L0phtCrack
|
| < Day Day Up > |
|
At first, Windows systems seemed to offer improvements in password security over their Unix peers. Most Unix-heads could never create passwords longer than eight characters.
Windows NT boasted a maximum length of 14 characters, almost doubling the length! Then, Mudge and Weld Pond from L0pht Heavy Industries peeked under the hood of the LANMan hash. The company subsequently released a tool that took advantage of some inadequacies of the password encryption scheme.
We’ve already mentioned the LANMan hash quite a bit in this chapter. We know that it is the hashed representation of a user’s password, much like a Unix /etc/passwd or /etc/shadow file. What we’ll do now is take a closer look at how the LANMan hash is actually generated and stored. A Windows system stores two versions of a user’s password. The first version is called the LANMan, or LM, hash. The second version is the NT hash, which is encrypted with MD4, a one-way function—that is, the password can be encrypted, but it can never be decrypted. The LANMan hash is also created by a one-way function, but in this case, the password is split into halves before being encrypted with the DES algorithm.
Let’s take a quick look at the content of three LANMan hashes for three different passwords. They are represented in hexadecimal notation and consist of 16 bytes of data:
898f30164a203ca0 14cc8d7feb12c1db 898f30164a203ca0 aad3b435b51404ee 14cc8d7feb12c1db aad3b435b51404ee
It doesn’t take a box of cereal and a secret decoder ring to notice some coincidences between these three examples. The last 8 bytes of the second and third examples are exactly the same: aad3b435b51404ee. This value will appear in the second half of any hash generated from a password that is less than eight characters long. This is a cryptography gaffe for two reasons: It implies that the content of the password is less than eight characters, and it reveals that the generation of the second half of the hash does not use any information from the first half. Notice that the second half of the first example (14cc8d7feb12c1db) matches the first half of the third example. This implies that the password is encrypted in independent sets of two (seven characters) rather than the second half depending on the content of the first half.
In effect, this turns everyone’s potentially 14-character password into two smaller 7-character passwords. To top it off, the LANMan hashes ignored the case of letters, which reduces the amount of time to complete a brute-force attack by a factor of 10.
Implementation
L0phtCrack brought password cracking to the GUI-rich environment of Windows NT and its descendants, Windows 2000 and XP. Trying to pilfer passwords from Unix systems usually requires nabbing the /etc/passwd or /etc/shadow file—both easily readable text files. Windows stores passwords in the Security Accounts Manager (SAM)—a binary file that is difficult to read without special tools. Not only will L0phtCrack guess passwords, it will extract LANMan hashes from any SAM file, the local system, or a remote system, and it will even sniff hashes as they cross a network.
The SAM file resides in the \WINNT\system32\config\ directory. If you try to copy or open this file you will receive an error:
C:\WINNT\system32\configcopy SAM c:\temp The process cannot access the file because it is being used by another process. 0 file(s) copied.
Don’t give up! Windows helpfully backs up a copy of the SAM file to the \WINNT\ repair\ or sometimes the \WINNT\repair\RegBack\ directory.
L0phtCrack will extract passwords from the local or remote computers with the Dump Passwords From Registry option.
Remote extraction requires a valid session to the ADMIN$ share. This requires access to the NetBIOS TCP port 139. L0phtCrack can establish the session for you, or you can do so manually:
C:\>net use \\victim\admin$ * /u:Administrator Type the password for \\localhost\admin$: The command completed successfully.
It can also sniff LANMan hashes from the network. Each time a net use command passes the sniffing computer, the authentication hash will be extracted. You must be on the local network and be able to see the traffic, so its use tends to be limited.
The password cracking speed of L0phtCrack is respectable, but not on par with the latest versions of John. Nor does it offer the versatility of modifying rules. It does allow for customizing the character list from the Options menu.
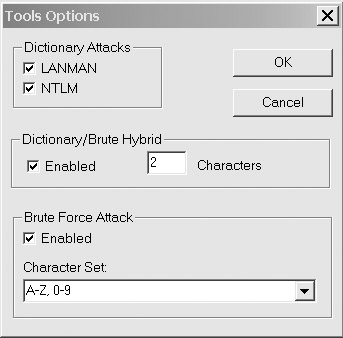
However, it’s usually best to use L0phtCrack to extract the passwords, and then save the password file for John to use—choose File | Save As.
You will need to massage the file for John to accept it. This involves placing the password hashes in the appropriate fields.
Here’s the L0phtCrack save file:
LastBruteIteration=0 CharacterSet=1234567890ABCDEFGHIJKLMNOPQRSTUVWXYZ ElapsedTime=0 0 Administrator:"":"": A34E6990556D7BA3BA1F6705936BF461: 2B1437DBB1DC57DA3DA1B88BADAB13B2:::
And here’s the file for John the Ripper. Note that the first three lines have been removed and there is only one field between the username (Administrator) and the password hash. The content of this field is unimportant to John, but we’ll put the user’s SID there as a reminder:
Administrator:500:A34E6990556D7BA3BA1F6705936BF461: 2B1437DBB1DC57DA3DA1B88BADAB13B2:::
Version 3.0 of L0phtCrack introduced improvements in the auditing ability of the application. Although it is easier for administrators to use and it’s geared toward their needs (such as the option of reporting only that a password was cracked rather than displaying the result), we prefer to use L0phtCrack 2.52 to grab passwords and use John the Ripper to crack them.
Using L0phtCrack version 3.0 has its advantages. Pure Windows 2000 domains can have accounts with 15-character passwords. This effectively disables the LANMan storage. Consequently, version 2.5 will report “No Password” for both the LANMan and NTLM hashes for any account with a 15-character password. Version 3.0 will correctly load and identify accounts with 15 characters. If you ever find a hash such as this,
AAD3B435B51404EEAAD3B435B51404EE:FA95F45CC70B670BD865F3748CA3E9FC:::
then you have discovered one of these “super passwords.” Note that the LANMan hash contains our friendly AAD3B435B51404EE null value repeated twice in the LANMan portion of the password (in boldface).
The other advantage of L0phtCrack version 3.0 is its ability to perform distributed cracking. Its method breaks up the brute-force guesses into blocks. This is a significant advantage for running it on heterogeneous systems and tracking the current status.
Protecting Your Passwords
Strong network and host security is the best method for protecting passwords and the password file. If a malicious user can grab the password file or the password hash for a Windows system, statistically speaking, it is only a short matter of time before the majority of the passwords are cracked. However, tools like John the Ripper and L0phtCrack cannot handle certain characters that Windows accepts as valid.
Several ALT-number pad combinations produce characters that will not be tested by current password crackers. To enter one of these combinations, remember to use numbers from the number pad. For example, the letters p-a-s-s-w-ALT-242-r-d (which spells passwòrd) will remain safe until someone updates the password cracking tools. Plus, the additional characters made available by the ALT-nnn technique vastly expands the brute-force key space.
| Tip | The ALT combinations for special characters start at 160 (AL+T+160) and end at 255. |
Removing the LANMan Hash
A benefit that Windows XP and Windows 2000 Service Pack 2 provided for security-conscious administrators is a registry key that removes the LANMan hash storage of a user’s password. Remember, the LM hash is the weak version of the user’s password that ignores the difference between upper- and lowercase characters. You could create a 15-character or longer password, as noted in the discussion of the L0phtCrack implementation. Or you could set the following registry key to instruct Windows not to store the LANMan hash for any later password change:
HKLM\SYSTEM\CurrentControlSet\Control\Lsa\NoLMHash
The NoLMHash value is a REG_DWORD that should be equal to 1. This will break compatibility with any Windows system in the 9x or Me series, but 2000 and XP will fare quite nicely. Once you’ve set this value, make sure to have all users change their passwords so the new setting will take effect. If setting this registry value doesn’t sound like it adds much more security for your passwords, consider this: The difference in key space for an eight-character password (and the amount of time it would take to brute force a password) between the LANMan hash and the MD4 hash is far greater than a factor of 1000! In other words, there are roughly 69^7 combinations for the LANMan hash (remember, an eight-character password is really a seven-character password plus a one-character password) and 96^8 combinations for the MD4 hash.
Anti-virus software may flag L0phtCrack as dangerous. This is because it is both a useful auditing tool for system administrators and an equally useful tool for malicious users who install it without permission. You may find files with .lc extensions, which is a good indicator that L0phtCrack has been there. If the tool has actually been installed on a system, as opposed to being run off of a floppy, you can perform registry searches for l0pht. Let's run through a few checks that a system administrator would make after discovering that the workstation of a temporary employee has been accessing the ADMIN$ share on the network's PDC.
We'll gloss over several steps, such as seizing data and finding out what commands have been run. Instead, we're concerned about our network's passwords. With more than 600 employees in the company, we might want to consider every password as compromised, but if we're looking for direct evidence that the inside user has been cracking passwords, we need to look for some key data. The most obvious entry that shows that L0phtCrack has been installed on the system is its own registry key:
HKLM\SYSTEM\Software\L0pht Heavy Industries\L0phtcrack 2.5
Unfortunately, this key is not present on the system. Other indicators show that L0phtCrack was installed. One key is related to the packet capture driver it uses for sniffing LANMan hashes:
HKLM\SYSTEM\CurrentControlSet\Service\NDIS3Pkt
Other programs may set this key, but the correct value that these programs set will be the following (note the case):
HKLM\SYSTEM\CurrentControlSet\Service\Ndis3pkt
The NDIS3Pkt key exists, so we can start to suspect that L0phtCrack has been installed. The wily insider may have tried to erase most of the tool's presence, even going so far as to defragment the hard drive and write over the original space on the disk to prevent forensic tools from finding the deleted data on the hard drive. However, Windows stores another entry for the uninstall information for L0phtCrack. Even if L0phtCrack has been uninstalled, the following registry key remains:
HKLM\SOFTWARE\Microsoft\Windows\CurrentVersion\Uninstall\L0phtcrack 2.5
If the system administrator finds this in the registry, she can be 100 percent sure that L0phtCrack had been installed on the system at some point in time. Next, the administrator could search the “most recently used” (MRU) values in the registry for files with a .lc extension. Even if the user deleted sam_pdc.lc from the file system, references to it could still exist in the registry!
|
| < Day Day Up > |
|
EAN: 2147483647
Pages: 189