Performing Advanced Administration Tasks
Performing Advanced Administration Tasks
In this section we talk about performing some of the more advanced administration tasks that are possible with FireWall-1 NG. These are some of the tricks of the trade that can make life easier for you.
Firewall Controls
Sometimes the best way or only way to do something is at the command line. Fortunately, many of the things that you can do with the GUI you can also do at the command line. In fact, in case you haven t noticed, many GUI actions invoke command-line functions. In this section, we discuss some of the most common command-line options and their purposes.
fwstop
At times you may need to stop and restart the firewall for maintenance or just to bounce it. The easiest way to do this is with the fwstop command. Executing fwstop will kill the following:
-
The FW-1 daemon (fwd)
-
The management server (fwm)
-
The SNMP daemon (snmpd)
-
The Authentication daemon (authd)
It is possible to unload FW-1 processes but to maintain security by loading the default filter. This enables the FW-1 administrator to take down the FW-1 processes for maintenance without exposing the firewall machine to attacks while unprotected . The commands to stop FW-1 NG and load the default filter are these:
fwstop -default fwstop proc
fwstart
fwstart will load FW-1 and start the processes killed by fwstop :
-
The FW-1 daemon ( fwd )
-
The management server ( fwm )
-
The SNMP daemon ( snmpd )
-
The Authentication daemon ( authd )
No options are needed with fwstart .
cpstop
Not to be confused with fwstop . In fact, cpstop is inclusive of the fwstop function. Executing cpstop will stop all running Check Point applications. One exception is the cprid, which is a Check Point process that is invoked at boot time and runs independently of other Check Point applications.
cpstart
Executing cpstart will start all Check Point applications. Similar to cpstop , executing cpstart implies that fwstart performs its function.
cpconfig
The command cpconfig is used to configure FW-1/VPN-1. In Windows NT, executing this command opens the Check Point Configuration Tool GUI. In *nix environments, the command displays a configuration screen with options that depend on what is installed. In both environments, executing cpconfig enables you to install and update licenses, create administrators, view the management server fingerprint , specify remote clients that can log into the management server, configure SNMP, and register PKCS#11 cryptographic tokens.
cpstat
Executing this command will provide you with the status of the target hosts . In NG, cpstat is intended to replace fw stat .
fw Commands
A number of fw commands are helpful for controlling the FW-1 daemon. fw commands follow this basic syntax:
fw [action] [target (default localhost)].
-
fw load This command will convert the *.W file from the GUI to a *.pf file and compile into Inspection code, installing a security policy on an enforcement module. A sample fw load command is as follows :
fw load Standard.W all.all@localgateway
This command will load the Standard.W policy onto the firewall object named localgateway .
-
fw unload The fwunload command will uninstall security policy from the specified target(s). It is obsolete and has been moved to a subcommand of the fwm executable. An example of usage is as follows:
fw unload ExternalFW
This command will actually call fwm unload ExternalFW and uninstall the policy from the ExternalFW firewall. The common command fw unload localhost has also been taken into account and has changed to the following command.
-
fwm unloadlocalfw fetch fw fetch is used to fetch Inspection code from a specified host and install it to the kernel of the current host. An example of usage is as follows:
fw fetch 192.168.0.2
This will fetch the security policy from the management station located at 192.168.0.2. You can also use the name of the management station s object or a DNS resolvable name .
-
fw putkey The fwputkey command is helpful if you are integrating an NG Management Server with 4. x enforcement modules. Executing fw putkey will install an authenticating password. The password is used to authenticate SIC between the management server and the module the first time the two communicate. For an example of a remote firewall module, type the following:
fw putkey n 192.168.0.2 192.168.0.1
The “n option specifies the dotted IP address that will be used to identify this host to other hosts. The second part of the syntax that specifies 192.168.0.1 is the closest interface on the target to which the password will be installed. Additionally, by not specifying the password to be used, you will be prompted for it.
-
fw ctl fw ctl is a utility for controlling the FW-1 kernel. In addition, fw ctl pstat will provide you with internal FW-1 statistics. It can also be used for obtaining interface information.
-
fw tab fw tab is used for displaying the contents of FW-1 s various tables INSPECT tables. For example, to display the connections table, you would type the following:
fw tab t connections
-
fw logswitch The fw logswitch command will save the current log and start a new one. This is particularly helpful in rotating logs on remote machines from the Management server:
fw logswitch h localgateway +old_log
This command will rotate the logs on the remote firewall named localgateway and copy the log to the management server with the name of localgateway.old_log.
-
fw logexport The fw logexport command dumps the log to an ASCII file. Log files in this format can be processed by third-party tools or imported into databases for further analysis. For example, to export your logs with a semicolon that delimits the output fields and to give the file the name 4analysis, you would type the following:
fw logexport -d -o 4analysis.txt
-
fw ver The fw ver command returns the version of FW-1 that s currently running. By adding the -k option, you can learn the kernel build as well:
fw ver -k
Firewall Processes
You can use a number of operating-specific commands to list the processes running on your bastion host:
-
*nix In *nix, executing ps “ef will display all currently running processes and full information, including their process ID.
-
Nokia For Nokias, using the command ps “aux will display running processes.
-
Windows In Windows NT, you may view the running processes and their allocated memory by executing the Task Manager. Be aware that all FireWall-1 processes will appear as fw.exe. It is not uncommon to have five or more fw.exe processes running.
-
$FWDIR\tmp FW-1 writes the process IDs of FW-1 processes as they are started and writes them to *.pid files that correlate with the processes started, as you can see in Figure 8.13. For example, opening the file fwd.pid in a text editor would display the process ID assigned to the fw.exe process. This is extremely helpful in Windows when each process is named fw.exe. This process-to-process ID mapping will help you figure out which fw.exe goes with what firewall process.
-
fwd The FW-1 daemon.
-
fwm The management server.
-
in.ahttpd The name of the process assigned to the HTTP security server.
-
in.asmtp.d The name of the process assigned to the SMTP security server.
-
in.atelnetd The name of the process assigned to the Telnet security server.
-
in.arlogind The name of the process assigned to the Rlogin security server.
-
in.aftpd The name of the process assigned to the FTP security server.
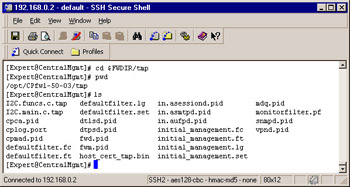
Figure 8.13: Process ID Mapping in SecurePlatform -
in.aclientd The process responsible for client authentication on port 259.
-
in.ahclientd The process responsible for client authentication on port 900 through a Web browser.
-
fw kill Can be used to terminate any running FireWall-1 process. The syntax is fw kill [process name] . For example, you can terminate the HTTP security server and restart it to resolve problems with the HTTP proxy by executing the following:
fw kill in.ahttpd