Lesson 2: Managing Groups in Windows Server 2003
|
| < Day Day Up > |
|
A group is a collection of user accounts. You can use groups to efficiently manage access to domain resources, which helps simplify network maintenance and administration. For example, if all employees in the research department should have access to a file server, you could grant each individual the right to read the files. However, each time an employee joined or left the research department, you would need to manually add or remove the employee from the file share's access control list. If you had hundreds of such network resources, this would be impossible to manage. A better way to organize this is to place all members of the research department into a group named Research, and then assign privileges to the Research group. When employees change departments, you only need to modify the Research group membership.
You can use groups separately, or you can place one group within another to further reduce the amount of administration involved in managing groups. For example, if you have created separate groups for the research departments on the East and West coasts, you could place both groups into a national Research group. This simplifies administration in the same way as putting user accounts into groups.
Before you can use groups effectively, you must understand the types of groups available in a Windows Server 2003 environment, and the function of those groups.
This lesson describes the types of groups that you can create in Windows Server 2003. The lesson also describes the behavior of global, domain local, and universal groups and the strategies to use when implementing groups.
After this lesson, you will be able to
-
Determine the type of group to create in Windows Server 2003 to meet the security requirements of your organization.
-
Determine the domain functionality-level impact on group nesting and universal groups.
-
Select an appropriate built-in group for controlling access to resources.
-
Select an appropriate special group for controlling access to resources.
-
Select appropriate tools for administering groups in Windows Server 2003.
-
Create a Restricted Group Policy.
Estimated lesson time: 30 minutes
Types of Groups in Windows Server 2003
You use groups to organize user accounts, computer accounts, and other group accounts into manageable units. While the local user databases on member servers and standalone servers only support security groups, there are two types of groups in Active Directory: distribution groups and security groups.
]Distribution groups are primarily used for sending e-mail to multiple users. You can use distribution groups with Active Directory-aware applications and e-mail applications, such as Microsoft Exchange Server and Microsoft Outlook, to send messages to users that are contained in the distribution group. Distribution groups are not security- enabled, and cannot be listed in ACLs. In other words, if you have created a distribution group for the human resources department, you cannot use the group to grant the members of that group access to a printer. You can, however, send the group an e-mail message telling them that they'll have access to their new printer as soon as you create a security group.
Security groups can be used to grant (or deny) access to network resources, because security groups can be listed in ACLs. For example, granting the Research security group Read access to a shared folder will enable the members of that group to access the files. Security groups can also be used for e-mail distribution. So you could use the Research security group to grant access to a shared folder, and then send an e-mail message to the group letting them know that they now have access to their files.
| Tip | Security groups do everything distribution groups do, and more. However, distribution groups should be used whenever possible because they do not become part of a user's security token. This makes the authentication process quicker than if a security group were used. |
You can use nesting to place one or more groups into another group. For example, if you need two separate groups named Accounts Payable and Accounts Receivable for users in the Accounting group, you could nest them into another group called All Accounting. You can then use the All Accounting group when assigning permissions for resources that all members of the accounting department should access. When you use nested groups, a group inherits the permissions of the group of which it is a member, which simplifies the process of assigning permissions to several groups at one time.
| Warning | In a mixed-mode domain, you cannot nest groups that have the same group scope. For example, if my domain was at Windows 2000 Mixed-Mode, you would not be able to nest global groups inside of other global groups. You can nest global groups only when the domain functional level is set to Windows 2000 native or higher. Group scope is described in the next section. |
Group Scopes
Each group in Windows Server 2003 has a scope attribute, which determines which security principals can be members of the group and where you can use that group in a multidomain or multiforest environment. Windows Server 2003 supports the following group scopes:
-
Local Groups. Local groups reside on member servers and client computers. Use a local group to grant access to local resources on the computer where they reside.
Note Local groups are the only group type available in a non-domain environment.
-
Global Groups. Global groups reside in Active Directory at the domain level. Use a global group to organize users who share the same job tasks and need similar network access requirements, such as all accountants in an organization's accounting department. Global groups can be members of other global groups, universal groups, and domain local groups.
-
Domain Local Groups. Domain local groups reside in Active Directory at the domain level. Use a domain local group when you want to assign access permissions to resources that are located in the same domain in which you create the domain local group. You can add all global groups that need to share the same resources to the appropriate domain local group.
-
Universal Groups. Universal groups reside in Active Directory at the forest level. Use universal groups when you want to nest global groups so that you can assign permissions to related resources in multiple domains. Universal groups can be members of other universal groups, global groups, and domain local groups. The Windows Server 2003 domain functional level must be at Windows 2000 native mode or higher to use universal security groups. You can use universal distribution groups in a Windows Server 2003 domain that is in Windows 2000 mixed mode and higher.
Figure 2.5 shows the relationship between the group scopes, with arrows used to indicate which group types can be nested within other group types.
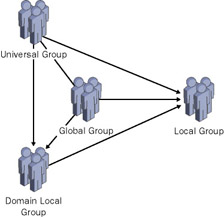
Figure 2.5: Some group types can be nested within other group types
| Note | The domain functional level determines the type of group that you can create. For example, not all group types are available until the domain functional level has been raised. You will learn more about domain functional levels in later topics. |
Domain and Forest Functional Levels
In Windows Server 2003, the forest or domain functional level defines which advanced features are available to domain controllers in the organization. The functional level of a domain or forest will also define which versions of operating systems can run on domain controllers. For example, if all domain controllers in your domain or forest are running Windows Server 2003 and the forest functional level is set to Windows Server 2003, all domain- and forest-wide features are available. When Microsoft Windows NT 4.0 or Windows 2000 domain controllers are included in your domain or forest with domain controllers running Windows Server 2003, Active Directory features are limited. The domain and forest functional levels for a domain determine which group types will be available in Windows Server 2003.
| Caution | Raising a functional level has the potential to alienate older operating systems. For example, if you raise the domain functional level to Windows 2000 native mode and Windows NT 4.0 domain controllers are present, they will no longer participate in replication. |
Table 2.1 lists the four domain functional levels and a list of features relevant to security associated with each level.
| Domain functional level | Features |
|---|---|
| Windows 2000 mixed | Universal groups (distribution only) Groups nesting (distribution only) |
| Windows 2000 native | Universal groups Nesting groups Converting groups SID history |
| Windows Server 2003 interim | Renaming domain controllers Update logon timestamp User password on InetOrgPerson object Universal groups Nesting groups Converting groups SID history |
| Windows Server 2003 | Renaming domain controllers Update logon timestamp User password on InetOrgPerson object Universal groups Nesting groups Converting groups SID history |
| See Also | For more information about the features available for each domain functional level, see Windows Server 2003 Help and Support or Microsoft Technet at http://www.microsoft.com |
| Note | When you first install Windows Server 2003, the default domain functional level is Windows 2000 mixed. When you raise the domain functional level to Windows 2000 native, Windows Server 2003 interim, or Windows Server 2003, the applicable features for that domain are enabled. |
Table 2.2 lists the forest functional levels and a list of relevant features associated with each level.
| Forest functional level | Features |
|---|---|
| Windows 2000 | Global catalog Partial Attribute Set (PAS) replication improvements (Windows Server 2003 global catalogs only) |
| Windows 2003 Interim | Global catalog PAS replication improvements |
| Windows Server 2003 | Global catalog PAS replication improvements |
| See Also | For more information about the features available for each forest functional level, see Windows Server 2003 Help and Support or Microsoft Technet at http://www.microsoft.com/technet/prodtechnol/windowsserver2003/proddocs/standard/sag_levels.asp. |
A detailed discussion of the features of Windows Server 2003 for each functional level is beyond the scope of this book.
Built-In Groups
Windows Server 2003 provides many built-in groups. Built-in groups are automatically created when you create an Active Directory domain. You can use built-in groups to manage access to shared resources and to delegate specific domain-wide administrative roles. For example, you could put the user account of a junior administrator into the Account Operators group to allow the junior administrator to create user accounts and groups.
Many built-in groups are automatically assigned a set of user rights that determine what each group and their members can do within the scope of a domain or forest. User rights authorize members of a group to perform specific actions, such as logging on to a local system or backing up files and folders. For example, a member of the Backup Operators group has the right to perform backup operations for all domain controllers in the domain. Therefore, to create an effective security strategy for a network, it is important that you understand the default rights associated with each built-in group. This section describes each built-in group and the rights and capabilities associated with each.
Account Operators
Members of the Account Operators group can create, modify, and delete accounts for users, groups, and computers located in the Users or Computers containers and organizational units in the domain, except the Domain Controllers organizational unit. Members of this group do not have permission to modify the Administrators or the Domain Admins groups, nor do they have permission to modify the accounts for members of those groups. Members of this group can log on locally to domain controllers in the domain and shut them down. Because this group has significant power in the domain, add users with caution. Members of this group have the following default user rights:
-
Allow logon locally.
-
Shut down the system.
Warning Do not change the default user right assignments on a production computer unless you really know what you are doing. If you do get into a position where you need to restore the default user right assignments, use the setup security.inf security template provided with Windows Server 2003. Security templates are covered in more detail in Chapter 3, 'Deploying and Troubleshooting Security Templates.'
Administrators
Members of the Administrators group have full control of the server and can assign user rights and access control permissions to users as necessary. Add users with caution. When joined to a domain, the Domain Admins group is automatically added to this group. The default Administrator user account is made a member of the Administrators group. Members of this group have almost every user right available on a system.
Backup Operators
Members can back up and restore all files on domain controllers in the domain, regardless of their own individual permissions on those files. Backup Operators can also log on to domain controllers and shut them down. This group has no default members. Because this group has significant power on domain controllers, add users with caution. Members of this group have the following default user rights:
-
Back up files and directories.
-
Allow logon locally.
-
Restore files and directories.
-
Shut down the system.
Incoming Forest Trust Builders
This group only appears in the forest root domain. Members of this group can create one-way, incoming forest trusts to the forest root domain. For example, members of this group residing in Forest A can create a one-way, incoming forest trust from Forest B. This one-way, incoming forest trust allows users in Forest A to access resources located in Forest B. Members of this group are granted the Create Inbound Forest Trust permission on the forest root domain. This group has no default members and no default user rights.
Network Configuration Operators
This group is intended to be used for staff responsible for managing the network configuration of servers and workstations in a domain. Members of this group can make changes to Transmission Control Protocol/Internet Protocol (TCP/IP) settings and renew and release TCP/IP addresses on domain controllers in the domain. This group has no default members and no default user rights.
Performance Log Users
Members of this group can manage performance counters, logs, and alerts on domain controllers in the domain, locally and from remote clients, without being a member of the Administrators group. Members of this group have no default user rights.
Performance Monitor Users
Members of this group can monitor performance counters on domain controllers in the domain, locally and from remote clients, without being a member of the Administrators or Performance Log Users groups. This group has no default members and no default user rights.
Pre-Windows 2000 Compatible Access
Members of this group have read access on all users and groups in the domain. This group is provided for backward compatibility with computers running Windows NT 4.0 and earlier. By default, the special identity Authenticated Users is a member of this group. Members of this group have the following default user rights:
-
Access this computer from the network.
-
Bypass traverse checking.
Print Operators
Members of this group can manage, create, share, and delete printers connected to domain controllers in the domain. They can also manage Active Directory printer objects in the domain. Because members of this group can load and unload device drivers on all domain controllers in the domain, add users with caution. A member of the Print Operators group with malicious intent could take control of a domain controller. This group has no default members. Members of this group have the following default user rights:
-
Allow logon locally.
-
Shut down the system.
Remote Desktop Users
Members of this group can remotely log on to domain controllers in the domain. This group has no default members and no default user rights.
Replicator
This group supports directory replication functions and is used by the File Replication service on domain controllers in the domain. This group has no default members and no default user rights. Because this group is owned by the operating system, adding users to this group can cause problems with the File Replication Service.
Server Operators
On domain controllers, members of this group can log on interactively, create and delete shared resources, start and stop some services, back up and restore files, format the hard disk, and shut down the computer. This group has no default members. Members of this group have the following default user rights:
-
Back up files and directories.
-
Change the system time.
-
Force shutdown from a remote system.
-
Allow logon locally.
-
Restore files and directories.
-
Shut down the system.
Terminal Server License Servers
Members of this group have access to Terminal Server License Servers on the system. This group has no default members and no default user rights.
Users
Members of this group can perform most common tasks, such as running applications, using local and network printers, and locking the server. By default, the Domain Users group, the Authenticated Users group, and the Interactive group are members of this group. All user accounts in the domain are members of this group. Members of this group have no default user rights.
Windows Authorization Access Group
This group exists to simplify granting accounts permission to query a user's group information. Members of this group have access to the computed tokenGroupsGlobalAndUniversal attribute on User objects. Add members to this group only when specifically required by an application. By default, only the Enterprise Domain Controllers group is a member of this group.
| See Also | For more information about built-in groups see http://www.microsoft.com/technet/prodtechnol/windowsserver2003/proddocs/entserver/sag_ADgroups_9builtin_intro.asp. |
In the real world, the built-in groups are often misused. It's a common practice to add users to the Power Users group so that an application that won't run with regular User privileges will work as expected. While this is better than adding the user to the Administrators group, there is a risk associated with this practice-the risk that the user will be granted unnecessary rights that will later be misused. Even if the user would never intentionally misuse the elevated privileges of the Power Users group, a virus or Trojan horse might take advantage of the additional privileges without the user being aware.
Special Groups and Accounts
Servers running Windows Server 2003 include several special identities in addition to the groups in the Users and Builtin containers. These identities are generally referred to as special groups. Special groups, also called special identities, are designed to provide access to resources without administrative or user interaction.
| Tip | You can recognize most special groups because their names are in all capital letters. There are a few exceptions to this, however, such as the Authenticated Users special group. |
Users become members of special groups by simply interacting with the operating system. For example, when users log on locally to a computer, they become members of the Interactive group. You can grant user rights and permissions to these special groups, but you cannot modify or view their memberships. In addition, group scopes do not apply to special groups.
It is important to understand the purpose of special groups because you can use them for security administration, as they allow you to create more granular access policies and control access to resources. To understand how special groups help provide secure access, consider blocking access for dial-up users to a folder containing confidential documents. As shown in Figure 2.6, denying access to a folder is as simple as adding the Dialup special group to the folder's ACL.
Figure 2.6: You can assign permissions to special groups that apply to users based on how they connect to the network
Following are the special groups included in Windows Server 2003 that can be used to control access to resources in an organization.
| Exam Tip | Digest Authentication, Schannel Authentication, NTLM Authentication, Proxy, Remote Interactive Logon, and Restricted are special groups and accounts that appear when browsing accounts. However, they are rarely used and are not likely to be covered on the exam. |
Anonymous Logon
The Anonymous Logon special group represents users and services that access a computer and its resources through the network without using an account name, password, or domain name. On computers running Windows NT and earlier, the Anonymous Logon special group is a member of the Everyone group by default. On computers running a member of the Windows Server 2003 family, the Anonymous Logon special group is not a member of the Everyone group by default. If you want to create a file share for an anonymous user, grant permissions to the Anonymous Logon special group.
Authenticated Users
The Authenticated Users special group represents all users and computers whose identities have been authenticated. Authenticated Users does not include Guest even if the Guest account has a password. Membership in the Authenticated Users special group is mutually exclusive to membership in the Anonymous Logons special group.
Batch
The Batch special group includes all users and services that access a computer and its resources through the network by using a batch queue facility, for example, task scheduler jobs.
Creator Group
The Creator Group special group includes the user account for the user who created the resource. The Creator Group special group is a placeholder in an inheritable ACE. When the ACE is inherited, the system replaces this security identifier (SID) with the SID for the primary group of the object's current owner.
Creator Owner
The Creator Owner special group includes the user account for the user who created or took ownership of a resource. If a member of the Administrators group creates a resource, the Administrators group is the owner of the resource. The Creator Owner special group is a placeholder in an inheritable ACE. When the ACE is inherited, the system replaces this SID with the SID for the object's current owner.
Dialup
The Dialup special group includes all users who are logged on to the system through a dial-up connection.
Everyone
The Everyone special group represents all current network users, including guests and users from other domains. Whenever a user logs on to the network, the user is automatically added to the Everyone special group. The Anonymous Logon special group is no longer contained in the Everyone special group, as in previous versions of Windows Server.
Interactive
The Interactive special group represents all users currently logged on to a particular computer and accessing a given resource located on that computer, as opposed to users who access the resource over the network. Whenever a user accesses a resource on the computer to which they are currently logged on, the user is automatically added to the Interactive special group.
Local Service
The Local Service account is a special built-in account that is similar to an authenticated user account. The Local Service account has the same level of access to resources and objects as members of the Users group. This limited access helps safeguard your system if individual services or processes are compromised. Services that run as the Local Service account access network resources as a null session with no credentials.
Network
The Network special group represents users currently accessing a given resource over the network, as opposed to users who access the resource by logging on locally at the computer on which the resource is located. Whenever a user accesses a given resource over the network, the user is automatically added to the Network special group.
Network Service
The Network Service account is a special built-in account that is similar to an authenticated user account. The Network Service account has the same level of access to resources and objects as members of the Users group. This limited access helps safeguard your system if individual services or processes are compromised. Services that run as the Network Service account access network resources using the credentials of the computer account.
Other Organization
This special group contains users who authenticated from another domain. Adding this special group to an ACL causes a check to ensure that a user from another forest or domain that is trusted is allowed to authenticate to a particular service in the trusted domain.
Self
The Self special group is a placeholder group in an ACE on a user, group, or computer object in Active Directory. When you grant permissions to Principal Self, you grant them to the security principal represented by the object. During an access check, the operating system replaces the SID for Principal Self with the SID for the security principal represented by the object.
Service
The Service special group is a group that includes all security principals that have logged on as a service. Membership is controlled by the operating system.
System
The System special group is used by the operating system and by services that run under Windows. It has privileges that are similar to those of the Administrators group. The System account is an internal account, does not show up in User Manager, cannot be added to any groups, and cannot have user rights assigned to it. The System account does show up when assigning file permissions, however.
Terminal Server Users
The Terminal Server Users special group includes all users who have logged on to a Terminal Services server that is in Terminal Services version 4.0 application compatibility mode.
This Organization
When there are trusted domains for forests, the This Organization special group is added by the authentication server to the authentication data of a user to identify the user's organization, provided the Other Organization SID is not already present.
Tools for Administering Security Groups
Windows Server 2003 supports a number of tools that make it easy for you to troubleshoot and enumerate groups and their members. Table 2.3 outlines the tools related to administering security groups and their functions:
| Tool | Description |
|---|---|
| Active Directory Users and Computers | Graphical tool used to administer users and groups in Active Directory. This tool can be started from the Administrative Tools program group. |
| Dsadd | Command-line tool for creating groups and manipulating group membership. |
| Getsid | Command-line tool for comparing the SIDs of two user accounts. |
| Ifmember | Command-line tool for enumerating all groups that the current member belongs to. Commonly used in logon scripts. This tool is one of the Windows Server 2003 Resource Kit tools. |
| Local Users and Groups | MMC snap-in that enables the creation and editing of users and groups in the local user database. This snap-in is often accessed from the Computer Management console. This tool is not available on domain controllers. |
| Whoami | Command-line tool capable of displaying the complete contents of the access token. It can display the user name and SID, the groups and their SIDs, the privileges and their status (for example, enabled or disabled), and the logon ID. For usage information, execute whoami /? at a command prompt. |
| See Also | For more information about the parameters for the security group administration tools, see A-Z Command Line Reference in Windows Server 2003 Help and Support. |
Creating Restricted Groups Policy
Earlier in this chapter, you learned that you can assign rights to computers by using both the groups stored on individual computers and groups stored in Active Directory. It would be difficult, however, to manually add a new IT group that you created in Active Directory as a member of the Administrators local group on every computer in an enterprise. Fortunately, you can use security policies to control local group memberships on domain member computers.
Windows Server 2003 includes a security policy setting called Restricted Groups that allows you to control group membership. By using the Restricted Groups policy, you can specify the membership of a group anywhere in your Active Directory domain. For example, you can create a Restricted Groups policy to limit the access on an OU that contains computers containing sensitive data. The Restricted Groups policy would remove domain users from the local users group and thereby limit the number of users who can log on to the computer. Group members that are not specified in the policy are removed when the Group Policy setting is applied or refreshed to the computer or OU. The Restricted Groups policy settings include two properties: Members and Member Of. The Members property defines who belongs and who does not belong to the restricted group. The Member Of property specifies the other groups to which the restricted group can belong.
When a Restricted Groups policy is enforced, any current member of a restricted group that is not on the Members list is removed. Members who can be removed include Administrators. Any user on the Members list who is not currently a member of the restricted group is added. In addition, each restricted group is a member of only those groups that are specified in the Member Of column.
Figure 2.7 shows Restricted Groups being used to add the IT security group from the cohowinery.com domain to the local Administrators group on all domain member computers.
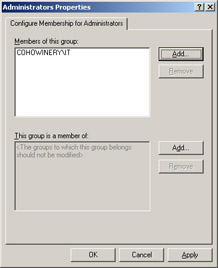
Figure 2.7: Use Restricted Groups to control group membership on domain members
| Note | The security setting is located in a security policy object in the Restricted Groups node. |
You can apply a Restricted Groups policy in the following ways:
-
Define the policy in a security template, which will be applied during configuration on your local computer.
-
Define the setting directly on a Group Policy object (GPO). Defining the setting in this way will ensure that the operating system continually enforces the restricted groups.
To create a Restricted Groups policy:
-
Open a security policy tool, such as the Domain Security Policy console.
-
In the console tree, right-click Restricted Groups, and then click Add Group.
-
In the Group field, type the name of the group to which you want to restrict membership, and then click OK.
-
On the properties dialog box, click Add beside the This Group Is A Member Of field.
-
Under Group Membership, type the name of the group you want to add to this group, and then click OK.
-
Click OK again.
Practice: Creating Groups and Assigning Rights
In this practice, you will create a restricted group and assign appropriate rights to the members of the group. To complete this practice, you must be logged in with an account that has permission to create and manage groups and GPOs in Active Directory. Complete this task from Computer1.cohowinery.com.
You are the security administrator for the Coho Winery organization. Your organization recently hired several new staff members to support desktop computers. These staff members should have administrative rights to all member computers in the domain, but they should not have rights to domain controllers. You decide to create a group for the new staff members and to add that group to the local Administrators group on all non-domain controller computers in your domain.
Exercise 1: Create a New Security Group
Create a new security group called Desktop Support.
-
Open Active Directory Users And Computers.
-
In the console tree, right-click the Users container, point to New, and then click Group.
-
In the New Object - Group dialog box, in the Group Name field, type Desktop Support.
-
Click OK.
Exercise 2: Configure the Domain Security Policy
-
Open the Domain Security Policy console.
-
In the console tree, right-click Restricted Groups, and then click Add Group.
-
Click the Browse button to select the Desktop Support group. Click OK.
-
On the Desktop Support Properties page, click Add beside the This Group Is A Member Of field.
-
Under Group Membership, type Administrators, and then click OK.
Exercise 3: Populate the Group
Finally, populate the Desktop Support security group with the following users:
-
Jo Berry
-
Ken Sanchez
-
Nancy Buchanan
-
Open a command prompt.
-
Type the following text, and then provide a complex password when prompted: dsadd user 'cn=Jo Berry,cn=Users,dc=cohowinery,dc=com' -disabled no -memberof 'cn=Desktop Support,cn=Users,dc=cohowinery,dc=com' -pwd *
-
Type the following text, and then provide a complex password when prompted: dsadd user 'cn=Ken Sanchez,cn=Users,dc=cohowinery,dc=com' -disabled no -memberof 'cn=Desktop Support,cn=Users,dc=cohowinery,dc=com' -pwd *
-
Type the following text, and then provide a complex password when prompted: dsadd user 'cn=Nancy Buchanan,cn=Users,dc=cohowinery,dc=com' -disabled no -memberof 'cn=Desktop Support,cn=Users,dc=cohowinery,dc=com' -pwd *
Lesson Review
The following questions are intended to reinforce key information presented in this lesson. If you are unable to answer a question, review the lesson materials and try the question again. You can find answers to the questions in the 'Questions and Answers' section at the end of this chapter.
-
Which of the following built-in groups is present on a domain controller?
-
Administrators
-
Power Users
-
DHCP Users
-
Backup Operators
-
-
Which of the following special groups could you assign to an ACL to prevent access from unauthenticated users?
-
Everyone
-
Anonymous Logon
-
Authenticated Users
-
Interactive
-
-
Which of the following are not available at the Windows 2000 native domain functional level?
-
Universal groups
-
Nesting groups
-
Converting groups
-
Renaming domain controllers
-
SID history
-
-
Which of the following group types could be nested within a universal group?
-
Local group
-
Domain local group
-
Global group
-
Distribution group
-
Lesson Summary
-
You can use groups to efficiently manage access to domain resources, which helps simplify administration.
-
There are two types of groups in Active Directory: distribution groups and security groups.
-
Groups are characterized by a scope that identifies the extent to which the group is applied in the domain tree or forest. The group scope determines whether the group spans multiple domains or is limited to a single domain. Windows Server 2003 supports the following group scopes:
-
Local
-
Global
-
Domain Local
-
Universal
-
-
Depending on the functional level, certain features are enabled or disabled in Active Directory.
-
The default domain functional level is Windows 2000 mixed. When you raise the domain functional level to Windows 2000 native, Windows Server 2003 interim, or Windows Server 2003, the applicable features for that domain are enabled.
-
You can use built-in groups to manage shared resources and delegate specific domain-wide administrative roles.
-
Special groups, also called special identities, are designed to provide access to resources without administrative or user interaction.
-
You can use Restricted Groups policy to control group membership.
|
| < Day Day Up > |
|
EAN: 2147483647
Pages: 217