5.6 Secure access - SSL based extranet appliances
|
5.6 Secure access SSL based extranet appliances [5]
The ability to provide remote access to corporate applications has always been a challenge. Virtual Private Networks (VPNs) have addressed this challenge, but not without a cost. VPNs require the installation of software on a client PC, ultimately resulting in increased calls to an already overburdened Help Desk. VPNs are also time consuming to deploy, so the lead-time to deliver access to a corporate application from the Internet can be quite long. Historically, VPNs have been adopted by employees and corporate partners for remote access. VPNs have not addressed access for kiosk users, retiree access, disaster recovery or access from locations where VPN connectivity is disabled.
An emerging market has developed for products that provide secure access for all client "profiles," meaning employees, retirees, corporate partners, kiosk access, and disaster recovery usage regardless of client location. Essentially, this market provides "anywhere, anytime, any-client" access to corporate applications. This market leverages existing desktop functionality to provide remote access to all applications, including Web, Client/Server, Terminal Services, Messaging, File Services, and Terminal Emulation Applications. These remote access technologies take advantage of the onboard security (SSL) built into a web browser, as well as the ease of use that a browser provides. By using a browser for connectivity, companies will avoid the cost of maintaining and deploying client software and provide a familiar interface for the end-user. These technologies are therefore referred to as clientless, as client VPN software is not required (see Figure 5.4).
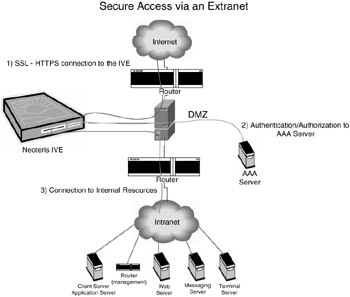
Figure 5.4
Clientless solutions enable enterprises to provide access to all of their internal IT resources over the public Internet, thereby creating what is often referred to as an Extranet. In the past, Extranets were typically implemented as distinct network elements to service a corporation's business partners. Rather than compromising security by opening up communication directly with internal production resources, IT managers prefer to offer limited access to an Extranet, which is deployed in a DMZ to ensure the security of critical production servers. The downside of such Extranet deployments is that they are customized for each application, so each deployment incurs a significant expense. Capital expenditures are required for each additional Web and application server, as well as authentication, and access control software. In the past, IT Departments would incur incremental charges every time they needed to customize and integrate a new service or application into the Extranet. As each discrete Extranet component is added, the risk of a security violation also increases.
When developing an Extranet, security is always a top priority. Regardless of the type of Extranet that is being developed, companies must ensure that each Extranet component has been rigorously tested to eliminate security vulnerabilities. Custom, nonappliance based Extranet components must go through a hardening process which should involve hardening web servers, operating systems, network components, and applications. The hardening process is a tedious, time-consuming process. The hardening of any device involves the removal of all unnecessary services and the application of all known security patches. SSL based Extranet Appliances should also be evaluated for Security integrity, however many are pre-hardened by the manufacturer. This eliminates the ongoing hardening process required by traditional Extranet components.
Because of the broad accessibility of Extranets (tens of thousands of people may have access to a large enterprise Extranet), the need for authentication, authorization, and accounting controls are very important. Authentication controls are important to ensure the user is who he claims to be. Static user names and passwords are easy to hack; therefore, most organizations require two-factor authentication technologies for Extranet remote access. These two factors include something that you possess (e.g. a random number generator token or digital certificate) and something you know (a PIN or password). Authorization controls (sometimes referred to as entitlement) provide each user or user group permission to access specific applications or resources. Each user profile has different requirements. For example, a retiree may only need to access an HR benefits web site; a clerical worker may need access to e-mail; and an executive may need access to ERP, Sales Force Automation, and Executive Information Systems applications. Accounting or auditing is important as it provides a trail of remote access activity. This is particularly important where customer privacy and regulatory compliance is an issue. In many cases system logs must provide information that allow a system administrator to re-create exactly what a remote client did while accessing a specific application.
Instant Virtual Extranet (IVE) appliances from companies like Neoteris, Inc. simplify the deployment of Extranets. They reduce the complexity and security implications of delivering internal applications to remote users. IVEs integrate with industry standard authentication databases, they provide access to a large number of IT applications, with robust application-layer security that allows for granular group-based authorization down to the URL and file level. Extranets that include an IVE do not require new servers or duplicated application software licenses or software plug-ins/APIs to be integrated with existing infrastructure. They give companies the benefit of being securely connected to all clients instantly, without the upfront and ongoing maintenance costs of custom Extranet installations.
[5]This section reprinted with permission from Neoteris, Inc. (Author: Ken Spinner).