Chapter 1: Cisco and the Internet
The Internet is amazing. There's just no other word to describe a technology that few had even heard of 20 years ago, yet now dominates so much of our collective consciousness. The gold fever surrounding the Internet makes the 1849 California gold rush seem insignificant in comparison. You've no doubt heard the analogies and the clichés-the Internet is the fastest-growing market in history; the fastest-growing technology in history; the first truly global, real-time marketplace of goods, services, and ideas. The Internet has and will continue to bring profound change to all sectors, from business to education to entertainment. The Internet is the information superhighway-that's our road to the future.
INTERNETWORKING
The most surprising thing about all the breathless Web hype is that most of it's true. Most research houses estimate Internet growth at about 18 percent annually. In fact, it's said that we reached the 1 billion user mark sometime in 2005 and are looking at a doubling of fellow Internet users during the next decade. The number of registered Internet domain names more than doubles annually. There are now billions of Web pages, up from a just a million of them a scant 15 years ago. In 2005, advertisers spent an estimated $150 billion on Internet-based ads. A thousand American households sign up for Internet access every hour. No matter how tired we are of hearing this litany, the numbers are awesome.
Although most press coverage dotes on visible technologies, such as browsers and cellular Internet phones, the real action is in Internet infrastructure. Billions are being invested by serious players who foresee a day when virtually all mass media-radio, telephone, and television-converge onto the Internet. This convergence will use the Internet as a single "pipe" through which virtually all communication will travel. There's disagreement about whether the Internet pipe will run over wireless devices, telephone lines, cable TV wires, or even satellites. In fact, it seems that for the time being, it's all of the above. However, battle lines are being drawn every day by a multitude of businesses, and a lot of money is being invested. The bets are large, because winning the Internet infrastructure game promises untold riches.
But there's trouble in paradise. As more people have hopped onto the bandwagon, the diameter of the pipe-called bandwidth, a measure of how much data can be moved over a link-has come under increasing scrutiny. New users and bigger applications are chewing up bandwidth as fast as additional network equipment can be added to the Internet's infrastructure-the global maze of telecommunications links and internetworking devices that makes it all go. Let's face it; with all of the advances, the Internet can still be slow, can't it? The Internet has undergone perennial bandwidth scares, with pundits worrying that additional loads finally may bring the whole thing to a grinding halt. That hasn't happened yet, but a huge amount of money and attention is focused on Internet infrastructure.

Users connect to servers over this Internet infrastructure, yet few are aware of how it works. Bandwidth isn't just a matter of telecommunications media running over highspeed, fiber-optic cable. The networking devices sitting at each end of the cables are every bit as important. In many situations, the speed of these devices is as big a factor in the Internet's bandwidth as telecom media.
This book surveys internetworking's infrastructure from the ground up, starting with underlying technology, up through the product level. If you're a beginner, read this book and you'll know the basics of internetworking. It's written from the perspective of the premier manufacturer of internetworking technology, Cisco Systems. Because the technologies are covered generically, you'll understand the systems and components needed to make any internetwork run, not just one built from Cisco products. But make no mistake; this book is about infrastructure-that is, about the devices over which internetworks operate:
-
Routers These devices route data between networks, like local area networks(LANs), wide area networks (WANs), and metro area networks (MANs). Routers put theinter in internetworking; without them, the Internet would not be possible. Routers use Internet Protocol (IP) addresses to figure out how to best route packets through internetworks.
-
Switches These devices also forward data on and between LANs, and have replaced the hub as the de facto standard for connecting workstations and servers to the network. Switches are faster than routers, but most don't look high enough in the stack to see or use IP addresses and, therefore, don't have the capability routers do for finding paths through large internetworks. There are, however, switches that incorporate routing-they are commonly referred to as "Layer 3 switches," and we'll discuss them in more detail later.
-
Firewalls Although these can be understood simply as special routers that filter packets to secure data connections between internal and external networks, they are highly evolved security devices that examine communications between devices at many layers and then take specific actions or determine what to allow and what to block.
-
Access Servers These dedicated devices answer phone calls from remote users and connect them to the internetwork. Most access servers are used by Internet service providers (ISPs) to connect home users and small businesses to the Internet.
Collectively, these devices make up the Internet's infrastructure. The only other major ingredient is telecommunications links to make WAN connections. In this book, we'll cover each device type as it exists within Cisco's product line and review WAN technologies also. Doing so (from the perspective of Cisco's product line) will give you a more detailed look at the inner workings of internetwork devices.
Cisco's Position in the Computer Industry
We all know that Microsoft Windows is, at this point, the world's most dominant computer operating system. But here's a pop quiz: Can you name the second most important operating system? Choose one:
-
MVS This is IBM's proprietary operating system used to run mainframe computers. MVS still has a stranglehold on the central corporate and government data centers that handle financial accounting and other sensitive transactions.
-
UNIX/LINUX There are actually about a dozen proprietary versions of UNIX from such computer manufacturers as Sun, HP, Compaq, Novell, and IBM. LINUX, the "new" kid on the block, has seen a boom in popularity. Nevertheless, "good old" UNIX is still the predominant server operating system in enterprise-class client-server applications.
-
IOS Short for Internetwork Operating System, this is Cisco Systems' proprietary operating system for its line of internetworking hardware.
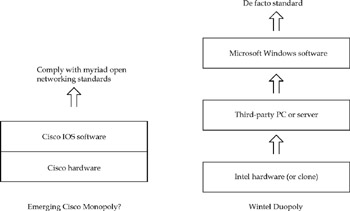
Since this is a Cisco book, this is sort of a loaded question. IOS is the second most-important operating system, and by a wide margin. We assert this partly because UNIX and MVS have both lost some of their edge-UNIX having lost market share to Microsoft Windows, and MVS, though still a mission-critical technology, having stopped growing altogether. However, the main reason IOS is so important is that Cisco has over an 80 percent share of the Internet router market, and the Internet is the fastest-growing market in history.
To put that in perspective, Cisco has about the same market share in router technology as Intel enjoys in Windows, orWintel, hardware platforms. The Wintel regime has been attacked as a monopoly by competitors and the U.S. Department of Justice. Not so with Cisco. IOS is their proprietary operating system architecture, and it runs on their hardware only. This means that Cisco's market leadership garners both hardware and software revenues and gives the company total architectural control over its products.
Cisco's present position has its strengths and weaknesses compared to the Wintel duopoly. On the negative side of the ledger, Cisco products are largely used to run truly open-standard protocols, which reduce the extent to which they can leverage product architecture to assert market control. Cisco doesn't widely freeze any competitor out of design cycles to prepare products that implement emerging technologies, because the technologies implement open standards. On the positive side, Cisco is a single company that makes its own products. This contrasts favorably to Wintel, a pair of companies that rely on hundreds of PC manufacturers to deliver their respective products to a highly fragmented market.
Financially speaking, by the turn of the millennium, Cisco was riding a gravy train with biscuit wheels. Even though you could mention the company name to someone and they couldn't tell Cisco from Crisco, chances are some part of their life was touched by a Cisco product. Maybe their computer network at work utilized Cisco gear; maybe the ISP they used for Internet connectivity relied on Cisco gear. But the fact of the matter is that at one point in history, Cisco was the most valuable company on the face of the planet. In March 2000-less than two decades after the company was founded-the company reached a value of half a trillion dollars.
More than a year later, however, all that changed. When the dot-com bubble burst, Cisco fell hard. Many companies no longer needed Cisco's gadgets, and by spring of 2001, Cisco faced a $2 billion write-off. From its leadership position, with stocks trading at a high of $146 per share in March 2000, the stocks dipped to a low of a little more than $8 per share in October 2002. Though Cisco fell, it didn't fall as hard as those companies that had to close up shop. Cisco has hung in there and has made a steady climb back to profitability. At the beginning of 2006, Cisco stock was trading at around $20 per share and second quarter revenues topped $6.6 billion. The upshot of this lesson in finances? Cisco was down, but they weren't out.
This book is not an endorsement of Cisco, however. Like any industry powerhouse, the company has its faults and is duly criticized in these pages when appropriate. But whether you're an individual mulling a career move or a manager weighing your company's Internet strategy, learning how Cisco technology works is your best possible introduction to the world of internetworking.
The Internet Landscape
The Internet isn't a single technology: it's a collection of related technologies that make internetworking possible.
-
Physical media From connectors to high-speed, fiber-optic cables, the physical links that connect everything together are the foundation of networking.
-
Network technologies LAN protocols run what happens over the wire. The best known is Ethernet, but there are other important ones.
-
TCP/IP The Transmission Control Protocol/Internet Protocol is what binds the Internet together. IP handles addressing, and TCP handles messaging. Also included in the Internet Protocol suite is User Datagram Protocol (UDP) which is used to send faster and timelier datagrams in a network. Internet Control Message Protocol (ICMP) is another component that is used to send error messages in a network.
-
Operational technologies Internetworks rely on a number of underlying standards and protocols to operate themselves, without which internetworking wouldn't be practical.
-
Application protocols Network applications define the kinds of useful tasks internetworks can do, from file transfers to Web page downloads.
To engineer its products, the networking industry uses a seven-layer architectural guideline called the Open Systems Interconnection (OSI) reference model. It's no coincidence that the preceding list of enabling technologies more or less adheres to the OSI model, from the physical level up.
Before we proceed, a quick word to make sure our terminology is clear: theInternet is a global interconnection of individual internetworks. Aninternetwork is any collection of local area networks (LANs) under a single administrative regime-usually an enterprise or an ISP (Internet service provider). A private internetwork is mechanically the same as the open Internet. Ahost is a user device, such as a PC, server, mainframe, or printer. Adevice is a piece of networking equipment, such as a router. The generic termsnode andstation refer to both hosts and devices. ALAN segment is a network medium that hosts a share. Anapplication protocol is a software standard that operates such things as Web browsers, filetransfers, e-mails, and other useful functions. Anintranet is an internal internetwork operating as a private Web, with enterprise applications software used through Web browsers instead of a more traditional graphical user interface (GUI), such as Microsoft Windows.
From a technical standpoint, private internetworks are composed of the same pieces as the Internet itself. The only thing that distinguishes the Internet from a large internetwork is its openness.
Internetworking's Four Major Device Types
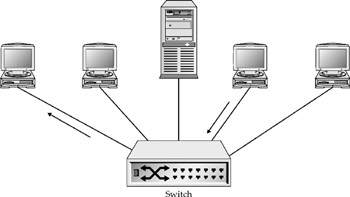
Aswitch connects hosts to the internetwork, much like a hub. However, switches are fundamentally different in that they form a virtual circuit between the sending and receiving hosts. In other words, the switch's bandwidth is reserved for a single switched connection between two hosts as if it were 100 percent dedicated to that virtual circuit. Switches are able to do this by using better electronics than those used by hubs to "slice" bandwidth time into slivers-called channels-large enough to service each switch port. Switches have almost all but replaced hubs.
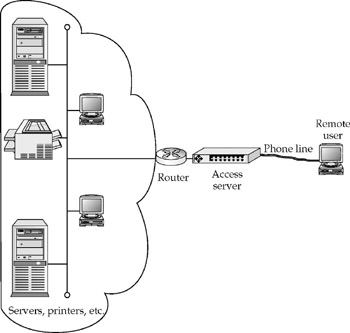
Anaccess server is a specialized device that, stated roughly, acts like a modem on one side and a hub on the other. Access servers connect remote users to internetworks. The majority of the millions of access server ports in the world are operated by ISPs to take phone calls from Internet subscribers. Some perform more specialized functions, but the access server's main purpose is to connect remote dial-in users to an internetwork. These servers often provide analog connectivity to the network.
Arouter is an intelligent device that forwards traffic based on the IP address of a message. Whereas switches have ports into which individual hosts plug, routers have interfaces to which LAN segments attach. In simple terms, a router's job is to move packets of data between attached LAN segments.
The router is the single most important type of device in internetworking. It provides the flexibility and decision-making power that make it possible to run complicated internetworks. Without the logical capability routers provide, the Internet would be hundreds of times slower and much more expensive. As detailed in the next chapter, internetwork architectures have seven layers: switches predominantly operate at layer 2, and routers at layer 3. Routers also have the capability to filter traffic based upon source and destination addresses, network application, and other parameters.
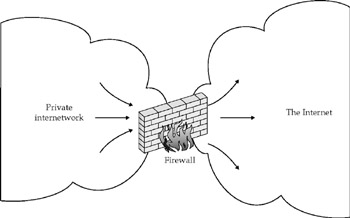
Firewalls are networking devices that act as checkpoints between an internetwork and the outside, filtering packets that don't belong in the network. They work by checking each packet for compliance with security policies they have been programmed to enforce. A firewall forms an intentional traffic choke point and persistently monitors internal/external connections for security compliance. Any enterprise connected to the Internet should have a firewall configured.
The most powerful firewalls have specialized hardware, but they don't have to. A normal router can be programmed to perform many duties of a firewall, although a dedicated firewall device is preferred in most instances. Firewalls are increasingly being used internally to safeguard assets from potential internal threats.
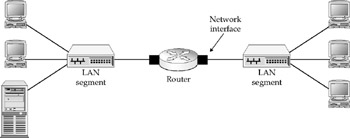
Basic Internetwork Topologies
Atopology is the physical arrangement of nodes within an internetwork. Usually, a topology is expressed as a logical map that graphically represents each node and the media links connecting the nodes. In fact, topology maps are used as the GUI through which most network management software tools operate. Figure 1-1 depicts the basic network elements that are combined in one way or another to make up internetworks.
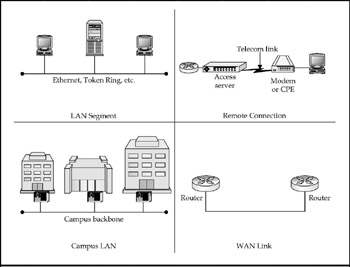
Figure 1-1: There are four basic elements to internetwork topologies
The LAN segment is the basic building block of internetworks. Put another way, LAN segments are the network units that internetworks link together. The Internet itself is a collection of millions of LAN segments. The reason we use the formal term LAN segment is that local collections of individual segments are commonly referred to as "LANs" even though, strictly speaking, they are actually local internet works. This may seem like nit-picking, but you'll be happy for the distinction in later chapters.
Remote connections use phone circuits, cable, and satellite signals to tiephysically removed hosts into the LAN segment. The telecom link can be anything from a regular analog voice line, to a Digital Subscriber Line (DSL), or cable-based broadband, and even satellite broadband-all now common technologies for small office/home office (SOHO) users.
The campus LAN is a double misnomer, but get used to it. Cisco uses it as a generic term to describe local enterprise internetworks. Most exist within a single building, not over an office campus, and all are composed of multiple LAN segments, not a single LAN. But campus LANs are distinguishable by the use of a high-speed backbone segment to interconnect the other local LAN segments. Most "heavy-duty" LAN backbones run over fiber-optic cabling.
WAN (wide area network) links are long-distance telecom links between cities, although some are strung across ocean floors to connect continents. Virtually all new WAN links being installed run over ultra-high-speed fiber-optic links. The current state of the art is still typically considered to be OC-768, with a data rate of 40 Gbps. (OC stands for optical carrier; Gbps stands forgigabits per second.) Slower WAN links run over technologies you've probably heard of-T1 andT3 (also called DS3), which run at 1.5 Mbps and 45 Mbps, respectively.
Internetwork Players
There is no "Internet network" as such. In other words, there is no separately owned dedicated trunk network operated under the auspices of some central management authority. The Internet is actually a free-for-all collection of individual networks bound together by two things:
-
Shared enabling technologies A complex of de facto standards and technologies that not only make the individual internetwork possible, but also enable internetworks to automatically interact with other internetworks.
-
Internet Protocol (IP) A globally accepted communication system that makes it possible to connect and exchange data with otherwise incompatible hosts anywhere on earth. IP unifies communication among virtually all computer systems into a unitary data format and addressing system.
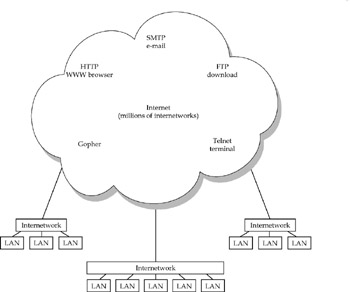
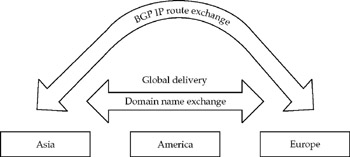
Figure 1-2 lays out approximately how the Internet is formed. The prerequisite is that users need to be on a network of some kind, and nowadays, in an office or plant, this usually means some type of Ethernet LAN. In the past, desktop protocols, such as Novell NetWare IPX and AppleTalk, used their respective protocols on Ethernet. Today, a vast majority of desktops and the networks they are on use the TCP/IP protocol over Ethernet.
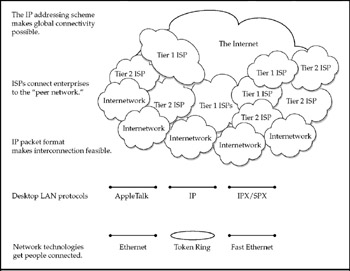
Figure 1-2: The global Internet is a layered collection of independent systems
ISPs play a central role in Internet connectivity for enterprises, not just for home users. Peer networking is the arrangement of traffic exchange between ISPs. From the Internet's standpoint, the key juncture is where you connect to the so-called peer network-a group of thousands of high-speed routers that pass IP routes and traffic among one another. Although some very large enterprises (big corporations, government agencies, and universities) have their own direct connections to the peer network, most tap in through ISPs.
Entry to the peer network almost always takes place through a high-speed fiber trunk line, usually controlled by so-called Internet backbone providers (IBPs), such as AT&T, MCI, and AOL. These IBPs are also called Tier 1 Internet service providers. They connect to each other by "peering" with each other. Peering is a set of agreed-upon connections that Tier 1 ISPs have with each other to exchange network traffic. These connections are usually ultra-high-speed (OC 198 fiber, etc.) and are done at multiple locations around the world known as peering points.
Tier 2 providers are the next level down. They don't peer directly at the backbone, but instead purchase access in "bulk" from Tier 1 carriers and then resell it to businesses, consumers, and other service providers. Most businesses and general consumers purchase their Internet connectivity through a Tier 2 carrier or a service provider that resells access.
Internetworking Protocols
Protocols are the key to internetworking. A networkingprotocol is an agreed-upon data format and set of rules for message exchange to govern a specific process. The Internet's two most fundamental protocols exist at the lower layers of the OSI model. These are the various network (or LAN) protocols and the IP protocol.
| Layer 3 | IP | Internetworking |
| Layer 2 | Ethernet, Token Ring, etc. | LAN segment media access |
Layers 2 and 3 are the primary focus of this book, because that's where Cisco and its competitors bring physical network infrastructures to life as internetworks. Layer 2 connects the host to its home LAN segment, and layer 3 interconnects LAN segments. (In case you're wondering, layer 1 covers cabling and other physical transport media.)
However, that's just the beginning of the protocol story. There are literally dozens of supplementary protocols, large and small, to do everything from checking whether a neighboring device is still running to calculating the best path to send packets to the other side of the world.
For example, consider the Session Initiation Protocol (SIP). SIP is an Internet Engineering Task Force (IETF) standard (RFC 3261) managing how voice, video, and data can exist on the same network. Most often, you'll see SIP at work as the protocol involved in Voice over IP (VoIP) technologies and devices. Because of this protocol, VoIP can be used on desktop computers, personal digital assistants (PDAs), IP phones, and other devices.
These supplementary protocols can be roughly divided into three groups:maintenance, management, and routing.
| Routing protocols | Best paths | Exchange updates, calculate the best current routes |
| Management protocols | Health and security | Monitor performance, trip alarms, reconfigure |
| Maintenance protocols | Housekeeping | Discover devices, trace routes, notify neighbors |
The maintenance protocols tend to be more proprietary (vendor-specific) the closer they are to the network device hardware. For example, the Cisco Discovery Protocol keeps track of devices-but only Cisco devices. The management protocols are more generic. However, Cisco is so big that they support the industry-standard protocols in addition to pushing their own proprietary security protocol. A third kind of maintenance protocols called routing protocols are what make large, complicated networks possible.
Routing protocols wring much of the labor and complexity out of very large networks by automatically tracking which routes to use between IP addresses. The Border Gateway Protocol (BGP) is the top-level routing protocol that connects everything within cities, between cities, and between continents. There are several other routing protocols used to track routes within private internetworks. Cisco supports industrystandard routing protocols in addition to pushing a couple of internal routing protocols of their own.
Routing vs. Switching
A few years ago, a technology war was waged between routing and switching. Hubs may have been trampled to death, but neither the switching nor routing camps can declare victory. As devices became less expensive and more powerful, switching emerged as a viable alternative to hubs on the low end and routers on the high end. Because switching is inherently faster, there was a push to replace routed networks with switched networks. The battle took place at both ends of the internetworking landscape. At the low end-called the access layer, because this is where hosts gain access to the internetwork-switches have replaced hubs as the device of choice to connect hosts because of switches' higher bandwidth. Switches have also displaced routers as backbones that connect LANs within a building or a campus. Layer 3 switches are able to perform the routing duties that a router would normally perform. Figure 1-3 shows the three different types of switching.
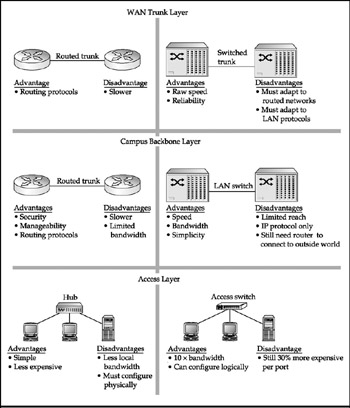
Figure 1-3: Switching is encroaching on hubs at the low end and routers at the high end
Switching has always been the norm over WAN trunks, such as the fiber-optic links Internet backbone providers operate between cities. In fact, voice telephone systems are switched networks built over permanent physical circuits in the form of the telephone cables running to businesses and homes.
Data switches, of course, don't have dedicated cabling-the switched circuits they create are virtual. That is, they create temporary logical (not hard-wired) end-to-end circuits that are set up and torn down on an as-needed basis. But nonetheless, data switches are inherently faster than shared networks. The phrase "switch where you can, route where you must" has emerged as the industry motto-the translation being that wherever possible, you should use access switches in place of hubs for host access and LAN switches instead of routers for internetwork connections.
Looking at Figure 1-3, you can see that the two technologies have their respective trade-offs. In a nutshell, routers are slower and more expensive, but are much more intelligent. Indeed, larger internetworks will never be able to entirely do away with routing functionality of some sort. Thus, the industry is seeing the melding of switching's physical layer speed with routing's network layer intelligence. Hybrid devices have been rolled out that incorporate some IP routing intelligence into hardware. These hybrids are variously called layer-3 switches, multilayer switches, and so on.
Other Internetworking Trends
Beyond the routing versus switching technology war, a number of other trends are afoot in the internetworking industry:
-
Network management A big push is under way to make large, complicated internetworks more reliable and manageable. Enterprises are adopting socalled management console or network management station (NMS) software products from which their network teams can centrally monitor and troubleshoot internetworks. These NMS consoles are being fed by a couple of established but still-developing network management protocols.
-
Network security To date, most industry effort has been on securing access to network packets. The trend now is turning toward encrypting their contents to virtually guarantee data security and integrity. Tight security requires a harsh trade-off in expense, performance, or both.
-
Virtual private networks (VPNs) Traditional leased-line WAN links are quickly being replaced by VPN links. VPNs use encryption to enable enterprises to operate private WANs over the Internet-at a fraction of the cost. Again, encryption exacts a trade-off in lowered performance. There are also reliability issues that must sometimes be dealt with.
-
Faster dial-in links Remote dial-in access technology to the home or small office is being upgraded by replacing plain old telephone line circuits with digital circuits. At one time, Integrated Services Digital Network (ISDN) looked like the answer, but now DSL and cable are viewed as the most likely way to travel the "last mile" from the local phone company switching office to the small office or home.
-
Faster WAN trunks Trunk lines running the Synchronous Optical Network(SONET) standard are advancing at a breakneck pace. The original 52-Mbps OC-1 has been improved over several increments to the present state-of-the-art 40-Gbps OC-768 standard.
-
Backbone technologies The campus backbone market has two highbandwidth network protocols to choose between: Asynchronous Transfer Mode (ATM) versus Gigabit Ethernet. ATM is a 622-Mbps non-IP standard that is ideal for multimedia traffic and has the ability to guarantee quality of service.
However, it must be adapted for use with Ethernet networks. As the name implies, Gigabit Ethernet is the 1,000-Mbps successor to the 100-Mbps Fast Ethernet specification.
-
IP telephony For years, conventional telephone lines have been used to facilitate WAN connections, or even the SOHO user, calling an ISP to log into the network. The street runs both ways, however. Thanks to IP telephony, computer networks can be used to transport voice calls. In essence, the calls are converted into the popular Internet Protocol (IP) and the packets sent across the network to their destination, where they are converted back into sound. A primary benefit of IP telephony is a cost savings-with a data network already in place, it's a simple matter to add an IP telephone system. IP telephony is nothing new-it's how telephone companies send calls between regional offices.
-
Wireless Conventional computer networks have had a major obstacle-computers having to be tethered to switches and hubs with Category 5 cabling. Obviously, this is not ideal in environments where mobility and computation must meet. The solution is wireless technology. This allows computers to be connected to the network, without having to be tied down with cabling. In recent months, wireless technology has taken impressive strides forward, allowing cable-free connectivity with increasing data rates.
-
Multimedia A half-dozen years ago, watching video and streaming music was really only a pipedream. Those with broadband connections could get it done, but it wasn't really prevalent. However, as broadband connections have increased in popularity, there is more multimedia content on the Internet. As such, there needs to be an effective, efficient way to give people the content they want.
-
MPLS Multiprotocol Label Switching (MPLS) has often been referred to as a key component of the "next-generation IP network." From a network perspective, MPLS is a packet-forwarding and switching technology. MPLS can interconnect to IP, ATM, Frame Relay, and other protocols, making it quite useful for wide area networks (WANs) and other networks. MPLS is built for speed and scalability, and supports robust quality-of-service (QoS).
These technologies and standards have all the internetworking industry vendors jumping. Smaller competitors have tended to focus on a particular niche and choose sides, betting that one technology will prevail over the others. The big players have the resources and clout to take a more agnostic view of things; this is true of Cisco in particular.
EAN: 2147483647
Pages: 102