FreeBSD as a VPN Server
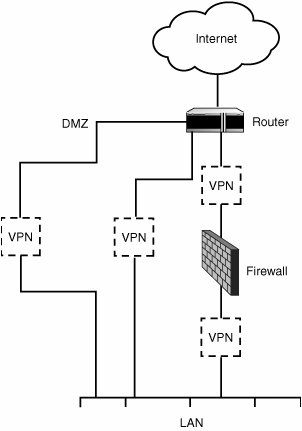
| It won't always be the case that you only have one FreeBSD machine to connect to a remote Virtual Private Network. You might have to set up a routed, translated subnetwork of your own, for example, and create a permanent VPN tunnel to the remote network for the use of multiple machines on your own subnet. Fortunately, because you have set up the gif0 interface to use a virtual private IP address on your own local machine, making the jump to a fully routed VPN link should be child's play. All that's required is a second Ethernet card on your machine that's plugged into the local private network. Follow the same instructions listed in the previous section, except for the part where you alias the private address (192.168.0.1) to the public Ethernet card. Instead, assign that address to the second Ethernet card. Then, set up the spdadd lines to reflect the network address of the whole network you're managing instead of just your own single machine. For instance, the following lines in /etc/ipsec.conf would allow you to tunnel the entire private 192.168.0.0 network (Class B, with a mask of 16 bits) to the remote VPN server, enabling the machines on your network to communicate with the machines in the remote 10.0.0.0 network, and vice versa: spdadd 192.168.0.0/16 10.0.0.0/8 any -P out ipsec esp/tunnel/111.112.113.114-221.222.223.224/require; spdadd 10.0.0.0/8 192.168.0.0/16 any -P in ipsec esp/tunnel/221.222.223.224-111.112.113.114/require; One final point to note is that to run a proper subnetwork, your FreeBSD machine will have to be doing all the routing and NAT/firewall work for that network; otherwise, you will have to have dedicated equipment on your end to handle those tasks, the same as on the remote end. Figure 31.8 shows a topological layout of the network, including several potential, correct locations for the VPN device or functionality (indicated by "VPN" in a dashed box). VPN can be handled by a dedicated machine, or it might be consolidated into the same machine as the firewall or router. If your FreeBSD machine is doing all these tasks itself, you probably won't have to worry; if it's not, however, you must ensure that each piece of functionality is positioned properly in the network so that the right addresses are visible to the devices that need them. Particularly bear in mind that if you have VPN functionality in the network at any point, your firewall will almost certainly have to be set up to allow its traffic through with specialized rules. Moreover, your router will have to be able to route the tunnel traffic to and from the VPN device. Most VPN misconfigurations stem from incorrect firewall or router rules that don't take into account the specialized addressing needs of the VPN tunnel. Figure 31.8. A topological diagram of a subnetwork, including the LAN, firewall, NAT, router, and WAN, as well as four potential locations for the VPN device. Note Refer to Chapter 28, for details on routing a subnetwork using FreeBSD as well as NAT configuration. See Chapter 30, "Network Security," for more on firewalls. |