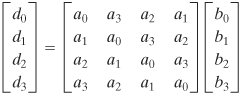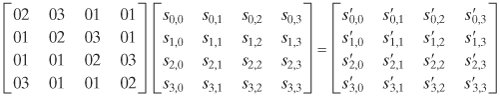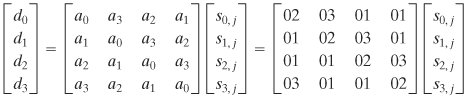Appendix 5A Polynomials with Coefficients in GF(28)
Appendix 5A Polynomials with Coefficients in GF(28)In Section 4.5, we discussed polynomial arithmetic in which the coefficients are in Zp and the polynomials are defined modulo a polynomial M(x) whose highest power is some integer n. In this case, addition and multiplication of coefficients occurred within the field Zp; that is, addition and multiplication were performed modulo p. The AES document defines polynomial arithmetic for polynomials of degree 3 or less with coefficients in GF(28). The following rules apply:
We need to keep straight which polynomial we are talking about. Recall from Section 4.6 that each element of GF(28) is a polynomial of degree 7 or less with binary coefficients, and multiplication is carried out modulo a polynomial of degree 8. Equivalently, each element of GF(28) can be viewed as an 8-bit byte whose bit values correspond to the binary coefficients of the corresponding polynomial. For the sets defined in this section, we are defining a polynomial ring in which each element of this ring is a polynomial of degree 3 or less with coefficients in GF(28), and multiplication is carried out modulo a polynomial of degree 4. Equivalently, each element of this ring can be viewed as a 4-byte word whose byte values are elements of GF(28) that correspond to the 8-bit coefficients of the corresponding polynomial. We denote the modular product of a(x) and b(x) by a(x) Equation 5-10 where c0 = a0 · b0 c1 = (a1 · b0) c2 = (a2 · b0) c3 = (a3 · b0) c4 = (a3 · b1) c5 = (a3 · b2) c6 = (a3 · b3) The final step is to perform the modulo operation: d(x) = c(x) mod (x4 + 1) That is, d(x) must satisfy the equation c(x) = [(x4 + 1) x q(x)] such that the degree of d(x) is 3 or less. A practical technique for performing multiplication over this polynomial ring is based on the observation that Equation 5-11 If we now combine Equations (5.10) and (5.11), we end up with d(x) = c(x) mod (x4 + 1) = [c6x6 + c5x5 + c4x4 + c3x3 + c2x2 + c1x + c0] mod (x4 + 1) = c3x3 + (c2 d0 = (a0 · b0) d1 = (a1 · b0) d2 = (a2) · b0) d3 = (a3 · b0) This can be written in matrix form: Equation 5-12 MixColumns TransformationIn the discussion of MixColumns, it was stated that there were two equivalent ways of defining the transformation. The first is the matrix multiplication shown in Equation (5.3), repeated here: The second method is to treat each column of State as a four-term polynomial with coefficients in GF(28). Each column is multiplied modulo (x4 + 1) by the fixed polynomial a(x), given by a(x = {03}x3 + {01}x2 + {01}x + {02} From Equation (5.8), we have a3 = {03}; a2 = {01}; a0 = {02}. For the jth column of State, we have the polynomial colj(x) = s3,jx3 + s2,jx2 + s1,jx + s0,j. Substituting into Equation (5.12), we can express d(x) = a(x) x colj(x) as which is equivalent to Equation (5.3). Multiplication by xConsider the multiplication of a polynomial in the ring by x: c(x) = x c(x) = x = (b3x4 + b2x3 + b1x2 + b0x) mod (x4 + 1) = b2x3 + b1x2 + b0x + b3 Thus, multiplication by x corresponds to a 1-byte circular left shift of the 4 bytes in the word representing the polynomial. If we represent the polynomial as a 4-byte column vector, then we have |
EAN: 2147483647
Pages: 209