Chapter 5: Directory Structure and Special Files
| | ||
| | ||
| | ||
When Microsoft Windows is installed on a personal computer, various directories and special files are created. An understanding of where each version of Windows places key files of note to a forensic examination and the underlying directory structures provides the basis for forensic analysis of the file system at the logical level.
Each of the different versions of Windows uses a slightly different directory structure with different names for key files. I will examine the specific directories and files created in Windows 9 x /NT//2000/2003/XP with an emphasis on their forensic value.
Windows NT/2000/XP
The Windows NT and 2000 operating systems provided the first structural break from the prior MS-DOS directory and file structures used by the Windows 9 x family. There are minimal differences from a file and directory standpoint between the various workstation and server versions of the operating systems. The server versions generally include a few additional files but have the same basic structure as the workstation versions. Additionally, the specific directories installed will vary slightly based on individual installation options. The items below reflect a default installation, with directories of special forensic interest installed as optional features noted.
Directories
The primary directories are created under the root on the partition the operating system was installed to (generally the partition assigned to the C: drive):
-
Documents and Settings. The subdirectories under this directory provide individual user profile information. User profiles are specific to an account and store individual application settings, desktop information, documents, and other details. This information is found under %SYSTEMROOT%/profiles on Windows NT machines.
-
Inetpub. The Windows Internet Information Services hierarchy is stored under subdirectories below this heading.
-
Program Files. The default installation location for software installed under Windows is the Program Files directory. Individual applications will create their own subdirectories under this hierarchy.
-
Recycler. On each drive, the Recycling Bin creates a Recycler folder with individual subfolders , labeled by the Security Identifier of their owners , for each user that has deleted a file on that drive. Recycling Bin analysis is covered in Chapter 10.
-
System volume information. This is a hidden system directory. It provides information on restore points. Although not commonly looked at in forensic analysis, they can include fragments of information (sometimes SAM information), and they are a favorite hiding spot for hackers to place hidden directories. Windows NT does not have restore points and therefore does not have a System Volume Information folder.
-
Temp. On Windows NT, a root level Temp folder was created for use by the operating system and applications for storage of temporary files.
-
WINNT/Windows. The primary operating system directory for the installation of the Windows system files. Most of the system-based forensic information is likely to be present in subdirectories of this directory.
| Note | The core Windows directory defaults to WINNT under 2000 and earlier versions, and WINDOWS for later versions. It can be set to any directory name, however, and the best way to identify the valid directory (if a multiboot machine is used) is to review the %SYSTEMROOT% environment variable by typing its name at the command prompt (or typing set ). |
| |
To access startup configuration information in one location with Windows 98/ME/2003/XP, Microsoft provides the MSConfig utility. To start MSConfig, select Start Run and type msconfig in the text box.
The MSConfig utility enables the viewing and editing of the WIN.INI, SYSTEM.INI, and BOOT.INI files. Additionally, any services set to start automatically or registry entries that execute automaticallya favorite way for viruses to re- infect after a re-bootare displayed under the Services and Startup tabs, respectively.
The following screenshot shows a list of programs set to run automatically when Windows is started.
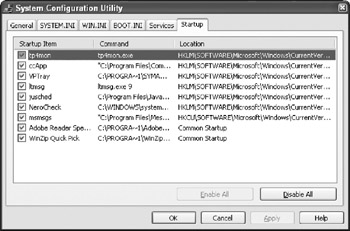
MSConfig Startup Information
| |
Under each of these directory structures are further directories of interest in a forensic examination. Table 5-1 details several key directories and their forensic value.
| MAIN DIRECTORY | SUBDIRECTORY | CONTENTS |
|---|---|---|
| Documents and Settings | All Users/Desktop | Stores items shown on the desktop as icons for all users. May be used with an individual profile to indicate whether an individual user added an item or someone else added it. |
| Documents and Settings | All Users/Documents | Stores any shared documents between machine users. Likewise, some applications will create individual user subdirectories under this directory. |
| Documents and Settings | All Users/Start Menu | Stores any items that appear on all Start menus . The Programs/Startup subfolder contains shortcuts to files that start automatically when the user logs in. |
| Documents and Settings | Default User | Stores the default profile which is copied to an individual profile upon adding an account to the system. Social-engineering and access to this folder have been used by hackers looking to exploit a specific account. |
| Documents and Settings | <Profile Name>/ Application Data | Contains application data for each individual profile. Configurations, log files, and general data may be stored under application subdirectories in this hierarchy. |
| Documents and Settings | <Profile Name>/ Cookies | Contains text files of individual cookies for a particular user. |
| Documents and Settings | <Profile Name>/ Favorites | Contains the individual's Internet Explorer favorites. |
| Documents and Settings | <Profile Name>/ Local Settings/ Application Data | Contains any application data specific to the computer. |
| Documents and Settings | <Profile Name>/ Local Settings/ History | Contains the individual's Internet Explorer browsing history. This directory is treated as special for display purposes in Windows Explorer. |
| Documents and Settings | <Profile Name>/ Local Settings/Temp | Stores any temporary files created or downloaded using Internet Explorer. This is used for temporary purposes (for example, installers ) as opposed to caching. |
| Documents and Settings | <Profile Name</ Local Settings/ Temporary Internet Files | Contains the individual's Internet Explorer-cached files. |
| Documents and Settings | <Profile Name>/Local Settings/My Documents | Acts as the default storage location for all user-created documents. My Pictures and My Music are also located under this subdirectory. This is one of the most common locations for forensic recovery. |
| Documents and Setting | <Profile Name</Nethood | Contains all Network Neighborhood shortcuts. Good for showing an individual knew about and accessed a particular network computer. |
| Documents and Settings | <Profile Name>/Printhood | Shows all installed printers. If an individual printer is mapped in this directory, the associated profile had that printer installed. |
| Documents and Settings | <Profile Name>/Recent | Shows recently opened items, including shortcuts to previously removed items. One of the best locations for evidence. |
| Documents and Settings | <Profile Name>/SendTo | Contains items that appear on the Send To right-click menu. Frequently, shortcuts to removable drives or CDburning software install items here. |
| Documents and Settings | <Profile Name>/Start Menu | Contains the applications an individual profile has installed. These are in addition to the All Users items. The Programs/Startup subfolder contains shortcuts to files that start automatically when the user logs on. |
| Inetpub | Ftproot | Acts as the default location for an IIS FTP server's files. |
| Inetpub | Mailroot | Acts as the default location for an IIS SMTP server's files. |
| Inetpub | Wwwroot | Acts as the default location for an IIS web server's files. |
| %SYSTEMROOT% | $NtUninstallxxxxxxx$ | Indicates installation of various patch files. The directory date can be used to indicate when a particular patch was applied, to prove whether an infection was possible at a point in time. You can use the xxxxxxx code to search on http://www.microsoft.com for particulars. |
| %SYSTEMROOT% | Addins | Shows any installed local ActiveX control files. Given recent ActiveX exploits, this is a possible malicious code location. |
| %SYSTEMROOT% | Downloaded Installations (and Installer) | Contains MSI installers (Microsoft's installer files). Even after removal, the installer for a piece of software may still be present in a subdirectory here. |
| %SYSTEMROOT% | Downloaded Program Files | Contains Internet Explorer add-ins (such as the Shockwave Flash Object). If a particular site requires a special download, this is a potential location to examine whether the site has been visited. |
| %SYSTEMROOT% | Driver Cache | Contains specific drivers files previously used by Windows. Of particular interest are files that indicate a specific device has been connected (such as the usbxxxx.sys files for USB Devices). |
| %SYSTEMROOT% | Offline Web Pages | Shows any web pages stored for later offline browsing using Internet Explorer. |
| %SYSTEMROOT% | Profiles | Shows the same items as the Documents and Settings hierarchy on Windows NT systems or systems upgraded from NT. |
| %SYSTEMROOT% | Repair | Contains backups of the registry files. This is an excellent location for old registry files and SAM information. |
| %SYSTEMROOT% | System32 | Contains essential system files, including .DLL and EXE files used by the operating system. Any infected operating system files are likely to be under this directory tree. |
| %SYSTEMROOT% | System32/Config | Contains the registry files and the event logs (except User hive information). This is a frequently visited directory in forensic analyses. |
| %SYSTEMROOT% | System32/Drivers | Indicates specific devices that have been installed on a system by the drivers referenced (like the Driver Cache folder). |
| %SYSTEMROOT% | System32/Drivers/Etc | Contains the hosts and lmhosts files, which provide local hostname resolution services. These are processed before DNS and WINS lookups, and therefore the entries here override these services. |
| %SYSTEMROOT% | System32/Spool/Printers | Shows Print spool files. These are files that have been printed or failed printings. |
| %SYSTEMROOT% | Tasks | Lists any scheduled tasks using the Windows Scheduler. The scheduler has been used for escalation of privileges as well as "logic bomb" scheduling in the past. |
| %SYSTEMROOT% | Temp | Contains a grab bag of items for forensic analysis. Log files, temporary files, and other miscellaneous items appear here. The Temp directory for individuals is generally Documents and Settings\<PROFILE NAME>\Local Settings\Temp. |
| Note | In Windows, each account has an associated profile. The profile stores information about the individual user, including application data, documents, and configuration settings. Microsoft also introduced the concept of Roaming Profiles to allow users to access their data from any machine on a given domain. With roaming profiles enabled, all of the user's informationexcept for the Application Data, Local Settings, Nethood, and Printhoodare stored on a network drive instead of the local computer. |
The above directories represent only a few of the many locations forensic evidence may reside. Users and applications can create their own directory hierarchies, rename an existing hierarchy, or use little-visited branches of the hierarchy to store information away from investigative prying eyes.
| |
When an application wants to find the default directory where Windows was installed or a user types a command that is not in the current directory, the locations are looked up in memory where they are stored as environment variables.
Environment variables may be added or changed using the set command along with the variable name. Typing set without a variable name will return all of the environment variables present on a given system. Here is an example of the environment variables present:
C:\Documents and Settings\Administrator>set ALLUSERSPROFILE=C:\Documents and Settings\All Users APPDATA=C:\Documents and Settings\Administrator\Application Data CLIENTNAME=MYSECURITY ClusterLog=C:\WINDOWS\Cluster\cluster.log CommonProgramFiles=C:\Program Files\Common Files COMPUTERNAME=CMSSWEB ComSpec=C:\WINDOWS\system32\cmd.exe HOMEDRIVE=C: HOMEPATH=\Documents and Settings\Administrator LOGONSERVER=\CMSSWEB NUMBER_OF_PROCESSORS=1 OS=Windows_NT Path=C:\WINDOWS\system32;C:\WINDOWS;C:\WINDOWS\System32\Wbem;C:\Progra m Files\Ex ecutive Software\Diskeeper\ PATHEXT=.COM;.EXE;.BAT;.CMD;.VBS;.VBE;.JS;.JSE;.WSF;.WSH PROCESSOR_ARCHITECTURE=x86 PROCESSOR_IDENTIFIER=x86 Family 6 Model 8 Stepping 3, GenuineIntel PROCESSOR_LEVEL=6 PROCESSOR_REVISION=0803 ProgramFiles=C:\Program Files PROMPT=$P$G SESSIONNAME=RDP-Tcp#1 SystemDrive=C: SystemRoot=C:\WINDOWS TEMP=C:\DOCUME~1\ADMINI~1\LOCALS~1\Temp TMP=C:\DOCUME~1\ADMINI~1\LOCALS~1\Temp USERDOMAIN=CMSSWEB USERNAME=Administrator USERPROFILE=C:\Documents and Settings\Administrator windir=C:\WINDOWS
Of key importance to the forensic analyst are the following environment variables:
-
COMPUTERNAME. The actual name assigned to the computer in the currently running version of Windows. (You didn't trust the P-Touch label with the computer name on it, did you?)
-
COMSPEC. The location of the command interpreter. If this is anything other than the expected http://www.%SYSTEMROOT%\Command.com (Windows 9 x ) or %SYSTEMROOT%\System32\cmd.exe (Windows NT) this may indicate malicious code is present.
-
HOMEDRIVE/HOMEPATH. The home drive and path for the current user. Any user-specific files are likely to be under this hierarchy.
-
LOGONSERVER. The name of the domain controller that validated the credentials of the system at logon. The controller is likely to have log event information on this system.
-
OS. The name of the OS; NT will be displayed for Windows NT/ 2000/2003/XP.
-
PATH. The search path for executable files. They are searched in the order present. If multiple executables with the same name are found (for example, another cmd.exe file), check the PATH statement to see which one will be executed first.
-
PATHEXT. A list of the file extensions that Windows will treat as executable. Unusual extensions may indicate hidden files with those extension names on the system.
-
SYSTEMDRIVE/SYSTEMROOT. The default location of the Windows directory and system files. If this is different from the Windows/WINNT directories, multiple versions of an OS may be present.
-
TEMP/TMP. The location for the individual user's temporary files. A great place to check for copies of deleted files or transient files that were viewed or printed but not saved.
-
USERDOMAIN/USERNAME. The domain and the name of the user currently logged in. This information is useful in a live analysis when determining who was on the system at the time.
-
WINDIR. The location of the Windows directory. This takes the place of SYSTEMROOT on 9 x machines and is present on other Windows versions for backward compatibility.
| |
Files
As with directories, there are a few special Windows files which are frequently accessed as part of computer investigations. These files contain information pertinent to a broad range of forensic analyses. This section covers the locations and purpose of these files. The analyses of these files are covered in Chapter 10. Some of the most frequently accessed files are noted in Table 5-2.
| FILE NAME | DEFAULT LOCATION | DESCRIPTION |
|---|---|---|
| Thumbs.db | Any | Any folder which displays its contents in the Thumbnails view (for XP/2003) will cache small copies of the current and past images and movies present in the thumbs.db file. EnCase is able to read these files to extract file names as well as images. |
| Index.dat | Multiple | The index.dat files catalog various aspects of Internet-browsing history. Found under individual profile subdirectories, the analysis of these files is covered in Chapter 12. |
| Autoexec.bat | Root | The Autoexec.bat file is a legacy batch file set to run on startup with older versions of Windows. Any Windows version later than Windows 95 should only have a PATH statement present. |
| Boot.ini | Root | Any multi-boot information handled by Windows is found in this file, including the default boot device. |
| Config.sys | Root | The config.sys file is a legacy configuration file that previously contained driver loading instructions. This should no longer be used in current versions of Windows. |
| Pagefile.sys | Root | The pagefile is where Windows swaps out unused data from memory to the local drive to conserve RAM for program use. Because of this, fragments of information from programs are frequently found in this fileeven those never saved to disk. This is probably the most useful file to search for text strings on a Windows machine. |
| Hiberfil.sys | Root | On machines that have a hibernation mode (Windows 2000/2003/XP), the hiberfil.sys stores the hibernated configuration. This configuration consists primarily of the entire contents of RAM. When a machine goes into sleep or hibernation mode, the contents of RAM are saved to allow for restoration of all current programs, making this as fruitful as the pagefile.sys for text searches when present. |
| NTUser.dat | Documents and Settings\ <Profile Name> | The HKEY_Current_User registry hive is stored in the main profile folder of each user. The Default User directory contains the basic hive file for new users. The .log versions of the registry files store changes made in the session to those files. The .sav files are backups of the files created at system setup time, and their datestamps are one of the mechanisms to identify when the system was initially built. |
| Default | %SYSTEMROOT%\ System32\Config | The HKEY_Users .Default profile is stored in this file. |
| Sam | %SYSTEMROOT%\ System32\Config | The HKEY_LocalMachine\SAM hive, used for Windows account management, is stored here. |
| Security | %SYSTEMROOT%\ System32\Config | The HKEY_LocalMachine\Security hive, used for network security, is stored here. |
| Software | %SYSTEMROOT%\ System32\Config | Any software-specific settings from HKEY_LocalMachine\software are stored in this file. |
| System | %SYSTEMROOT%\System32\Config | The HKEY_Current_Config hive information is stored in this file. |
| AppEvent.evt | %SYSTEMROOT%\System32\Config | The Application event log file information is located here. Recovery of Event Logs is covered in a later chapter. |
| SecEvent.evt | %SYSTEMROOT%\System32\Config | The Security event log file information is located here. Recovery of event logs is covered in Chapter 11. |
| Hosts | %SYSTEMROOT%\System32\Drivers\Etc | Contains a mapping of DNS hostnames to IP addresses. Used before DNS lookups on Windows systems. |
| LMHosts | %SYSTEMROOT%\System32\Drivers\Etc | Contains a mapping of NetBIOS hostnames to IP addresses. Used before WINS lookups on Windows systems. |
| System.ini | %SYSTEMROOT% | Provides driver information to the operating system. Some of the functionality of this file has been transported to the Registry as Windows has evolved. |
| Win.ini | %SYSTEMROOT% | Provides operating system and application information to the operating system. Some of the functionality of this file has been transported to the Registry as Windows has evolved. |
| |
An unusual user problem prompted a security incident at one of the companies where I worked. The user reporting the problem consistently visited several well-known websites such as http://www.yahoo.com and http://www.google.com only to have pornography appear on her system. When asked how the user went to the websites , she indicated that she typed the individual site names into her web browser (as opposed to clicking email links or other mechanisms which may have created a similar problem).
The company had a proxy server setup, so an initial review of the proxy logs was done remotely. The proxy logs showed no requests for http://www.yahoo.com or http://www.google.com from the user reporting the problem. However, it did show requests based on IP addresses to two well-known sites containing hardcore pornography.
Initially, the evidence pointed to spyware or malware installed on the user's system which was redirecting web requests to the other sites. I had made the mistake of looking for a zebra before a horse. The Internet Explorer files did not match. The TypedURLs showed the Yahoo! and Google sites, but the Temporary Internet Files location showed the inappropriate content. No unusual plug-ins or ActiveX controls were found and both a virus and spyware scan turned up nothing.
To rule out the browser itself, I performed an nslookup on the command line, which returned the proper addresses for the hostnames. A ping, however, was sent to the offending IP addresses. This ruled out any Internet Explorer specific calamities.
As the resolution of the domain name from the company's server was correct, I looked for local resolution issues in the Hosts file. Opening this file revealed entries for several commonly typed websites, with the IP addresses of the inappropriate sites observed .
After interviewing her co-workers (not all computer investigation work involves sitting in front of a keyboard), one admitted that another person in the group had decided to play a joke on the user. The new suspect had altered the Hosts file while the user was away from her computer (she did not lock the system) to point her requests for innocent websites to the inappropriate material.
Because I could not prove who changed the file from the local evidence (the suspect performed the actions while logged in as the user), I reasoned how the suspect would have committed the act. Since most users do not know the IP addresses of websites by heart, I surmised the individual may have done a DNS lookup immediately before the last changed date on the Hosts file.
Sure enough, a review of the DNS server logs revealed the IP address of the requests. Matching that to DHCP logs (to determine who had the IP address) and then Event logs (to determine who was logged in to the machine at the time), I was able to identify and appropriately discipline the actual perpetrator for violating company policies on both appropriate usage and sexual harassment .
| |
| Tip | When entering into the command line a value that has spaces in it, surround the value with double quotes. |
| |
Microsoft uses a unique Security Identifier (SID) to link assets to user accounts. Every user account has an SID generated when it is created based on both the user name and the domain. Because the SID includes domain information, it will be unique for that particular domain/user combination (that is, the user name ihack on the domain CORPORATE will be different than ihack on the domain AUTHORIZED).
The SID is frequently used in computer investigations. By searching a drive for the SID of a particular user, files created by that user or profile information related to that user can be found. Likewise, by performing a reverse lookup of a SID, the user name associated with a given SID can be ascertained.
To facilitate this, there are two freeware tools, sid2user and user2sid. By running the tools on a known user name or SID (the relevant domain needs to be available), the analyst can determine their counterparts. As an example, looking at the Recycler folder shows an associated SID (the /a is needed, as the folder is hidden):
C:\RECYCLER>dir /a Volume in drive C has no label. Volume Serial Number is 0401-17DD Directory of C:\RECYCLER 09/08/2003 05:58 PM <DIR> . 09/08/2003 05:58 PM <DIR> .. 09/13/2004 04:39 PM <DIR> S-1-5- 21-117609710-764733703-842925346-1003 0 File(s) 0 bytes 3 Dir(s) 231,620,608 bytes free C:\RECYCLER>C:\temp\sid2user 5 21 117609710 764733703 842925346 Name is Domain is CLASS Type of SID is SidTypeDomain C:\RECYCLER>C:\temp\sid2user 5 21 117609710 764733703 842925346 1003 Name is Chad M.S. Steel Domain is CLASS Type of SID is SidTypeUser C:\RECYCLER>C:\temp\user2sid "Chad M.S. Steel" S-1-5-21-117609710-764733703-842925346-1003 Number of subauthorities is 5 Domain is CLASS Length of SID in memory is 28 bytes Type of SID is SidTypeUser C:\RECYCLER>C:\temp\user2sid Administrator S-1-5-21-117609710-764733703-842925346-500 Number of subauthorities is 5 Domain is CLASS Length of SID in memory is 28 bytes Type of SID is SidTypeUser C:\RECYCLER>C:\temp\user2sid Guest S-1-5-21-117609710-764733703-842925346-501 Number of subauthorities is 5 Domain is CLASS Length of SID in memory is 28 bytes Type of SID is SidTypeUser
In the preceding example, first the domain and then the individual user of the SID are looked up. The domain is everything except the generic S-1 and the final number and returns the name CLASS in this case. The user name in the domain, specified by 1003, returns the name Chad M.S. Steel. Performing a reverse lookup returns on the name returns the SID value.
Even if the domain is not available, some information can be obtained from the last group of numbers in the identifier. Specifically, any identifier ending in ˆ 500 will always refer to the Administrator account, even if that account is renamed . Likewise, any identifier ending in =501 always refers to the Guest account.
| |
| | ||
| | ||
| | ||
EAN: 2147483647
Pages: 71