Process Injection
When a Windows application is loaded into memory, all of the required external functions located in Dynamic Link Libraries (DLLs) are loaded into the same memory space. These external functions are mapped into memory as if they were an integral part of the application. The kernel function responsible for this mapping is ZwMapViewOfSection.
Once ZwMapViewOfSection has been hooked, the mapping of Dynamic Link Library functions can be altered. Because every function added while loading a DLL must be copied to the memory space of the calling process, replacement functions will also need to be injected into this memory space - hence the term process injection. Figure 4-1 shows the ZwMapViewOfSection.
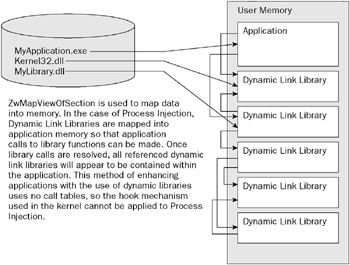
Figure 4-1
Professional Rootkits (Programmer to Programmer)
ISBN: 0470101547
EAN: 2147483647
EAN: 2147483647
Year: 2007
Pages: 229
Pages: 229
Authors: Ric Vieler