Exam 70-124: Objective 3.4: Securing Server Message Block Traffic
|
|
The Server Message Block (SMB) authentication protocol provides for mutual authentication, which can help prevent the man-in-the-middle type of attack, and it supports message authentication, which helps prevent message attacks. This security, which is easily configured, is provided by placing a digital signature into each SMB, which is then verified by both the client and the server involved in the communication.
| Test Day Tip | Although we discuss the man-in-the-middle attack in more detail in later chapters, a brief explanation is in order here so that you fully understand how securing SMB traffic is something that you want to do. A man-in-the-middle attack occurs when data is intercepted by a third party (an unauthorized attacker), modified, and sent through to the party that was the original recipient. The attacker can thus intercept and modify traffic from both legitimate ends of the connection, in effect driving the connection in the direction he or she wants. |
In order for SMB signing to actually work on your network, it must be configured at the same minimum level on both the client and the workstation. You have two basic levels of configuration from which to choose:
-
To digitally sign client communication (when possible) and digitally sign server communication (when possible)
-
To digitally sign client communication (always) and digitally sign server communication (always)
Table 2.1 presents the default SMB settings that are configured on a server or workstation, depending on the security template that has been implemented on the device.
| Template | Digitally Sign Client Communication (When Possible) | Digitally Sign Client Communication (Always) | Digitally Sign Server Communication (When Possible) | Digitally Sign Server Communication (Always) |
|---|---|---|---|---|
| basicdc.inf | Not defined | Not defined | Enabled | Not defined |
| basicsv.inf | Enabled | Disabled | Disabled | Disabled |
| basicwk.inf | Enabled | Disabled | Disabled | Disabled |
| compatws.inf | Not defined | Not defined | Not defined | Not defined |
| securedc.inf | Enabled | Disabled | Enabled | Disabled |
| securews.inf | Enabled | Disabled | Enabled | Disabled |
| hisecdc.inf | Enabled | Enabled | Enabled | Enabled |
| hisecws.inf | Enabled | Enabled | Enabled | Enabled |
| setup security.inf | Enabled | Disabled | Disabled | Disabled |
If SMB signing is enabled on a server, clients that are also enabled for SMB signing (or require it) will be able to establish a communications session with that server. If SMB signing is required on a server, a client will not be able to establish a session unless the client, at the minimum, has SMB signing enabled.
SMB signing is configured from the Computer Configuration | Windows Settings | Security Settings | Local Policies | Security Options node, as shown in Figure 2.26.SMB signing consumes some CPU cycles on any machine on which it is configured. Conservative estimates place this value as high as 15 percent overhead, although the value you can expect to see is largely dependent on the amount of traffic a specific computer receives.
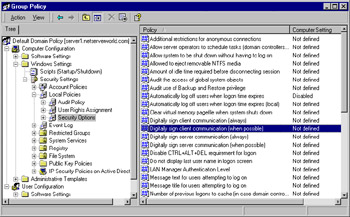
Figure 2.26: Configuring SMB Signing
| Exam Warning | Make sure that you understand the various configuration options available to you for configuring SMB signing. It's quite easy to get tripped up by not paying attention to what a question is asking when it comes to SMB signing options. You should expect to be asked briefly about SMB signing in some fashion on the exam. |
|
|
EAN: 2147483647
Pages: 162