The Inefficiencies of FLSM
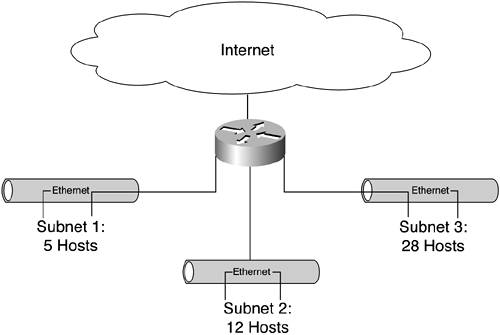
| Chapter 3, "Fixed-Length Subnet Masks," showed you how FLSM lets you conserve the IP address space by creating locally significant subnetwork addresses. The benefit of this is that you can use a single network address to service multiple local networks. But in the real world, those local networks are seldom the same size. Thus, implementing FLSM actually wastes IP addresses. To better illustrate this point, consider the network shown in Figure 4-1. We will use this basic network diagram as the basis for exploring VLSM throughout this chapter. Figure 4-1. Sample Network
This example is simplified throughout this chapter for the sake of demonstrating the relative efficiencies of VLSM versus FLSM. It is not intended as a realistic example, nor is it indicative of how you would actually subnet a block of network addresses. Consequently, you might notice that there are no IP addresses in the subnets assigned to LAN switch or hub management ports. Similarly, some of the subnet address ranges do not end neatly on the bit boundaries indicated by their mask. Although this scheme would work, it is not ideal. Again, it is intended solely to demonstrate relative efficiencies. It's not a guide for how to subnet on the job. We'll look at how to do that in subsequent chapters. For now, we'll just concentrate on the basics, and that requires some simplifying assumptions. In Figure 4-1, you can see that the local subnets are of very different sizes. Subnet 1 contains just five hosts. Subnet 2 contains 12 hosts, and Subnet 3 contains 28 hosts. Without any form of subnetting, you might have to resort to using three different Class C networks for each of these subnetworks. That would be a tremendous waste of addresses: 765 total addresses for just 45 hosts! Subnetting a traditional Class C network using fixed-length subnet masking requires you to use a mask large enough to satisfy the largest of the three subnets. That would be Subnet 3 with its 28 hosts. As you saw in Chapter 3, this would require subnetting the entire 24-bit network address with a mask of 255.255.255.224. That mask borrows 3 bits from the host field to create a 27-bit extended network prefix. The result is a 5-bit host field that lets you define six usable subnets, each with 30 assignable IP addresses. When I say "assignable," I'm referring to the reservation of both the all-0s and all-1s addresses. There are 32 mathematically possible addresses per subnet, but you need to reserve one host address (the all-0s address) for subnet identification and the all-1s address for IP-based broadcasting within that subnet. NOTE The notion of reserving all 0s and all 1s is found throughout the history of the Internet and the Internet's address space. Confusion results because this convention has been applied to both subnet addresses and host addresses. As host addresses, these values are necessary within a subnet for subnet identification and broadcasting. Broadcasting is a transmission technique that sends the same packets of information to every connected host within a specific scope. In this particular case, the all-1s host address within any given subnet would be used to communicate with all hosts within that subnet. This practice differs starkly from the obsolete practice of reserving all-0s and all-1s subnet addresses. Reserving those subnet addresses was arbitrary and was recommended solely for the sake of maintaining consistency of language within the network engineering community. In this example, a total of 45 addresses are wasted through inflexibility. Using a mask of 255.255.255.224 to accommodate the needs of your largest subnet (Subnet 3) results in varying surpluses of addresses available in each subnet. Table 4-2 demonstrates how FLSM wastes addresses through the inflexibility of its subnetting mask.
Using FLSM saves IP addresses in this example when compared to just giving each subnetwork its own Class C network address. Of course, you could make a very convincing argument that you would never want to precisely size a subnet, even if doing so were technically feasible. Such an effort might well result in a very painful renumbering exercise in the future when growth inevitably occurs. We'll look at how you can manage growth within a subnet later in this chapter. For now, let's look at how VLSM can improve on the efficiency with which you can use an address space. Comparing VLSM to FLSMVLSM greatly improves the efficiency with which the sample network can be subnetted. Instead of just using a 3-bit subnetwork field (mask of 255.255.255.224) for all fields, you can use whichever size mask makes sense for each subnet. In Chapter 3, we looked at a table that correlated the trade-offs between the number of hosts and the number of subnets that could be created from a 24-bit network address. That table, and that entire chapter, were focused on Classical IPin other words, the way things used to be! Reserving the all-0s and all-1s subnets is no longer necessary or desirable. Consequently, the tables in this chapter reflect the availability of all mathematically possible subnet addresses. With that caveat in mind, take a look at Table 4-3. Notice the gaps between subnet sizes? This should be a very familiar pattern by now, because it is a function of binary mathematics. Intuitively, you should recognize that VLSM won't be perfectly efficient, simply because subnet sizes (created from a 24-bit network address) increment from two usable host addresses to 6, to 14, to 30, and then to 62. We'll talk about this phenomenon later in this chapter, including why such gaps might be useful.
Armed with this information, you can return your attention to the sample network. Looking at Table 4-2, Subnet 3 (which contains 28 hosts) would still require 5 bits for host addressing, so the best-size mask would still be 255.255.255.224. Subnet 1, however, would be better off with a mask of 255.255.255.248. That mask allocates 5 bits to the subnet identification field and 3 bits to host identification. A 3-bit host field yields six usable host addresses, which is perfect for the five-host subnet, and it still leaves an extra address for future growth. Subnet 2, with its 12 hosts, would be best-served with a mask of 255.255.255.240, because that mask evenly splits the host address into 4 bits for the subnet and 4 bits for host identification. This lets you assign 14 unique host addresses within a subnet. Table 4-4 demonstrates the binary and decimal mathematics of the right-sized mask for each of the three subnets. Given that the first three octets are all high values of 255 or 11111111 in binary, I conserve space and save your eyesight by showing only the contents of the mask's last octet. The first three octets are indicated with the constant n. The binary values in this table adhere to my convention of showing the bits representing the subnet ID in a bold italic font.
As you can see, the most efficient subnet mask for each of the three subnets differs for each network. The downside of carefully tailoring a subnet mask to a subnet is the limitation of capacity for future growth. Ideally, you want some room for future growth, but predicting how much growth will be experienced is more of an art than an exact science. For the sake of the example, you need only 3 bits for host addressing in Subnet 1, 4 bits for host addressing in Subnet 2, and 5 bits for host addressing in Subnet 3. Using VLSM lets you use those three different masks within the same network address to achieve a dramatic reduction in wasted or unusable IP addresses. Table 4-5 compares the relative efficiency of FLSM versus VLSM in the sample network.
Quickly summing the number of IP addresses wasted using FLSM for the sample network vis-à-vis VLSM reveals that there can be a dramatic improvement. In the sample network, FLSM requires you to use a 3-bit mask, resulting in a waste of 45 IP addresses in just three subnets. That wasted amount drops to just five with a VLSM scheme. | ||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||
EAN: 2147483647
Pages: 118