Managing Your OSPF Network
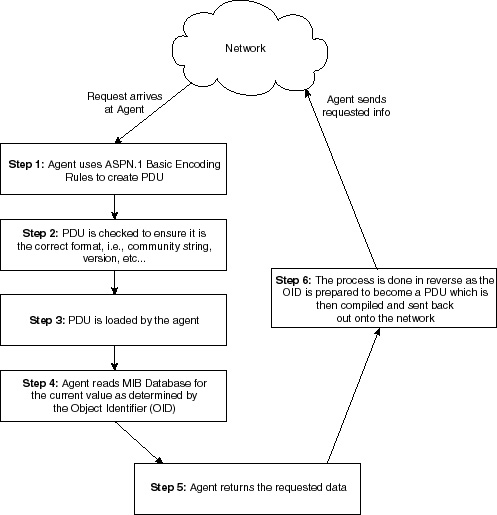
This is of course only the first part of the process (that is, the request for information); the second part of the process is where the managed device receives the request. The managed device then passes the request on to the SNMP Agent which then processes and replies to the request. This sequence of events is covered in the next section, “Agent Response to NMS Request.” Agent Response to NMS Request The flow chart presented in Figure 9-7 describes the second part of the SNMP operation in which the SNMP request is received by the managed device, which passes it on to the agent who will process and answer the request. This flow of events is presented in a generic format from a high level perspective. As with any complex network operation, there are a great many events that also occur which allow the operation to take place. The sequence of events that occurs during an agent response to an NMS request is as follows:
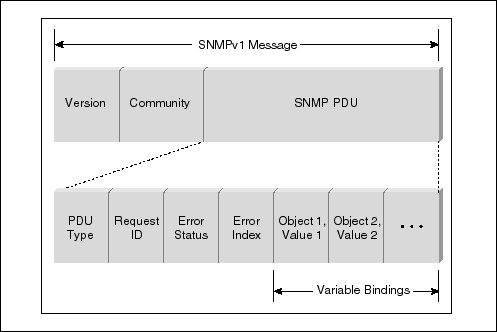
SNMP MessagesThe TCP/IP protocol stack views SNMP as an application, which in many ways is true. However, it is more than just an application, it is a protocol as well. When data is requested of NMS, it passes the request onto SNMP. At that time, SNMP looks at the type of data requested and decides upon which message to send. The two types of SNMP messages—SNMPv1 and SNMPv2—are described in the following sections. SNMPv1 Messages SNMPv1 messages (packets) contain two parts. The first part contains a version and a community name. The second part contains the actual SNMP protocol data unit (PDU) specifying the operation to be performed (get, set, and so on) and the object instances involved in the operation. Figure 9-8 illustrates the SNMPv1 message format.
The SNMP Version field is used to ensure that all network elements are running software based on the same SNMP version. The community name assigns an access environment for a set of NMSs using that community name. NMSs within the community can be said to exist within the same administrative domain. Because devices that do not know the proper community name are precluded from SNMP operations, network management personnel also have used the community name as a weak form of authentication. The SNMP Protocol Data Unit (PDU) has the following fields:
SNMPv2 Messages Even though SNMPv2 will be formally presented in Chapter 12, it is more logical to include its message format here while covering SNMPv1. Like SNMPv1 messages, SNMPv2 messages (shown in Figure 9-9) contain two parts. The first part of the SNMPv2 message (often referred to as a wrapper) contains the majority of the differences between SNMPv1 and SNMPv2. The second part of the SNMPv2 message (the PDU) is virtually identical to a SNMPv1 message (see the previous description of an SNMP PDU for differences).
The wrapper includes authentication and privacy information in the form of destination and source parties. As mentioned earlier, a party includes the specification of both an authentication and a privacy protocol. In addition to a destination and a source party, the wrapper includes a context, which specifies the managed objects visible to an operation. The authentication protocol is designed to reliably identify the integrity of the originating SNMPv2 party. It consists of authentication information required to support the authentication protocol used. The privacy protocol is designed to protect information within the SNMPv2 message from disclosure. Only authenticated messages can be protected from disclosure. In other words, authentication is required for privacy. This is covered in greater detail in Chapter 12. Additional Resources for SNMP
|
EAN: 2147483647
Pages: 200