7.5 Certificate revocation list
|
7.5 Certificate revocation list
At long last, we finally get to the CRL. So what is this magical thing called the CRL?[3] Figure 7.6 shows an example of a CRL, or certificate revocation list. When a certificate is issued to an end user or systems, it is expected to be in use for the period that it is valid. So far, so good. Following, however, are circumstances in which you may want to revoke that certificate:
-
An employee quits. If an employee leaves your organization, you will want to invalidate the certificates he or she has been using. The CRL will accomplish this step.
-
You suspect that the certificate has been compromised. This is actually an old problem, notably with passwords: "Here, use my password while I am gone. It's okay but don't tell anyone." In many browsers, you can export a certificate and import it into another browser. Next thing you know, someone has submitted a purchase order for a billion dollars in chewing tobacco. In this example, you place the old certificate into the CRL and issue a new one.
-
A person changes his or her name. In this case, the old certificate is placed into the CRL and a new one is issued. There are some PKI systems that accommodate for new names without issuing a new certificate (such as Lotus Notes).
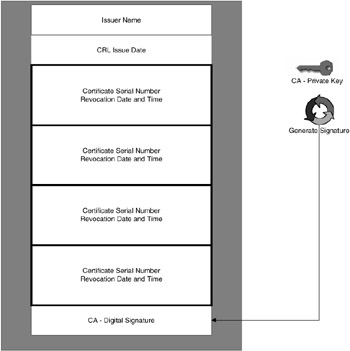
Figure 7.6
Overall, the CRL is a list of revoked certificates that is signed by a CA. One of the biggest issues with a CRL is the time difference between when a certificate has been identified as required to be in the CRL and when it actually gets put into the CRL. PKIs have actually been around for several years, and, as a result, many bad habits have been noticed by most organizations, such as:
-
Days or even weeks pass before a certificate is placed into the CRL (in some implementations, this is also known as the termination list).
-
The certificate is not put into the CRL at all.
-
A CRL does not exist!
Make sure you put processes in place to manage certificates that need to be removed from your organization. Another concern is the huge size that the CRL can become. In the case of a large enterprise organization, the CA can be expected to certify thousands, or even hundreds of thousands of entities. Over time, the CRL can get really big. In itself, this could be a problem. Some PKI systems have software that can help manage this. Check with your vendor.
[3]You can find one answer at http://www.ieft.org/rfc/rfc2459.txt