Setting Up Session Authentication
| The basic steps for setting up Session Authentication are similar to the steps described in the previous section for setting up User Authentication.
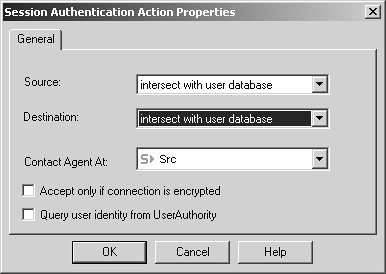
The source and destination for the rule are defined in the same way as shown in the preceding section. A Session Authentication rule might look like the one shown in Figure 8.34. Figure 8.34. Sample Session Authentication rule You then configure the Session Authentication action properties by right-clicking Session Auth and selecting Edit Properties. A screen similar to the one shown in Figure 8.35 appears. Figure 8.35. Session Authentication Action Properties, General tab The Source and Destination fields are defined as they were for User Authentication. The Contact Agent At field tells FireWall-1 on which host to attempt to contact a Session Authentication agent. The possibilities are as follows .
Two other options are also available on the General tab.
Once the rules are set up to your liking, verify that the Authentication Failure Track is set appropriately in the Policy Properties Authentication tab, and install the security policy. NOTE!
|
EAN: 2147483647
Pages: 143