| The previous two chapters discuss how to make Web services interactions reliable in the presence of failures. WS-ReliableMessaging and supporting middleware isolate applications from lost and duplicate messages, which might be caused by network errors. WS-Coordination, WS-Transactions, and WS-BusinessAgreement allow Web services to agree on the outcome of multiparty interactions. This chapter will show how to make Web services reliable even when the network, the Web service, or both are under possible security attacks. For example: The network traffic might be eavesdropped upon. An involved party might tamper with messages or attachments. For example, this party might send a message that includes portions of another message, in an effort to gain access to otherwise unauthorized information. An involved party might construct and send fake messages to a receiver who believes them to have come from a party other than the sender. An attacker might pose to the real sender and receiver parties as receiver and sender, respectively, in order to fool both of them. For example, the attacker might be able to downgrade the level of cryptography used to secure the message. An attacker can start a denial-of-service (DOS) attack, in which the attacker does a small amount of work that forces the attacked system to do a large amount of work. This is an important issue in design, and perhaps profiling in some cases.
Web Services Security (WS-Security) is a family of specifications that addresses these concerns. The family has many specifications, as shown in Figure 12-1. Figure 12-1. Web Services Security architecture. 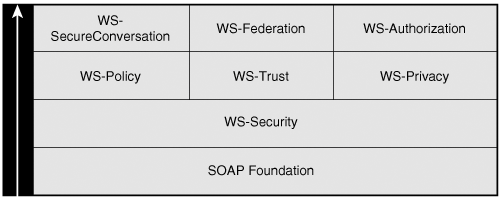
Security is a complex topic that is fundamental to the adoption of Web services. This chapter discusses the most fundamental layers of WS-Security: WS-Security SOAP Message Security 1.0 provides the foundation for security. This specification supports the following: Origin Authentication Identifying the origin of a message securely. Integrity Detecting that no one has tampered with information in a message. Confidentiality Ensuring that only the intended recipient of information is able to view it.
WS-Trust Trust is fundamental to security, and security only works because of trust relationships. Public key security works only if the certificate authorities are trusted and trustworthy. Kerberos works only if the Kerberos Key Distribution Centers and services are trusted and trustworthy. WS-Trust is a specification that enterprises and sites use to build trust relationships and interoperability. This chapter briefly discusses WS-Trust; the following chapter provides more details.
Chapter 13, "Advanced Security," discusses the other members of the WS-Security family. These specifications provide enhanced security functions, building on the foundational WS-Security specification. Before delving into the details of WS-Security, let's look at a simple scenario that motivates the security function introduced by WS-Security. This scenario will be used in the detailed explanations in this and the following chapter. |
