| Previous | Table of Contents | Next |
OSI Reference Model Layers and Information Exchange The seven OSI layers use various forms of control information to communicate with their peer layers in other computer systems. This control information consists of specific requests and instructions that are exchanged between peer OSI layers. Control information typically takes one of two forms: - Headers: Appended to the front of data passed down from upper layers.
- Trailers: Appended to the back of data passed down from upper layers.
An OSI layer is not necessarily required to attach a header or trailer to upper layer data.
Notes:
Even though OSI is currently one of the most widely recognized frameworks, that was not always the case. Several other frameworks, such as the Digital Network Architecture (DNA), used to compete with ISO, but they did not stand the test of time.
Headers and Data Headers (and trailers) and data are relative concepts, depending on the layer that is analyzing the information unit at the time. For example, at the Network layer, an information unit consists of a Layer 3 header and data, known as the payload. At the Data Link layer (Layer 2), however, all of the information passed down by the Network layer (the Layer 3 header and the data) is treated simply as data. In other words, the data portion of an information unit at a given OSI layer can potentially contain headers, trailers, and data from all of the higher layers. This is known as encapsulation. Figure 1-6 shows the header and data from one layer encapsulated in the header of the next lowest layer. 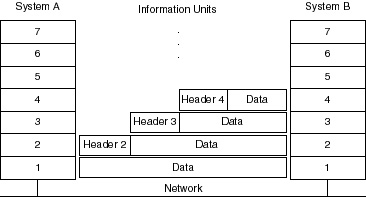
Figure 1-6 OSI packet encapsulation through the OSI layers.
How Does the OSI Reference Model Process Work? Every person who uses a computer residing upon a network is operating under the OSI reference model. The following real world example takes this statement a step further. You have written an e-mail message and want to send it a coworker (Dan) who is in another state. The following sequence illustrates how this transaction operates under the OSI reference model. Figure 1-7 depicts the necessary sequence of events. 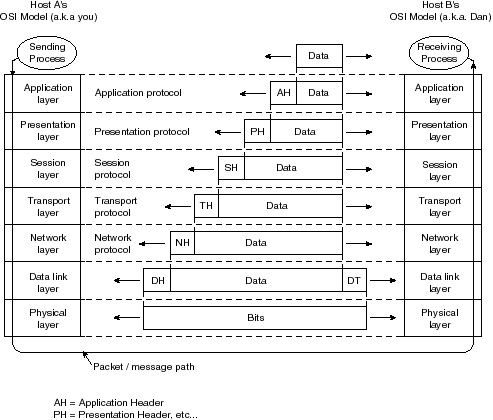
Figure 1-7 How the OSI reference model is used.
- 1. You finish writing your e-mail message and enter the send command.
- 2. The e-mail application determines how the workstation is configured to process this command. In this scenario, the workstation is connected via an Ethernet card to the LAN.
- 3. The e-mail application knows that the message needs to be formatted a certain way to be sent. The e-mail application knows how do this because its code is written to interpret the command and sends the data. The e-mail application begins the encapsulation process and sends the message through the first three top layers of the OSI reference model: Application, Presentation, and Session.
- 4. Within the workstation, the encapsulated e-mail message is sent to the Ethernet card. The e-mail message becomes encapsulated in whatever protocol stack happens to be configured on the PC. For purposes of this discussion you will assume TCP/IP is configured.
- 5. The Ethernet card receives the message and knows that all outgoing traffic must be TCP, so it encapsulates the message accordingly (that is, the packet now contains the destination IP address). The message has now passed through Layer 4, the Transportation layer.
- 6. Further encapsulation takes place at the Network layer (Layer 3), which is IP in this scenario. The message is now further encapsulated in IP. Here, between Layers 3 and 4, ARP is executed to find out the next hops IP address, and the information is added to the IP packet.
- 7. The message is now ready to leave the network card; however, the type of LAN on which the message is going to be traveling must be determined (Ethernet, token ring, FDDI, and so on). In this case, the LAN is Ethernet, so the Data Link layer (Layer 2) encapsulates the message to travel on an Ethernet segment.
- 8. Now the message needs to know the type of physical connection from which it has to enter the LAN segment. Let s say your workstation happens to use an RJ45 cable. Therefore, the very last encapsulation is done at the Physical layer (Layer 1). The message is now transitioned to use the RJ45 physical connection type.
- 9. POOF! In a zing of electrons, the ones and zeros in the message to Dan now become a series of voltages and electrical impulses out onto your LAN ready for transmission.
- 10. The message enters the Ethernet interface as a series of bits that the interface can interpret and process, based upon a set of standards that define the interface.
- 11. The information that has been received is error-checked using a Cycle Redundancy Check (CRC). If the frame is received intact, the interface continues to process the packet by looking for the destination address in the IP packet header. If the destination is not found, the frame is discarded and an error is registered on the interface. The end user will then need to resend the message.
- 12. At this point, the interface acts as an interpreter for the binary transmissions, and forwards the data based upon the logical destination address.
- 13. The device (router, bridge, hub, and so forth) continues to forward the message based upon the type of media (Frame Relay, ISDN, ATM, and so on) needed to connect to Dan s LAN.
- 14. After the message reaches the device that is physically connected to Dan s LAN, steps 11, 12, and 13 are repeated inversely until the message is sent onto the LAN to which Dan s workstation is connected.
- 15. Steps 1-9 are now repeated inversely as all of the information on how to send the data, how to route the data, and so forth that is needed to deliver the message is transferred to Dan s e-mail application.
- 16. TADA! You ve Got Mail.
- 17. Now Dan determines the importance of the message and whether to read it now or wait until his schedule permits.
| Previous | Table of Contents | Next |
|

