When Domains Multiply
| |
In this section, you look at new methods available in Windows Server 2003 to interconnect domains. In Windows NT 4.0 domains, you're limited to simple unidirectional or bidirectional trust relationships to interconnect two domains explicitly at a time. Windows Server 2003 has many more sophisticated, functional models to create relationships and connections among its domains.
Trust relationships across domains
Windows NT 4.0 trust relationships are not transitive. For example, if domain A trusts domain B, and domain C trusts domain B, domain C does not automatically trust domain A (see Figure 11-2).
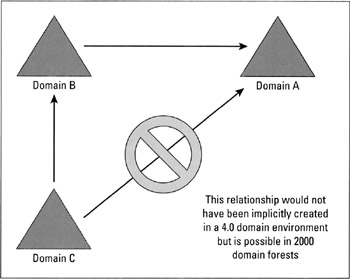
Figure 11-2: An example of a trust relationship in Windows NT 4.0
This lack of transitivity is no longer the case with the trust relationships used to connect members of a tree or forest in Windows Server 2003 or Windows 2000. Trust relationships used in a Windows Server 2003 or 2000 tree are two-way, transitive trusts. This means that any domain in the forest implicitly trusts every other domain in its tree and forest. This removes the need for time-consuming administration of individual trusts between pairs of domains, because such trusts are created automatically whenever a new domain joins a tree.
The security of Windows Server 2003 trusts is maintained by employing Kerberos. Kerberos Version 5.0 is the primary security protocol for Windows Server 2003, but it's not a Microsoft protocol. Kerberos is a security system developed at the Massachusetts Institute of Technology (MIT). It verifies both the identity of the user and the integrity of all session data while that user is logged in. Kerberos services are installed on each domain controller, and a Kerberos client is installed on each workstation and server. A user's initial Kerberos authentication provides that user with a single logon to enterprise resources. For more information about Kerberos, see the Internet Engineering Task Force's (IETF's) Requests for Comments (RFCs) 1510 and 1964. These documents are available on the Web at http://www.rfc-editor.org.
Building trees
In Windows Server 2003, one domain can be a child of another domain. For example, http://legal.savilltech.com is a child of http://savilltech.com (which is the root domain name and therefore the name of the tree). A child domain always contains the complete domain name of the parent. As shown in Figure 11-3, http://dev.savillCORP.com can't be a child of http://savilltech.com because the domain names do not match. A child domain and its parent share a two-way, transitive trust.
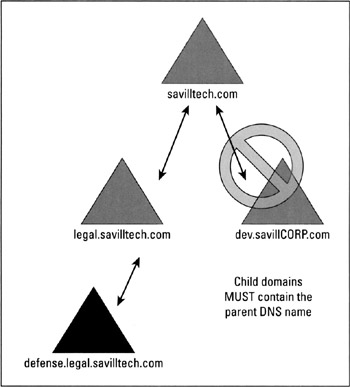
Figure 11-3: Parent/child relationship example.
| Tip | When a domain is the child of another domain, a domain tree is formed . A domain tree must have a contiguous namespace (which means all name-spaces share a common root, that is, have the same parent). |
Domain trees can be created only during the server-to-domain-controller-promotion process with DCPROMO.EXE.
There are a number of advantages in placing domains in a tree. The first and most useful is that all members of a tree have Kerberos transitive trusts with their parent and all its children. These transitive trusts also mean that any user or group in a domain tree can be granted access to any object in the entire tree. In addition, a single network logon can be used at any workstation in the domain tree.
Understanding forests
You may have a number of separate domain trees in your organization with which you would like to share resources. You can share resources between domain trees by joining those trees to form a forest.
A forest is a collection of trees that does not explicitly share a single, contiguous namespace (however, each tree still has to be contiguous). Creating a forest may be useful if your company has multiple root DNS addresses.
For example, in Figure 11-4, the two root domains are joined via transitive, two-way Kerberos trusts (like the trust created between a child and its parent). Forests always contain the entire domain tree of each domain, and you can't create a forest that contains only parts of a domain tree.
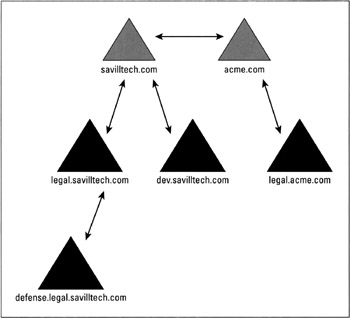
Figure 11-4: An example of a forest.
Forest are created when the first server-to-domain-controller-promotion process using DCPROMO is initialized and cannot currently be created at any other time.
You're not limited to only two domain trees in a forest. (You can have as few as one, because a single domain by itself is technically considered both a tree and a forest.) You can add as many trees as you want, and all domains in the forest will be able to grant access to objects for any user in the forest. Again, this cuts back the need to manage trust relationships manually. The advantages of creating forests are as follows :
-
All trees have a common global catalog containing specific information about every object in the forest.
-
The trees all contain a common schema. Microsoft has not yet confirmed what will happen if two trees have different schemas before they're joined. We assume that the changes will be merged.
-
Searches in a forest perform deep searches of the entire tree of the domain from which the request is initiated and use the global catalog entries for the rest of the forest.
| |
EAN: 2147483647
Pages: 195
- Integration Strategies and Tactics for Information Technology Governance
- An Emerging Strategy for E-Business IT Governance
- Linking the IT Balanced Scorecard to the Business Objectives at a Major Canadian Financial Group
- Measuring and Managing E-Business Initiatives Through the Balanced Scorecard
- The Evolution of IT Governance at NB Power