Mitigating Technologies
| Known threats can usually be mitigated by security equipment and sound security policies. The following sections cover the most pervasive mitigation techniques, which are grouped in these four major categories:
Threat DefenseThreat defense refers to the activities that are necessary to guard against known and unknown attacks, specifically by doing the following:
To do so, the campus design should include the following:
Virus protectionProbably the easiest and most cost-effective way to start protecting an organization is through up-to-date virus protection. Virus scanning can be performed at the following levels on a network:
Practitioners recommend that IT departments implement different brands of virus protection at different junctions and functions of the network, thus benefiting from multiple comprehensive virus-signature databases and hopefully enlarging the spectrum of the virus dragnet. Traffic FilteringTraffic filtering can be achieved at many layers of the OSI model. It can be done at the data link layer using the Media Access Control (MAC) address but is most commonly done at the network layer through packet filtering. Packet filtering is further divided into the following areas:
Static Packet FilteringStatic packet filtering is also referred to as stateless packet filtering or stateless firewalling. It is often performed at the perimeter router, which acts as the logical point of demarcation between the ISP and the corporate network. With stateless firewalling, the router does not track the state of packets and does not know whether a packet is part of the SYN process, the actual transmission, or the FIN process. A stateless firewall typically tracks only IP addresses and therefore can be tricked by a hacker who spoofs IP addresses. Dynamic Packet FilteringDynamic packet filtering is also referred to as stateful firewalling. It is usually done by a firewall, which is a dedicated appliance that performs packet scans. Stateful firewalling capabilities are also built into some routers. The default behavior of a firewall is that outgoing traffictraffic that flows from the inside network to the outside networkis allowed to leave and its reply traffic is allowed back in. However, traffic that originates from the outside network and attempts to come to the inside network is automatically denied. This is possible because the firewall meticulously tracks connections and records the following connection-state information in a table:
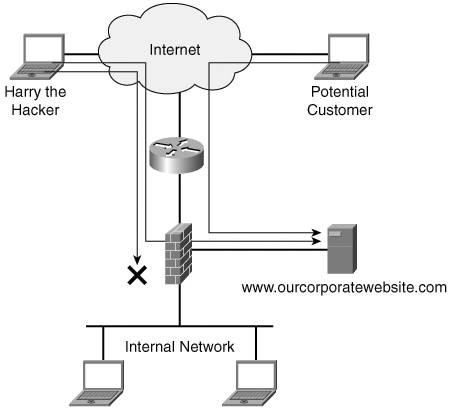
This default behavior of a firewall is sometimes changed to accommodate the presence of a corporate server to which outside users need access. This "public" server is usually located in the demilitarized zone (DMZ) of a corporate network. A rule can be configured in the firewall to stipulate which outside traffic is permitted to enter for the purpose of visiting the web server, as shown in Figure 4-4. Figure 4-4. DMZ and Firewall[3] Firewalling is evolving. For example, Cisco offers, on some switch models, a stateful firewall at the port level, thus providing tighter security inside the network, not just at the perimeter. The Cisco Catalyst 6500 Firewall Services Module provides a real-time, hardened and embedded security system. Intrusion Detection and PreventionIDSs and IPSs are part of the design solution for protecting primarily the perimeter, extranet, and increasingly internal network. The purpose of IDSs and IPSs is to monitor network traffic by analyzing each packet that enters the network. Intrusion Detection SystemsAs previously explained, an IDS scans network traffic for malicious activity. A management server, located on the inside network, logs the alerts of suspicious activities that are sent by the IDS. An IDS watches for the following:
An IDS can be one of the following:
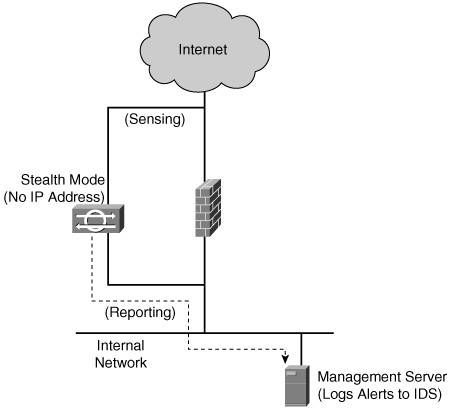
Network-Based IDSsNIDSs are efficient and don't introduce latency in a network because they perform their analysis on "copies" of the data, not on the packets themselves, as shown in Figure 4-5. When designing a campus network, set up the NIDS to have its reporting interface on the inside network and its stealth interface on the outside network. A stealth interface is physically present on a network but has no IP address. Without an IP address, the hacker cannot address and therefore hack through that stealth interface. Figure 4-5. Stealth Operation of an IDS[4] As an alternative to buying a dedicated IDS appliance, your network design might harness the basic IDS capabilities that are built into Cisco PIX Firewalls and specific Cisco router IOS versions. Host-Based IDSsHIDSs are typically installed on mission-critical devices, such as web servers and e-mail servers, but can also be installed on desktop and laptop PCs. Cisco offers an HIDS solution called the Cisco Secure Agent (CSA). CSA closely monitors the behavior of codes that are coming to the end point and prevents attacks while reporting the incident to the management server. Intrusion Prevention SystemsIPSs have naturally evolved from IDSs. An IPS has the extra capabilities of taking remedial actions when it confirms suspicious activities. Upon discovering malicious activity, the IPS can take at least one of the following actions:
Currently, only subtle differences exist between IDSs and IPSs; therefore, many vendors interchange the terms. Target-Based Intrusion Detection SystemsA significant issue with IDSs is the number of alarms that they generate. The number of alarms generated by the sensor can be reduced by locating the monitoring interface on the inside link of a firewall, instead of the outside link. If you put your IDS monitoring connection before the firewall (the outside interface), you will get alarms for traffic that would be stopped by the firewall anyway; however, if you put the IDS monitoring interface on the inside interface, it will only catch, and therefore generate alarms about, malicious traffic that has passed through the firewall. Another significant issue with IDSs/IPSs are false positives. False positives are alerts triggered by legitimate activities, in which case no alarm should have been raised. A target-based IDS, such as Cisco Threat Response, tries to address this problem by investigating in-depth and relative to the target an alert received by the network management console. The target-based IDS does the following:
Content FilteringIn addition to controlling outbound traffic through filtering configured in the perimeter router or Internet firewall, the network design might also include the following:
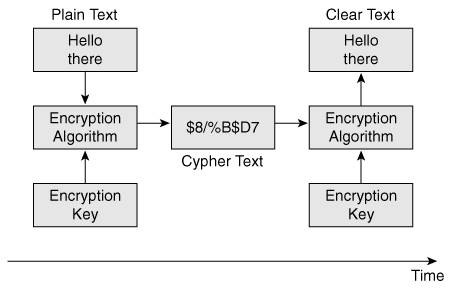
URL FilteringCorporations use content filtering to enforce their Internet usage policies, hoping to protect themselves from possible legal implications should their employees visit objectionable websites. With content filtering, outbound user traffic that is looking for a specific URL is checked by the firewall against the content-filtering server that is installed on the corporate network. The firewall is provided by the content-filtering server with a permit or deny for the website requested by the user. The sophisticated content-filtering software installed on a corporate server can have over 5 million websites in its database. The network administrator sets the policies to allow or deny access to groups and individual websites. The permissions can also be based on daily usage or time of day. As an example, a system administrator could set a rule that allows users to visit online banking sites only during the lunch hour. E-mail FilteringWhen designing your corporate e-mail services, consider including an e-mail filtering service. That service, installed on the same network segment as your mail server (usually in a DMZ), sanitizes the e-mail from malware and some executable attachments prior to delivery of the messages to the end user. Secure CommunicationEncryption addresses the need for data confidentiality, which often finds itself in the forefront of network design. Confidentiality of data refers to the inability for wandering eyes to see and/or decipher a message sent from one party to another. Encryption is a significant topic and can easily fill books by itself. Therefore, this section provides only enough information to assist you in network design. Should you be interested in a detailed book on encryption, read The Code Book: The Science of Secrecy from Ancient Egypt to Quantum Cryptography, by Simon Singh (ISBN 0-385-49532-3, Anchor, 2000). Some basic principles of encryption are presented in this section. As shown in Figure 4-6, the following two components are essential to encryption:
Figure 4-6. Encryption Operation[5] Data Encryption Standard (DES), Triple Data Encryption Standard (3DES), and Advanced Encryption Standard (AES) are all common encryption algorithms used in IP security (IPsec). IPsec is discussed in the next section of this chapter. The algorithm can be seen as the engine of encryptionthe morphing device through which the data goes. The "pattern" of morphing is provided by the "key." An encryption key is a code that enciphers and deciphers a stream of data. Encryption keys must be well guarded and shared only between the two parties requiring securing communications. The following are the two types of encryption keys:
A key becomes vulnerable when it has been in service for a long period because the hacker has had time to attempt to break it. A key is also vulnerable if a large quantity of data is encrypted with it: The hacker would then have a large sample of cipher text to try deciphering. Therefore, when designing a network, you should consider having keys that expire frequently and when large amounts of data have been encrypted through that key. As part of network design activities, you might consider using one of the following common encryption scenarios:
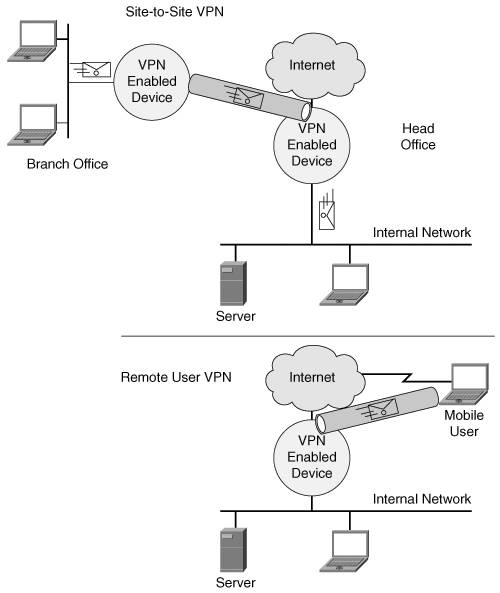
Encrypted VPNAn encrypted VPN consists of a tunnel in which data transiting through it is encrypted, as shown in Figure 4-7. The tunnel can originate from a VPN-enabled device or from a remote user running VPN software on his computer. Figure 4-7. Encrypted Tunnels[6] The most common standard for encrypted VPN is IPsec. IPsec provides three optional mechanisms, as explained in Table 4-1.
VPN-enabled devices that might be included in the design of a network are as follows:
SSLSSL provides encryption of data to and from a web browser and could be included in a network design if a point-to-point encryption is needed for a service. It is commonly seen for online banking or shopping transactions and web mail operations. It is also popular for organizations that do not want to install VPN-client software on remote hosts. File EncryptionIn the case where a document requires confidentiality but the communication might be in clear text, a person can use file-encryption software such as Pretty Good Privacy (PGP) to encrypt the file. The encrypted file must be unencrypted by the reader after it is received. Trust and IdentityTrust and identity management includes the following:
Authentication, Authorization, and AccountingAAA is a crucial aspect of network security and should be considered during the network design. This can be accomplished through a AAA server, which handles the following:
AAA can be managed by a Cisco Secure Access Control Server (ACS). The principles of strong authentication should be included in the user authentication. Key Point Strong authentication refers to the two-factor authentication method. The users are authenticated using two of the following factors:
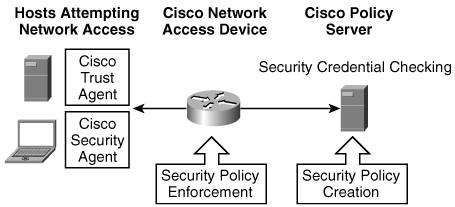
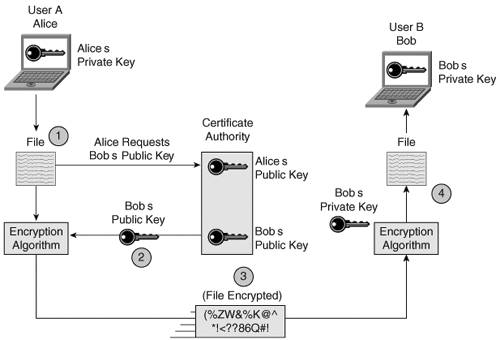
As an example, when accessing an automated teller machine, strong authentication is enforced because a bank card (something you have) and a PIN (something you know) are used. Network Admission ControlNAC, the latest feature in Cisco's security portfolio, should be considered in the design of your network. NAC ensures that users and their computers comply with corporate network policies. On a corporate network with NAC, a network access device (NAD)for example, a routerintercepts attempts to connect from local or remote users. As shown in Figure 4-8, the Cisco trust agent, residing on the end point (for example, a user's laptop), provides the NAD with pertinent information, such as the version of antivirus software and the patch level of the connecting laptop. The NAD passes the end-point security credentials to a policy server, which decides whether access will be granted to the end point. Noncompliant end points are quarantined until they meet NAC standards. Figure 4-8. Network Admission Control Public Key InfrastructurePKI is a set of technologies and procedures that authenticate users. It addresses the issue of key distribution by using private keys and public keys. These are asymmetrical keys, and the public keys usually reside on a central repository called a certification authority (CA). The private keys are usually stored locally on devices. PKI operations are shown in Figure 4-9. Figure 4-9. Private and Public Key Operations[7] Each unique pair of public and private keys is related, but not identical. Data encrypted with a public key can be deciphered only with the corresponding private key, while data encrypted with a private key can be deciphered only with its corresponding public key. PKI is usually considered in the design of complex enterprise networks where it is too cumber-some for each party to locally keep the public key of every other party that he or she wants to communicate with using encryption. In a PKI environment, the public keys are kept centrally, thus simplifying the distribution and management of those keys. Network Security Best PracticesAs in any field, network security also possesses a set of best practices. Best practices are the recommendation of due care that subject-matter experts have agreed upon for a particular field. Network security includes many well-known practices presented in the following sections. Network ManagementMost security appliances, such as firewalls, routers, and IDSs, can send syslog security triggers to a central repository such as a syslog server. There is a saying in network security: "If you log it, read it." This is to say that it's futile to just log information if you never analyze the logs. To help the network administrator sort and extract meaningful information from the large quantity of syslog data received, security event management software should be used. Should a significant anomaly be discovered, the software can notify the network administrator through e-mail, pager, or text messaging. In addition, correlation tool modules can be added to assist the network administrator in seeing security anomaly patterns from what would otherwise appear to be random activity taking place. Assessment and AuditsPrior to designing your network, you should conduct a security assessment to uncover potential vulnerabilities and therefore target your security efforts where they are the most effective. Subsequently, when your network security systems are in full production, it can be beneficial to hire a security audit company that can perform penetration testing and report on the corporate network security position. PoliciesSophisticated security equipment is no match for sloppy user behavior. Organizations must develop basic network policies, disseminate them, and enforce them. Examples of network security policies are as follows:
|
EAN: 2147483647
Pages: 156