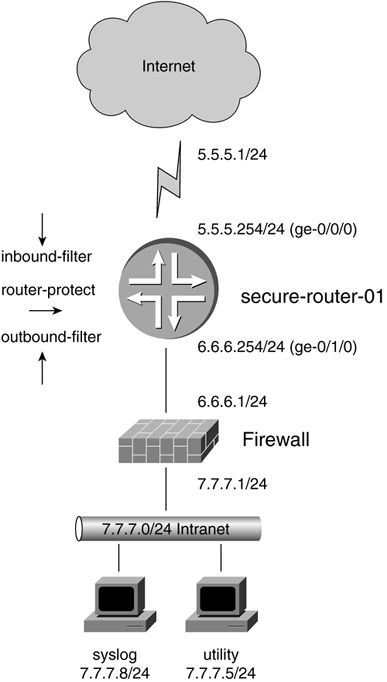
Case Study: Securing a Juniper Networks Router
| This case study has been designed to provide you with a secure template with comments that explain the various firewall filters and other parameters. The goal of this template is to ensure that any Juniper Networks router can be completely and fully secured. Of course, the configuration here is super safe; however, your network may have other security tools in place already. Please feel free to alter and adjust this configuration file as needed to meet your needs. In Figure 6-12 we have named the Juniper Networks router secure-router-01 and placed it as the router that connects our network to the Internet. This connection is, of course, GigE! Figure 6-12. Case Study Network As you read through this configuration, notice that we have highlighted various sections to reflect comments placed therein. These comments are designed to help you understand the various configurations presented. The comments are placed before the commands they will be discussing. This configuration was developed under JUNOS 4.3R3 by Stephen R. Gill (gillsr@yahoo.com) to serve as a reference and starting point for those interested in increasing the level of security on their Juniper Networks routers, and in turn , on their networks. Its original annotations have been expanded, and it has been sourced with express written permission from the author. Additionally, the most recent version of the template along with other JUNOS-security- related articles can be found at www.qorbit.net. /* ... begin template ... */ version 4.3R3; system { host-name secure-router-01; /* Enable a backup router during boot for ntp. It will be used before rpd has started or if it fails. */ backup-router 6.6.6.1 destination 7.7.7.0/24; time-zone America/Chicago; /* Do not send ICMP redirects */ no-redirects; /* Use local password authentication if TACACS+ fails */ authentication-order [ tacplus password ]; location country-code US; /* Configure authentication passwords */ diag-port-authentication { encrypted-password "<PASSWORD>"; # SECRET-DATA } root-authentication { encrypted-password "<PASSWORD>"; # SECRET-DATA } /* Enable TACACS+ authentication. */ tacplus-server { 7.7.7.5 { secret "<PASSWORD>"; # SECRET-DATA /* Wait 5 seconds until timeout */ timeout 5; } } login { /* A stern Message of the Day (MOTD) banner */ message "********************************************************\n * [WARNING] secure-router-01 *\n * This system is owned by [COMPANY]. If you are not *\n * authorized to access this system, exit immediately. *\n * Unauthorized access to this system is forbidden by *\n * company policies, national, and international laws. *\n * Unauthorized users are subject to criminal and civil *\n * penalties as well as company initiated disciplinary *\n * proceedings. *\n * *\n * By entry into this system you acknowledge that you *\n * are authorized access and the level of privilege you *\n * subsequently execute on this system. You further *\n * acknowledge that by entry into this system you *\n * expect no privacy from monitoring. *\n ********************************************************\n"; /* Configure an administrator class with all privileges. We cannot modify the predefined classes, so we must create our own. */ class admin { /* Causes telnet sessions to time out after 15 minutes of inactivity */ idle-timeout 15; permissions all; } /* Configure a view-only account especially good for use by junior engineers or directors */ class view-only { idle-timeout 15; permissions [ configure firewall interface network routing snmp system trace view]; } /* This is a superuser account */ user admin { full-name Administrator; uid 2000; class admin; authentication { encrypted-password "<PASSWORD>"; # SECRET-DATA } } /* This is a view-only user account */ user ops { full-name Operations; uid 2001; class view-only; authentication { encrypted-password "<PASSWORD>"; # SECRET-DATA } } /* This is the template account used by TACACS+ and MUST be here. TACACS+ is limited to 1 template account, RADIUS can have many */ user remote { full-name "All remote users"; uid 9999; class admin; } } /* List of IPs and their hostnames to allow easy English reference to the devices within the network */ static-host-mapping { /* Put localhost entry for NTP to work */ localhost inet 127.0.0.1; firewall-ext inet 6.6.6.1; firewall-int inet 7.7.7.1; upstream inet 5.5.5.1; utility inet 7.7.7.5; syslog inet 7.7.7.8; } /* Enable router services */ services { /* Enable 5 ssh sessions. Max 10 connection attempts per minute. */ ssh connection-limit 5 rate-limit 10; } syslog { /* Archive old files up to 10MB total (1 MB per file), thereby giving a good historical view of what is happening on the router*/ archive size 1m files 10; user * { any emergency; } /* Transmit log data over to the corporate syslog server */ host 7.7.7.8 { any info; } file messages { any notice; authorization info; } } /* Synchronize the clock with a trusted authenticated NTP server */ ntp { authentication-key 6767 type md5 value "<PASSWORD>"; # SECRET-DATA /* NTP will not sync if times are too different, so remember to set the router's time at bootup */ boot-server 7.7.7.5; server 7.7.7.5; } } chassis { /* Disable source routing */ no-source-route; } interfaces { /* Log additional interface information to aid in troubleshooting. To view, use 'show log log-interfaces' */ traceoptions { /* Rotate through 5 files at 1MB each */ file log-interfaces size 1m files 5; /* Trace changes that produce configuration events */ flag change-events; } ge-0/0/0 { description "Upstream Interface - facing Internet"; /* Enable snmp-traps for this interface */ traps; link-mode full-duplex; unit 0 { family inet { /* Do not send ICMP redirect messages */ no-redirects; /* Filter inbound packets from the Internet */ filter { input inbound-filter; } address 5.5.5.254/24; } } } ge-0/1/0 { description "Protected Interface - facing DMZ" traps; link-mode full-duplex; unit 0 { family inet { no-redirects; /* Filter outbound packets from the internal network */ filter { input outbound-filter; } address 6.6.6.254/24; } } } /* Configure management interface. Cannot route over this. */ fxp0 { description "Management Interface OOB management" unit 0 { family inet { no-redirects; address 10.10.11.11/24; } } } /* Configure loopback interface. Used for routing protocols and other purposes. */ lo0 { description "Loopback Interface internal" unit 0 { family inet { no-redirects; /* Restrict connections coming to this router */ filter { input router-protect; } address 10.10.10.10/32; } } } } forwarding-options { /* Enable packet sampling for CflowD */ sampling { input { family inet { /* Sample 1 out of 100 packets + next 4 in sequence. Total = 4/100 packets. You may want to just sample the SYN/FIN packets instead. */ rate 100; run-length 4; /* This is a built-in max throttle, listed here for completeness */ max-packets-per-second 7000; } } /* Send the output to the designated CflowD collector using v 8 */ output { cflowd 7.7.7.5 { port 2055; version 8; no-local-dump; autonomous-system-type origin; aggregation { autonomous-system; } } } } } snmp { description secure-router-01; location "Site, Row, Rack, Shelf"; contact "(555) 555-5555"; /* Restrict SNMP requests to a particular interface */ interface ge-0/1/0.0; /* Configure the SNMP community. Replace COMMUNITY with your string */ community COMMUNITY { authorization read-only; /* Determine who is allowed access via SNMP */ clients { default restrict; /* Restrict access to ALL but the following */ 7.7.7.5/32; } } /* Send traps using v2 for all categories to designated trap server */ trap-group all { version v2; categories authentication chassis link routing startup; targets { 7.7.7.5; } } } routing-options { options { /* Turn off DNS resolution */ no-resolve; syslog { level debug; } } /* Configure static routes */ static { /* Default route out to the Internet */ route 0.0.0.0/0 next-hop 5.5.5.1; /* Route to network on the other side of the Firewall */ route 7.7.7.0/24 next-hop 6.6.6.1; /* Black-hole routes for traffic destined to these networks */ route 0.0.0.0/8 discard; route 1.0.0.0/8 discard; route 2.0.0.0/8 discard; route 5.0.0.0/8 discard; route 7.0.0.0/8 discard; route 10.0.0.0/8 discard; route 23.0.0.0/8 discard; route 27.0.0.0/8 discard; route 31.0.0.0/8 discard; route 36.0.0.0/8 discard; route 37.0.0.0/8 discard; route 39.0.0.0/8 discard; route 41.0.0.0/8 discard; route 42.0.0.0/8 discard; route 49.0.0.0/8 discard; route 50.0.0.0/8 discard; route 58.0.0.0/8 discard; route 59.0.0.0/8 discard; route 60.0.0.0/8 discard; route 69.0.0.0/8 discard; route 70.0.0.0/8 discard; route 71.0.0.0/8 discard; route 72.0.0.0/8 discard; route 73.0.0.0/8 discard; route 74.0.0.0/8 discard; route 75.0.0.0/8 discard; route 76.0.0.0/8 discard; route 77.0.0.0/8 discard; route 78.0.0.0/8 discard; route 79.0.0.0/8 discard; route 82.0.0.0/8 discard; route 83.0.0.0/8 discard; route 84.0.0.0/8 discard; route 85.0.0.0/8 discard; route 86.0.0.0/8 discard; route 87.0.0.0/8 discard; route 88.0.0.0/8 discard; route 89.0.0.0/8 discard; route 90.0.0.0/8 discard; route 91.0.0.0/8 discard; route 92.0.0.0/8 discard; route 93.0.0.0/8 discard; route 94.0.0.0/8 discard; route 95.0.0.0/8 discard; route 96.0.0.0/8 discard; route 97.0.0.0/8 discard; route 98.0.0.0/8 discard; route 99.0.0.0/8 discard; route 100.0.0.0/8 discard; route 101.0.0.0/8 discard; route 102.0.0.0/8 discard; route 103.0.0.0/8 discard; route 104.0.0.0/8 discard; route 105.0.0.0/8 discard; route 106.0.0.0/8 discard; route 107.0.0.0/8 discard; route 108.0.0.0/8 discard; route 109.0.0.0/8 discard; route 110.0.0.0/8 discard; route 111.0.0.0/8 discard; route 112.0.0.0/8 discard; route 113.0.0.0/8 discard; route 114.0.0.0/8 discard; route 115.0.0.0/8 discard; route 116.0.0.0/8 discard; route 117.0.0.0/8 discard; route 118.0.0.0/8 discard; route 119.0.0.0/8 discard; route 120.0.0.0/8 discard; route 121.0.0.0/8 discard; route 122.0.0.0/8 discard; route 123.0.0.0/8 discard; route 124.0.0.0/8 discard; route 125.0.0.0/8 discard; route 126.0.0.0/8 discard; route 127.0.0.0/8 discard; route 169.254.0.0/16 discard; route 172.16.0.0/12 discard; route 192.0.2.0/24 discard; route 192.168.0.0/16 discard; route 197.0.0.0/8 discard; route 201.0.0.0/8 discard; route 220.0.0.0/8 discard; route 221.0.0.0/8 discard; route 222.0.0.0/8 discard; route 223.0.0.0/8 discard; route 240.0.0.0/4 discard; } } policy-options { prefix-list iana-reserved { /* IANA reserved networks that are not supposed to be in use */ 0.0.0.0/8; 1.0.0.0/8; 2.0.0.0/8; 5.0.0.0/8; 7.0.0.0/8; 23.0.0.0/8; 27.0.0.0/8; 31.0.0.0/8; 36.0.0.0/8; 37.0.0.0/8; 39.0.0.0/8; 41.0.0.0/8; 42.0.0.0/8; 49.0.0.0/8; 50.0.0.0/8; 58.0.0.0/8; 59.0.0.0/8; 60.0.0.0/8; 69.0.0.0/8; 70.0.0.0/8; 71.0.0.0/8; 72.0.0.0/8; 73.0.0.0/8; 74.0.0.0/8; 75.0.0.0/8; 76.0.0.0/8; 77.0.0.0/8; 78.0.0.0/8; 79.0.0.0/8; 82.0.0.0/8; 83.0.0.0/8; 84.0.0.0/8; 85.0.0.0/8; 86.0.0.0/8; 87.0.0.0/8; 88.0.0.0/8; 89.0.0.0/8; 90.0.0.0/8; 91.0.0.0/8; 92.0.0.0/8; 93.0.0.0/8; 94.0.0.0/8; 95.0.0.0/8; 96.0.0.0/8; 97.0.0.0/8; 98.0.0.0/8; 99.0.0.0/8; 100.0.0.0/8; 101.0.0.0/8; 102.0.0.0/8; 103.0.0.0/8; 104.0.0.0/8; 105.0.0.0/8; 106.0.0.0/8; 107.0.0.0/8; 108.0.0.0/8; 109.0.0.0/8; 110.0.0.0/8; 111.0.0.0/8; 112.0.0.0/8; 113.0.0.0/8; 114.0.0.0/8; 115.0.0.0/8; 116.0.0.0/8; 117.0.0.0/8; 118.0.0.0/8; 119.0.0.0/8; 120.0.0.0/8; 121.0.0.0/8; 122.0.0.0/8; 123.0.0.0/8; 124.0.0.0/8; 125.0.0.0/8; 126.0.0.0/8; 127.0.0.0/8; 169.254.0.0/16; 192.0.2.0/24; 197.0.0.0/8; 201.0.0.0/8; 220.0.0.0/8; 221.0.0.0/8; 222.0.0.0/8; 223.0.0.0/8; /* Multicast and Experimental */ 224.0.0.0/3; } prefix-list rfc1918 { /* RFC 1918 addresses */ 10.0.0.0/8; 192.168.0.0/16; 172.16.0.0/12; } } firewall { filter inbound-filter { /* Rate-limit for 5 m/s used for multicast */ policer 5m { if-exceeding { bandwidth-limit 5m; burst-size-limit 375k; } then discard; } /* Rate-limit for 500 k/s used for ICMP */ policer 500k { if-exceeding { bandwidth-limit 500k; burst-size-limit 62k; } then discard; } /* Rate-limit for 2 m/s used for UDP */ policer 2m { if-exceeding { bandwidth-limit 2m; burst-size-limit 250k; } then discard; } /* The first three terms have been separated for accounting only */ term 1 { from { source-address { /* Spoof of inside networks */ 6.6.6.0/24; 7.7.7.0/24; } } then { /* Count spoofed traffic. Type 'show firewall' to view */ count spoof-inbound-internal; log; discard; } } /* The following prefix-list can be divided for finer granularity */ term 2 { from { prefix-list { iana-reserved; } } then { count spoof-inbound-iana; log; discard; } } term 3 { from { prefix-list { rfc1918; } } then { count spoof-inbound-rfc1918; log; discard; } } /* Discard all ICMP fragments */ term 4 { from { is-fragment; protocol icmp; } then { count icmp-fragments; log; discard; } } /* Rate-limit ICMP traffic to 500 k/s */ term 5 { from { protocol icmp; } then { count policer-icmp-500k; policer 500k; } } /* Rate-limit Multicast traffic to 5 m/s */ term 6 { from { destination-address { 224.0.0.0/4; } protocol udp; } then { count policer-multicast-5m; policer 5m; accept; } } /* Rate-limit other UDP traffic to 2 m/s */ term 7 { from { protocol udp; } then { count policer-udp-2m; policer 2m; } } /* Allow access to Intranet (firewall filters specific ports) */ term 8 { from { destination-address { 7.7.7.0/24; } } then accept; } /* Our explicit (read: logged) drop all rule */ term 9 { then { log; discard; } } } /* Be a good netizen by preventing spoofing from within the network. You may wish to add further 'terms' if more access is required. */ filter outbound-filter { term 1 { from { source-address { 7.7.7.0/24; 6.6.6.1/32; } } then accept; } term 2 { then { count spoof-outbound; log; discard; } } } /* You may apply this filter outbound on fxp0 to count and compare TCP and TCP-SYN traffic. This can be used to detect a SYN-Flood if you suspect you are under attack. A high 'packets-syn' to 'packets-tcp' ratio could be a good indicator. TCP-intercept is not supported. */ filter syn-flood-detect { term 1 { from { protocol tcp; tcp-flags syn; } then { count packets-syn; log; accept; } } term 2 { from { protocol tcp; } then { count packets-tcp; accept; } } } /* Apply this filter inbound on interface loopback 0 in order to restrict ssh, ntp, and snmp connections destined to this router. You may wish to add entries for ICMP, FTP, BGP, VRRP, TACACS+, etc. */ filter router-protect { term 1 { from { /* Allow access from firewall, syslog, and utility server */ source-address { 0.0.0.0/0; 6.6.6.1/32 except; 7.7.7.5/32 except; 7.7.7.8/32 except; } protocol tcp; destination-port ssh; } then { count manage-discard-tcp; log; discard; } } term 2 { from { /* Allow access from designated SNMP and NTP servers */ source-address { 0.0.0.0/0; 7.7.7.5/32 except; } protocol udp; destination-port [ snmp ntp ]; } then { count manage-discard-udp; log; discard; } } |
EAN: 2147483647
Pages: 176
- RIP PE-CE Routing Command Reference
- Configuring L2TPv3 Static Tunnels
- Command Reference
- Case Study 2: Implementing Multi-VRF CE, VRF Selection Using Source IP Address, VRF Selection Using Policy-Based Routing, NAT and HSRP Support in MPLS VPN, and Multicast VPN Support over Multi-VRF CE
- Case Study 4: Implementing Layer 3 VPNs over Layer 2 VPN Topologies and Providing L2 VPN Redundancy