol
| File Transfer Protocol (FTP) enables two computers to upload and download data across a network. Although it has been around for a long time, as has Telnet and email, it is considered an advanced protocol because it operates a little differently in the way it uses ports. FTP uses two main ports ”20 and 21. Port 21 is used for a control connection that is used to transmit commands to and from the FTP server. For example, as a user enters FTP commands, the commands are transmitted on port 21. When data must be downloaded, port 20 provides this basic function. FTP comes in two main modes: standard and passive.
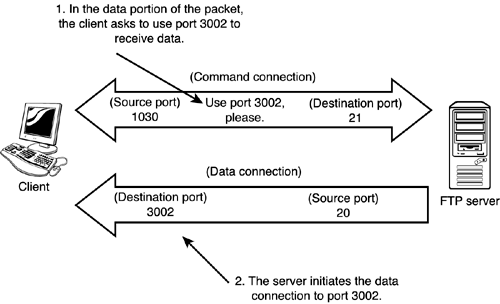
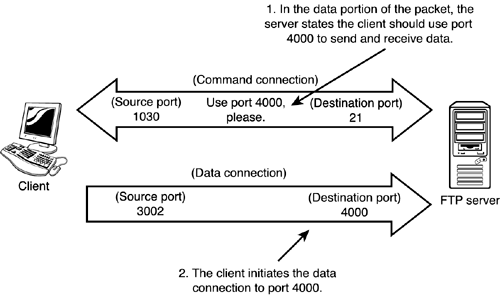
Standard ModeFTP operates in a couple of modes. In standard mode, the FTP client and the server send commands across a command connection on port 21. In this command connection, the client requests to use a port for uploading or downloading. This request is embedded inside the data portion of a packet sent to the server. Because the ASA monitors source port and destination port headers, this request is missed by ASA. Additionally, as the server initiates the data connection back to the client, the firewall drops the packets because no connection slot is created for this traffic. Figure 8.1 show a basic example of a client requesting traffic from an FTP server. In step 1 the client requests to use 3002 as its data port; in step 2 the server starts to make a connection to that port. No connection slot for port 3002 exists, so the packets are dropped. Figure 8.1. Standard mode FTP. Passive ModeThe second FTP mode is passive mode, which operates a little differently from standard mode. The command connection still exists using port 21 on the server. However, the data connection on the server doesn't have to use port 20. When data needs to be transmitted, the client requests asks the server which port it should use. Again, this request is embedded in the data portion of a packet within the command connection traffic. The server sends the port number it wants the client to use, and then the client initiates the data connection to the server. This is the exact opposite from standard mode, in which the server initiates the data connection. Figure 8.2 is a basic example of passive mode FTP. In step 1 the client and server negotiate which server port will be used to transfer data; then in step 2 the client initiates the data connection to the server. Because the client makes this connection, the ASA creates a connection slot and has no problems allowing traffic to pass back and forth. Figure 8.2. Passive mode FTP.
The fixup protocol ftp CommandWith the possible problems of FTP data connections and the ASA dropping uninitiated traffic, the PIX has a fixup protocol option for FTP that compensates for the FTP traffic. This fixup monitors the embedded data portions of the command connection traffic. When embedded port requests are detected , the PIX dynamically creates connection slots for the necessary ports, allowing the uninitiated traffic to flow. The following is the syntax for the ftp command: pixfirewall(config)# fixup protocol ftp <port> [<strict>] Table 8.3. fixup protocol ftp Command Options
The following is the command to enable the FTP fixup protocol: pixfirewall(config)# fixup protocol ftp 21 |
EAN: 2147483647
Pages: 218