Virtual Private Network (VPN)
Virtual Private Network (VPN)
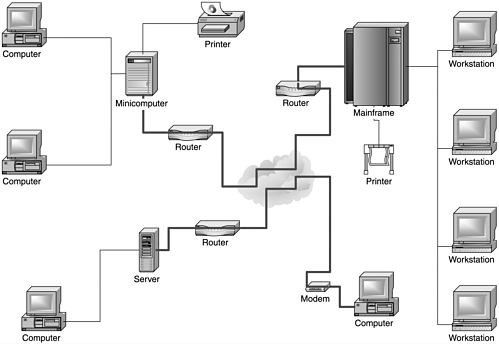
A VPN is a network of two or more computers, or computer systems, linked together over the public network in a manner that virtually creates a private network. Figure 7.1 shows how the network can be connected, with the lines between networks indicating two VPNs: one between Computer A and the PDA and one between Computer B and Server 2.
Figure 7.1. An example of VPNs
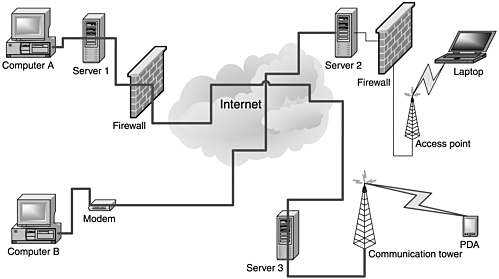
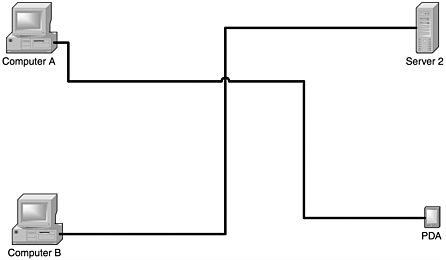
Figure 7.2 shows how the network is logically connected. When implemented correctly, these VPNs provide the security of a direct private network connection, with the cost saving and scalability of using public Internet connectivity. The key word in the preceding sentence is when. Just because you have a VPN system in place does not mean that your communications and network are safe.
Figure 7.2. VPN logical connections
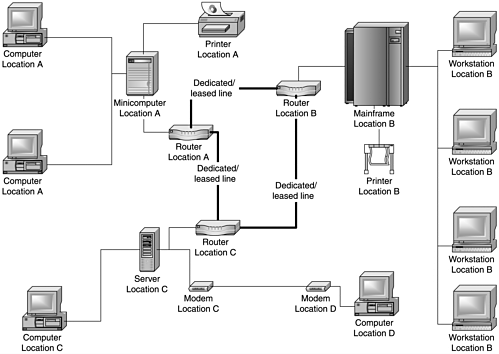
A private network used to mean a network with no external connectivity, only accessible by direct, controlled, co-located connectivity, as depicted in Figure 7.3. To expand this type of network to multiple locations required the use of dial-up or dedicated/leased lines between locations, and in security-sensitive deployments, the use of some form of link encryption over these leased or dial-up lines. This model was expensive to maintain and not very scalable (see Figure 7.4).
Figure 7.3. A private network with no external connections
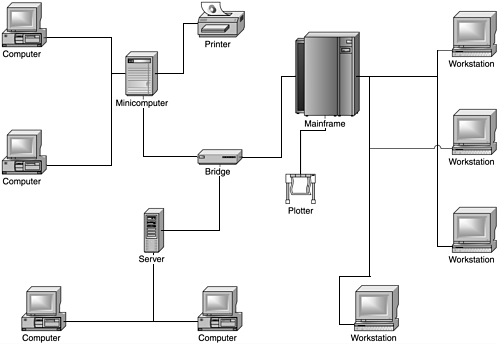
Figure 7.4. A private network with external connections
To be able to utilize the cost savings and scalability of the Internet or public networks, security professionals began to create VPNs via the combined use of encryption, authentication, and mechanisms for obfuscating information about the private network topology from the public network. The benefit of this idea is that by utilizing a properly implemented VPN, you have access to the entire private network from any location, as if you were physically co-located and connected to the network.
The disadvantages are that the Internet cannot provide the level of security, bandwidth, versatility, and reliability available on a private network. However, as we have discussed in other chapters, the increased utility of being able to access the private network from outside and varying locations outweighs the limitations currently imposed by the use of a VPN.
Three basic types of VPN products are on the market today: hardware-based, firewall-based, and software-based.
Hardware-Based VPNs
Most hardware-based VPN systems are encrypting routers. They are generally secure and easy to implement. Of all VPN systems, they tend to provide the highest network throughput because they are functionally specific and processor resources are concentrated on performing the routing and encryption tasks. Looking at Figure 7.5, you will notice that it is essentially the same layout as Figure 7.4, except that it utilizes the public Internet for between-location connectivity.
Figure 7.5. A hardware-based VPN
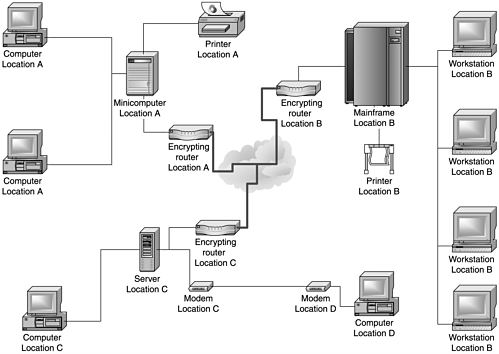
However, hardware-based VPNs are not as flexible as software-based systems, should changes be required because of upgrades or modifications in the backend network. Certain complete hardware VPN packages offer software-only clients for remote installation and incorporate access control features more traditionally managed by firewalls or other perimeter security devices. As with many additional features, they come with security concerns. That the VPN is remotely installable implies that it is remotely administrable, and this raises questions about the authentication and security mechanisms in place on this device.
Firewall-Based VPNs
Firewall-based VPNs leverage the firewall's security mechanisms to provide VPN functionality (see Figure 7.6). These VPNs use the firewall to restrict access to the internal network, perform address translation and authentication, and provide real-time alarm and logging capability. Most commercial firewalls strip out potentially vulnerable or unnecessary services (called hardening), increasing their security posture. Many resources are available for ensuring the integrity and security of firewalls. Network administrators should utilize these resources to ensure that a firewall is performing the tasks anticipated so that the additional security provided by a VPN is not circumvented by some other vulnerability in the firewall.
Figure 7.6. A firewall-based VPN
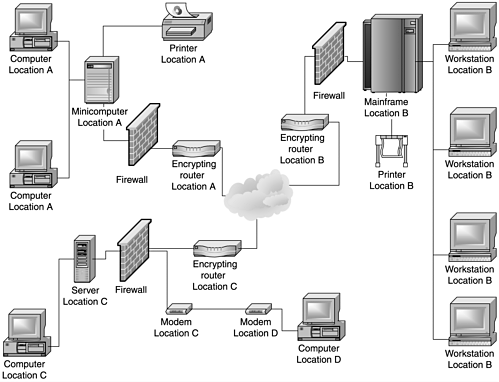
The drawback is that VPN services place additional processing responsibility on the firewall, and if the firewall is already heavily utilized, performance can be affected. Some vendors are offering hardware-based encryption co-processors or accelerators to increase the efficiency of firewall-based VPNs.
Software-Based VPNs
Software-based VPNs are ideally suited for situations in which the client and server sides are not necessarily controlled by the same administrative organization (see Figure 7.7). They are also beneficial when a variety of network hardware, such as firewalls and routers, is implemented within the same organization. This is because they provide VPN services above the hardware level and provide the greatest flexibility in how network traffic is managed. Many software-based VPN products provide for tunneling (more on this in the next section) based on address or protocol, whereas firewall and hardware-based VPN products tunnel all traffic.
Figure 7.7. A software-based VPN
Software-based VPN systems are generally harder to administrate than hardware-based or firewall-based VPN solutions. Software-based solutions generally require familiarity with the host OS, the application, the network architecture, and the security mechanisms being employed. With the preceding combination there is greater risk that the software will not be implemented or configured properly, opening vulnerabilities that may be exploitable. Software-based solutions may be vulnerable to weaknesses at lower network layers or in the hardware itself. The best software security solution does no good if there is a way to bypass it altogether at the hardware level. Implantation of individual components of the VPN solution may have vulnerabilities that expose the entire system to risk, such as vulnerabilities in the way authentication is achieved or weakness in the session key or encryption algorithm. Every component must function properly and securely for the overall system to be reliable and secure.
The trend in the VPN market is to combine the best of the three VPN solutions into more useful, functional, and flexible products. As this trend continues, the lines between these three basic VPN systems will blur and eventually may disappear altogether. The proposed implementation of IPSec (discussed in a later section) is likely to hasten the transition to a more integrated VPN solution.
EAN: 2147483647
Pages: 73