Chapter 8: Remote System Management
In Brief
Remote management is essential to becoming a good administrator. When you're working at a site with 300 or more systems, visiting and updating every single system becomes an impossible task. In this chapter, you will learn how to manage remote systems from the command line and through Windows Management Instrumentation.
Administrative Shares
By default, Windows 2000/XP/2003 creates special shares so that administrators can perform various tasks remotely. These special shares are called administrative shares and are automatically created when you install the operating system and whenever you add a nonremovable drive or partition. Administrative shares are hidden shares that only administrators can access. The permissions, names , and settings for these shares cannot be modified, and these shares can only be removed by making special registry entries. The most common administrative shares are:
-
ADMIN$ ”Shares the directory Windows was installed in (for example, C:\WINNT)
-
DRIVE $ ”Shares all available drives , where drive is the specific drive letter
-
IPC$ ”Share that represents the named pipes communication mechanism
-
PRINT$ ”Share for shared printer drivers
-
REPL$ ”Shares replication directory on a server
Attaching to Shares
Many remote administrative tasks can be performed through network share access. Once you attach to a share, you can perform tasks on these shares as if they were local resources. The process of attaching to a network share and assigning that connection a drive letter is called mapping . Mapping a drive requires that you specify the complete Universal Naming Convention (UNC) path of the share and the available drive letter to which you want to map it.
Once you map a drive to a share, you will be able to perform many of the tasks you perform on your drives locally. To map a drive from within Windows, right-click Network Neighborhood and select Map Drive. The Map Network Drive dialog box will appear (see Figure 8.1).
Figure 8.1: Mapping a network drive.
To map a drive from the command line, start a command prompt and enter the following:
NET USE DRIVE : \ COMPUTER \ SHARE
Here, DRIVE is the drive letter you want to map the SHARE name to, and COMPUTER is the system holding the shared resource.
You can also map a drive as a different user :
NET USE DRIVE : \ COMPUTER \ SHARE /USER: DOMAIN \ USERNAME PASSWORD
Performing Tasks through a Share
Once a remote share has been mapped, you can perform commandline tasks on it as if it were a local drive. Here is an example to delete all the files within a directory on a remote system:
NET USE DRIVE : \ COMPUTER \ SHARE DEL DRIVE :\*.*
Once a drive is successfully mapped, you can utilize any of the file management methods that were detailed in Chapter 4.
Disconnecting Mapped Shares
When you no longer need to access the resources of a mapped share, you can disconnect it to free up available drives. To disconnect a mapped drive from within Windows, right-click Network Neighborhood and select Disconnect Drive. When the Disconnect Network Drive dialog box appears (see Figure 8.2), select the drive and click OK.
Figure 8.2: Disconnecting a mapped drive.
To disconnect a mapped share from the command line, start a command prompt and enter the following:
NET USE DRIVE : /DELETE
Here, DRIVE is the drive letter mapped to the share that you want to disconnect.
| Tip | sol;D is the abbreviated form of the /DELETE switch. |
Windows Management Instrumentation
As enterprises grow larger, they become more difficult to manage. WebBased Enterprise Management (WBEM) is an initiative to provide an environment-independent solution to manage data and devices. WBEM was developed by the Desktop Management Task Force (DMTF), a collective organization consisting of Microsoft, Compaq, and other large corporations. Windows Management Instrumentation (WMI) is Microsoft's Windows implementation of the WBEM initiative.
What Is WMI?
WMI, formerly called WBEM, provides scripters and developers with a standardized method to monitor and manage local and remote resources. It comes included in Windows 98 and Windows 2000/XP/ 2003, and is available as a download for Windows 95 and Windows NT (Service Pack 5 or higher). WMI provides a standard, scriptable interface to various resources. The devices and applications controlled by WMI are known as managed objects . Managed objects can be anything from hardware, such as a hub or motherboard, to software, such as the operating system or an application.
The WMI Process
The executable that provides all the functionality of WMI is called WINMGMT.EXE. WINMGMT.EXE runs as a standard executable on Windows 9 x (because Windows 9 x does not support services) and as a service on Windows NT/2000/XP/2003 systems. When a script or application (known as a consumer) issues calls to the WMI namespace, the executable awakes and passes these calls to the CIM Object Manager (CIMOM). The CIMOM is the entrance to the WMI infrastructure. It allows for the initial object creation and provides a uniform method to access managed objects. When CIMOM receives a request to control a managed object, it first checks the CIMOM object repository.
The CIMOM object repository is a storage area for the Common Information Model (CIM). The CIM contains the WMI object models and a description of all the available managed objects, called the management schema . This repository is full of all the different access methods and properties of manageable objects, known as static management data. If the information requested cannot be found in the repository, the repository passes the request down to the object provider.
A provider is the interface between the device to be managed and the CIMOM. The provider collects the information from a device and makes it available to the CIMOM. This information is known as dynamic management data. Developers create providers when the CIM does not contain methods to access a managed resource. Several providers come packaged with WMI:
-
Active Directory provider
-
Event Log provider
-
Performance Counter provider
-
Registry provider
-
SNMP provider
-
View provider
-
WDM provider
-
Win32 provider
-
Windows Installer provider
Once the provider has completed processing the request, it sends all results back to the originating script or application.
Scripting WMI
In Chapter 1, you learned how to connect to a WSH object. The process of connecting to the WMI object model is similar to connecting to the WSH object model. To gain access to an object, you use the GetObject function and set it to a variable. This is called instantiating an object, as in the following example:
Set variable = GetObject("winmgmts:{impersonationLevel= impersonate}!\ computer \root\ namespace ").ExecQuery ( WQL ) | Note | The code above must be placed on one line. |
Here, variable is the variable used throughout your script to access all the properties and methods within the object. The winmgmts namespace specifies a call to the WMI service.
Impersonation
{Impersonationlevel=impersonate}! instructs WMI to execute the script with the credentials of the caller (person who executed the script) and not the credentials of the currently logged-on user of the targeted system. This instruction is extremely useful when administrators are running remote scripts on systems and the logged on user does not have sufficient privileges to perform all the specified requests .
| Tip | {Impersonationlevel=impersonate}! is the default impersonation level on Windows 2000/ XP/2003, and therefore can be omitted from your scripts if you are running Windows 2000. It is included in the scripts in this book only for Windows NT compatibility. Impersonations are not supported by Windows 9x because the operating system does not support user privileges. |
Namespaces
Computer is the name of the target system to run the script on, and \ROOT\ namespace specifies which namespace to connect to within the CIMOM object repository. Namespaces are organized containers of information within a schema. Namespace hierarchy runs from left to right and is separated with backslashes. ROOT is the parent namespace for WMI and contains all the child namespaces. WMI includes three child namespaces:
-
Cimv2 ”Stores Win32 system classes
-
Default ”Stores system classes
-
Security ”Stores WMI security classes
Most of your WMI scripting will include the Cimv2 namespace, because it holds many classes and instances for a Win32 system.
WMI Query Language
WMI uses a rich query language called the WMI Query Language (WQL). This language, similar to SQL (Structured Query Language), allows you to query WMI information. The basic syntax for a WQL statement is as follows :
.ExecQuery("select propmeth from class ") | Tip | In addition to the select and from statements above, you can use many statements and keywords based on SQL. |
ExecQuery runs the WQL statement, which is stored in quotes and surrounded by parentheses. Propmeth specifies the property or method to retrieve from the specified class . Classes are organized containers for properties and methods of a manageable device. For example, the Win32_TapeDrive class contains all the properties and methods to manage tape drives.
In addition to the ExecQuery , you can also use the ExecNotification-Query to perform WQL queries. The ExecNotificationQuery method is used to detect when instances of a class are modified. In plain English, this method allows you to poll for events. Combined with WQL, you can use this method to monitor the event log, CPU, memory, and more based on a specified interval.
The WMI SDK: Worth Its Weight in Gold
Microsoft creates software developer kits (SDKs) to assist third-party application developers in creating Windows applications. The WMI SDK includes the core WMI installation, documentation, utilities, and examples. You can obtain the WMI SDK free from msdn.microsoft.com .
WMI Object Browser
The WMI Object Browser (see Figure 8.3) is a Web application to explore WMI namespaces. Through it, you can view and manipulate all the classes and their properties and methods. The application runs within a Web browser and allows you to connect to any namespace on a local or remote system.
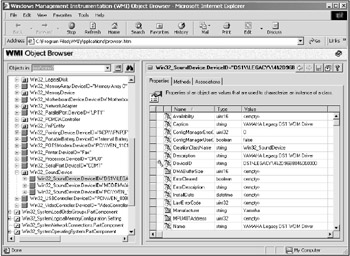
Figure 8.3: The WMI Object Browser.
| Note | The WMI Object Browser is an intensive Web application. If it seems to be frozen when navigating through the various classes, it may actually be loading the properties, methods, and subclasses into memory. |
EAN: 2147483647
Pages: 89