Secure Personal Identification
| With the growth of network-centric businesses and services, everyone connects with a great deal of trust to a faceless application channel to access information and do transactions. Everyone is required to confirm his or her identity by verification and validation using a set of credentials. However, identity theft, identity fraud, and impersonation crimes are increasing because someone has wrongfully obtained and abused another person's identity information for economic or personal gain. It is surprising to note that most identities are stolen from trusted insiders such as employees, colleagues, friends, and even family members who have easy access to private information. These fraudulent acts include unauthorized access to confidential information, bank accounts, transactions, and so on. According to The 9/11 Commission Report (page 401) ". . . terrorists use evasive methods, such as altered and counterfeit passports and visas, specific travel methods and routes, liaisons with corrupt government officials, human smuggling networks, supportive travel agencies, and immigration and identity fraud." The stealing and forging of magnetic-strip credit cards are also on the rise and have caused many people losses that have led to bankruptcy. The Christian Science Monitor, October 7, 2004, reported that Phishing has victimized some 1.8 million consumers and cost banks and credit-card issuers nearly $1.2 billion in the past year. The most common reasons for the success of identity-theft related crimes are poor personal identification and verification processes, stolen passwords, inaccurate authentication mechanisms, counterfeiting, and impersonation. Some of those issues are due to processes that are more susceptible to error, particularly when they rely on manual verification. Traditional identification technologies and authentication mechanisms are not adequate to counter and prevent identity-theft related crimes. For example, traditional identification mechanisms such as passwords, PINs (magnetic-stripe cards), and driver's licenses can be lost or stolen, and these credentials can be hacked, manipulated, or forged. Personal Identification and AuthenticationFrom a technical perspective, most of us get confused when we try to distinguish between identification and authentication processes. Identification is a process of assigning an identity to a specific entity (i.e., a person) and authentication is a process of verifying an identity. The requesting identity can be identified and authenticated by using his or her information credentials and/or his or her possessions and physical characteristics, particularly what he or she knows (e.g., PIN, passwords), what he or she owns (e.g., smart card), or what his or her human characteristics are (e.g., biometrics). Adoption of identification and authentication technologies using smart cards, biometrics, RFID tags, digital certificates, or a combination of any of them has proven to be a viable method of thwarting mostly identity-theft related crimes. Let's take a high-level look at using smart cards and biometrics for personal identification and verification. Smart Card IdentitySmart cards are credit-card sized computing devices that can act as tokens to enable services that require security. A smart card is a plastic card with an integrated circuit (IC) chip embedded within the plastic substrate of its body. The smart card IC chip is meant for processing, data transmission, and storage. Smart cards do not contain power supply, display, or keyboard. For communication, it makes use of a card acceptance device (CAD), also referred to as a smart card reader, that is connected to a computer via USB or serial port. A smart card may also have a magnetic strip on the other face of the card. Smart cards can be divided into groups as microprocessor and memory cards. They can be further categorized as contact cards and contactless cards based on the difference in the card access mechanism. The physical appearance of a smart card is defined in ISO 7816, which set the standards for the smart card industry. With industry support, Sun Microsystems introduced Java Card specifications that define a Java runtime environment for smart cards as a Java technology platform for developing smart card applications. The platform also supports smart card manufacturers, card issuers, and related communities. We will discuss the Java Card platform and its security features in Chapter 3, "The Java 2 Platform Security." Figure 1-1 illustrates the physical appearance of a smart card (from Sun Microsystems). Figure 1-1. The Java Card (Source: Sun Microsystems) Microprocessor cards, as the name implies, contain a processor. The microprocessor performs data handling, processing, and memory access according to a given set of conditions (PINs, encryptions, and so on). Microprocessor-based cards are widely used for access control, banking, wireless telecommunication, and so on. Memory cards contain memory chips with non-programmable logic and do not contain a processor. Memory cards are typically used for prepaid phone cards, for gift cards, and for buying goods sold based on prepayment. Since memory cards do not contain a processor, they cannot be reprogrammed or reused. Contact cards must be inserted in a CAD reader to communicate with a user or an application. Contactless cards makes use of an antenna, and the power can be provided by the internal or collected by the antenna. Typically, contactless cards transmit data to the CAD reader through electromagnetic fields. One limitation of contactless cards is the requirement that they be used within a certain distance of the CAD reader. The Role of Smart Cards in Personal IdentificationWith the built-in power of a processor and storage, smart cards offer security and portability in support of personal identification. Smart cards are resistant to cyber-attacks and hackers, because they do not connect with vulnerable external resources. Any attack on a smart card requires physical possession of the card and specialized expertise to verify it. In addition, accessing a smart card usually requires the card holder's PIN (personal identification number), which prevents the card from being used by an unauthorized person. Using cryptographic algorithms can further strengthen the security features of smart cards, allowing storing the data as encrypted in memory. The data exchanged between the card and CAD readers can be encrypted as well using mutual authentication. Today, smart cards are commonly adopted by various industries, particularly for personal identification and authentication. Smart cards are considered as secure alternatives to traditional identification documents such as driver's licenses, national IDs, and visas. Unlike traditional identification cards, smart cards are often impossible to forge or copy. Personal confidential information and images can be securely stored into the card and protected by using cryptographic algorithms. By setting up the access conditions, such as PIN and passwords, only authorized persons or authorities can access the secured information. Smart cards also allow storage of digital certificates representing a person that can be used to digitally sign documents and request logical access to applications. The smart card store certificates can be verified for validity using CRLs (Certificate Revocation Lists) and OCSP (Online Certificate Status Protocol) services facilitated by a Certificate Authority (CA). Combined with biometric technologies, smart cards also offer a highly assured and trusted personal identification solution to counter identity theft and related crimes. Biometric information about the cardholder can also be stored on the card. With biometrics information on the card, in addition to providing password/PIN, the cardholder must use a biometrics scanner device to identify or verify the biometric sample, whether the cardholder owns the card or not. Biometric IdentityBiometric identity refers to the use of physiological or behavioral characteristics of a human being to identify a person. It verifies a person's identity based on his or her unique physical attributes, referred to as biometric samples, such as fingerprints, face geometry, hand geometry, retinal information, iris information, and so on. The biometric identification system stores the biometric samples of the identity during registration and then matches it every time the identity is claimed. Biometric identification systems typically work using pattern-recognition algorithms that determine the authenticity of the provided physiological or behavioral characteristic sample. Popular biometric identification systems based on physical and behavioral characteristics are as follows:
Figure 1-2 shows a biometric facial recognition solution (BiObex). Figure 1-2. BiObexBiometric identification using facial recognition (Courtesy: AC Technology, Inc.)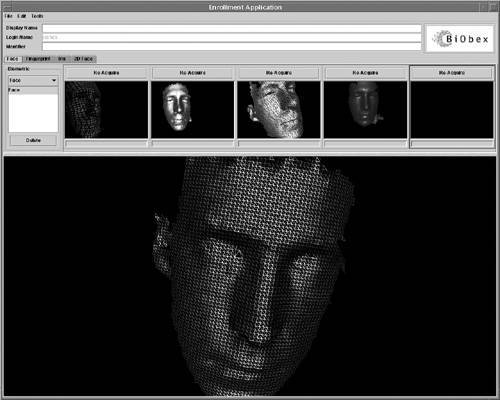 Industry standards and specifications are available for developing and representing biometric information. The key standards are as follows:
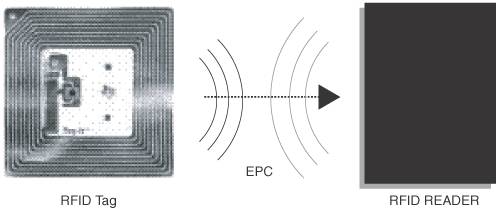
The Role of Biometric Identity in Secure IdentificationBiometric identification is not a new mechanism or even considered as an emerging technology solution. In 1870, French criminologist Alphonse Bertillon invented a method for identifying criminals. The method used measurements and characteristics based on morphological representation of bony parts of the human body, descriptions of peculiar marks, and mental or moral qualities [Forensic-evidence]. Although many experts feel that biometric techniques are still in their infancy, it has already been shown that adoption of biometric technologies leads to more accurate and reliable identification and authentication than any other mechanisms. Biometric identification provides a strong alternative to manual verification, where passwords and PINs may be forgotten, lost, or stolen and smart cards can be shared, stolen, or lost. A biometric sample cannot be stolen or lost. Adopting biometrics in multifactor authentication is becoming the de facto standard for securing security-sensitive applications and resources. Today, biometric identification solutions are widely deployed in forensic investigation, intelligence, government, military, homeland security, financial institutions, and casinos. These solutions play a vital role in criminal identification, terrorist identification, access control, and security-sensitive information systems. With the increasing adoption, acceptance, and availability of biometric identification solutions and tools, biometrics is expected to become a standard identification and authentication solution for the prevention of identity-theft related crimes and for all security-sensitive applications and services. In a Security by Default strategy, secure personal identification using smart cards and biometrics plays a vital role in providing highly secure logical access control to security-sensitive applications. For more information about the architecture and implementation of secure personal identification solutions using smart card and biometric technologies, refer to Chapter 15, "Secure Personal Identification Using Smart Cards and Biometrics." RFID-Based IdentityRadio Frequency Identification (RFID) provides a mechanism for identification services using radio frequencies. It makes use of an RFID tag, comprised of an integrated circuit chip and an antenna. The RFID tag stores a unique Electronic Product Code (EPC) and uses an antenna to receive the radio frequency for emitting and transmitting the EPC data as signals to the RFID readers. When an RFID passes through an electromagnetic zone, the RFID tag is activated and sends signals to the RFID reader. The RFID reader receives and decodes the signals and then communicates the EPC to the RFID server that provides the Object Name Service (ONS). The ONS identifies the object by interpreting the EPC and sends it for further processing. The EPC data may provide information related to the identification, location, and other specifics related to the identified object. The standards and specifications related to RFID systems are defined by EPCglobal (www.epcglobalinc.org) an industry standard initiative with participation by leading firms and industries promoting RFID technologies. Figure 1-3 illustrates the transmission of EPC data from the RFID tag to the RFID reader. Figure 1-3. RFID Tag and Reader RFID tags are available in a wide variety of shapes and sizes. RFID tags can be categorized as active or passive. Active RFID tags have a power source that supports read/write, longer read range frequencies, and larger storage (operating up to 1 Mb). Passive RFID tags do not contain any power source; they generate power by using the incoming radio frequency energy induced in the antenna to transfer the EPC from the RFID tag to the RFID reader. Passive RFID tags are usually less expensive than active tags and are commonly adopted to support shorter read ranges. The Role of RFID in Secure IdentificationRFID was originally intended to replace product bar codes such as UPC and EAN due to their limitations. The uniqueness of RFID tags and their flexibility in identifying any object presented a promising solution to the industry, particularly for supporting identification and tracking of objects, combat thefts, and so on. Today, RFID-based systems are best suited to detect unauthorized access and theft in organizations, to manage the supply chain in retail stores by speeding up restocking and reducing shrinkage, to manage book inventories in libraries that use self check-out procedures, to identify expired products in food industries, to track patients and matching prescriptions in hospitals and pharmacies, to track passenger baggage in commercial airlines, and to identify livestock and track animals. While RFID technologies are gaining momentum in a lot of industries, they are also becoming controversial because of security concerns related to information privacy. The EPCglobal standards define privacy-related guidelines for the use of RFID in consumer industries. These guidelines require notifying consumers about the presence of EPC and advising them to discard, deactivate, or remove EPC tags. At the time of writing this book, the EPCglobal standards committee is working on network and information-level security specifications to support all of the security aspects related to RFID tags, tag discovery, and network security. |
EAN: 2147483647
Pages: 204