| Earlier in the chapter, we examined how to use the Event Viewer to work with various log files. Most of the other log files, such as the Application and System log files, can be viewed by all users. However, the Security log can be viewed only by administrators. You can make various configuration changes to the Security log, the most important of which is to increase the size of the log. The default size is 16,384KB, which is sufficient for light logging in small- to medium-sized organizations but becomes quickly filled in larger organizations that perform a lot of auditing. Although we covered how to manually increase the size of the event logs earlier in the chapter, it would be time consuming to make this change on every server in your enterprise. To make the configuration of the event logs consistent on the computers in your organization, you can create an Event Log Settings policy. This policy can be created via the Group Policy snap-in. After the policy is configured, it can be applied to the desired computers just like any other policy. To configure the Security log size for all computers in the domain, perform the procedure outlined in Step by Step 16.9. Step by Step 16.9 Creating a Security log policy 1. | From the Start menu, click Start, All Programs, Administrative Tools, Domain Security Policy.
| 2. | From the Default Domain Security Settings MMC, shown in Figure 16.15, click Security Settings, Event Log.
Figure 16.15. The Default Domain Security Settings MMC, showing the available settings for the event logs. 
| | | 3. | The policies available for the object are displayed. Double-click the Maximum Security Log Size policy. This opens the Properties dialog box shown in Figure 16.16.
Figure 16.16. Select Define This Policy Setting, and then increase the default value to 30,000. 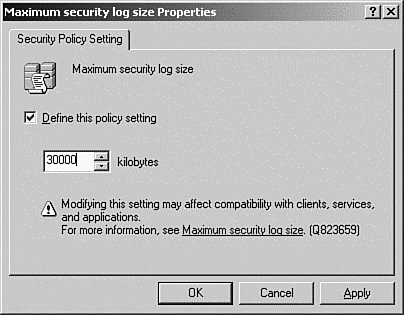
| 4. | Set the log size to 30,000. Note that the settings are in kilobytes. Click OK to save.
| 5. | Close the Default Domain Security Settings MMC.
|
|
Recording security events is used as a form of intrusion detection. When security auditing and the Security logs are configured properly, it is possible to detect some types of network break-ins before they succeed. An example of this is a password attack, which in a network with a good password policy can take some time to perform successfully. The Security log is also invaluable after a break-in has occurred, so you can track the movements and actions of the intruder and how he was able to enter your system. Above all, security logging is effective only if the network administrator takes the time to review it frequently. Best Practices It is important to realize that a good security implementation involves the coordination of many network functions. Above all, it is imperative that the user is able to log on to the network and locate and use the appropriate resources without an undue level of difficulty. Critical network servers should always be kept in a secure area. The odds of a system break-in are greatly increased if a skilled intruder has physical access to a server console. In addition, having critical servers in an open area can make them vulnerable to a disgruntled employee with nothing more sophisticated than a baseball bat or a bucket of water. Attacks do not have to be sophisticated to be damaging, and historically most losses occur from inside the company versus from the outside. One of the best security policies is proper user education. Users should be aware of how important it is to protect company resources and the implications of what could happen if critical information falls into the wrong hands. Users should be educated about how to keep their passwords confidential and secure. A good idea is to publish a clearly worded security policy and require everyone, including network administrators, to review it periodically. |
|

