Addressing Wireless Remote Access Design Considerations
|
EXAM 70-293 OBJECTIVE 3
Wireless networks are fast becoming one of the most common network types. Although they are not cost-effective or efficient as a replacement for wired networking, wireless networks are a great choice for temporary networks, networking in areas where networking is normally difficult, or offering wireless access to customers or employees with portable computers.
Windows Server 2003’s RRAS server can be used to manage wireless connections to the network. If you will be allowing wireless access, you will need to do the following:
-
Configure remote access policies.
-
Determine whether to use IAS for authentication.
-
Configure the WAPs.
The 802.11 Wireless Standards
Today’s wireless networks generally use one of the standards developed by the IEEE under the 802.11 working group and based on the original 802.11 protocol, which supported speeds of 2 Mbps in the 2.4 GHz radio spectrum. The newer standards support higher speeds and are popularly known as Wi-Fi. There are three current versions of 802.11 that define different wireless standards:
-
802.11b was the first standard to be widely accepted. It operates at 11 Mbps and has a range of about 50 meters. It uses the 2.4 GHz spectrum.
-
802.11a appeared in products in 2001. This standard uses the 5 GHz spectrum, has a theoretical maximum speed of 54 Mbps, but does not handle distance and obstacles as well as 802.11b.
-
802.11g is the latest standard, ratified in 2003. It uses the 2.4GHz band and is backward compatible with 802.11b equipment, but supports a theoretical throughput of 54 Mbps.
Note The distance and speed ratings of wireless equipment tend to be optimistic. In practice, the speed will depend on the distance between equipment, any obstacles such as brick walls, interference from power lines or other sources, and other factors.
Using IAS for Wireless Connections
Many WAPs support RADIUS authentication. Because the security of normal wireless authentication with the 802.11 protocols is minimal, using RADIUS provides stronger authentication as well as a centralized source for authentication and accounting for all wireless access. IAS can be used for this purpose.
Because WAPs configured for RADIUS authentication rely on the presence of a RADIUS server, you might need to configure a second IAS server and specify it as a backup server in the WAP configuration. This ensures that wireless users can still connect if the primary IAS server is unavailable.
Configuring Remote Access Policies for Wireless Connections
To enable wireless connections, you need a basic remote access Policy to allow wireless users. This policy can restrict access to a group, require certificate-based authentication, and/or mandate a high level of encryption. Exercise 7.04 describes how to create this remote access policy.
Exercise 7.04: Creating a Policy for Wireless Access
Follow these steps to create a remote access Policy. For this example, the policy will enable access to the Domain Admins group, require certificate-based authentication, and require the highest level of encryption. Remote access Policies are described in more detail later in this chapter.
-
From the IAS or RRAS console, select Remote Access Policies in the left-hand column.
-
Select Action | New Remote Access Policy from the menu.
-
A welcome message is displayed. Click Next to continue.
-
The Policy Configuration Method dialog box is displayed. Select Use the wizard to set up a typical policy and enter Wireless access in the policy name field. Click Next to continue.
-
The Access Method dialog box is displayed, as shown in Figure 7.7. Select Wireless and click Next.
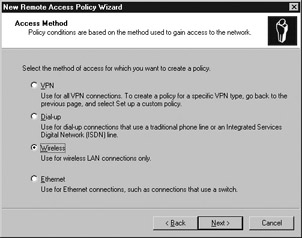
Figure 7.7: Access Method -
The User or Group Access dialog box is displayed. Select Group and click Add. Enter Domain Admins and click OK, and then click Next.
-
You are prompted to choose an EAP type to allow. Select Smart card or other certificate and click Next.
-
A completion message is displayed. Click Finish to exit the wizard.
Multiple Wireless Access Points
You can support multiple WAPs for wireless access using RRAS or IAS for authentication. Because each access point covers only a limited area, it is common to have multiple WAPs. Keep the following considerations in mind when planning to deal with multiple WAPs:
-
IAS authentication will enable all WAPs to use a central server for authentication.
-
Each WAP will need to be added to the IAS server’s list of clients and configured to use RADIUS authentication.
-
There are several variations of the 802.11 protocols and not all devices are compatible. Be sure all WAPs and clients support the same protocols.
Placing CA on VLAN for New Wireless Clients
Wireless clients typically use certificate-based authentication, either using the EAP-TLS protocol with a user certificate or using a certificate stored in a smart card. Each client also needs a computer certificate installed in order to use EAP-TLS authentication. You need to configure a certificate server to issue certificates to wireless clients.
For new clients that might not have a certificate already, one strategy is to create a virtual LAN (VLAN) and place a certification authority (CA) on the VLAN to issue certificates. You can use a remote access policy to restrict new wireless clients to this VLAN so they will be unable to access other network resources and to limit their connection time. After a client successfully connects to the VLAN and is issued a certificate, it can reconnect using the standard wireless access policy and gain full access.
Configuring WAPs as RADIUS Clients
For WAPs to use the IAS server for authentication, you must configure both ends:
-
In the IAS MMC snap-in, add each WAP as a RADIUS client.
-
In the WAP’s configuration, enable RADIUS authentication and specify the IAS server (or both servers, if you have a backup server configured.)
How you configure the WAP varies depending on the hardware in use. Consult the documentation provided by the manufacturer to find out how to do this.
Wireless Encryption and Security
Wireless networks are more vulnerable to snooping than wired networks, since it is difficult to control exactly how far the wireless radio signals travel. Due to this concern, several technologies have been developed to add security to 802.11 wireless networks: WEP (Wired Equivalent Privacy), 802.1x, and WPA (Wi-Fi Protected Access).
WEP (Wired Equivalent Privacy)
WEP was included as part of the 802.11 standard to provide a way to encrypt wireless data and reduce the possibility of intercepted signals. WEP is supported by most 802.11 hardware. When you activate WEP, wireless LAN cards and access points encrypt each packet before transmitting it over the antenna. WEP supports a 40- or 64-bit key for encryption, although some vendor-specific solutions support higher levels of encryption.
Although WEP provides basic privacy, it is not considered highly secure. It uses manually configured fixed keys rather than PKI, and all the equipment must be manually configured with the same key. Because the keys are rarely changed, a dedicated hacker can eventually collect enough data to break the encryption.
| Test Day Tip | WEP only encrypts the data when it is sent between wireless equipment; it does not affect data sent over the wired network, so you should use IPSec if you need end-to-end encryption. |
802.1X
The newer 802.1x standard enables EAP (Extensible Authentication Protocol) authentication methods to be used for wireless networks using the 802.11 standards. Along with supporting stronger authentication, this system can be used to exchange keys and create a more secure encrypted connection than WEP supports.
802.1x usually requires a RADIUS server to work, and is supported by Microsoft IAS in Windows 2000 and Windows Server 2003. Windows XP supports 802.1x natively for wireless connections, and support can be added to other client operating systems.
| Note | Although 802.1x goes a long way toward improving wireless security, it is not by any means perfect—several exploits using forged packets have already been demonstrated. For now, you should always consider wireless networks less secure than a well-secured wired network. |
WPA
At this writing, the IEEE is working on a standard known as 802.11i, a replacement for earlier wireless standards with higher security. Some vendors have already implemented an early version of 802.11i known as WPA (Wi-Fi Protected Access). WPA requires the use of 802.1x authentication and a key exchange and supports stronger encryption than WEP. Windows Server 2003 and Windows XP SP1 include support for WPA. To use this feature, it must also be supported by all the wireless hardware.
|
EAN: 2147483647
Pages: 173