Group Policy Planning Issues
Group Policy Planning IssuesWhen designing Active Directory for Group Policy, you need to consider several issues. The planning issues that require consideration are filtering using security, inheritance modification, and optimizing Group Policy performance. For example, the user or group who is responsible for the administration of a domain or an OU might need to remain exempt from a GPO. When you filter a GPO, you are exempting a group from those settings. Filtering Using SecurityBy default, all objects in a container are affected by a Group Policy that has been applied. However, in some instances you might not want all the objects to be affected by the Group Policy. In such cases, filtering can be used. Filtering is a feature that allows an administrator to exclude certain groups from being affected by a Group Policy (by limiting the scope of the policy). When you filter a GPO, you exempt a group from the settings in the policy.
The Group Policies applied to a container affect all users who have read permission for the GPO. This is the default permission given to all users for a GPO, and it causes users in a container to be affected by the policy, by default. To change the scope of the GPO and exclude certain users from being affected, simply create a security group containing the users who need to be excluded and deny the group access to the GPO.
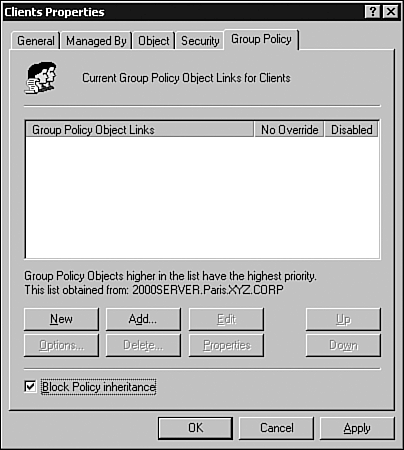
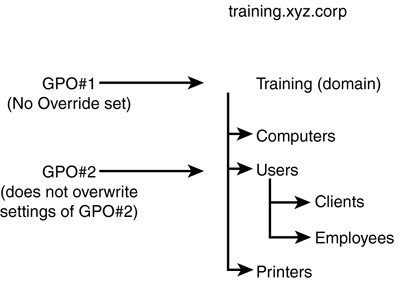
If a Group Policy is applied to the Users OU (as shown previously in Figure 6.7), you might need to limit its scope so that it does not affect the users or the group in the OU who are responsible for administration. If the policy applies restrictions to the users' computing environment, some of the restrictions might not be required for administrative purposes. In this case, a filter can be applied to exempt those users responsible for administration of the OU from the policy. Inheritance ModificationIn some instances, a GPO applied to a parent container should not be applied to its child containers (remember, a GPO applied at the OU level is passed down from parent container to child container). Referring to Figure 6.7, a GPO applied to the Users OU will be inherited by the Clients and Employees containers. In such a case, blocking inheritance can prevent the GPO settings applied to a parent OU from being applied to a child OU. BlockingUsing a feature called blocking , the inheritance of a GPO can be modified so that it is not passed on from parent container to child container. Any policy applied at the site, domain, or OU level can be blocked. If the Group Policy applied to the Users container should not apply to the Clients container (as shown previously in Figure 6.7), inheritance of the GPO could be blocked. The Employees container would still be affected, but not the Clients container.
Use the following steps to block the inheritance of a GPO:
By selecting this check box, the Clients container is no longer affected by the Group Policy linked to the Users container.
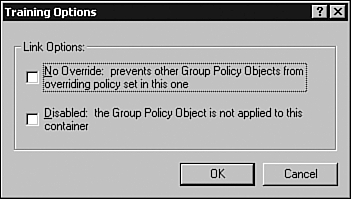
The only time that the Block Policy Inheritance option is ignored and the policy still applied is if the No Override option is set, as discussed next . No OverrideThe No Override option means exactly that: If this option is set, any Group Policies linked to a parent container are applied to the child containers, regardless of whether the Block Policy Inheritance option is set. This option prevents any other GPO from overwriting the settings contained in it, and any GPO link that has the No Override option set will not be overwritten by another policy. To see how this option can affect inheritance of Group Policies, refer to Figure 6.9. Suppose a GPO has been linked to the Training domain and another GPO has been linked to the Users OU. Without any inheritance modification, the GPO at the domain level would be processed first, and the GPO at the OU level would be processed second, overwriting previous settings (remember also that local policies would be applied before any others). If the No Override option is set on the first GPO link at the domain level, its settings will not be overwritten when the second GPO is applied. Figure 6.9. Setting the No Override option on the GPO link at the domain level prevents any other GPOs from overwriting its policy settings. Use the following steps to specify the No Override option:
Loopback ProcessingFor certain special-purpose computers, the computer configuration settings applied by Group Policy should remain in effect regardless of who logs on to that computer. In other words, the user's Group Policy settings should not override the specified settings for specific computers. Special-purpose computers can be kiosk machines located in common areas, computers configured as email terminals, or any other application where a common interface look and feel needs to be set and retained for all uses. By default, because User Group Policy is applied at logon (whereas Computer Group Policy is applied at startup), a user's settings override the computer settings. To ensure that computer settings are retained, Loopback Processing can be selected using Group Policy for all computers in a specified container, be it a site, domain, or OU. Loopback Processing essentially reapplies the computer Group Policy instead of, or following, the application of a user's Group Policy at logon. Loopback Processing can be configured in either Merge mode or Replace mode. In Merge mode, the user's GPOs are processed first, in their normal order, at logon. Then, after all the user GPOs have been applied, the entire set of computer GPOs is processed. The result is that any user settings not overridden by the computer settings are retained, but whenever a conflict exists, the computer settings take precedence. In Replace mode, user GPOs are not processed at all; only the computer Group Policy is applied when a user logs on. In this case, no user settings at all are applied during the user's sessiononly computer settings. Optimizing Group Policy PerformanceOne of the overall goals when designing any network infrastructure is to optimize the performance of the network. There are some issues to keep in mind and some settings that can be configured to optimize the performance of Group Policies. When designing Active Directory for Group Policy, keep the following points in mind to ensure performance is optimized:
|
EAN: 2147483647
Pages: 148