Mass Verification
|
| < Day Day Up > |
|
Have you ever noticed the common trend in e-mail addresses? Almost every e-mail server has an address called neo@company.com, a name made popular by the hit movie “The Matrix.” The names John, Paul, Peter, and Adam are also highly popular e-mail addresses. This predictable nature of e-mail addresses has led spammers to become more creative in how they harvest e-mail accounts, by using a method known as brute-force or mass verification.
When attempting to deliver an e-mail message to john@mailserver.com, adam@mailserver.com, and paul@mailserver.com, you are able to determine if that e-mail account is legitimate and will accept e-mail by the messages the server returns. For example:
$ telnet mx1.hotmail.com 25 Trying 65.54.xxx.xx... Connected to mx1.hotmail.com. Escape character is '^]'. 220 mc5-f30.law1.hotmail.com Microsoft ESMTP MAIL Service, Version: 5.0.2195.5600 ready at Mon, 13 Jan 2003 20:50:59 -0800 helo spammerx 250 mc5-f30.law1.hotmail.com Hello [127.0.0.1] mail from: spammerx@hotmail.com 250 spammerx@hotmail.com....Sender OK RCPT To: john@hotmail.com 550 Requested action not taken: mailbox unavailable $ telnet mx1.hotmail.com 25 Trying 65.54.xxx.xx... Connected to mx1.hotmail.com. Escape character is '^]'. 220 mc5-f30.law1.hotmail.com Microsoft ESMTP MAIL Service, Version: 5.0.2195.5600 ready at Mon, 13 Jan 2003 20:50:59 -0800 helo spammerx 250 mc5-f30.law1.hotmail.com Hello [127.0.0.1] mail from: spammerx@hotmail.com 250 spammerx@hotmail.com....Sender OK RCPT To: peter@hotmail.com 250 Requested mail action okay, completed
This example shows that john@hotmail.com is not a valid account, while peter@hotmail.com is a valid account and will accept e-mail. However, neither account will receive any notification that their account has been verified.
Testing a large dictionary of common names on a small e-mail server would result in discovering most accounts within a few hours (hotmail would take a bit longer). This produces a highly efficient technique of finding “random” e-mail accounts on a mail-server. Often used against free e-mail providers, this method is highly popular. Many spammers have harvested humongous lists against e-mail servers such as hotmail and yahoo, where the user base is very significant.
When verifying e-mail addresses, it is necessary to be creative when setting which host you “HELO” from. Many e-mail servers (for example, lycos.com) will refuse a HELO from hotmail.com or yahoo.com, therefore using a random host such as HELO mail.jbconnect.dk will greatly reduce the amount of false negatives you get, as seen in the following message reply:
You are seeing this message mostly due to one of your e-mails being blocked by our systems. Your e-mail has been blocked because your mailserver sent e-mail to us using a suspicious HELO string. HELO is an SMTP command with which one e-mailserver identifies itself to another when starting an SMTP session to deliver e-mail. Some spammers, in order to forge headers, issue forged HELOs that match the IPs and / or domains of our system, and those of other free-mail providers, such as – >HELO e-mail.com >HELO operamail-com.mr.outblaze.com >HELO 205.158.xx.xx >HELO yahoo.com >HELO SGSScstsgs.excite.com Your e-mailserver sent us e-mail with HELO yahoo.com
This verification method is often taken one step further. Although the e-mail accounts with John, Paul, and Peter are common names and probably exist, what about the e-mail accounts with uncommon names?
Accounts such as ihatespammerx@hotmail.com would never be found in any list of common names. In such a case, spammers begin a very long-winded process of verifying every possible combination of letters and numbers in an e-mail address, such as:
a@hotmail.com b@hotmail.com c@hotmail.com .. .. abea@hotmail.com abeb@hotmail.com abec@hotmail.com ..
This technique will find every e-mail account on the server if the e-mail server is not set up to deny connections after too many failed recipient (RCPT) attempts. Many applications exist to accomplish this. One such application is 1st E-mail address harvester (see Figure 4.6).
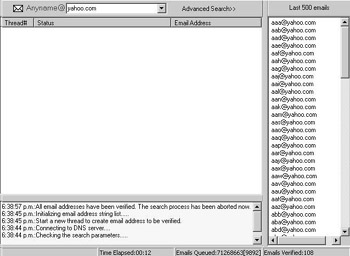
Figure 4.6: 1st E-mail Address Harvester
In this example, 71,268,663 e-mail addresses will be verified at yahoo.com (all alphanumeric accounts up to eight characters in length). As you can see, the results are quick. After running the program for 12 seconds, there is already 108 verified e-mail accounts that are ready for spam.
Although this method can easily produce a very large amount of e-mail accounts, you have no idea who is behind the e-mail account or what they like or dislike. Spammers often use this method when selling a product that has no clearly defined demographic. The popular 419 Nigerian scam that cons unsuspecting victims into believing they are freeing tied up money from Nigeria while stealing millions from them, often targets anyone able of receiving an e-mail. There is no way of targeting naive people, so the scammers simply broadcast their message to as many people as possible. Mass verification provides an easy method of finding active e-mail accounts on e-mail servers that may have poor spam filtering installed.
Verification also plays a large part in existing e-mail lists. There is often a price attached to sending a piece of spam, whether in the time it takes the spammer to send it or the amount being paid for someone else to send it. You do not want to waste time or money sending spam to an account that doesn’t exist.
This is where e-mail verification helps. Any self-respecting spammer will verify a list of e-mails before spamming it. Many applications exist that will scan a list of e-mails, looking for any obvious “bad ideas” such as .mil or .gov e-mail addresses. They will then verify all of the accounts remaining with the e-mail host, thus reducing the amount of e-mail that has to be sent and making sure only legitimate accounts receive the spam (see Figure 4.7).
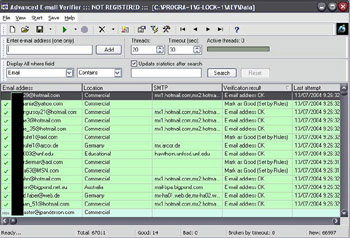
Figure 4.7: Verified and Ready for Spam
Verification is a vital part of spam; it allows you to not only harvest new e-mail accounts but to also verify the validity of existing accounts. It should be the first step any spammer takes before sending spam. It can also help reduce host blacklisting by real-time black hole lists (RBLs) by attracting less attention to the sending host by sending the spam more efficiently and with a higher delivery rate.
Inside Information
“If you enter your e-mail address we promise to never sell, lease or send you any unsolicited e-mail (or spam).”
Sounds promising, right? For many large corporations this is true; however, for the individuals who work within that corporation it’s an entirely different story.
Take Jason Smathers, a 24-year-old AOL employee who was arrested in June of 2004. Jason had stolen 92 million AOL screen names from AOL and sold them to 21-year-old Sean Dunaway. Sean then sold the screen names to various spammers for a total of $52,000.00, who then used them to promote herbal penis enlargement pills.
After an undercover sting, both Jason and Sean were arrested under the new Controlling the Assault of Non-Solicited Pornography and Marketing (CAN-SPAM) Act of 2003. They’re currently facing up to five years in prison or a $250,000.00 fine. AOL would never sell your private data; there is not enough profit to be made in it, and they stand to loose too much if their customers leave them. However, for the lowly underpaid employee it is a different story. Sean would have offered Jason at least $30,000.00 for the list, probably in cash; for many, this would be enough for them to betray their company. Personally, I would have a hard time saying no. I am 22 and currently saving for my first house; $30,000.00 would definitely help my efforts. This is how personal data is often leaked; employees and ex-employees sometimes seek revenge against their employer, so when a lucrative offer comes up they are quick to betray any trust they may have.
Corporations know that you do not want your e-mail address used for spam, and they know that they cannot legally sell it without your consent. However, if you agree to their terms and conditions without reading the fine print, you may be giving a company your name, interests, and e-mail address, plus the right for them to send you spam. Hotmail.com is a classic example of this. Have you ever read the terms and conditions carefully? Figure 4.8 shows a portion of the MSN Privacy Agreement as shown on http://privacy.msn.com/.

Figure 4.8: Corporate Spammers
The three outlined boxes are of great interest:
“MSN does not sell, rent or lease its customer lists to third parties. MSN may, from time to time, contact you on behalf of external business partners about a particular offering that may be of interest to you. In those cases, your personal information (e-mail, name, address, telephone number) is not transferred to the third party.”
“Personal information collected on this site may be stored and processed in the United States or any other country in which Microsoft or its affiliates, subsidiaries or agents maintain facilities, and by using this site, you consent to any such transfer of information outside of your country. Microsoft abides by the safe harbor framework as set forth by the U.S. Department of Commerce regarding the collection, use, and retention of data from the European Union.”
“MSN offers its customers choices for the collection, use and sharing of personal information. You may go to the MSN Communications Preferences page to proactively make choices about the use and sharing of your personal information. You may choose not to receive marketing material from MSN or on behalf of external third party business partners. You may also stop the delivery of future promotional e-mail from MSN by following the specific instructions in the e-mail you receive. The instructions explain how to stop receiving such e-mails.”
For a loose translation, while it may not be their intent, by the letter of their agreement, MSN may:
-
Serve as a proxy for other companies’ (“offerings that may be of interest to you.”), but one man’s interesting offer may be another man’s spam.
-
Transfer your data from a highly-secure US location owned or operated by Microsoft, to a location outside the US that may or may not be so secure. At a certain level, this is like making a reservation at a 5 star hotel, only to end up in a “sister location” under the freeway because the 5 star hotel was overbooked.
Microsoft is very smart; in my opinion they are corporate spammers but you would never know it. They have the full legal right to send you spam, share your information with any part of Microsoft, and send your data to other countries where the security and integrity may be significantly less than in the US. This is legal spamming and is very common.
I often see companies that have a small checkbox on their sign-up page that, ticked by default reads something along the lines of:
“UnTick this box if you do not want to receive updates, newsletters, or information from this company or any of our affiliate companies.”
“Any of our affiliate companies” includes anyone who is willing to pay us enough money, but don’t worry, we won’t sell your e-mail address to any old spammer. We will, however, send you spam ourselves, which you just gave us permission to do.
Spam is everywhere, and no one does it better than a legitimate corporation.
|
| < Day Day Up > |
|
EAN: 2147483647
Pages: 79