Miscellaneous
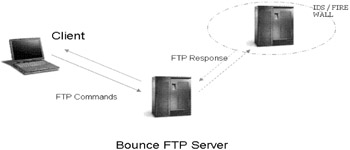
| Concept | FTP bounce A creative scan first detailed by 'Hobbit', takes advantage of the FTP servers with read/write access. The advantage of this scan can be both anonymity and accessibility. For instance suppose the target network allows FTP data transfer from only its recognized partners . |
An attacker might discover a service business partner who has a FTP service running with a world- writeable directory that any anonymous user can drop files into and read them back from. It could even be the ISP hosting services on its FTP server.
The attacker, who has a FTP server and able to run in passive mode, logs in anonymously to the legitimate server and issues instructions for scanning or accessing the target server through a series of FTP commands. He may choose to make this into a batch file and execute it from the legitimate server to avoid detection.
If a connection is established as a means of active data transfer processing (DTP), the client knows a port is open , with a 150 and 226 response issued by the server. If the transfer fails a 425 error will be generated with a refused build data message. The PASV listener connection can be opened on any machine that grants a file write access to the attacker and used to bounce the scan attack for anonymity. Hobbit points out that "it does not even have to be an FTP server -- any utility that will listen on a known TCP port and read raw data from it into a file will do".
Often these scans are executed as batch files padded with junk so that the TCP windows are full and the connection stays alive long enough for the attacker to execute his commands. Fingerprinting the OS can help determine the TCP window size and allow the attacker to pad his commands for further access accordingly . Fingerprinting is discussed in detail later in this module.
This scan is hard to trace, permits access to local networks and evades firewalls. However, most FTP servers have patched this vulnerability by adopting countermeasures such as preventing third party connections and disallowing listing of restricted ports. Another measure adopted has been to restrict write access.
| Concept | UDP Scan We have seen how private ports are assigned at the higher end and UDP scans try to detect the state of the port by transmitting a zero byte UDP packet to the target system and the concerned port. An open port does not respond, while a closed port will reply with an ICMP HOST UNREACHABLE response. Similar to inverse mapping, the absence of evidence is considered as the evidence of presence. |
The disadvantage to the attacker is that UDP is a connectionless protocol and unlike TCP does not retransmit packets if they are lost or dropped on the network. Moreover, it is easily detected and unreliable (false positives). Linux kernels limit ICMP error message rates, with destination unreachable set to 80 per 4 seconds, thereafter implementing a 1/4 second penalty if the count is exceeded. This makes the scan slow and moreover the scan requires root access. However, it avoids TCP based IDS and can scan non-TCP ports.
EAN: N/A
Pages: 109