Chapter 4: Secure Networks
|
4.1 TCP/IP and OSI
Imagine if you will, a classroom filled with entry-level web technology students. We have some questions from the audience: "What makes up the Internet?" "What is it?" One answer is TCP/IP. "Oh that tells me a lot! It sounds like some kind of drug!" The next question is, "Where should we start and what level of detail should we go into?" The useful answers to these questions will be answered in this chapter.
TCP/IP is a very complex protocol. There are entire books dedicated to the subject. We need to discuss TCP/IP at some length in order to understand the security issues with the protocol. Throughout this chapter, we will list some books and URLs that provide further information on TCP/IP. Most major operating system vendors offer some type of course on TCP/IP. As part of the MCSE program from Microsoft (MCSE 2000 Microsoft Corporation), there is a test that is specifically dedicated to TCP/IP. Please see the references or take a course for a full coverage of TCP/IP. We will start with a high-level overview of TCP and its components and then cover a few security-related issues.
In 1973, Vinton Cerf, a UCLA graduate student who is also known as the "father of the Internet," and Robert Kahn, an MIT math professor, developed a set of software "protocols" to enable different types of computers to exchange data. These protocols are now known as TCP/IP. The base part of the protocol is called IP, or "Internet Protocol." It is the IP part of the protocol that actually transports the packets of data between the various computer systems on the Internet. The part of the protocol that actually ports data to the applications is called "TCP." TCP is the mechanism that allows the WWW (World Wide Web) to communicate. Programs are built on top of this medium that allow communication between server and client.
There is an old story about Vinton Cerf. He was at a computer convention and was trying to make a point about the protocol, which he did by removing his overcoat to display this message on his T-shirt: IP on Everything.
We have no idea if this story is true, but it is a good one anyway.
The Transmission Control Protocol (TCP) is intended for use as a highly reliable host-to-host protocol between hosts in packet-switched computer communication networks. Hacking into computers can include port scanning, or surfing.
Figure 4.1 shows a port scanner run on the program on a private address on a home network, 192.9.200.69. The results showed that ports 80 and 139 were open. Looking at this, we can see that we could access those ports with some type of application. We could possibly even flood those ports with requests from several sources. Also, we could test other addresses to see if other services were available, such as Telnet, FTP, and TFTP. Then, using that information, we could attack those IP addresses and attempt to access the sites or block access to the sites with a denial-of-service attack.
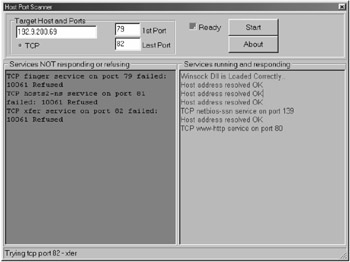
Figure 4.1
Figure 4.2 shows an example from the Savant Software Program HostScan Version 1.5.
Figure 4.2
|