GhostTracker
The GhostTracker form, shown in Figure 12-2, contains a single list control that is filled with the IP addresses of connecting rootkits. Double-clicking any of these list entries will bring up the control panel for that rootkit. This is not the main page of a commercial rootkit controller; it is an example to show remote control operations - hence, the stark simplicity of the design.
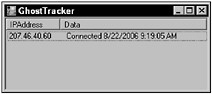
Figure 12-2
Professional Rootkits (Programmer to Programmer)
ISBN: 0470101547
EAN: 2147483647
EAN: 2147483647
Year: 2007
Pages: 229
Pages: 229
Authors: Ric Vieler