Brute Force Attacks
| < Day Day Up > |
| When most people think of web hacking, they think of breaking into accounts on websites. However, there is no real easy way about this other than just guessing passwords. You can do password guessing manually, where you attempt passwords that you think a person might use, or automatically through a software utility.
Software utilities rely on two techniques:
Dictionary attacks require the use of a dictionary file containing words (and often combinations of common words and numbers like password123) that the utility uses to guess passwords on websites. Brute force attacks take longer because they check every possible sequence of numbers, letters, and special characters. You can perform web authentication in two ways:
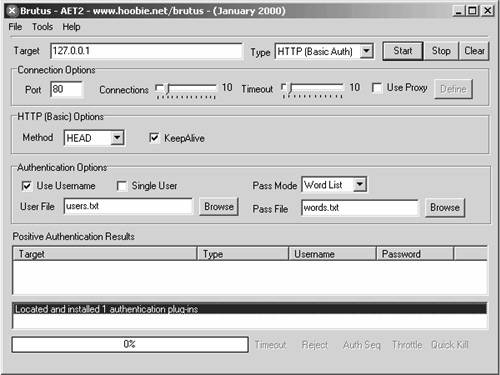
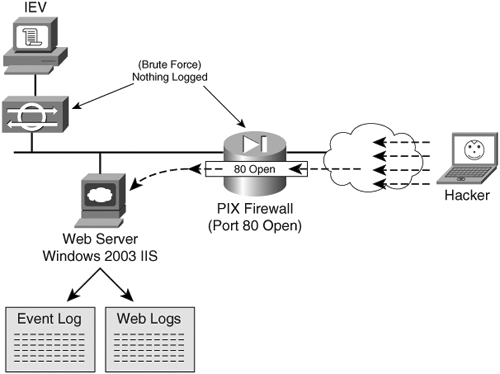
As a penetration tester, you will come across both types of authentication. The former type, basic authentication, is commonly found on network devices, such as with the Cisco Visual Switch Manager (VSM), which runs on Catalyst switches. The second type, form-based authentication, is more commonly found when authenticating into websites where account information is typically stored. Knowing the type of authentication used is important because it dictates what type of utility to use for attempting to crack logon credentials. Two common utilities for web-based password cracking are Brutus and HTTP Brute Forcer by Munga Bunga. BrutusBrutus is a powerful yet free password cracker that runs in Windows. You can download it from http://www.hoobie.net/brutus/. Brutus runs a brute force attack (called a custom attack) at about 30,000 attempts per minute against HTTP basic authentication, HTTP forms, FTP, POP3, and Telnet. (See Figure 7-18.) Figure 7-18. Brutus One of the advantages of Brutus is that you can change the number of connections and timeout values. Many sites begin to block your connection if they see many connections from a single IP address or multiple authentication attempts within a short period of time. Changing these settings aids in going undetected. HTTP Brute ForcerYou can find HTTP Brute Forcer utility by Munga Bunga at http://www.hackology.com/html/mungabunga.shtml. One of the advantages of HTTP Brute Forcer over Brutus is that it allows a more customized approach to brute force cracking through the use of definition files. Although Brutus has .bad files that allow some customization, Brute Forcer allows for greater flexibility. You can download numerous Brute Forcer definition files off of the Hackology website. Example 7-15 demonstrates a definition file for Hotmail. Example 7-15. Hotmail Definition File' Hotmail.com .def file -={ Updated }=- ' This definition file was written by JeiAr 7/26/2001 ' comments,questions,whatever can be sent to coolbreeze1979@hotmail.com ' Thanks to michelle,hackology.com and munga bunga for writing such a great prog. :) ' Works kinda slow, but if you can find a hotmail.def that works faster let me know login? sbox https://lc1.law5.hotmail.passport.com/cgi-bin/dologin &domain=hotmail.com &passwd=strPassword &submit=enter &curmbox=F000000001 &login=strUsername &ishotmail=1 &reauth=yes &sec=no &rru= &_lang=EN &js=yes &id=2 &fs=1 &cb=_lang%3dEN &ct=996103701 &svc=mail &beta=Caution Be careful when downloading these programs from other locations than those mentioned, because malicious hackers have modified these programs to include viruses and provide them for download on other sites. Always be sure to run a virus scanner on this program before executing it. Detecting a Brute Force AttackBrute force attacks can be relatively easy to launch with tools such as Brutus and easy to detect, too. During testing by the authors, Cisco IDS and Cisco PIX Firewall failed to make any significant type of detection while brute forcing an HTTP Basic Authentication on a 2003 IIS web server. See the network testing in Figure 7-19. Figure 7-19. Web Server Network Because Cisco IDS failed to detect such an attack, you have to look deeper into the web server. There, the Windows Security Event Log is helpful if it has been enabled. It displays thousands of failed login attempts with Event ID 529. (See Figure 7-20.) Figure 7-20. Windows 2003 Event Viewer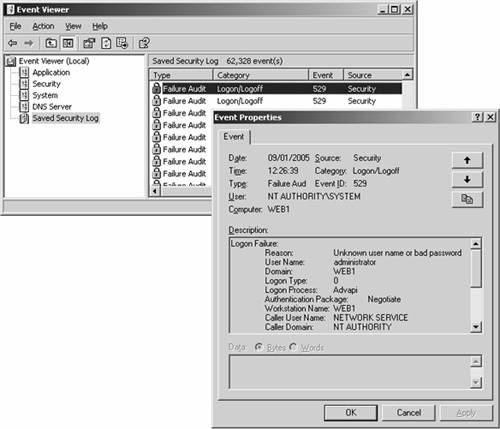 The next place is within the IIS logs typically at C:\windows\system32\logfiles\w3svc1. (See Figure 7-21.) Figure 7-21. IIS Web Server Log Files Location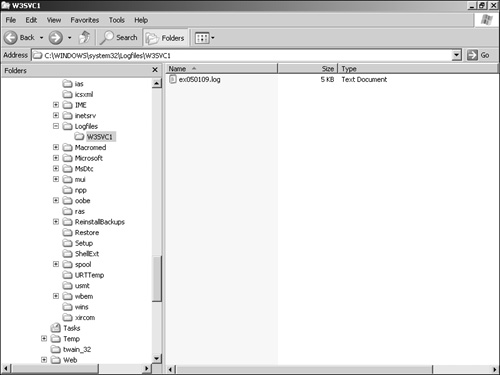 The text-based log files display hundreds or thousands of 401 errors, which translates into a failed login attempt. Most systems experience failed logons; however, when you see hundreds or even thousands within a short period, you should start to suspect the intent of the user, or hacker. (See Figure 7-22.) Figure 7-22. IIS Web Server Log Files Showing Attack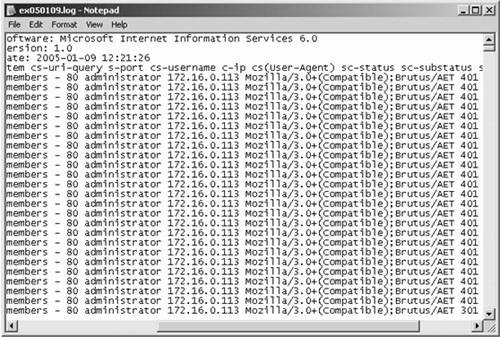 Finally, Figure 7-23 displays what the hacker will eventually see on Brutus. A successful password match was found, and in this case only 3124 attempts were needed. Figure 7-23. Success with Brutus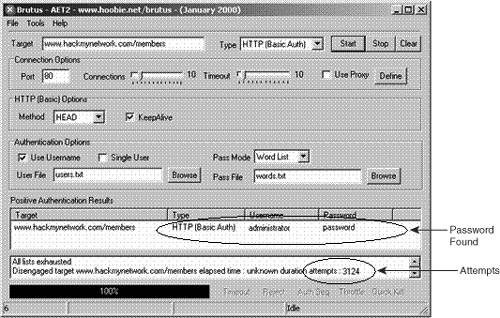 Protecting Against Brute Force AttacksProjecting against brute force is difficult in most cases. The simplest way is to implement account lockout policies. When sites are using basic authentication, all logon checks are made against the SAM database within Windows (or Active Directory in domain configurations). Simple settings of account lockout after five attempts definitely minimize the success rate of brute forcers. You can find these settings in the Administrative Tools\Local Security Policy on local systems. (See Figure 7-24.) Figure 7-24. Account Lockout Policies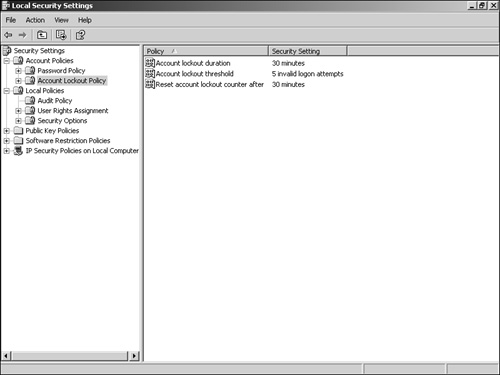 Form-based authentication provides another level of difficulty for brute force attacks. You have to involve the website developers to customize their code to include a form of lockout attempt. These definitely assist in preventing the guessing of brute forcing passwords. However, this comes at the cost of DoS attacks. If someone uses Brutus against your system and you lock out accounts after five attempts, the normal user who wants to log in has now been potentially denied access to her own account should she exceed five attempts. Like all things with security, there is tradeoff, so implement these measures with caution. Another method for protecting against brute force attacks is to monitor the log files for logon failure activity and then manually implement blocking or filtering at the firewall level or within IIS. By preventing the IP address from reaching the web server, you can effectively stop the hacker. However, yet again this tool is at a cost. If multiple users are behind a NAT or Proxy server, blocking the IP address might invoke a self-inflicted DoS of every user behind that IP address. As you can see, preventing brute force attacks can be quite touchy for website administrators. Even if the hacker is detected, it can be difficult to shut him down. In most cases, account locking and IP blocking can have a positive effect if they are time-based. For example, if 172.16.0.113 if found to be brute forcing the website, block the IP address for 30 minutes. If it happens again, block it again. Eventually, you should contact the ISP about the activity. |
| < Day Day Up > |
EAN: 2147483647
Pages: 209