E-Mail Impersonation
| < Day Day Up > |
| Appearing in person and using the telephone are not the only two methods of impersonation. E-mail is also a viable means of extracting information from unsuspecting people. It is easy to send a spoofed e-mail with the sender address being whatever you want it to be, as demonstrated in the following example: From: Visa Credit credit@visacredit.com To: xxxx@hotmail.com Date: Wed, July 5th, 2005 04:11:03 -0500 Subject: Visa Credit Check Reply-To: Visa Credit Service credit@visacredit.com Received: from mx.chi.a.com (mx.wash.a.com[10.1.2.3]) by mailserver1.wash.a.com with SMTP id A93AABVQ35A for xxxx@hotmail.com (sender thief@hackmynetwork.com); Wed, July 5th, 2005 03:09:01 -0500 (EST) X-Mailer: Microsoft Outlook Express 6.00.2800.1158 MIME-Version: 1.0 Content-Type: text/html; charset=iso-8859-1 Content-Transfer-Encoding: 8bit X-Priority: 3 (Normal) X-MAIL-INFO: 4316792387897d34b9877 X-ContentStamp: 2:3:1818012451 Return-Path: thief@hackmynetwork.com Message-ID: < A93AABVQ35A@mx.chi.a.com> The best way to explain why spoofed e-mails are important to use in testing is to show an example of how they can be used maliciously. Start by creating an e-mail with a spoofed e-mail header. Included within this e-mail is a message that says the following: Importance: HIGH We hope you are enjoying Microsoft Hotmail services. Due to recent security concerns, we are upgrading all of our servers using a new authentication mechanism. This will require all users to change their passwords. The new authentication mechanism will take place December 1, 2005. All subscribers who have not changed their passwords using the hyperlink below will not be able to access Hotmail services. 1. You will need to change your e-mail password by May 31, 2005. To do so, please log in at this URL: http://www.microsoft.com/passport/hotmail/login.asp@333868852/ login.asp and change your password under PASSWORD. 2. Please allow at least 5-6 minutes for your account to register the password update. 3. If you face any login problems due to this password change, please try the process again later. We apologize for any inconvenience this may have caused. We hope you understand that we are making this change for your benefit and that it is part of our continuous efforts to improve Microsoft Hotmail services. Sincerely, Bob Smith Executive Director of Hotmail Security Microsoft Hotmail Support http://www.microsoft.com After the e-mail recipient clicks the link contained in the e-mail, he is directed to the website shown in Figure 4-2. The recipient then enters his logon name and password, but instead of sending that information to Microsoft, the information is e-mailed to you. Figure 4-2. Website to Extract Password Information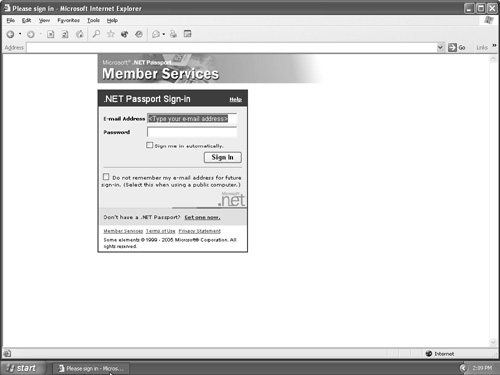 It works like this: First, use an e-mail spoofer program to create a bogus e-mail. Send the e-mail to the recipient with an official-sounding message like the one listed in the previous example. Be sure to make up an e-mail signature that sounds authentic. Simply signing the preceding message as Bob Smith would probably cause many to be suspicious of the e-mail. Signing it with a title, company name, and hyperlink makes it sound more official. Next, include in the link a base-10 encoded URL that redirects the user to your website. In the preceding example, the URL is http://www.microsoft.com/passport/hotmail/login.asp@333868852/login.asp. The base-10 encoded link is contained after the @ symbol. When you use an @ symbol, everything contained before it is ignored. In this example, then, the initial part of the link is an authentic link to the Microsoft Hotmail service, but the @ symbol causes the web browser to ignore it and be sent to the real URL of 333868852/login.asp. To create an encoded URL, begin with the IP address. In this example, the recipient is sent to the website located at IP address 19.230.111.52. To encode this IP address, do the following:
This total becomes the base-10 encoded URL of http://333868852. So instead of going to the Microsoft website, the recipient is sent to http://333868852/login.asp. Now create a web page that appears just like the one on the real website. You can download the original website contents using web crawler software like WinHTTrack Website Copier. (See Figure 4-3.) Modify the site source code so that the Submit button sends the form contents to a location on your web server or is e-mailed to your account. Figure 4-3. WinHTTrack Website Copier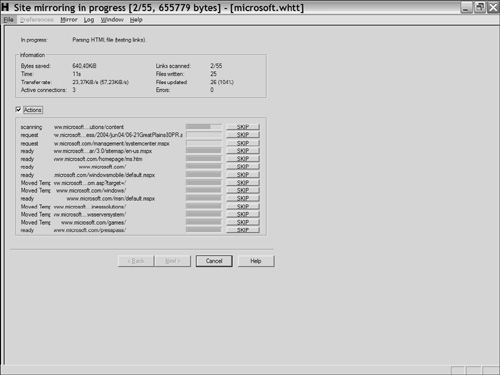 Alternatively, you can register a site with a similar sounding title. For example, you can send users to http://WWW.YAH00.COM. At first glance, this looks like the website managed by Yahoo. Giving it a closer look, however, you see that it is using zeroes in the name and is not the popular Yahoo web portal. This process of sending e-mails that ask recipients to go to spoofed websites is called phishing. According to a 2004 Internet Identity survey (http://www.internetidentity.com/), ten percent of all e-commerce sites have "brand spoofing" websites that can be used by social engineers who are doing phishing scams. Phishing is difficult to protect against. Most of the time phishing scams are sent to home customers, not corporate accounts. Unfortunately, even though the original company is not responsible for the scam, it does cause bad publicity and can result in fewer customers. The best defense for a website is to post warnings of such scams on the company website to educate customers of their existence. A second type of e-mail social engineering attack is to send malware attachments. Malware is malicious software such as viruses or Trojans. The e-mail subject line should contain something that catches the attention of the recipient, such as, "I missed you," or "Check this out." In the past, viruses have been sent containing such messages as "I love you" or "Naked picture of Anna Kournikova attached." The recipient then launches the attachment, which spreads the virus or installs the Trojan horse. Note A Trojan horse program is a small malicious software application that comes disguised as something useful. An example is the BoSniffer program, which operated under the pretext of security scanning software. BoSniffer advertised that it would scan a system for the Back Orifice 2000 software, which is used by malicious hackers to gain complete access to a system undetected. Although the BoSniffer program seemed legitimate, if it did not find Back Orifice installed, it would install it discretely and announce it to the Internet Relay Chat (IRC) channel #BO_OWNED. The name "Trojan horse" comes from the story of the Trojan War, where the Greeks were able to conquer the protected city of Troy by hiding themselves in a giant horse that was offered as a gift to the king of Troy. One popular virus, called the NakedWife virus, was propogated with the e-mail subject line reading "NakedWife" and the body text reading, "My wife never look [sic] like that :-)." Upon the recipient opening the attachment, a virus would be installed that would begin deleting files on the hard drive of the recipient. Then it would send itself to contacts in the Outlook Address Book. This, in turn, would make it look like the recipient of the virus was the sender so that when the next person received the e-mail, he would see it coming from someone he knew, such as a friend or business contact. Another scam is to inform someone that he has won a prize. Although this can be done via e-mail, many are skeptical of these types of e-mail messages. Instead, if you send the message through postal mail, using letterhead stationary, most people would believe it. Include in the message a website or e-mail address that the recipient needs to contact to claim the prize. State in the message that all the person has to do to receive this prize is provide you with his name, address, and credit card number to pay for shipping. Penetration testers can be hired as part of an employee awareness program. By sending phishing e-mails or other types of scam messages, they can assess if the employees of an organization are aware of such tactics and how they are responding to them. |
| < Day Day Up > |
EAN: 2147483647
Pages: 209