The Server Structure
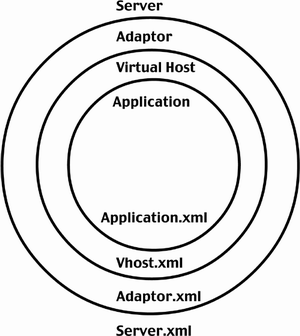
| The Flash Communication Server is divided into four levels, as shown in Figure 14.1's Venn diagram. Each inner circle adopts the access model and resource limitations defined by the outer circle. Each inner circle also applies additional limitations on security and resources. The security and resources of the application (inner-most circle) are a culmination of the outer levels. The four levels are:
Figure 14.1. The Server structure and the corresponding configuration files. Up to this point you have only been interacting with the application. You can section off applications just like creating web servers in Windows IIS or domain entries in your DNS server. You can manage the bandwidth and user capacity for each "section," as well as manage ports and limits per adaptor. These next sections will step you through the controls for each server level. Each level will address the physical location, user management, configuration, and security tips. At the end of the chapter, the exercises will step you through the process of creating and managing multiple adaptors and virtual hosts. Note An important security consideration for Flash Communication Server is that the RTMP protocol, although it is a binary format, does not support encryption. You can achieve encrypted communication when you use ticket-based authentication over a secure Flash Remoting MX connection on the Flash client. Because Flash Remoting MX can use the secure HTTPS protocol, it safe to transfer secure information. A ticket-based system would engage the Flash player to request a "code" assigned by an application server through a secure Flash Remoting MX connection. That code would then be passed to Flash Communication Server using RTMP. Flash Communication Server would connect with the application server to validate the code. This technique is used between many systems to pass secure information from a secure environment to the public interface. |
EAN: 2147483647
Pages: 200