Configuration Management for MPLS-Based Networks
| Deploying and offering MPLS VPN services for enterprise customers requires network resource planning, as well as deployment, maintenance, and configuration of the network elements and services. This manual procedure can be time-consuming and inaccurate. Service providers have expressed the desire to automate these steps to be competitive in this market. For a complete service offering, however, service providers must be able to quickly and effectively plan, provision, operate, and bill for the VPN-based services they offer. Figure 12-3 highlights the challenges in MPLS service provisioning; simply put, manual deployments no longer scale. Figure 12-3. MPLS Service Provisioning Challenge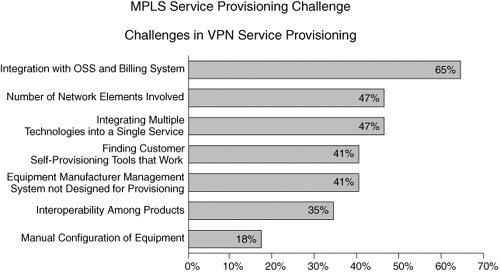 Customer priorities for provisioning are as follows:
Layer 3 VPNs differ from Layer 1 and Layer 2 VPNs in that the service provider interacts with the customer at Layer 3 and provides routing and forwarding services to the service user, thereby delegating control of the routing architecture of the core transport to the service provider. Layer 3 VPN service providers have multiple Layer 2 access technologies, such as ATM, Frame Relay, serial, Ethernet, and virtual LANs, to provide connectivity to users. For Layer 3 VPNs, the customer premises equipment (CPE) can be a router or switch because a Layer 3 VPN can consist of an Ethernet segment as a handoff to the customer. In this scenario, the customer might choose to implement an Ethernet switch and use the service provider router as the default gateway between sites. Layer 3 VPNs provide only routed connectivity and do not bridge or forward non-IP protocols. The routing characteristics of the Layer 3 VPN are strictly defined and enforced within the service provider's network and, more importantly, provide security from other Layer 3 (and Layer 2) VPNs that are defined across the same infrastructure. The degree of scaling achievable within a Layer 3 VPN is provided by the use of extensions to the Border Gateway Protocol (BGP4), a robust, Internet-scale routing protocol that has been extended to support the concept of VPN awareness. We have already discussed these scaling attributes earlier in the book. Because service providers need to bring services to market quickly, train field operators, and deploy accurate customer services, they are increasingly turning to OSSs or business support systems (BSS) to find solutions. The Cisco IP Solution Center manages a range of Layer 2 and 3 MPLS-related technologies, including these:
Cisco Info Center VPN Policy Manager integrates with Cisco IP Solution Center to enable a deeper understanding of which MPLS VPNs are affected by a network fault, how to prioritize events, and how to effectively and quickly troubleshoot the problem. After the VPN has been analyzed, a report is sent to the Cisco Info Center detailing the affected MPLS VPNs and the customers running across those VPNs. This information is presented to the network operations center (NOC) or VPN user as a specific customer network managed view. This capability provides clear benefits, including:
For fault management in particular, Cisco Info Center is integrated with the Cisco ISC Northbound Programmatic Interface (XML over HTTP) to provide fault management functions in a service provider's NOC. The following fault scenarios are supported:
For all these events (SNMP traps or syslog messages), Cisco Info Center initiates a query via the Cisco ISC Northbound Interface to extract the impacted provider edge, customer edge, site, customer, and VPN information. In the case of Layer 2 access into MPLS VPN, the added fault conditions are in the Layer 2 Ethernet access domain. VLANs are used to distribute the customer access. Ethernet Relay Service (ERS), Ethernet Wire Service (EWS), and Layer 2 access into MPLS VPN are the services currently supported for the Cisco Metro Ethernet Services. Many customers could be serviced using the same Layer 2 Ethernet infrastructure. A failure in any given link can potentially impact many customers. In this scenario, Cisco Info Center correlates a single interface failure to many customers and services. The types of failures include, for example:
ISC also has two proactive mechanisms to detect any fault in the network. For all the MPLS VPN and L2 VPN services that ISC deployed, ISC has the corresponding IOS CLI configuration. Network operators can schedule on a periodic basis a configuration audit for the deployed services. A configuration audit connects to all the routers/switches involved in a given service request and verifies the presence of the IOS CLI commands on the network devices. For MPLS VPN services in particular, ISC can perform a functional audit, which consists of a configuration audit and a routing audit that consists of verifying that the 30 PE-CE IP addresses have propagated to the correct PE. This routing audit is performed in the context of an MPLS VPN hierarchy (full mesh, hub and spoke, or partial mesh). If a problem is detected, ISC marks the service request to the "Broken" state for a routing problem and to "Lost" for a missing configuration. A tool such as ISC can certainly facilitate provisioning for both Layer 2 and Layer 3 VPNs and is a key component for OSS/BSS. |
EAN: 2147483647
Pages: 162
- Chapter VII Objective and Perceived Complexity and Their Impacts on Internet Communication
- Chapter X Converting Browsers to Buyers: Key Considerations in Designing Business-to-Consumer Web Sites
- Chapter XI User Satisfaction with Web Portals: An Empirical Study
- Chapter XII Web Design and E-Commerce
- Chapter XV Customer Trust in Online Commerce