3.4 PKI and business solutions
|
3.4 PKI and business solutions
What will all this security do for your business and how will it keep it secure? Let's look at several business scenarios.
-
You are sending important messages to sales reps via the Internet to different parts of the world. These sales reps travel extensively and carry a laptop with them. How can you protect these messages from unauthorized access?
-
Vendors place orders into an Extranet. This Extranet will take the orders and trigger an immediate shipment to the vendor. "But wait," the vendor says. "I did not order 10,000 horseshoes." How can you prove the vendor actually ordered the horseshoes?
-
Your business also sells horseshoes to customers who pay by credit card. How can you keep the credit card information safe and secure during transmission between the customer's browser and your web server (i.e., prevent the bandits from getting the card and expiration data)?
-
Your business has 1,000 users worldwide. You know who these users are, and these users provide at least 80 percent of your sales via the Internet. You have heard from your techie smart people that user names and passwords are not secure without SSL. But these users also need to send encrypted e-mail. Wow! How do you solve this problem?
Before we start to review each scenario, we need to add a disclaimer. These scenarios are here to facilitate a discussion for real-life examples. There are several methods to solve these problems, and the method presented may not necessarily be the right one for your business. As you read in Chapters 1 and 2, you must balance the solutions with your business requirements. These examples are presented here to demonstrate technical solutions. With that said, here they are.
3.4.1 Scenario one
| Example: | You are sending important messages to sales reps via the Internet to different parts of the world. These sales reps travel extensively and carry a laptop with them. How can you protect these messages from unauthorized access? |
S/MIME is the solution for this problem. S/MIME has nothing to do with Marcel Marceau. The problem here is that you need to send important messages via the Internet, a potentially dangerous place where someone unscrupulous can easily intercept your messages and decipher them unless you encrypt the message via a method such as S/MIME. Other methods such as PGP may be better, but first a point will be made here and then we will talk more about PGP.
As we said before, S/MIME provides a method to send and receive secure MIME messages. So what exactly is a MIME message? MIME is described in the IETF standard RFC 1521 and explains how an electronic message is formatted. MIME (Multipurpose Internet Mail Extensions) is a set of specifications that describes a method to offer text via various character sets and multimedia. In order to fully understand S/MIME we also need to cover a topic called "certificates." Chapter 7 will take you through a detailed certificate discussion.
Figure 3.5 is an example of a certificate, a digital identity that is linked to a specific user or person. In our example, a certificate will be placed into each user's e-mail system, another is placed into the public directory (the public key), and another is placed into the e-mail client (the private key).
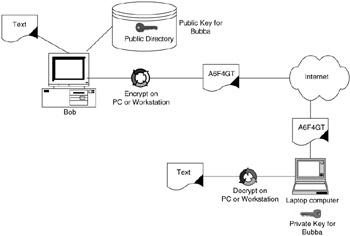
Figure 3.5
In our example, Pistol Jack sends a message to Tex Hunter. Jack finds Tex's public key in the directory and sends him a message. Jack's workstation software encrypts the message and it is then sent via the Internet (SMTP) to Tex's workstation (via a service provider and a POP account). When Tex opens the message, it is automatically decrypted. Now Tex can reverse the process. If he has Jack's public key or access to the directory where Jack's key is stored, then Tex can send an encrypted message back to Jack. This process is accomplished by the S/MIME protocol. See these RFCs for more information.
-
S/MIME Version 2 Message Specification (RFC 2311)
-
S/MIME Version 2 Certificate Handling (RFC 2312)
The solution for our first problem is to implement a mechanism to send S/MIME messages between the home office and the person in the field.
3.4.2 Scenario two
| Example: | Vendors place orders into an Extranet. This Extranet will take the orders and trigger an immediate shipment to the vendor. "But wait," the vendor says. "I did not order 10,000 horseshoes." How can you prove the vendor actually ordered the horseshoes? |
In this example, the vendor said they did not place the order that you received into your on-line order system. From the Internet perspective, it can be difficult to say exactly who "someone" is. It is easy to impersonate another person, unless a digital certificate is being used.
The same digital certificate that is used for reading encrypted mail can also be used to digitally sign documents. When the document is signed, you can then tell who actually sent the document. With messages sent on the Internet, it is easy to modify the "from" field and spoof the identity of the sender. No problem there. We will require that the sender digitally signs all orders so we can prove that the messages really originated from the vendor. There are many issues to this problem, and we will stick with our case in point, digital signatures. (The assumption is made that the order did arrive and our order processing department did not make an error.) This process of proving who actually sent the message is called "nonrepudiation." This service provides virtually unforgeable evidence that a specific action occurred or, in our case, a transaction was fulfilled. This is all possible via a certificate. (Another assumption made is that the vendor has not lost control of the certificate stay with us on that.) Nonrepudiation can be used by both the sender of the order and the recipient that is, the business receiving the order to prove to a third party (such as a judge) that the sender did indeed send the transaction and also that the recipient received the same transaction that was sent. Remember the MD2 and MD5 message digests? If any one character of a message were changed, then up to half of the message digest would change. It is very difficult to modify a message and keep the message digest the same (for most of the world's population, it is impossible).
In our example (see Figure 3.6), Jack has digitally signed a message and it is sent to Tex. The software that Tex has will automatically attempt to verify that the signature is from Jack via the public directory. Now back to the scenario: If the vendor says that they did not send the order or that the order was for 1,000 horseshoes instead of 10,000, then you have proof that the order was sent for 10,000 horseshoes, thanks to the digital signature that they sent you (and that you required before filling the order).
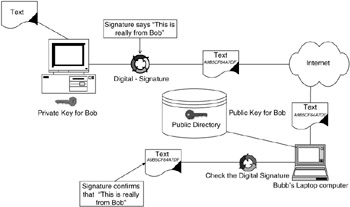
Figure 3.6
3.4.3 Scenario three
| Example: | Your business also sells horseshoes to customers who pay by credit card. How can you keep the credit card information safe and secure during transmission between the customer's browser and your web server (i.e., prevent the bandits from getting the card and expiration data)? |
Data is transmitted between your browser and the web server via some type of network and protocol. The network could be your network at the office or a dial-in system from your house. There are also networks that connect to the cable in your house. The protocol that is used in most cases by the Internet is TCP/IP, which we will discuss in a later chapter. Using a packet sniffer, the bandits can hook on to your network or at your ISP and capture your network packets. There are many places on the Internet where someone can "steal" your packets. A network packet, for this discussion, is an envelope of data. Much like you would send a letter in an envelope to a friend via the post office, you would send e-mail via packets of data via a network. This is all done for you with software and protocols. TCP/IP is the underlying protocol of the Internet. So with a packet sniffer, these packets can be captured and read. It is possible to extract all types of information such as the following:
-
Where the packet is going
-
Where the packet is from
-
If the data in the packet is encrypted
-
Any user name in the packet
-
Any password in the packet
-
Any data contained in the packet, such as a message or a part of a message, such as your credit card number
-
Much more
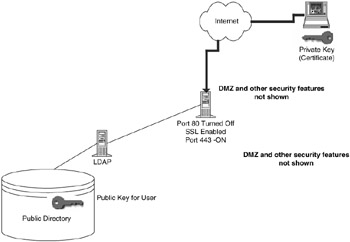
In our discussion of TCP/IP to come, we will see the OSI reference model, which helps us understand the technical aspect of where we should encrypt data. In this chapter we will discuss why we encrypt the data: to establish customer trust and customer confidence. We can enable a feature on our servers called SSL (Secure Sockets Layer). SSL uses encryption technology developed by RSA Data Security, Inc. The encryption is implemented at the network layer so that anyone trying to capture a packet will receive a packet with encrypted data, which would be very difficult to decode or crack. In order to start a secure session between the client and server you need to have set up certificates on both the server and the client.
Today, most browsers used will have some type of "root certificate." This root certificate is a mechanism that identifies what company issues the certificate. There are companies known as (actually, that act as) certificate authorities (CA). These CAs will act as an authority that certifies that the server you are accessing is really the server you want. Say, for example, when you go to http://www.amazon.com/ and purchase something, you want to be sure that you are actually putting your credit card information at amazon.com and not at http://www.fakeyououtwithafalseaddress.com/. The CA will certify that you are talking with the server to which you want to be connected. There are mechanisms that can route you to the wrong server. So, using a CA such as Verisign, you can be sure that you have connected to the correct server. You may ask, "How will I know this?" Here is how it works.
You have a business and you want to set up a secure server that will accept credit cards. Following are the steps to follow:
-
Install the hardware.
-
Install the software.
-
Install the web server (called the "HTTP stack" or "HTTP server").
-
Set up the application to process the credit card information.
-
Set up the DNS.
-
Create a key ring file request for your HTTP server.
-
Send the key file request to a CA (with payment and some identification on your company).
-
The CA will certify the request.
-
The CA will send the request back to you.
-
You will merge the request into your key ring file.
-
Now you are ready to turn on SSL.
Now your question is probably, "What is the process to turn on SSL?" The answer for the most part is simple.
-
Turn on the port (more on that later) and the port number you want to use for SSL. The default port is 443, so turn this setting "on" in your server.
-
At the URL, enter "https" (note the "s"). Example: http://www.https://www.thisismywebpageanditissecure.com.
There are several methods to enable SSL. You can turn off the main port on a server that will accept HTTP requests: For example, Port 80. You can redirect http requests to SSL. See your server Help file to determine if your server supports these functions. Also, you can force a redirect to SSL in your application.
So how does all this information solve our business problem?
-
It enables SSL, using a known CA to certify your server key ring file.
-
It forces the credit card application to only accept https (or SSL) to send the credit card data. This will encrypt the data at the port level (more to follow on this) and keep the data safe. Safe in this case is defined as "very difficult to break."
-
It tells the customer that you are using some type of encryption to keep their credit card information safe. This is the customer confidence part of the business transaction very important.
-
It monitors your server and your systems to break-ins and hacking attempts.
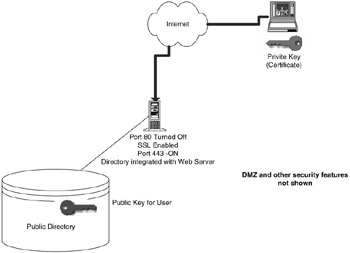
Figure 3.7 shows a browser accessing a server with SSL enabled. The user will use, or be forced to use, https:// in the URL name. The transmission will not be encrypted using SSL.
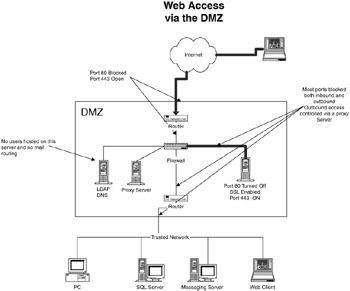
Figure 3.7