Threats
| As mentioned earlier, regardless of their motivation, hackers capitalize on vulnerabilities. Hackers exploiting vulnerabilities are real threats to network security. The following is a generic list of attack categories:
Reconnaissance AttacksReconnaissance attacks consist of intelligence gathering, often using tools like network scanners or packet analyzers. The information collected can then be used to compromise networks. Some of the proverbial reconnaissance attacks, conducted with specialized tools, are as follows:
Access AttacksDuring an access attack, the hacker exploits the vulnerabilities he has discovered during the reconnaissance attack. Some common access attacks are as follows:
Access SubterfugesHackers continuously come up with crafty access attacks. Consider the case of a user who receives an e-mail tantalizing him to play a virtual game of Spinning Wheel for a cash prize by simply opening the attachment. In the short time it takes the user to open the attachment, wait for the spinning wheel to stop turning, and hope the needle points to WINNER, an inconspicuous application meticulously collects all the entries in the user's e-mail address book and sends them back to the originator of the attack. The originator could be a spammer who plans to use this information for future spamming. Proper dissemination and enforcement of an e-mail security policy would have taught the user not to open an attachment from an unknown source. Alternatively, the organization might have considered installing an e-mail filtering service to purge the message of executable attachments. E-mail filtering is discussed in the section "Content Filtering," later in this chapter. Information Disclosure AttacksInformation disclosure attacks are different from an access attack in the sense that the information is provided voluntarily through a sophisticated subterfuge. The following attacks, though considered information disclosure attacks, could fall into the category of white-collar crimes:
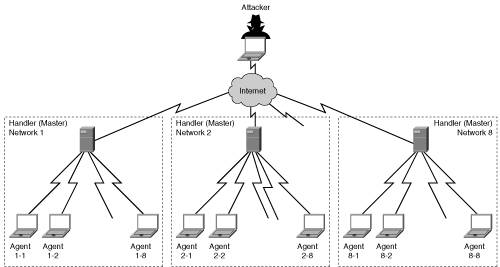
Social EngineeringSocial engineering, a form of low-tech hacking, is defined as someone, claiming to be someone he is not, who approaches a user either through e-mail or through a phone call for the purpose of infiltrating the organization. Great technical ability is not necessary to perform social engineering. PhishingInternet scammers who cast about for people's financial information have a new way to lure unsuspecting victims: they go phishing. Phishing is a high-tech scam that uses spam or pop-up messages to deceive readers into disclosing credit card numbers, bank account information, Social Security numbers, passwords, or other sensitive information. Figure 4-1 is an example of an e-mail that looked legitimate but was actually a scam. Figure 4-1. Phishing E-mail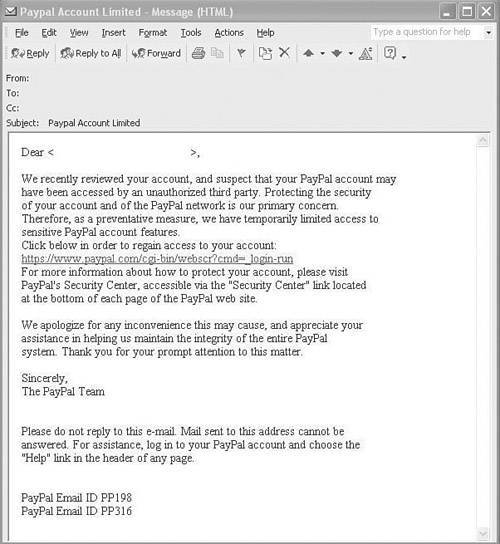 Unfortunately, no security systems can protect against information disclosure. Only the dissemination and enforcement of sound security policies can help users learn to be suspicious and to confirm the origin of these e-mails prior to taking actions. Denial of Service AttacksWith a DoS attack, a hacker attempts to render a network or an Internet resource, such as a web server, worthless to users. A DoS attack typically achieves its goal by sending large amounts of repeated requests that paralyze the network or a server. A common form of a DoS attack is a SYN flood, where the server is overwhelmed by embryonic connections. A hacker sends to a server countless Transmission Control Protocol (TCP) synchronization attempts known as SYN requests. The server answers each of those requests with a SYN ACK reply and allocates some of its computing resources to servicing this connection when it becomes a "full connection." Connections are said to be embryonic or half-opened until the originator completes the three-way handshake with an ACK for each request originated. A server that is inundated with half-opened connections soon runs out of resources to allocate to upcoming connection requests, thus the expression "denial of service attack." The following sidebars provide the anatomy of DoS attacks and distributed DoS (DDoS) attacks.
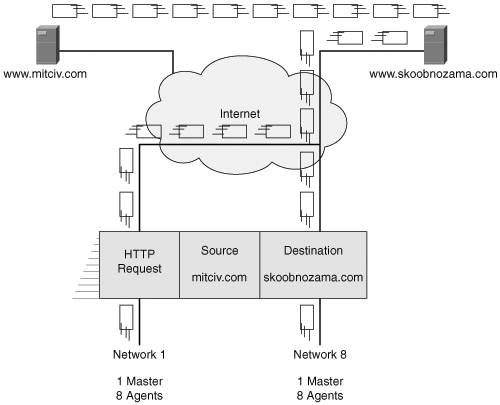
Those handlers in turn scan their own corporate network, hunting for workstations to compromise and turn into DDoS agents. Those agents are also referred to as bots, thus the expression of botnets. When his army of agents is strategically in place, the hacker launches the attack. He transmits his orders for the mission to the handlers and agents; these orders usually cause each of these hosts to send large quantities of packets to the same specific destination, at a precise time, thus overwhelming the victim and the path to it. It also creates significant congestion on corporate networks that are infected with handlers and agents when they all simultaneously launch their attack on the ultimate victim. As an added twist, the crafty hacker might have requested that the agents use a spoofed source IP address when sending the large quantities of packets to the destination. The target would reply to the best of its ability to the source, which happens to be an innocent bystander, as shown in Figure 4-3. Figure 4-3. DDoSLaunching an Attack Using a Spoofed Source IP Address[2] A basic knowledge of the different types of threats and attacks is crucial to understanding the purpose of mitigation equipment and proper network security design. These topics are covered in the following sections. |
EAN: 2147483647
Pages: 156