User Accounts and Groups
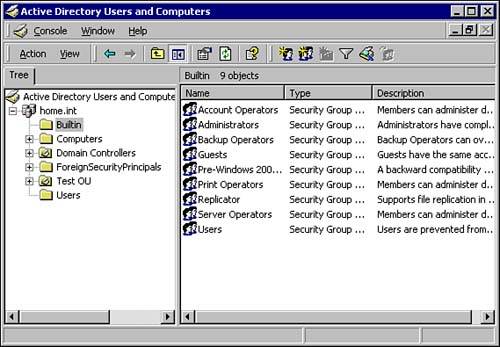
User Accounts and GroupsA Windows 2000 user account allows the user to log on to a computer or a domain. In addition, a user account controls what access, if any, that a user has to local or domain resources. To grant these access rights, the administrator assigns rights and permissions to the user's account. Permissions control what a user can do with a resource, such as a file, folder, or printer. When an administrator assigns permissions, she specifies what type of access the user has. For example, a member of the accounting department may have read and write access to all folders and files related to the accounting department. Yet, this same user may well be denied all access to human resources' files and folders. Most likely this user has little to no business dealing with confidential files found in human resources. A group is a collection of one or more user accounts that have at least one thing in common, such as all personnel in the sales department who will likely need access to the same resources. Assembling users into groups simplifies administration because the administrator has to configure permissions to resources only once, rather than for each user individually. Also the administrator can add or remove users from the group at any time. This comes in especially handy when another user, not part of the group, needs access to the resources to which the group collectively has access. All the administrator has to do is to add the user to the group that has such access. There are two types of user accounts and groups, domain and local . A local account or group can be used to assign a user or a group of users access to the resources only on the computer where the account resides. However, domain user accounts and groups can be used to grant access to any resources that are contained within the domain. You will discover each in more depth next . Domain AccountsA domain is the basic security, administrative, and replication unit of the Active Directory. Multiple domains can be connected to form a tree or forest. However, because Active Directory, forests, and trees are covered on other exams, we limit our discussion to the domain level. Each domain has an Active Directory security database that can contain millions of objects. These objects are the users, groups, computers, and other objects that are the resources contained within the domain. Access to these resources is controlled by granting access to users and groups. To assist in sorting and categorizing these users, groups,and resources, there is a subdomain container called an Organizational Unit (OU). Each OU can hold a large number of objects. Access to the objects in an OU can be granted at the object, OU, or domain level. Each Active Directory domain controller contains a read/write copy of the domain database. This allows you to manage the database using any domain controller. Any changes are replicated to all of the other domain controllers. Domain users, groups, and other objects are created and managed using the Active Directory Users and Computers snap-in, as shown in Figure 8.1. This snap-in is installed by default on Windows 2000 servers that are domain controllers, or it can be added to a Windows 2000 Professional or Windows 2000 member server by installing the Administrative Tools package. The installation file, adminpak .msi , is located on the Windows 2000 Server CD in the I386 folder. The snap-in is started by selecting Start, Programs, Administrative Tools, Active Directory Users and Computers. Figure 8.1. The Active Directory Users and Computers snap-in is used to create and manage users, groups, and other objects. The Active Directory Users and Computers snap-in has five default nodes and two invisible ones:
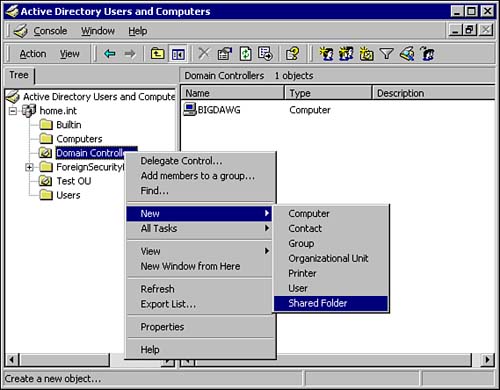
As shown earlier in Figure 8.1, the containers are represented in Active Directory as blank file folders, whereas OUs are file folders with an open book icon. The difference between the two is that you can rename, nest, and configure the properties for OUs. You are also limited as to what objects can be created or moved to some containers. There may possibly be other containers shown if Active Directoryaware applications, such as Exchange 2000, are installed. To create a new object, right-click the desired container in the Active Directory Users and Computers snap-in, click New, then select the type of object that you want to create (see Figure 8.2). Figure 8.2. The Active Directory Users and Computers snap-in, showing how to create an object.
Local AccountsEvery member server and all workstations will have their own local accounts . Unlike domain accounts, in which every domain controller contains a shared database of all users, groups, and resources in the domain, these local accounts exist only on the computer where they were created. Also, these accounts can be used only to grant access to resources on the computer on which the local accounts reside. Local users and groups are created in the local security database. Local accounts cannot be used to access any resources other than those on the local computer because other computers cannot see the local Active Directory security database in order to authenticate the users and group in the database.
The Local Administrator and Guest AccountsBy default, Windows 2000 Server creates two local user accounts, Administrator and Guest . The Administrator account has the following properties:
The Administrator account is used when Windows 2000 Server is installed. This account cannot be deleted or disabled, to ensure that you never lock yourself out of your server. This is the only account that cannot be deleted or disabled. The Guest account is disabled by default, and has the following properties:
The Guest account is just what the name implies, an account that has limited privileges, and is only to be used temporarily by a user who won't be around long. Local GroupsIn addition, there are several default local groups created when Windows 2000 Server is installed:
Local groups can be used only to assign permissions to resources residing on the server where the group is created. Like local user accounts, local groups are stored in the local security database. Local groups can contain local accounts from the same computer on which they are created, and a local group can't be a member of any other group. If a server is a member of a domain, the local groups on that server can contain domain user accounts and groups. To create a new local group, perform the following steps:
When creating and using local groups, you should always keep the following points in mind:
Built-in System GroupsIn addition to the built-in local groups, Windows 2000 also has several built-in system groups. The user cannot manipulate the membership of these groups; they are used to assign rights and permissions to resources. The Windows 2000 operating system dynamically manipulates the membership of these groups according to how the server is accessed, not by whom. The commonly used built-in system groups are
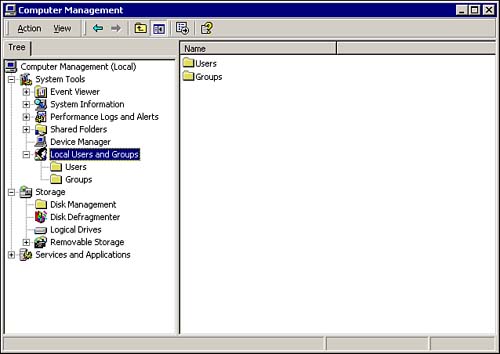
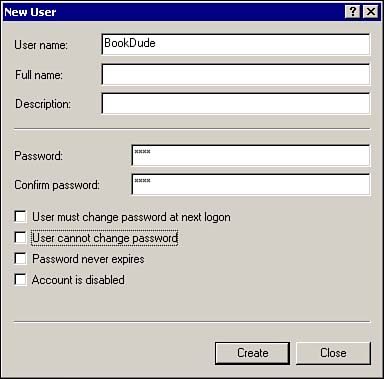
Assigning permissions to the Everyone group can be a huge security exposure if the Guest account is enabled. Windows 2000 will authenticate a user without a valid user account as Guest. This automatically gives this user all rights and permissions that you have assigned to the Everyone group. A better strategy would be to assign rights and permissions for resources to the Authenticated Users group instead of the Everyone Group, and never enable the Guest account, or, at a minimum, rename it. The Local Users and Groups Snap-InLocal User accounts and groups are created and managed using the Local Users and Groups snap-in, as shown in Figure 8.4. To open the snap-in, select Start, Programs, Administrative Tools, Computer Management. Figure 8.4. The Computer Management MMC, showing the Local Users and Groups snap-in. The Local Users and Groups snap-in is part of the Computer Management MMC. To create a new user
The rules for usernames in Windows 2000 are as follows :
The rules for passwords in Windows 2000 are:
User AuthenticationWhen a user logs on to a Windows 2000 computer, the user supplies a user account and a password, or possibly a Smart Card, if that technology is being used. This information is used to authenticate the user. In other words, these items are used to confirm that the user is who he says he is. After the user is properly authenticated, an access token is created for that user. This access token consists of
After the user is logged on to the server, each process or resource that the user attempts to access will examine this access token to confirm that the user has been granted the appropriate access. All Windows 2000 objects have security restrictions. These security restrictions are configured in the Access Control List (ACL) . The ACL containsa listing of the users and groups that have access to the object, and specifically what type of access. Although the username is how we identify accounts, Windows 2000 uses the account's SID for authentication and access levels. Note that the SID will always be a unique string, such as S-1-5-25-1123561935-920026236-84092546-1000. For example, if you accidentally delete a user account and create another one using the same username and other properties, it will have a totally different SID. The new user account will not have access to the same resources as the old account unless you manually grant the permissions by assigning the user account to the same groups. The access permissions were assigned to the deleted SID. Windows 2000 never reuses a SID; they will always be unique. If you have a user who leaves the organization and is replaced by a new employee who will be performing the same tasks, you should rename the old user account for use by the new user. This ensures that the new user has access to the same resources as the old user. |
EAN: 2147483647
Pages: 155
- Structures, Processes and Relational Mechanisms for IT Governance
- Assessing Business-IT Alignment Maturity
- Measuring ROI in E-Commerce Applications: Analysis to Action
- Technical Issues Related to IT Governance Tactics: Product Metrics, Measurements and Process Control
- The Evolution of IT Governance at NB Power