Planning Remote Access Security
|
EXAM 70-293 OBJECTIVE 3.2.2, 3, 3.2, 3.2.1
Windows Server 2003 includes a number of security features for remote access, including some new features that were not available in Windows 2000. When you plan a strategy for remote access security, you need to take several things into account:
-
The functional levels of your domains
-
The methods you will use for data encryption and authentication
-
Whether you will use advanced security features such as callback security and smart cards
These items are discussed in the following sections.
Domain Functional Level
Domains hosted on Windows Server 2003 computers can have one of several different domain functional levels. The functional level of your domain affects which remote access security features you can use. Depending on your needs, you might need to raise the functional level of the domain to take advantage of new security features.
| Test Day Tip | In Windows 2000 terminology, a domain’s mode was either Windows 2000 Native or Mixed-mode. Windows Server 2003’s domain function levels include these two options as well as options for domains with support for .NET and the new Windows Server 2003 security features. |
Determining the Function Level
The domain functional level indicates whether the domain supports new security features added in Windows 2000 and in Windows Server 2003, and also whether support is available for older operating systems to participate in the domain. The following functional levels are possible:
-
Windows 2000 Mixed: Supports a domain containing a combination of Windows 2000, Windows Server 2003, and Windows NT 4.0 servers. Active Directory support is limited and many of the security features of Windows 2000 and Windows Server 2003 are not available.
-
Windows 2000 Native: The same as the native mode supported by Windows 2000. Supports all Active Directory features, but not the latest changes in Windows Server 2003. This level allows Windows 2000 and Windows Server 2003 DCs.
-
Windows Server 2003 Interim: Supports a domain containing Windows Server 2003 and Windows NT 4.0 DCs, but no Windows 2000 DCs.
-
Windows Server 2003: Supports all features of Windows Server 2003. Windows 2000 and earlier domain controllers are not supported.
You can determine the current functional level of a domain by examining its properties in the Active Directory Domains and Trusts console. Exercise 7.05 guides you through this process.
Exercise 7.05: Checking the Domain Function Level
Follow these steps to check a domain’s functional level:
-
From the Start menu, select Programs | Administrative Tools | Active Directory Domains and Trusts.
-
Highlight the domain name in the left-hand column.
-
Select Action | Properties from the menu.
-
The domain properties dialog box is displayed, as shown in Figure 7.8. The text in the lower part of this dialog box shows the current level for the domain and for the Active Directory forest.
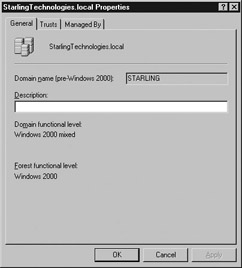
Figure 7.8: Domain Properties
| Note | Along with the domain functional level, the domain controller also keeps track of the functional level of the Active Directory forest. This is the minimum functional level supported by all the domains within the forest. |
Raising the Domain Functional Level
If you have determined that your domain is operating at a lower functional level than you need, you can raise the functional level. However, after this is done, you cannot lower the level. Exercise 7.06 shows the steps to follow to raise a domain’s functional level.
Exercise 7.06: Raising the Domain Functional Level
Follow these steps to raise a domain’s functional level:
-
From the Start menu, select Programs | Administrative Tools | Active Directory Domains and Trusts.
-
Highlight the domain name in the left-hand column.
-
Select Action | Raise Domain Functional Level from the menu.
-
The Raise Domain Functional Level dialog box is displayed, as shown in Figure 7.9. Select the new level from the drop-down list and click Raise.
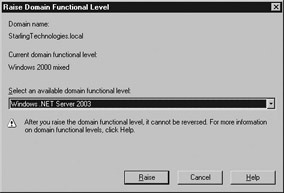
Figure 7.9: Raising the Functional Level -
A dialog box warns you that the change will affect the entire domain and cannot be reversed. Click OK to confirm your choice.
-
After the process is completed, a dialog box indicates that the level was raised successfully. Click OK to exit.
After you have raised the domain’s functional level, the change is replicated to all the domain controllers. This process can take several minutes.
Selecting Authentication Methods
EXAM 70-293 OBJECTIVE 3.2.3
When a user attempts to connect to a remote access server, one or more protocols are used for authentication, verifying the user’s identity. After the user is authenticated, the RRAS server can determine what resources the user is authorized to access.
When you configure a remote access server you can select which authentication methods will be allowed. You should choose authentication methods based on their relative levels of security. Additionally, the methods you choose will depend on the client operating systems and the authentication methods they support.
Disallowing Password-Based Connections (PAP, SPAP, CHAP, MS-CHAP v1)
A number of the available authentication methods use simple user names and passwords for authentication. The simplest of these is PAP (Password Authentication Protocol). In PAP, the client transmits the user’s password as unencrypted text. To ensure a secure network, you should disable SPAP, a variation of the same protocol that is used by Shiva clients.
| Note | Shiva Corporation manufactured some of the most popular routers used in early LANs. Shiva was acquired by Intel and renamed Intel Network Systems, and was later acquired by a different company and renamed Shiva Corporation in 2002. Shiva still makes routers and VPN products, although they support modern authentication methods rather than SPAP. |
CHAP (Challenge Handshake Authentication Protocol) improves security by creating an encrypted challenge and enabling the client to create a response using the password. This avoids sending the password over the network. However, CHAP stores passwords using reversible encryption, and is therefore also considered insecure. MS-CHAP v1, Microsoft’s adaptation of CHAP, improves security but is superceded by the more secure version 2.
To ensure secure remote access, you should disable the less-secure authentication methods. Exercise 7.07 explains how to disable these methods and enable the more secure methods.
Exercise 7.07: Disabling Password-Based Authentication Methods
Follow these steps to disable PAP, CHAP, and MS-CHAP v1 authentication:
-
From the Start menu, select Programs | Administrative Tools | Routing and Remote Access.
-
Highlight the RRAS server name in the left-hand column.
-
Select Action | Properties from the menu.
-
The Properties dialog box is displayed. Click the Security tab.
-
The Security properties are displayed, as shown in Figure 7.10.
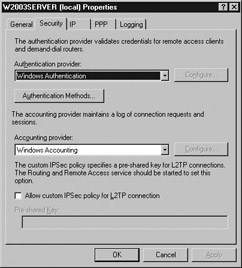
Figure 7.10: Security Properties -
Click the Authentication Methods button.
-
The Authentication Methods dialog box is displayed. Uncheck the box next to Microsoft encrypted authentication (MS-CHAP).
-
Uncheck the box for Encrypted authentication (CHAP).
-
Uncheck the boxes next to Shiva Password Authentication Protocol (SPAP) and Unencrypted password (PAP). Figure 7.11 shows how the dialog box looks with all these options disabled.
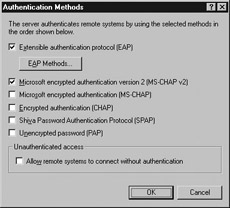
Figure 7.11: Authentication Methods -
Click OK to exit the Authentication Methods dialog box, and then click OK to exit the Properties dialog box and save the changes.
| Test Day Tip | You can also restrict authentication methods by changing settings in the Authentication tab of the Properties dialog box for a Remote Access Policy. Policies are described in detail later in this chapter. |
Using MS-CHAP v2
MS-CHAP v2 is a more secure version of MS-CHAP. This version uses stronger initial encryption keys, uses different keys for sending and receiving data, and supports mutual authentication—this means that after the server sends a challenge to the client and the client responds correctly, proving that it has the correct password, the client sends its own challenge to the server. The client disconnects immediately if the server responds incorrectly to this challenge. This enables the client to detect a server attempting to impersonate the legitimate server.
MS-CHAP v2 is supported by operating systems as old as Windows NT 4.0 and Windows 98, and is even supported by Windows 95 if the Dial-Up Networking upgrade is installed. This means that unless you are supporting very old computers, there is no need to risk security by supporting MS-CHAP v1.
Using EAP
EAP (Extensible Authentication Protocol) is not itself an authentication protocol, but provides a framework that enables authentication using a variety of different methods, known as EAP types. The following are the EAP types supported by Windows Server 2003:
-
EAP-MD5 A challenge-response protocol similar to CHAP. This method uses reversible encryption to store passwords, and is thus vulnerable to the same security problems as CHAP.
-
EAP-TLS (Transport Level Security) A high-security protocol based on the SSL (Secure Sockets Layer) system used for Web server security. EAP-TLS uses encrypted certificates for authentication. It also supports mutual authentication, similar to MS-CHAP v2. This is considered the most secure authentication protocol supported by Windows Server 2003.
Test Day Tip EAP-TLS is the most secure authentication method, but is not supported by all clients. Only Windows 2000, Windows XP, and Windows Server 2003 clients support this authentication method.
Using RADIUS/IAS vs. Windows Authentication
Windows Server 2003 supports RADIUS, an Internet standard for a centralized server to handle a network’s authentication and accounting needs. Internet Access Server (IAS) is Microsoft’s implementation of a RADIUS server, and is included with Windows Server 2003 but is not installed by default. You can install it through the Add/Remove Programs applet in Control Panel as a Windows component. When you configure an RRAS server, you can choose one of two authentication methods:
-
Windows Authentication: The traditional method. Each RRAS server handles authentication itself, and you can configure the authentication methods supported in the Remote Access Policy section of the Routing and Remote Access MMC snap-in. Policies you create for one RRAS server apply only to that server.
-
RADIUS Authentication: The RRAS server acts as a RADIUS client and contacts an IAS (or RADIUS) server to authenticate users. When RADIUS is in use, you configure authentication methods and other remote access security settings from the Remote Access Policy section of the Internet Access Server MMC snap-in. The policies you create for the IAS server apply to any RRAS server that authenticates using that server.
Test Day Tip EAP supports an authentication type called EAP Over RADIUS. This is not an authentication method itself; instead, authentication requests are forwarded to a RADIUS server for processing. This enables you to install and configure EAP types on the RADIUS server and use them from any remote access server, without installing the types on each RRAS server.
Selecting the Data Encryption Level
In a VPN, you can control the level of encryption that is allowed for access. By disallowing unencrypted connections or those that use less-secure encryption, you can decrease the risk of network snooping. You can enable or disable the following levels of encryption:
-
No encryption: Unencrypted connections, unsuitable for VPN use.
-
Basic encryption: Encryption with a 40-bit key, considered relatively easy to break.
-
Strong encryption: Encryption with a 56-bit key. In IPSec, this uses the DES standard for encryption. Although more secure, DES-encrypted data has been demonstrated to be breakable.
-
Strongest encryption: Encryption with a 128-bit key for MPPE connections, or triple DES (3DES), which uses a 168-bit key (56-bit times three) for IPSec connections.
The Strongest Encryption option might not be available in international versions of Windows Server 2003 or US editions without the High Encryption Pack installed. You can enable or disable these encryption levels using remote access Policies. This process is described later in this chapter.
Using Callback Security
Callback security is a high-security system used for dial-in connections. When a client connects to a system using callback, the system disconnects and calls the client back at the client’s phone number. There are two variations of callback:
-
Allowing the user to specify the callback number. This does not provide a high level of security, but does ensure that the client’s phone number can be logged and can be used to avoid long-distance charges being incurred by the client.
-
Using a callback number specified by the administrator. This is very secure because it is difficult to impersonate a valid client, but it requires that a client always connect from the same number.
You can configure callback security as part of a remote access profile. This process is described in the final section of this chapter.
Managed Connections
For a user to connect to a remote access server via dial-in or VPN, the client computer must have the correct settings configured to match the server. Because this can be a daunting process for administrators, Windows Server 2003 supports two components to simplify the process of managing connections:
-
Connection Manager is the client software Windows clients use to make a connection to a dial-in server or VPN server. Current versions of Windows include Connection Manager.
-
Connection Manager Administration Kit (CMAK) is an administrator’s tool that enables you to create a customized version of Connection Manager to distribute to clients. The customizations are stored in a dial-in profile and can include settings for your server, phone numbers, and even custom graphics, icons, and help files.
Connection Manager and CMAK are described in detail in Chapter 5.
Mandating Operating System/File System
Windows Server 2003 supports a new feature called Network Access Quarantine control. This feature enables you to restrict access to particular operating systems, file systems, and other aspects of the client’s configuration. You use a script to accomplish this.
When Quarantine control is enabled, clients can connect normally to the RRAS server and are issued IP addresses. However, when a client first connects, it is put into quarantine mode and allowed only limited access to network resources. A script is then run through Connection Manager on the client machine to determine if the client’s configuration matches the requirements. If it does, the quarantine is released and the client gains full access to the network.
| Test Day Tip | Quarantine Control requires an IAS (RADIUS) server, a customized Connection Manager profile created with CMAK, and a custom script. It also requires that clients run Windows 98, Windows ME, Windows XP, Windows 2000, or Windows Server 2003. |
Using Smart Cards for Remote Access
A smart card is a credit card-sized device that can store a public/private key pair or certificate for encryption. To use smart cards, you install card readers on client computers. Clients can request certificates from a certification authority (CA) and store them on the smart card. Because the encryption keys are not stored on client computers, this eliminates many potential security problems.
Smart cards are typically used with the EAP-TLS authentication method. Because IPSec encryption is used with L2TP VPN connections, smart cards can be used to encrypt a VPN connection that uses L2TP over IPSec.
Smart cards can store an encryption key with a large number of bits, making for highly secure communications. Their chief disadvantage is the smart card hardware; if it is damaged, a new card must be configured for the user, and if the card falls into the wrong hands, it can be used to gain unauthorized access to the network. However, smart cards use a PIN number to eliminate much of this risk.
|
EAN: 2147483647
Pages: 173