Using Remote Login, Copy, and Execution
This section describes some features for allowing users to use resources across a network. They are the telnet, ssh, ftp, wget, rsync, rlogin, rcp, and rsh commands.
| Cross-Reference: | Only the ssh service is turned on by default in Fedora Core. That is because the other remote login, execution, and copy commands described here do not provide encrypted communications by default, and so they can represent significant security risks. For information on how to turn on the services described in this chapter on a Fedora Core server, refer to Chapter 14 and Appendix C. |
Two of the commands described in this section that are generally available are remote login and file transfer programs: telnet and ftp, respectively. Other commands for accessing FTP servers are ncftp and gFTP.
Two newer commands for copying files over the network are wget and rsync. Both of these tools can be used for efficiently downloading files that you can identify on the network.
Other commands described in this section are more specific to Fedora Core and other UNIX systems, but they provide simplified ways of copying files, logging in, and executing commands among trusted systems: rcp, rlogin, and rsh, respectively. Also, a more secure tool for remote login, called ssh, is included with Fedora Core. The ssh command can be used for remote execution as well.
Using telnet for remote login
Telnet is a service provided by many different types of computer systems to enable remote users to log in to their machines over TCP/IP networks. The telnet command is the client program that you use to do the remote login. The most common way to use telnet is with a host name. The following is a typical telnet session:
$ telnet maple Trying 10.0.0.11 ... Connected to maple.linuxtoys.net (10.0.0.11). Escape character is '^]'. Fedora Core release 3 Kernel 2.6.8-1 on an i686 login: mike Password: ******** Last login: Mon Nov 28 13:15:57 from pine [mike@maple mike]$
This example shows what happens when the telnet command is used to log in from a computer named pine to a computer named maple by typing telnet maple. My computer tries to connect to the telnet port on maple (IP address 10.0.0.11). Because maple is also a Fedora system, once the connection is established, I see the standard login: prompt. I type the user name (mike) and the password when prompted. When the login and password are accepted, I see the shell prompt for the user named mike.
The telnet service is disabled by default on Fedora Core systems (as are most network services). So, to be able to log in to your computer using telnet, refer to Appendix C for information on how to turn on the telnet service.
Here are a few useful options you can use with telnet:
-
-a — Automatic login. With this option, your computer attempts to log in to the remote computer using your local user name. So, if you are logged in to your computer as mike, when you use telnet to log in to a remote computer, the remote computer assumes that you want to log in as mike. It simply prompts you for mike’s password.
-
-l user — User name. This option is similar to the -a option, except that instead of using your current user name, you can ask to log in using any user name you choose.
-
-r — Rlogin-style interface. This option lets you use tilde (~) options. For example, to disconnect while in rlogin mode, type ~. (tilde+dot), or to suspend the telnet session, type ~^z (tilde+Ctrl+z). Only use ~. if your remote shell is hung (exit is a better way to quit normally). If you use ~^z to suspend your telnet session temporarily, you are returned to your local system shell. To get back to the suspended session, type fg to put telnet back in the foreground. See the description of rlogin later in this chapter for more features you can use in rlogin mode.
Another way to use telnet is in command mode. Instead of using a host name, simply type the word telnet. You will see a telnet prompt as follows:
$ telnet telnet>
At this point, there are several commands available to you. You are not yet connected to a remote host. To open a login session to a remote computer from the telnet prompt (for example, to a computer named maple), type:
telnet> open maple
After you do connect to a remote computer, you can return to the telnet session at any time by typing Ctrl+]. Here are other options you can use during your telnet session:
-
? — Print help information.
-
! — Escape to the shell. (Type exit to leave the subshell and return to telnet.)
-
close — If you have an open connection, type close to close it.
-
display — Shows the operating parameters that are in effect.
-
logout — Logs you off any remote connection in this session and closes it.
-
mode — Tries to enter line mode or character mode. (Type mode ? to see other options that go with the mode option.)
-
quit — Close telnet and exit.
-
z — Suspend the current telnet session. (Type fg to return to the suspended telnet session.)
If you suspend a telnet session or escape to the shell, return to telnet by typing fg.
Copying files with FTP
Like telnet, FTP is a protocol that is available on many different operating systems. Archives of files on the Internet are stored on what are called FTP servers. To connect to those servers from Fedora Core, you can either type the URL of that server into a Web browser or you can use the ftp command or graphical FTP windows such as gFTP. Of the other FTP client programs available with Fedora Core, my favorite is the ncftp command.
| Tip | The ftp program runs on Windows as well. All of the commands listed here run on UNIX, Linux, and Windows versions of the ftp program. |
Using the ftp command
The ftp command is available on Fedora Core, as well as every other Linux and UNIX system, for copying files to and from FTP servers. Like telnet, FTP has a command mode or you (more typically) can use it to connect directly to a remote computer. For example:
$ ftp maple Connected to maple. 220 (vsFTPd 2.01) Name (maple:mike): jake 331 Please specify the password. Password: ********* 230 Login successful. Remote system type is UNIX. Using binary mode to transfer files. ftp>
In this example, ftp connects to a computer called maple (ftp maple). When I was prompted for a name, it assumed that I was going to use my current login name on maple (maple:mike). I could have pressed Enter to use the name mike, but instead I logged in as jake and typed the password when prompted. The password was accepted and, after some information was printed, I was given an ftp> prompt.
Because FTP is used for public servers, you can often log in using the word anonymous as your user name. By entering a valid e-mail address as your password, you can enter the anonymous FTP site and download files that the server makes available to the public.
Unlike telnet, instead of being in a regular UNIX shell after I logged in with FTP, I was placed in FTP command mode. Command mode with FTP includes a whole lot of commands for moving around the remote file system and for copying files (which is its main job).
FTP directory commands
To get your bearings and move around the remote file system, you could use some of the following commands from the ftp> prompt. The commands are used to work with both the remote and local directories associated with the FTP connection.
-
pwd — Shows the name of the current directory on the remote system.
-
ls — Lists the contents of the current remote directory using the UNIX ls command. You can use any valid ls options with this command, provided that they are supported by the particular FTP server you are connected to.
-
dir — Same as ls.
-
cd — Use the cd command to move to the named directory on the remote system.
-
cdup — Moves up one directory in the file system.
-
lcd — Use the lcd command to move to the named directory on the local system.
If you want to make changes to any of the remote files or directories, use the following commands:
-
mkdir — Creates a directory on the remote system.
-
rename — Renames a file or directory on the remote system.
-
rmdir — Removes a remote directory.
-
delete — Removes a remote file.
-
mdelete — Removes multiple remote files.
Depending on how the FTP server is configured, you may or may not be able to execute some of the file and directory commands shown above. In general, if you log in as the anonymous user, you will not be able to modify any files or directories. You will only be able to download files. If you have a real login account, you will typically have the same read and write permission you have when you enter the computer using a standard login prompt.
FTP file copying commands
Before you copy files between the remote and local systems, consider the type of transfer you want to do. The two types of transfer modes are:
-
binary — For transferring binary files (such as data files and executable commands). This is also referred to as an image transfer.
-
ascii — For transferring plain-text files.
The Linux ftp command seems to set the default to binary when you start FTP. Binary seems to work well for either binary or text files. However, binary transfers may not work transferring ASCII files from non-UNIX systems. If you transfer an executable file in ASCII mode, the file may not work when you try to run it on your local system.
Most file copying is done with the get and put commands. Likewise, you can use the mget and mput commands to transfer multiple files at once. Some FTP servers will even allow you to use matching characters (for example, mget abc* to get all files beginning with the letters abc). Here are descriptions of those commands:
-
get file — Copies a file from the current directory on the remote file system and copies it to the current directory on the local file system. You can use a full path along with the filename. Here are some examples:
ftp> get route ftp> get /tmp/sting
The first example takes the file route from the current remote directory and copies it to the current local directory. The second example copies the file /tmp/sting from the remote system to the file tmp/sting relative to the current directory on the local system. So if your current directory were /home/jake, ftp would try to copy the file to /home/jake/tmp/sting.
-
put file — Copies a file from the current local directory to the current remote directory. The usage of this command is essentially the same as the get command, except that files are copied from the local to the remote system.
Note Anonymous FTP sites (described later) usually let you copy files from them, but not to them. If they do allow you to put files on their servers, it will usually be in a restricted area.
-
mget file . . . — This command lets you download multiple files at once. You can specify multiple files either individually or by using metacharacters (such as the asterisk). FTP prompts you for each file to make sure you want to copy it.
-
mput file . . . — This command lets you put multiple files on the remote computer. Like mget, mput prompts you before transferring each file.
FTP exiting commands
While a connection is open to a remote computer from an FTP client in Fedora, you can use several commands to either temporarily or permanently exit from that connection. Here are some useful commands:
-
! — This command temporarily exits you to the local shell. After you have done what you need to do, type exit to return to your FTP session. You can also use this command to run other local commands. For example, you can type !pwd to see what the current directory is on the local system, !uname -a to remind yourself of your local system name, or !ls -l to see the contents of your current directory.
-
close — Closes the current connection.
-
bye — Closes the connection and exits the ftp command.
Using the ncftp command
By virtue of being an FTP client program, the ncftp command supports all the standard commands you would expect to find in an FTP client (get, put, ls, cd, and so on).
However, ncftp has added features that make it more efficient and friendlier than most FTP clients.
With ncftp, you can connect to an FTP server in the same way you did with ftp. One convenient difference is that if you enter no user name, ncftp assumes you want to use the anonymous user name and just logs you in. Here is an example:
$ ncftp ns1 NcFTP 3.1.8 (Jul 27, 2004) by Mike Gleason http://www.NcFTP.com/contact/ Connecting to 63.240.14.64... (vsFTPd 2.0.1). Logging in... Login successful. Logged in to ns1. ncftp / >
To log in as a user name other than anonymous, add a –u user option, where user is replaced by the name you want to log in as. Enter the password as prompted to continue.
Using ncftp
After you are logged in with the ncftp session running, there are a few nice features you can use that aren’t available with other FTP clients. Here are some examples:
-
bookmark — If you are visiting a site that you want to return to, type the bookmark command and type a name to identify that site. The next time you start an ncftp session, type the bookmark name as an option. Not only are you logged into the FTP site you bookmarked; you are taken to the directory where you set the bookmark.
-
lls, lcd, lmkdir, lpwd — There is a set of commands that enables you to move around the local file system. Just place a letter “l" in front of standard shell commands like ls, cd, mkdir, pwd, rm and rmdir and you can move around and work with your local file system while you are in ncftp.
-
rhelp — Use rhelp to see commands that are recognized by the remote FTP server. To see commands that are specific to the FTP server, type help while you are in an ncftp session.
-
Auto-resume — If you were disconnected in the middle of a large download, you will appreciate this new feature. After a connection is broken during a download, reconnect to the FTP site and begin downloading the file again in the same local directory. The ncftp command resumes downloading where it left off.
Using ncftp for background transfers
If you are moving around to different parts of the FTP site, or jumping between different sites, you might not want to wait around for a file transfer to complete before you can go somewhere else. The ncftp command has an excellent feature for placing transfer commands in a spool file and then running them in the background immediately or later.
To select a file for background transfer, use the bgget command. Here is an example:
ncftp /pub > bgget wireless.doc • Spooled: get wireless.doc ncftp /pub > jobs ---Scheduled-For-----Host------------Command-------------------- 2003-09-01 18:38 maple GET wireless.doc ncftp /pub > bgstart Background process started. Watch the "/home/br/.ncftp/spool/log" file to see how it is progressing
In this example, the bgget command spools the wireless.doc file from the remote current directory (/pub) and sets it to be copied to the local current directory. Typing the jobs command shows that the job (GET wireless.doc), from the host named maple, is scheduled to run immediately (6:38 p.m., September 1, 2003). By running the bgstart command this process, and any other spooled jobs, are run immediately.
Instead of starting the background transfers immediately you can do them later. For background jobs spooled for transfer, the transfer begins when you quit ncftp, leave your current FTP site or go to another FTP site. In this way, the program that does the transfer (ncftpbatch) can take over your current login session to do the transfer.
If you wanted to wait even longer to do the transfers, you can pass an option to the bgget command to have it start the transfer at a particular time. Here is an example:
ncftp /pub > bgget -@ 2003090410000 wireless.doc
With this command, the transfer is set to run at 1 a.m. on September 4, 2003 to transfer the file called wireless.doc. Again, you can check the .ncftp/spool/log file in your home directory to see if the transfer has completed.
Using the gFTP window
If you prefer a more graphical interface for accessing FTP servers, you can use the gFTP window. You can open a gFTP window by typing gftp or by choosing Internet ® gFTP from the Red Hat menu on the desktop. Figure 9-10 shows an example of the gFTP window.
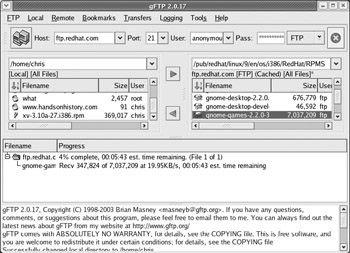
Figure 9-10: View local and remote files simultaneously from the gFTP window.
Unlike the ftp command, the gFTP window lets you simultaneously see the contents of the current remote and local directories. To transfer a file from one side to the other, simply double-click it or drag-and-drop it to the other pane. (Normally, you will just be copying files from FTP sites, unless a site provides you with permission to write to it.)
Follow this procedure to connect to an FTP site:
-
Type the name of the FTP server to which you want to connect (for example, ftp.redhat.com) into the Host box.
-
Type the port number on the FTP server (you can leave this blank to use the default port number 21).
-
Type the user name used to log in to the FTP server. Use the default anonymous if you don’t have a specific user name and the server is pubically accessible.
-
Type the password for the user name you entered. The convention with anonymous FTP servers is to use your e-mail address as the password.
-
Click the icon displaying two little monitors to connect to the FTP site.
-
If you entered the information correctly, the bottom pane on the window should show that the transfer was complete and the right pane should show the contents of the current directory of the FTP site. Here are some actions you can take once you are connected:
-
Move around. Double-click a directory to move to that directory or double-click on the two dots (. .) to move up a level. You can do this on both the remote and local directories.
-
Drag-and-drop files. You can drag-and-drop files from the FTP site on to the left pane (representing your current local directory).
-
Save this site. If you want to return to this site later, choose Bookmarks ® Add Bookmark. A pop-up window lets you name this site for the bookmarks list. After you do, you can select that entry from the list at a later date to connect to that site. The gFTP window will have stored not only the host name, but also the port, user name, and password. So you are just one click away from connecting. This is one of the best features of graphical FTP programs such as gFTP.
-
A nice feature of gFTP is that it stores log information. Choose Logging ® View Log. A window appears showing you the conversations that have taken place between your computer and each FTP site. You can look at these messages to see what is wrong if you are unable to connect to a site or to remember where you have been and what you have done on an FTP site.
Getting files with wget
If you already know where a file is on the network, there are more efficient ways of downloading that file than opening an FTP session, moving around the FTP server, and running the get command. The wget command is a simple, efficient tool for doing noninteractive downloads of files over the Internet.
If there is a file you want to download from an FTP site or Web server (HTTP), and you know exactly where the file is, wget is a good way to download. The wget command is very useful if you want to copy a whole site, recursively, from one computer to another (for example, containing user home directories). When downloading from FTP sites, wget can let you just download as the anonymous user or add your own user name and password to the command line.
Here is an example of using wget to get a file from an FTP site:
$ wget ftp://ftp.redhat.com/pub/contrib/libc6/i386/zsh-4.1.1-1.i386.rpm -- 01:53:33- ftp://ftp.redhat.com/pub/contrib/libc6/i386 = `zsch-4.1.1-1.i386.rpm` Resolving ftp.redhat.com ... done. Conecting to ftp.redhat.com[216.148.218.201]:21... connected. Loggin in as anonymous ... Logged in! ==> SYST ... done. ==> PWD ... done. ==> TYPE I ... done. ==> CWD /pub/contrib/libc6/i386 ... done. ==> PASV ... done. ==> RETR zsh-4.1.1-1.i386.rpm... done. Length: 2,541,655 (unauthoritative) 100%[=================================>] 2,541,655 50.31K/s ETA 00:00 05:16:39 (50.31 KB/s) - `zsch-4.1.1-1.i386.rpm` saved [2541655]
By the first part of the URL (ftp://), wget knows you are copying a file from using FTP to the current directory (.) on the local host. After resolving the address (ftp.redhat.com), wget connects to the site, logs in as the anonymous user, changes the working directory (to /pub/contrib/libc6/i386), and transfers the file. As the file downloads, wget shows the progress of the download, and then exits.
If you need to log in as a user other than anonymous, you can add that information to the command line or to a .netrc file in your home directory (type man netrc to see the format of that file). Here is an example of adding the password to the command line:
$ wget ftp://joe:my67chevy@ftp.handsonhistory.com/memol.doc .
| Caution | Adding a password to a command line leaves the password exposed to onlookers. This practice is generally discouraged, except in cases where no one can see your monitor or your history files. |
In the previous example, the user logs in as joe with the password my67chevy. The wget then copies the file memo1.doc from the current directory on the host computer named ftp.handsonhistory.com. That current directory is most likely /home/joe.
Using wget, you can download files from Web servers as well. The wget command downloads files using the http protocol, if file addresses begin with http://. Downloading a single file, you would use the same form as you would for an FTP file (for example: wget http://host/file.). The best wget option for HTTP downloads is -r (recursive).
A recursive download lets you choose a point at a Web site and download all content below that point. Here is an example of a recursive download used to download the contents of the www.handsonhistory Web site.
$ wget –r www.handsonhistory.com .
In this example, the directory structure making up the www.handsonhistory.com Web site is copied below the current directory in the directory www.handsonhistory.com. This is useful if you want to move the contents of a Web site from one computer to another.
| Caution | Downloading an entire Web site can result in a massive amount of data being downloaded. If you only want part of a Web site, start from a point lower in the site’s structure. Because content is taken by following links, if there is content in a directory at the Web site that isn’t in a link, it won’t be downloaded. |
| Note | Another command that you might be interested in, similar to wget, is the curl command. Like wget, curl can download files using the ftp or http protocols. However, it also includes support for secure http (https), telnet and gopher protocols. Curl can also do multiple file transfers on the sameconnection. |
Using ssh for remote login/remote execution
Although the telnet and rlogin login commands and rsh remote execution command have been around much longer, the ssh command is the preferred tool for remote logins and executions. The reason is that ssh provides encrypted communication so you can use it securely over insecure, public networks between hosts that don’t know each other.
In the following example, ssh is being used to log in to a computer named maple. Because no user is specified, ssh tries to log in as the current user (which is the root user in this case).
# ssh maple root@maple's password:
If you wanted to log in as a different user, you could use the -l option. For example, to log in to the computer named maple as the user named jake, you could type the following:
# ssh jake@maple jake@maple's password:
The ssh command can also be used to execute a command on the remote computer. For example, if you wanted to monitor the messages file on a remote computer for a minute, you could type the following command:
# ssh root@maple "tail -f /var/log/messages" root@maple's password:
After you typed the password in the above case, the last several lines of the /var/log/messages file on the remote computer would be displayed. As messages were received, they would continue to be displayed until you decided to exit (press Ctrl+C to exit the tail command).
| Note | Find out more about the ssh command from the SSH Web site (www.openssh.org). |
Using scp for remote file copy
The scp command is a simple yet secure way of copying files among Linux systems. It uses the underlying ssh facility, so if ssh is enabled, so is scp. Here is an example of using scp to copy a file from one computer to another:
# scp myfile toys.linuxtoys.net:/home/chris root@toys.linuxtoys.net's password: ******
In this example, the file myfile is copied to the computer named toys.linuxtoys.net in the /home/chris directory. If you don’t provide a user name (as is the case here), scp assumes you are using the current user name. Unlike some tools that provide remote login, scp and ssh do allow you to login as root user over the network, by default. (Many people turn off this feature for security reasons.)
To use scp with a different user name, you can append the user name with an @ character. For example, chris@toys.linuxtoys.net:/home/chris would attempt to log in as the user named chris to do the file copy.
The first time you connect to a remote computer using scp or ssh, those commands try to establish the authenticity of the remote host. If it cannot establish the host’s authenticity, it will display the RSA key fingerprint and ask you if you want to continue. If you type yes, scp will not question the authenticity of that computer again for subsequent scp commands.
However, if the RSA key fingerprint should change in the future for the remote computer (which will happen if, for example, the operating system is reinstalled on that computer), scp will refuse to let you connect to that remote computer. To override that refusal, you need to edit your $HOME/.ssh/known_hosts file and delete the entry for the remote computer. You can then verify the authenticity of the remote computer and continue to use scp.
Using the “r” commands: rlogin, rcp, and rsh
The rlogin, rcp, and rsh commands all use the same underlying security mechanism to enable remote login, remote file copy, and remote execution, respectively, among computers. These commands are included with Fedora Core to be compatible with legacy UNIX systems. Because "r" commands are inherently insecure, however, most people use ssh and scp commands to provide the same functionality in a more secure way.
| Cross reference: | For a description of these “r” commands, refer to the Red Hat Linux Bible Web site at Wiley Publishing: www.wiley.com/go/fedora3bible. |
EAN: 2147483647
Pages: 286