Chapter 13. General IP (Layer 3Layer 4)
|
Chapter 13. General IP (Layer 3/Layer 4)Whether you're running a host-based firewall and are only concerned about services connecting to your system or a multi-homed firewall handling VPNs, DMZs, and internal networks, knowing how to cleanly process basic protocols and services is imperative. This chapter should serve as a guide to creating rules for simple services that might not be covered in other chapters in this book and provides the basics to implement those rules effectively. In nearly every rule we use in this section, you will note that we use "$IPTABLES" instead of "iptables." This is to ease the integration of these examples into scripts. The default on Redhat systems is to place iptables in /sbin/iptables. You might or might not use this. Additionally you might have multiple versions of iptables installed on the system. Using $IPTABLES allows you to select which instance of iptables you want to use. As an example, the following setting at the top of your script will allow you to dictate which version of iptables you are going to use: #!/bin/sh IPTABLES=/sbin/iptables Secondly, in addition to the three internally supplied chains, INPUT, OUTPUT, and FORWARD, there are user-defined chains. Depending on what you're doing, sometimes you'll want to create your own chain. In general you should create user-defined chains whenever you're doing something complicated. This reduces the chances that your user-defined chain is going to interact in a negative way with the other rules on the system. Consider this a suggestion, rather than a hard and fast rule. Sometimes we create user-defined chains, and sometimes we do not in our examples. After you get the hang of creating your own and some of the more complex actions that you can perform in one, it will be very easy to convert our examples into your rules. Finally, throughout this book we use the convention that eth0 is the external (or Internet facing) interface, eth1 is generally reserved for internal wired networks and etH2 for DMZ or wireless networks. We create these settings in all our scripts like this: EXTERNAL=eth0 INTERNAL=eth1 DMZ=eth2 Figure 13.1 shows our firewall with three interfaces and how each device corresponds to each interface. Figure 13.1. Firewall with three interfaces and their corresponding devices.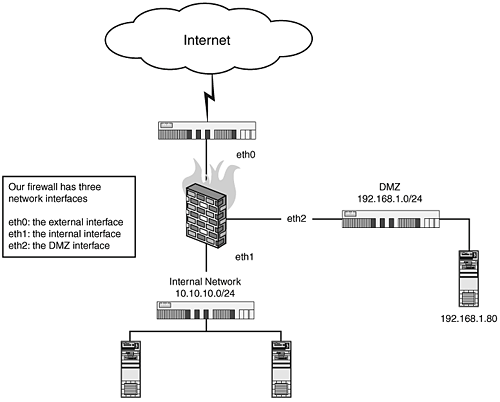 |
|